Silverfort
The Silverfort plugin for Microsoft Security Copilot enables seamless integration of Silverfort's advanced CEF data within the Microsoft Sentinel environment to bring in Identity protection insights. This plugin empowers security teams to enhance their threat detection and response capabilities through intuitive natural language queries and detailed insights.
The Silverfort plugin leverages KQL-based queries to extract and analyze data from Silverfort's security logs within the Microsoft Sentinel workspace. Users can customize their queries using a range of input parameters to retrieve targeted information, enabling more efficient threat investigation and proactive defense measures.
Note
This article contains information about third-party plugins. This is provided to help complete integration scenarios. However, Microsoft does not provide troubleshooting support for third-party plugins. Contact the third-party vendor for support.
Prerequisites
To use the Silverfort plugin you must first configure Common Event Format (CEF) and Syslog through Azure Monitor Agent (AMA) forwarding using the following guide. This plugin queries data stored in the CommonSecurityLog table in a log Analytics workspace enabled for Microsoft Sentinel. For more information, see Ingest syslog and CEF messages to Microsoft Sentinel with the Azure Monitor Agent.
After setting up a forwarder, proceed to:
- Assign a public IP address
- Allow Syslog inbound traffic on port 514 in network settings
You're now ready to set up your Syslog Server in Silverfort to send the events and have the newly configured AMA forward the information to Microsoft Sentinel.
Enter the IP Address of your AMA Forwarder in the Server IP field.
Enter port 514 in the Port field.
Select TCP Protocol in the Protocol Field.
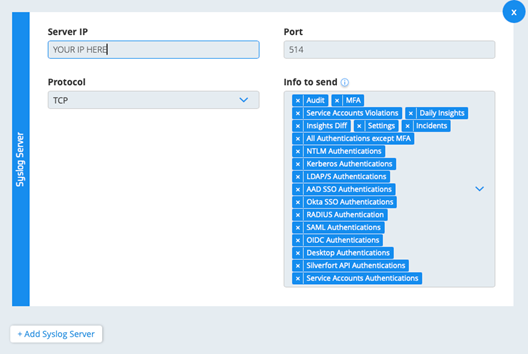
Verify that all the information in the fields are present except the Splunk application.
Select Save All.
Know before you begin
You'll need to take the following steps before using the plugin.
Sign in to Microsoft Security Copilot.
Access Manage Plugins by selecting the Plugin button from the prompt bar.
Next to Silverfort, select the toggle to enable it.
Provide the following information:
- TenantId: The ID of the Microsoft Entra ID Organization that the Microsoft Sentinel workspace is in.
- WorkspaceName: The name of the Microsoft Sentinel workspace.
- SubscriptionId: The ID of the Azure Subscription that the Microsoft Sentinel workspace is in.
- ResourceGroupName: The name of the Resource Group that the Microsoft Sentinel workspace is in.
Save your changes.
Sample Silverfort prompts
After the Silverfort plugin is configured, you can use it by taking one of the following steps:
- Access the plugin capabilities by selecting the Plugin button from the prompt bar and selecting Silverfort.
- Prompt Security Copilot using any of the following example prompts.
The following table lists example prompts to try:
| Capability | Example prompts |
|---|---|
| QuerySilverfortInformation Queries information related to CEF data within Microsoft Sentinel based on time, risk, indicator, source IP, source hostname, and others. |
Provide a count of Silverfort risk requests that have the Silverfort policy name 'mypolicy' in the last week. How many Silverfort MFA subtype requests have there been in the last week that have an MFA response of 'Blocked'?How many requests in the last week have a Silverfort policy action of 'MFA'?Give me the top 10 Silverfort requests with Criticalrisk where the source username is "john.doe@something.com". |
| QuerySilverfortIncidents Queries for all Silverfort related Incidents within the time period specified |
Give me all Silverfort incidents in the last month. Give me all Silverfort incidents in the last week with status ongoing. |
Troubleshoot the Silverfort plugin
Errors occur
If you encounter errors, such as Couldn't complete your request, or An unknown error occurred | Make sure the plugin is turned on. This error may occur if the lookback period is too long, causing the query to attempt to retrieve an excessive amount of data. If the issue persists, sign out of Security Copilot, and then sign back in.
Prompts aren't invoking the correct capabilities
If prompts aren't invoking the correct capabilities, or prompts are invoking some other capability set, you might have custom plugins or other plugins that have similar functionality as the capability set you want to use.
Provide feedback
To provide feedback, contact Silverfort.