Enable passkeys in Authenticator
This article lists steps to enable and enforce use of passkeys in Authenticator for Microsoft Entra ID. First, you update the Authentication methods policy to allow users to register and sign in with passkeys in Authenticator. Then you can use Conditional Access authentication strengths policies to enforce passkey sign-in when users access a sensitive resource.
Requirements
Android 14 and later or iOS 17 and later.
For cross-device registration and authentication:
- Both devices must have Bluetooth enabled.
- Internet connectivity to these two endpoints must be allowed in your organization:
https://cable.ua5v.comhttps://cable.auth.com
Note
Users can't use cross-device registration if you enable attestation.
To learn more about FIDO2 support, see Support for FIDO2 authentication with Microsoft Entra ID.
Enable passkeys in Authenticator in the admin center
Sign in to the Microsoft Entra admin center as at least an Authentication Policy Administrator.
Browse to Protection > Authentication methods > Authentication method policy.
Under the method Passkey (FIDO2), select All users or Add groups to select specific groups. Only security groups are supported.
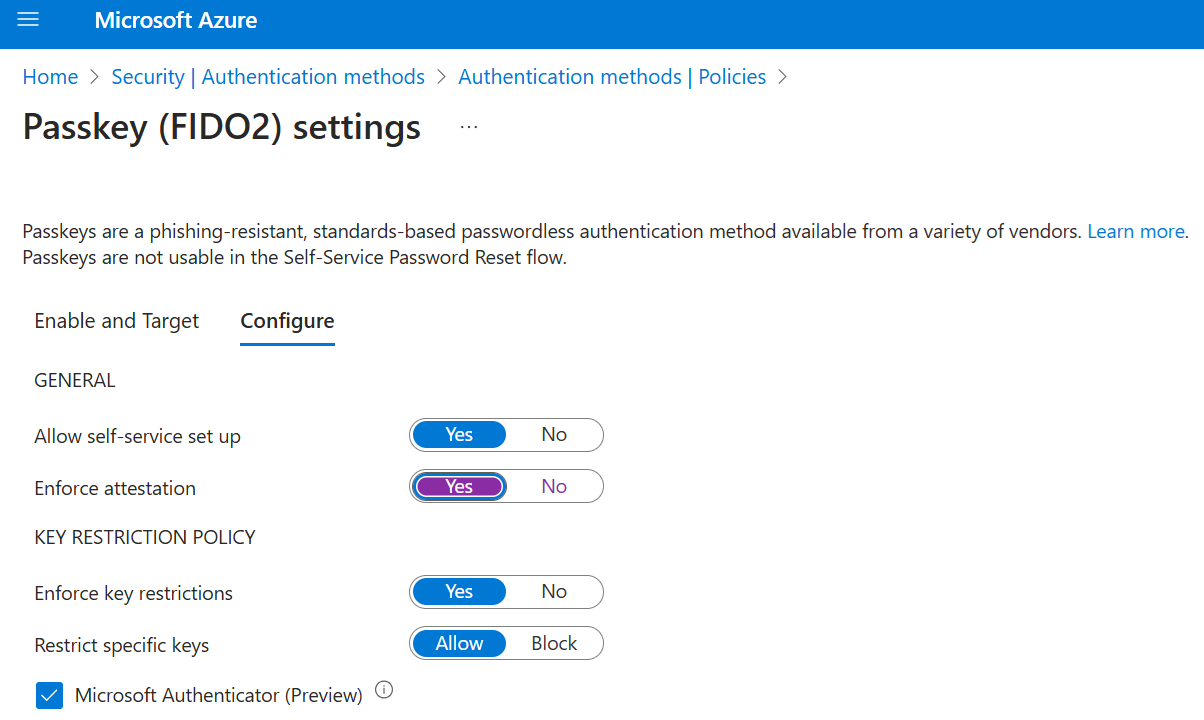
On the Configure tab:
Set Allow self-service set up to Yes. If it's set to No, users can't register a passkey by using Security info, even if passkeys (FIDO2) are enabled by the Authentication methods policy.
Set Enforce attestation to Yes or No.
When attestation is enabled in the passkey (FIDO2) policy, Microsoft Entra ID tries to verify the legitimacy of the passkey being created. When the user is registering a passkey in the Authenticator, attestation verifies that the legitimate Authenticator app created the passkey by using Apple and Google services. Here are more details:
iOS: Authenticator attestation uses the iOS App Attest service to ensure the legitimacy of the Authenticator app before registering the passkey.
Android:
- For Play Integrity attestation, Authenticator attestation uses the Play Integrity API to ensure the legitimacy of the Authenticator app before registering the passkey.
- For Key attestation, Authenticator attestation uses key attestation by Android to verify that the passkey being registered is hardware-backed.
Note
For both iOS and Android, Authenticator attestation relies upon Apple and Google services to verify the authenticity of the Authenticator app. Heavy service usage can make passkey registration fail, and users might need to try again. If Apple and Google services are down, Authenticator attestation blocks registration that requires attestation until services are restored. To monitor the status of Google Play Integrity service, see Google Play Status Dashboard. To monitor the status of the iOS App Attest service, see System Status.
Note
Users can only register attested passkeys directly in the Authenticator app. Cross-device registration flows don't support registration of attested passkeys.
Key restrictions set the usability of specific passkeys for both registration and authentication. You can set Enforce key restrictions to No to allow users to register any supported passkey, including passkey registration directly in the Authenticator app.
You can set Enforce key restrictions to Yes to only allow or block certain passkeys, which are identified by their AAGUIDs. Until mid-February, Security info requires this setting to be set to Yes so that users can choose Passkey in Authenticator and go through a dedicated Authenticator passkey registration flow. If you choose No, users navigating to SecurityInfo might still be able to add a passkey in Authenticator by choosing the Security key or passkey method, depending on their operating system and browser. However, we don't expect many users to discover and use that method.
If you enforce key restrictions and already have active passkey usage, you should collect the AAGUIDs of the passkeys being used today. You can use a PowerShell script to find AAGUIDs that are used in your tenant. For more information, see Find AAGUIDs.
If you set Restrict specific keys to Allow, select Microsoft Authenticator to automatically add the Authenticator app AAGUIDs to the key restrictions list. You can also manually add the following AAGUIDs to allow users to register passkeys in Authenticator by signing in to the Authenticator app or by going through a guided flow on Security info:
- Authenticator for Android:
de1e552d-db1d-4423-a619-566b625cdc84 - Authenticator for iOS:
90a3ccdf-635c-4729-a248-9b709135078f
If you change key restrictions and remove an AAGUID that you previously allowed, users who previously registered an allowed method can no longer use it for sign-in.
Note
If you turn off key restrictions, make sure you clear the Microsoft Authenticator checkbox so that users aren't prompted to set up a passkey in the Authenticator app on Security info.
- Authenticator for Android:
After you finish the configuration, select Save.
If you see an error when you try to save, replace multiple groups with a single group in one operation, and then select Save again.
Enable passkeys in Authenticator by using Graph Explorer
In addition to using the Microsoft Entra admin center, you can also enable passkeys in Authenticator by using Graph Explorer. If you're assigned at least the Authentication Policy Administrator role, you can update the Authentication methods policy to allow the AAGUIDs for Authenticator.
To configure the policy by using Graph Explorer:
Sign in to Graph Explorer and consent to the Policy.Read.All and Policy.ReadWrite.AuthenticationMethod permissions.
Retrieve the Authentication methods policy:
GET https://graph.microsoft.com/v1.0/authenticationMethodsPolicy/authenticationMethodConfigurations/FIDO2To disable attestation enforcement and enforce key restrictions to allow only AAGUIDs for Authenticator, perform a
PATCHoperation by using the following request body:PATCH https://graph.microsoft.com/v1.0/authenticationMethodsPolicy/authenticationMethodConfigurations/FIDO2 Request Body: { "@odata.type": "#microsoft.graph.fido2AuthenticationMethodConfiguration", "isAttestationEnforced": true, "keyRestrictions": { "isEnforced": true, "enforcementType": "allow", "aaGuids": [ "90a3ccdf-635c-4729-a248-9b709135078f", "de1e552d-db1d-4423-a619-566b625cdc84" <insert previous AAGUIDs here to keep them stored in policy> ] } }Make sure that the passkey (FIDO2) policy is updated properly.
GET https://graph.microsoft.com/v1.0/authenticationMethodsPolicy/authenticationMethodConfigurations/FIDO2
Find AAGUIDs
Use the GetRegisteredPasskeyAAGUIDsForAllUsers.ps1 Microsoft Graph PowerShell script to enumerate the AAGUIDs of all registered passkeys in the tenant.
Save the body of this script to a file called GetRegisteredPasskeyAAGUIDsForAllUsers.ps1.
# Disconnect from Microsoft Graph
Disconnect-MgGraph
# Connect to Microsoft Graph with required scopes
Connect-MgGraph -Scope 'User.Read,UserAuthenticationMethod.Read,UserAuthenticationMethod.Read.All'
# Define the output file [If the script is run more than once, delete the file to avoid appending to it.]
$file = ".\AAGUIDs.txt"
# Initialize the file with a header
Set-Content -Path $file -Value '---'
# Retrieve all users
$UserArray = Get-MgBetaUser -All
# Iterate through each user
foreach ($user in $UserArray) {
# Retrieve Passkey authentication methods for the user
$fidos = Get-MgBetaUserAuthenticationFido2Method -UserId $user.Id
if ($fidos -eq $null) {
# Log and write to file if no Passkey methods are found
Write-Host "User object ID $($user.Id) has no Passkey"
Add-Content -Path $file -Value "User object ID $($user.Id) has no Passkey"
} else {
# Iterate through each Passkey method
foreach ($fido in $fidos) {
# Log and write to file the Passkey details
Write-Host "- User object ID $($user.Id) has a Passkey with AAGUID $($fido.Aaguid) of Model type '$($fido.Model)'"
Add-Content -Path $file -Value "- User object ID $($user.Id) has a Passkey with AAGUID $($fido.Aaguid) of Model type '$($fido.Model)'"
}
}
# Log and write a separator to file
Write-Host "==="
Add-Content -Path $file -Value "==="
}
Restrict Bluetooth usage to passkeys in Authenticator
Some organizations restrict Bluetooth usage, which includes the use of passkeys. In such cases, organizations can allow passkeys by permitting Bluetooth pairing exclusively with passkey-enabled FIDO2 authenticators. For more information about how to configure Bluetooth usage only for passkeys, see Passkeys in Bluetooth-restricted environments.
Delete a passkey
If a user deletes a passkey in Authenticator, the passkey is also removed from the user's sign-in methods. An Authentication Policy Administrator can also follow these steps to delete a passkey from the user's authentication methods, but it won't remove the passkey from Authenticator.
Sign in to the Microsoft Entra admin center, and search for the user whose passkey must be removed.
Select Authentication methods, right-click Passkey, and select Delete.
Unless the user initiated the passkey deletion themselves in Authenticator, they need to also remove the passkey in Authenticator on their device.
Enforce sign-in with passkeys in Authenticator
To make users sign in with a passkey when they access a sensitive resource, use the built-in phishing-resistant authentication strength, or create a custom authentication strength by following these steps:
Sign in to the Microsoft Entra admin center as a Conditional Access Administrator.
Browse to Protection > Authentication methods > Authentication strengths.
Select New authentication strength.
Provide a descriptive name for your new authentication strength.
Optionally, provide a description.
Select Passkeys (FIDO2), and then select Advanced options.
Select Phishing-resistant MFA strength or add AAGUIDs for passkeys in Authenticator:
- Authenticator for Android:
de1e552d-db1d-4423-a619-566b625cdc84 - Authenticator for iOS:
90a3ccdf-635c-4729-a248-9b709135078f
- Authenticator for Android:
Select Next, and review the policy configuration.