Intel 471 Threat Intelligence
Intel 471 delivers relevant and timely insights into the cyber underground.
You can use the Intel 471 Threat Intelligence plugin with Microsoft Security Copilot to provide:
- Rich context about threats through indicators of compromise to facilitate responding to active threats found in the networks and CTI analysis.
- Relevant and timely intelligence information about the activity groups and adversary scenarios.
- Visibility of potential third-party breaches to improve the risk posture and change the odds of a successful attack.
- Vulnerability intelligence, including the precursors to such activity such as an increase in interest levels among activity groups, proof-of-concept (POC) code being developed, traded, or sold, and more.
Note
This article contains information about third-party plugins. This is provided to help complete integration scenarios. However, Microsoft does not provide troubleshooting support for third-party plugins. Contact the third-party vendor for support.
Know before you begin
Integration with Security Copilot requires Intel 471 API credentials, which are available as part of Intel 471's paid subscriptions. For more information, please contact sales@intel471.com. You'll need to take the following steps before using the plugin.
Get your Intel 471 user account and password.
Sign in to Microsoft Security Copilot.
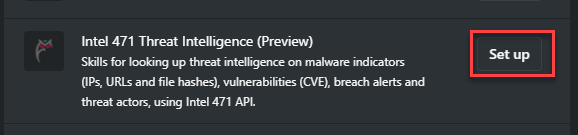
Access Manage Plugins by selecting the Sources button from the prompt bar.
Next to Intel 471 Threat Intelligence, select Set up.
In the Intel 471 Threat Intelligence settings pane, provide your Intel 471 user account and password.
Save your changes.
Sample Intel 471 Threat Intelligence prompts
After the Intel 471 Threat Intelligence plugin is configured, you can use natural language prompts such as the examples provided in the following image. You can also choose them from the prompts menu located in the prompt input.
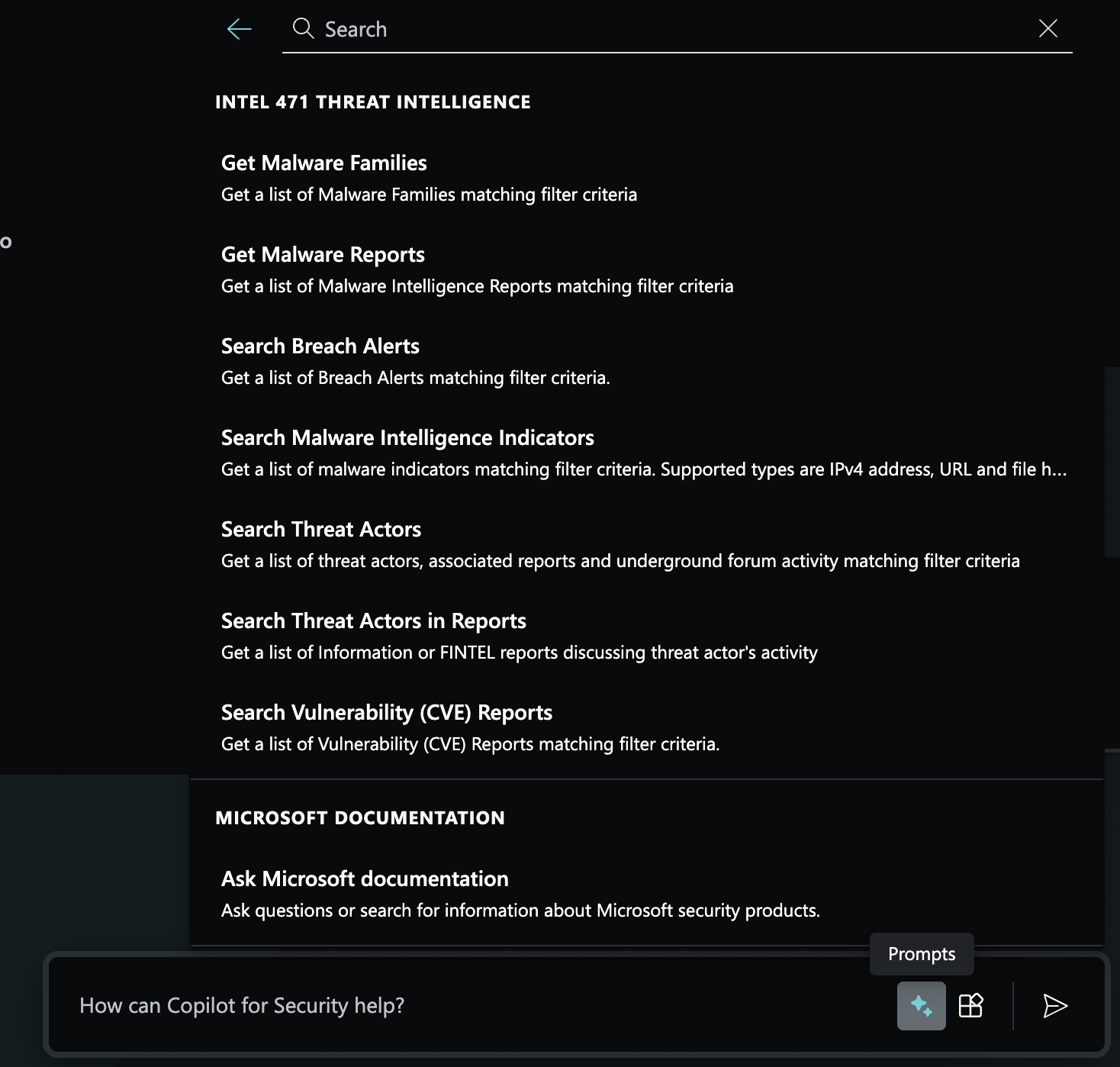
The following table provides examples you can try:
| Capability Prompt Suggestion | Example natural language prompt |
|---|---|
| Malware Intelligence | - Search for Malware Intelligence Indicator with sha256 hash cdf2489960aa1acefedf4f1ab4165365db481591a17e31e7b5fca03cc0ccff0f - Search for reports on operaloader malware family |
| Vulnerability Intelligence | - Search for vulnerability report on CVE-2023-6553 |
| Breach Intelligence | - Find a breach alert for victim TTEC - What is the source of the information for breach of TTEC by actor netsher? |
| Adversary Intelligence | - Find information regarding activity group with handle netnsher. Use Intel 471 plugin |
Provide feedback
To provide feedback, contact Intel 471 Threat Intelligence.