Tutorial: Extract incident entities with non-native actions
Entity mapping enriches alerts and incidents with information essential for any investigative processes and remedial actions that follow.
Microsoft Sentinel playbooks include these native actions to extract entity info:
- Accounts
- DNS
- File hashes
- Hosts
- IPs
- URLs
In addition to these actions, analytic rule entity mapping contains entity types that aren't native actions, like malware, process, registry key, mailbox, and more. In this tutorial, you learn how to work with non-native actions using different built-in actions to extract the relevant values.
In this tutorial, you learn how to:
- Create a playbook with an incident trigger and run it manually on the incident.
- Initialize an array variable.
- Filter the required entity type from other entity types.
- Parse the results in a JSON file.
- Create the values as dynamic content for future use.
Important
Microsoft Sentinel is generally available within Microsoft's unified security operations platform in the Microsoft Defender portal. For preview, Microsoft Sentinel is available in the Defender portal without Microsoft Defender XDR or an E5 license. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
Prerequisites
To complete this tutorial, make sure you have:
An Azure subscription. Create a free account if you don't already have one.
An Azure user with the following roles assigned on the following resources:
- Microsoft Sentinel Contributor on the Log Analytics workspace where Microsoft Sentinel is deployed.
- Logic App Contributor, and Owner or equivalent, on whichever resource group will contain the playbook created in this tutorial.
A (free) VirusTotal account will suffice for this tutorial. A production implementation requires a VirusTotal Premium account.
Create a playbook with an incident trigger
For Microsoft Sentinel in the Azure portal, select the Configuration > Automation page. For Microsoft Sentinel in the Defender portal, select Microsoft Sentinel > Configuration > Automation.
On the Automation page, select Create > Playbook with incident trigger.
In the Create playbook wizard, under Basics, select the subscription and resource group, and give the playbook a name.
Select Next: Connections >.
Under Connections, the Microsoft Sentinel - Connect with managed identity connection should be visible. For example:
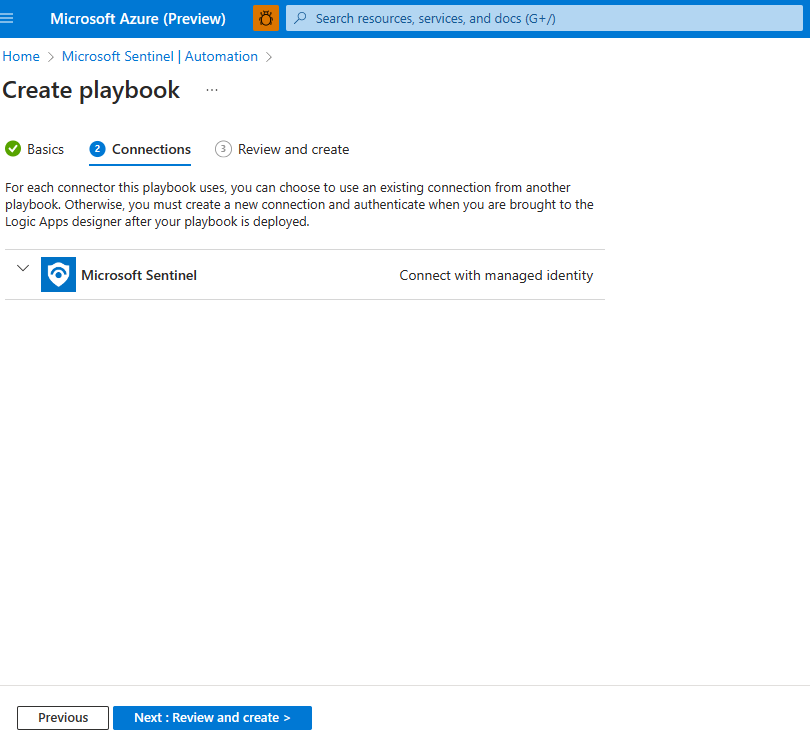
Select Next: Review and create >.
Under Review and create, select Create and continue to designer.
The Logic app designer opens a logic app with the name of your playbook.

Initialize an Array variable
In the Logic app designer, under the step where you want to add a variable, select New step.
Under Choose an operation, in the search box, type variables as your filter. From the actions list, select Initialize variable.
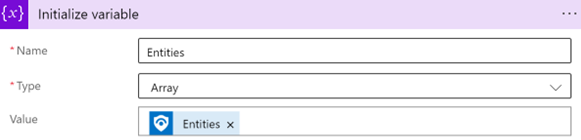
Provide this information about your variable:
For the variable name, use Entities.
For the type, select Array.
For the value, start typing entities and select Entities under Dynamic content.
Select an existing incident
In Microsoft Sentinel, navigate to Incidents and select an incident on which you want to run the playbook.
In the incident page on the right, select Actions > Run playbook (Preview).
Under Playbooks, next to the playbook you created, select Run.
When the playbook is triggered, a Playbook is triggered successfully message is visible on the top right.
Select Runs, and next to your playbook, select View Run.
The Logic app run page is visible.
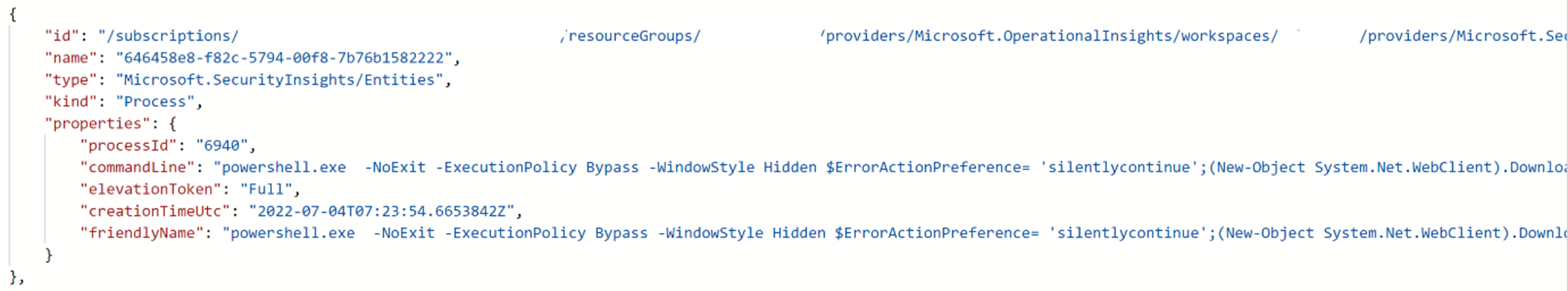
Under Initialize variable, the sample payload is visible under Value. Note the sample payload for later use.
Filter the required entity type from other entity types
Navigate back to the Automation page and select your playbook.
Under the step where you want to add a variable, select New step.
Under Choose an action, in the search box, enter filter array as your filter. From the actions list, select Data operations.
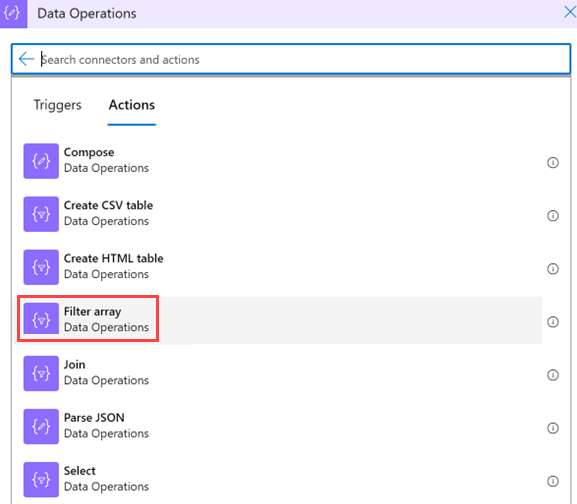
Provide this information about your filter array:
Under From > Dynamic content, select the Entities variable you initialized previously.
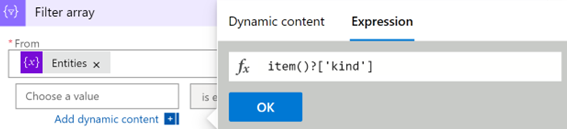
Select the first Choose a value field (on the left), and select Expression.
Paste the value item()?['kind'], and select OK.
Leave the is equal to value (do not modify it).
In the second Choose a value field (on the right), type Process. This needs to be an exact match to the value in the system.
Note
This query is case-sensitive. Ensure that the
kindvalue matches the value in the sample payload. See the sample payload from when you create a playbook.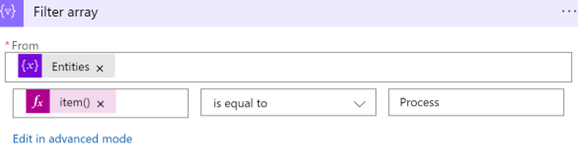
Parse the results to a JSON file
In your logic app, under the step where you want to add a variable, select New step.
Select Data operations > Parse JSON.
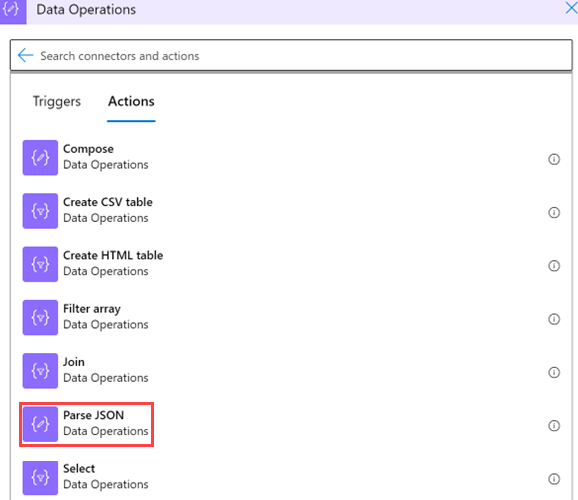
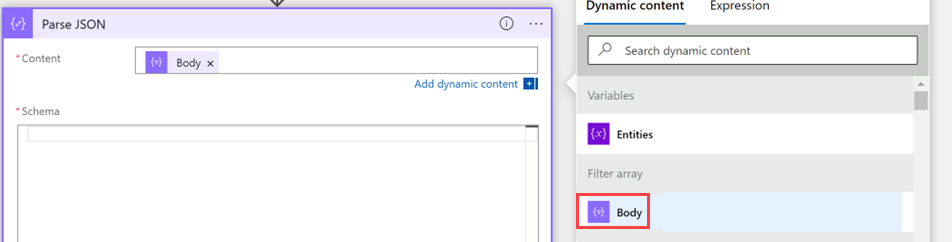
Provide this information about your operation:
Select Content, and under Dynamic content > Filter array, select Body.
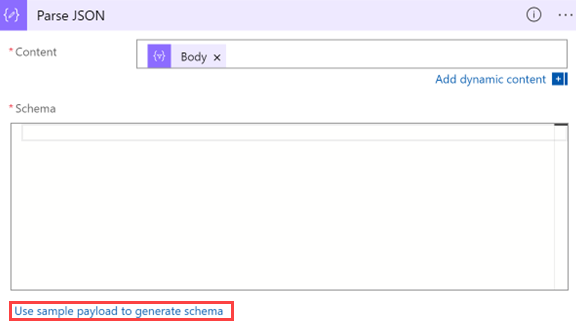
Under Schema, paste a JSON schema so that you can extract values from an array. Copy the sample payload you generated when you created the playbook.
Return to the playbook, and select Use sample payload to generate schema.
Paste the payload. Add an opening square bracket (
[) at the beginning of the schema and close them at the end of the schema].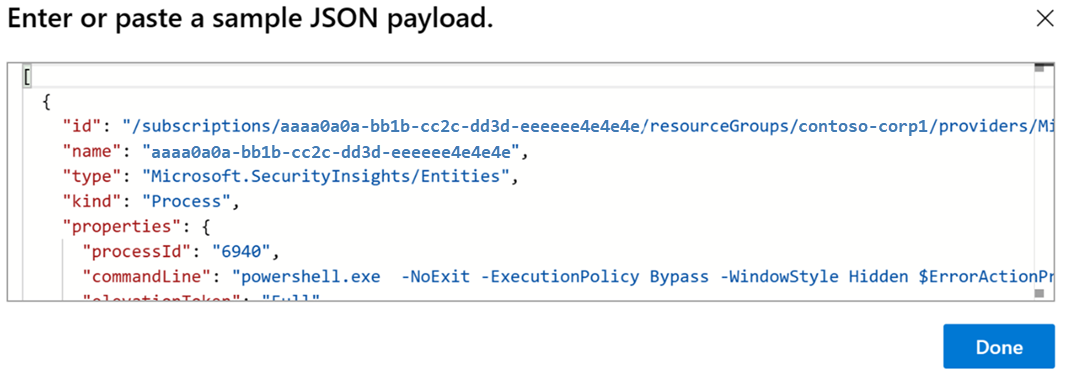
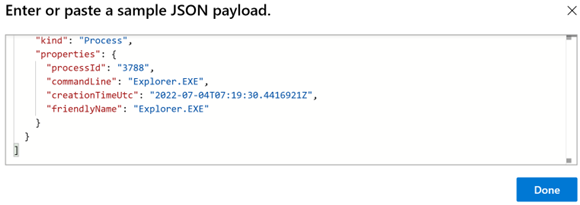
Select Done.
Use the new values as dynamic content for future use
You can now use the values you created as dynamic content for further actions. For example, if you want to send an email with process data, you can find the Parse JSON action under Dynamic content, if you didn't change the action name.
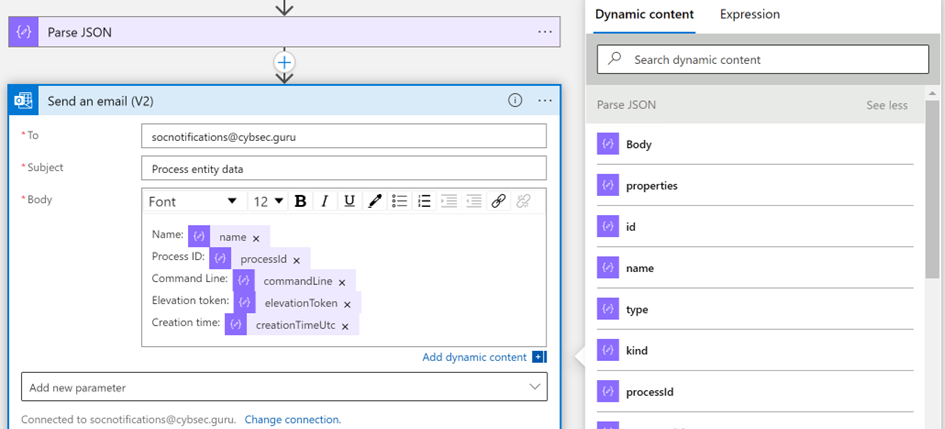
Ensure that your playbook is saved
Ensure that the playbook is saved, and you can now use your playbook for SOC operations.
Next steps
Advance to the next article to learn how to create and perform incident tasks in Microsoft Sentinel using playbooks.