Use case: Incident response and remediation
Role mentioned: Tier 1 SOC analysts investigating security incidents and resolving non-critical alerts
Scenario
Security Copilot can support Tier 1, entry-level, or junior analysts in assessing and managing incidents with greater efficiency and effectiveness.
This use case presents an abbreviated version of the incident analysis in Case Study: Harnessing Security Copilot in Defending Against Cyberthreats and extended here to include remediation steps.
You are a tier 1 analyst. An incident has been assigned to you by your team lead and your job is to determine whether the incident is indeed malicious and if it is, to resolve it as soon as possible.
Steps
In the Microsoft Defender XDR incident queue, you can see that the high-severity incident titled Multistage incident involving Initial access & Lateral movement on multiple endpoints reported by multiple sources correlates 25 alerts from various Microsoft security solutions. It involves three devices, four users, and one email account.
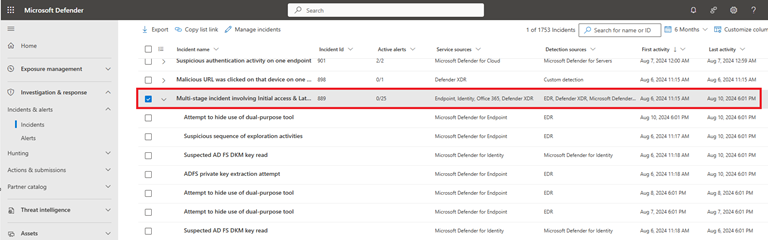
Open the incident page to see the attack story. You check the Security Copilot pane on the right side of the attack story and see that it automatically creates a summary of the incident, along with some steps under guided response.
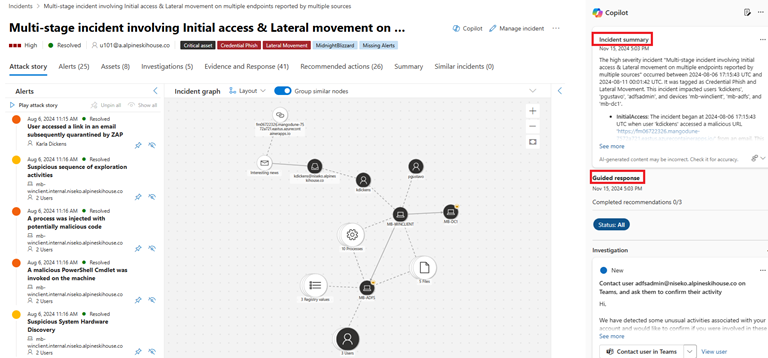
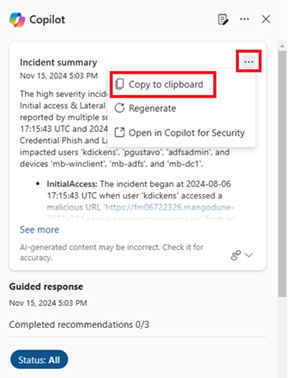
To get an overview of what transpired, you read the summary provided by Security Copilot. You copy the incident summary by selecting Copy to clipboard in the options menu and paste it in another document.
This is useful for the required report as it is already organized by attack phase and highlights the important aspects of the attack. Without Security Copilot, you would need to develop the report from scratch.You then easily determine that the complex incident involved multiple attacks. You go through each of the attack phase as laid out in Initial access, discovery, and defense evasion. For this use case, you are interested in the suspected DCSync attack under the credential access activity.
You select Open in Security Copilot from the Copilot pane to ask about DCSync attacks.
Prompt: What's a DCSync attack? Can you provide its TTPs?
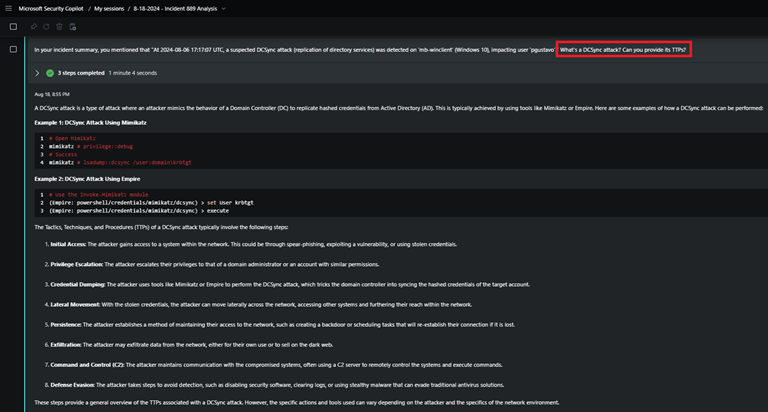 Security Copilot tells you that in DCSync attacks, an attacker mimics the behavior of a domain controller to replicate hashed credentials from Active Directory, usually through Mimikatz or Empire.
Security Copilot tells you that in DCSync attacks, an attacker mimics the behavior of a domain controller to replicate hashed credentials from Active Directory, usually through Mimikatz or Empire.Knowing this, you return to Defender XDR and look at the Suspected DCSync attack more closely. You see that the user sent a replication request to a domain controller. You ask the standalone Security Copilot whether this is considered typical behavior.
Prompt: Is it common for a regular user on a Windows 10 device to send a replication request to a DC?
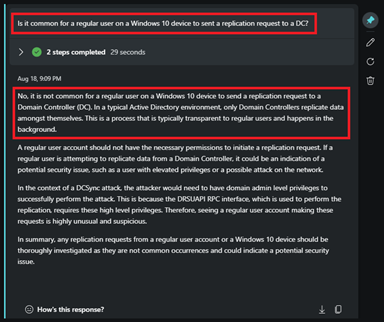
With Security Copilot's response you can confirm that this is a true security incident that needs further investigation by the Tier 2 team.The next security alert in the incident summary is a suspicious service creation event that is classified under Persistence. You see that the same alert title was generated by Defender for Identity and Defender for Endpoint. However, when you check the alert, you see that the service path listed is encoded.
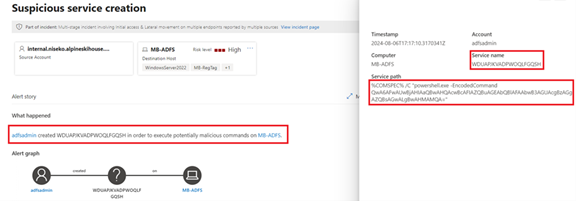
To investigate the script, you consult Security Copilot.
Prompt: Can you decode then tell me more about this service path: %COMSPEC% /C “powershell.exe -EncodedCommand QwA6AFwAUwBjAHIAaQBwAHQAcwBcAFIAZQBuAGEAbQBlAFAAbwB3AGUAcgBzAGgAZQBsAGwALgBwAHMAMQA=”
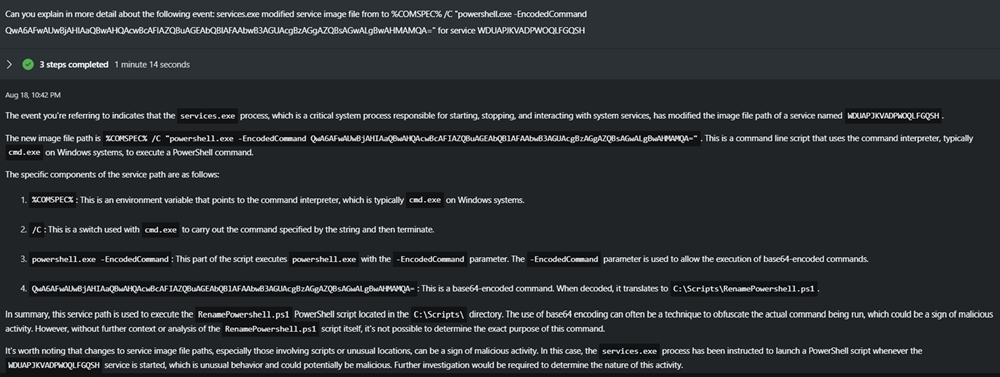
Copilot identifies the encoded command as Base64 encoding and decodes it for you. It appears that the service path is used to run a PowerShell script located in a certain directory. The use of encoding to obfuscate the command could be a sign of malicious activity.As you gain more confidence that this is a true security incident, you can go back to review the Guided response in the Security Copilot pane in the incident page to determine which actions you can take to contain or mitigate the attack.
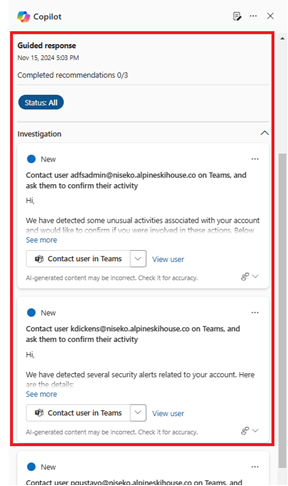
Conclusion
Using Security Copilot can provide several efficiency benefits to analysts tasked to investigate and remediate large incidents involving multiple alerts and entities. It helps in understanding the attack overview, in providing analysis for malicious scripts, in providing context for named attacks, and in performing the necessary steps to remediate the threat.