Error: heap-use-after-free
Address Sanitizer Error: Use of deallocated memory
We show three examples where storage in the heap can be allocated via malloc, realloc (C), and new (C++), along with a mistaken use of volatile.
Example - malloc
// example1.cpp
// heap-use-after-free error
#include <stdlib.h>
int main() {
char *x = (char*)malloc(10 * sizeof(char));
free(x);
// ...
return x[5]; // Boom!
}
To build and test this example, run these commands in a Visual Studio 2019 version 16.9 or later developer command prompt:
cl example1.cpp /fsanitize=address /Zi
devenv /debugexe example1.exe
When Visual Studio appears, press F5 to run example 1.
Resulting error
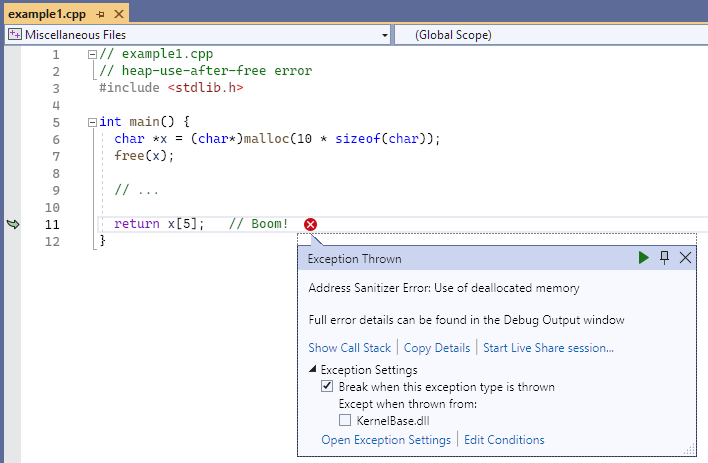
The exception thrown dialog points to line 11, return x [ 5 ], and says: Address Sanitizer Error Use of deallocated memory. Not shown in the screenshot is the output in the console window that shows memory addresses, and a key to identify addressable bytes, partially addressable bytes, freed heap regions, and heap left red zone bytes in the area of the error.
Example - operator new
// example2.cpp
// heap-use-after-free error
#include <windows.h>
int main() {
char *buffer = new char[42];
delete [] buffer;
// ...
buffer[0] = 42; // Boom!
return 0;
}
To build and test this example, run these commands in a Visual Studio 2019 version 16.9 or later developer command prompt:
cl example2.cpp /fsanitize=address /Zi
devenv /debugexe example2.exe
When Visual Studio appears, press F5 to run example 2.
Resulting error - operator new
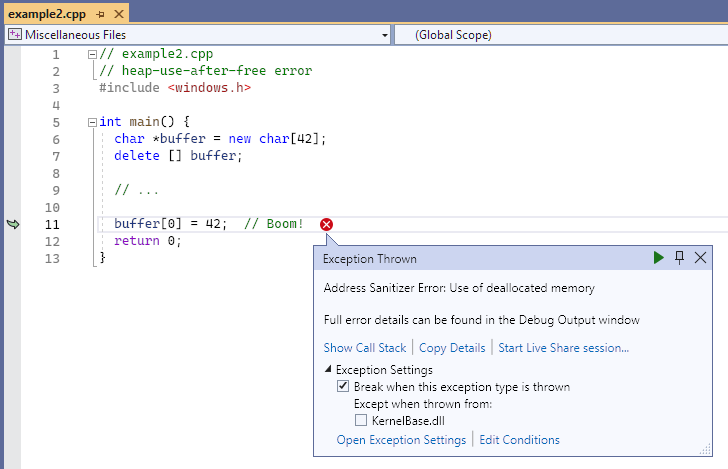
The exception thrown dialog points to line 11, buffer[0] = 42, and says: Address Sanitizer Error: Use of deallocated memory. Not shown in the screenshot is the output in the console window that shows memory addresses, and a key to identify addressable bytes, partially addressable bytes, freed heap regions, and heap left alloca red zone bytes in the area of the error.
Example - realloc
// example3.cpp
// heap-use-after-free error
#include <malloc.h>
int main() {
char *buffer = (char*)realloc(0, 42);
free(buffer);
// ...
buffer[0] = 42; // Boom!
return 0;
}
To build and test this example, run these commands in a Visual Studio 2019 version 16.9 or later developer command prompt:
cl example3.cpp /fsanitize=address /Zi
devenv /debugexe example3.exe
When Visual Studio appears, press F5 to run example 3.
Resulting error - realloc
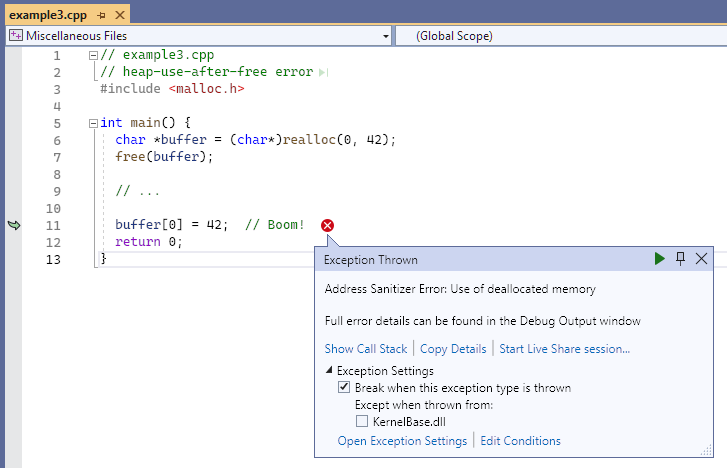
The exception thrown dialog points to line 11, buffer[0] = 42, and says: Address Sanitizer Error: Use of deallocated memory. Not shown in the screenshot is the output in the console window that shows memory addresses, and a key to identify addressable bytes, partially addressable bytes, freed heap regions, and heap left red zone bytes in the area of the error.
Example - volatile
// example4.cpp
// heap-use-after-free error
#include <stdlib.h>
int main() {
volatile char *x = (char*)malloc(sizeof(char));
free((void*)x);
//...
*x = 42; // Boom!
}
To build and test this example, run these commands in a Visual Studio 2019 version 16.9 or later developer command prompt:
cl example4.cpp /fsanitize=address /Zi
devenv /debugexe example4.exe
When Visual Studio appears, press F5 to run example 4.
Resulting error - volatile
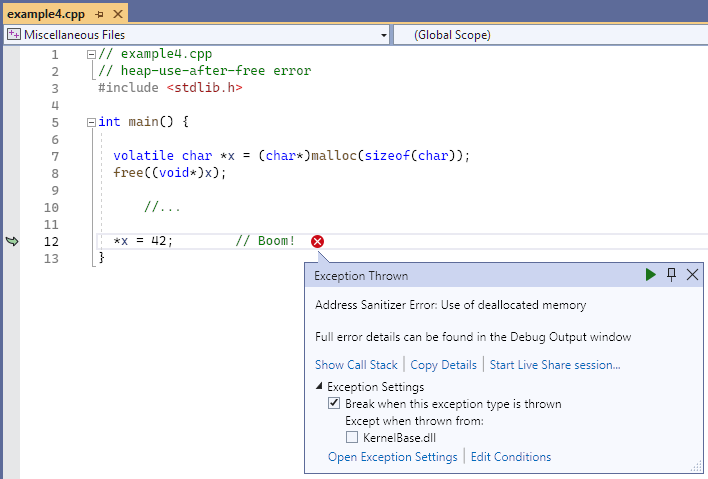
The exception thrown dialog points to line 12, *x = 42, and says: Address Sanitizer Error: Use of deallocated memory. Not shown in the screenshot is the output in the console window that shows memory addresses, and a key to identify addressable bytes, heap left red zone bytes, and some addressable and partially addressable bytes in the area of the error.
See also
AddressSanitizer overview
AddressSanitizer known issues
AddressSanitizer build and language reference
AddressSanitizer runtime reference
AddressSanitizer shadow bytes
AddressSanitizer cloud or distributed testing
AddressSanitizer debugger integration
AddressSanitizer error examples