How to investigate Microsoft Entra Health monitoring alerts (preview)
Microsoft Entra Health monitoring helps you monitor the health of your Microsoft Entra tenant through a set of health metrics and intelligent alerts. Health metrics are fed into our anomaly detection service, which uses machine learning to understand the patterns for your tenant. When the anomaly detection service identifies a significant change in one of the tenant-level patterns, it triggers an alert.
The signals and alerts provided by Microsoft Entra Health provide you with the starting point for investigating potential issues in your tenant. Because there's a wide range of scenarios and even more data points to consider, it's important to understand how to investigate these alerts effectively. This article provides guidance on how to investigate an alert, but isn't specific to any alert.
Important
Microsoft Entra Health scenario monitoring and alerts are currently in PREVIEW. This information relates to a prerelease product that might be substantially modified before release. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Prerequisites
There are different roles, permissions, and license requirements to view health monitoring signals and configure and receive alerts. We recommend using a role with least privilege access to align with the Zero Trust guidance.
- A tenant with a Microsoft Entra P1 or P2 license is required to view the Microsoft Entra health scenario monitoring signals.
- A tenant with both a Microsoft Entra P1 or P2 license and at least 100 monthly active users is required to view alerts and receive alert notifications.
- The Reports Reader role is the least privileged role required to view scenario monitoring signals, alerts, and alert configurations.
- The Helpdesk Administrator is the least privileged role required to update alerts and update alert notification configurations.
- The
HealthMonitoringAlert.Read.Allpermission is required to view the alerts using the Microsoft Graph API. - The
HealthMonitoringAlert.ReadWrite.Allpermission is required to view and modify the alerts using the Microsoft Graph API. - For a full list of roles, see Least privileged role by task.
Known limitations
- Newly onboarded tenants might not have enough data to generate alerts for about 30 days.
- Currently, alerts are only available with the Microsoft Graph API.
Access Microsoft Entra Health metrics and signals
You can view the Microsoft Entra Health monitoring signals from the Microsoft Entra admin center. You can also view the properties of the signals and the public preview of health monitoring alerts, using Microsoft Graph APIs.
Sign into the Microsoft Entra admin center as at least a Reports Reader.
Browse to Identity > Monitoring and health > Health. The page opens to the Service Level Agreement (SLA) Attainment page.
Select the Scenario Monitoring tab.
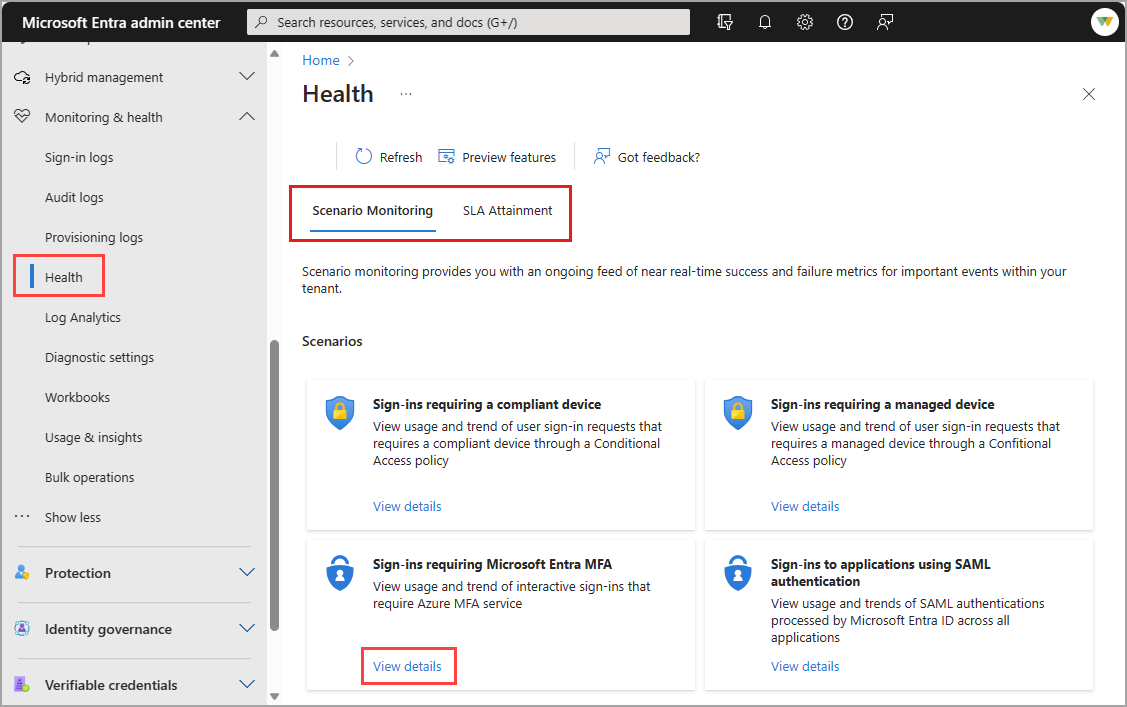
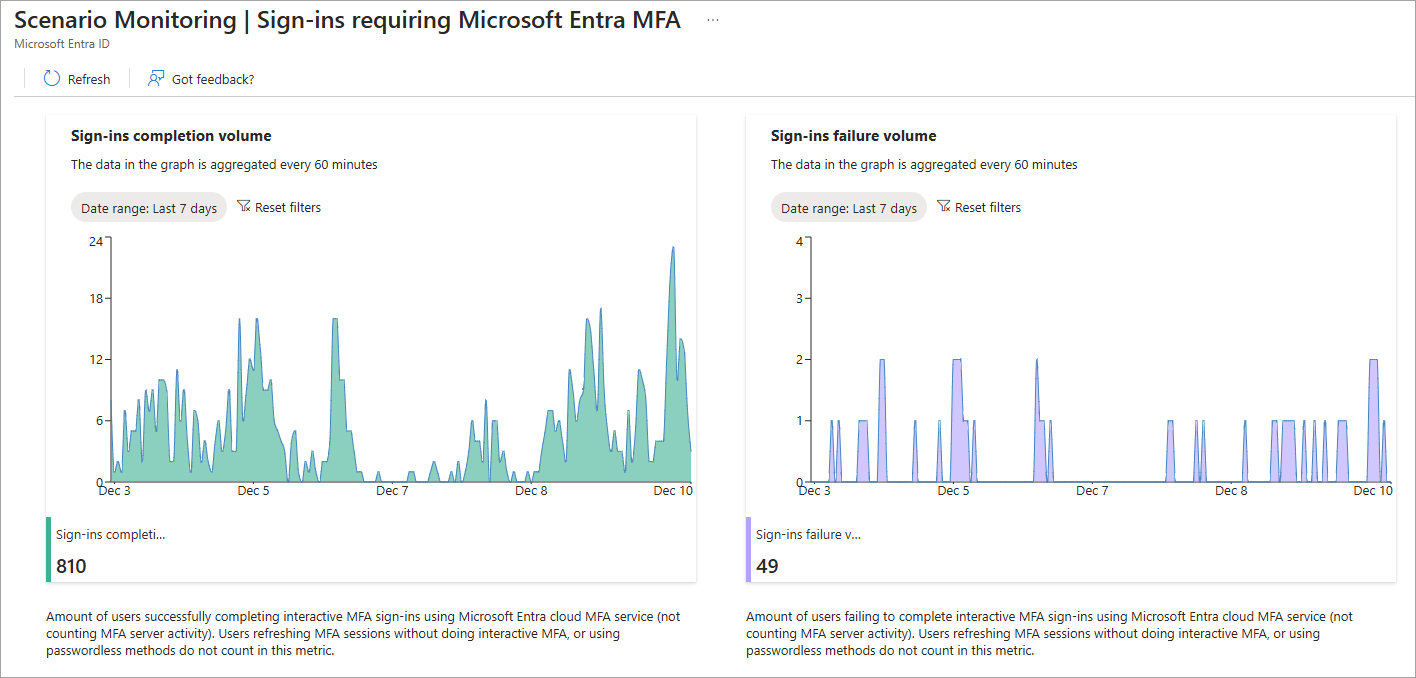
Select View details for the scenario you wish to investigate.
- The default view is the last seven days, but you can adjust the date range to 24 hours, seven days, or one month.
- The data is updated every 15 minutes.
- We recommend reviewing these signals on a regular schedule so that you can recognize your tenant's trends and patterns.