Microsoft Sentinel Solution for SAP BTP: security content reference
This article details the security content available for the Microsoft Sentinel Solution for SAP BTP.
Available security content currently includes a built-in workbook and analytics rules. You can also add SAP-related watchlists to use in your search, detection rules, threat hunting, and response playbooks.
Learn more about the solution.
SAP BTP workbook
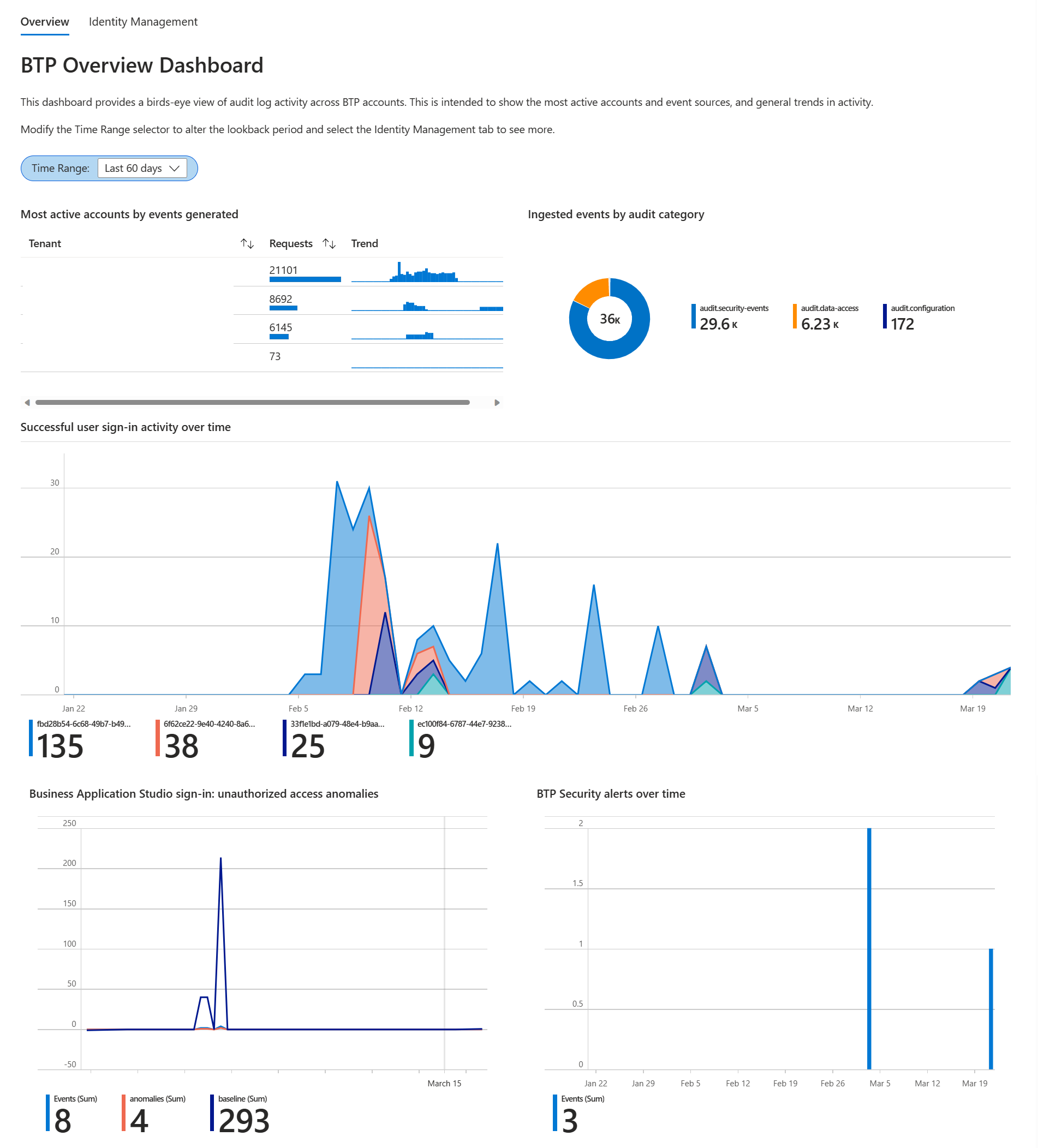
The BTP Activity Workbook provides a dashboard overview of BTP activity.
The Overview tab shows:
- An overview of BTP subaccounts, helping analysts identify the most active accounts and the type of ingested data.
- Subaccount sign-in activity, helping analysts identify spikes and trends that might be associated with sign-in failures in SAP Business Application Studio (BAS).
- Timeline of BTP activity and number of BTP security alerts, helping analysts search for any correlation between the two.
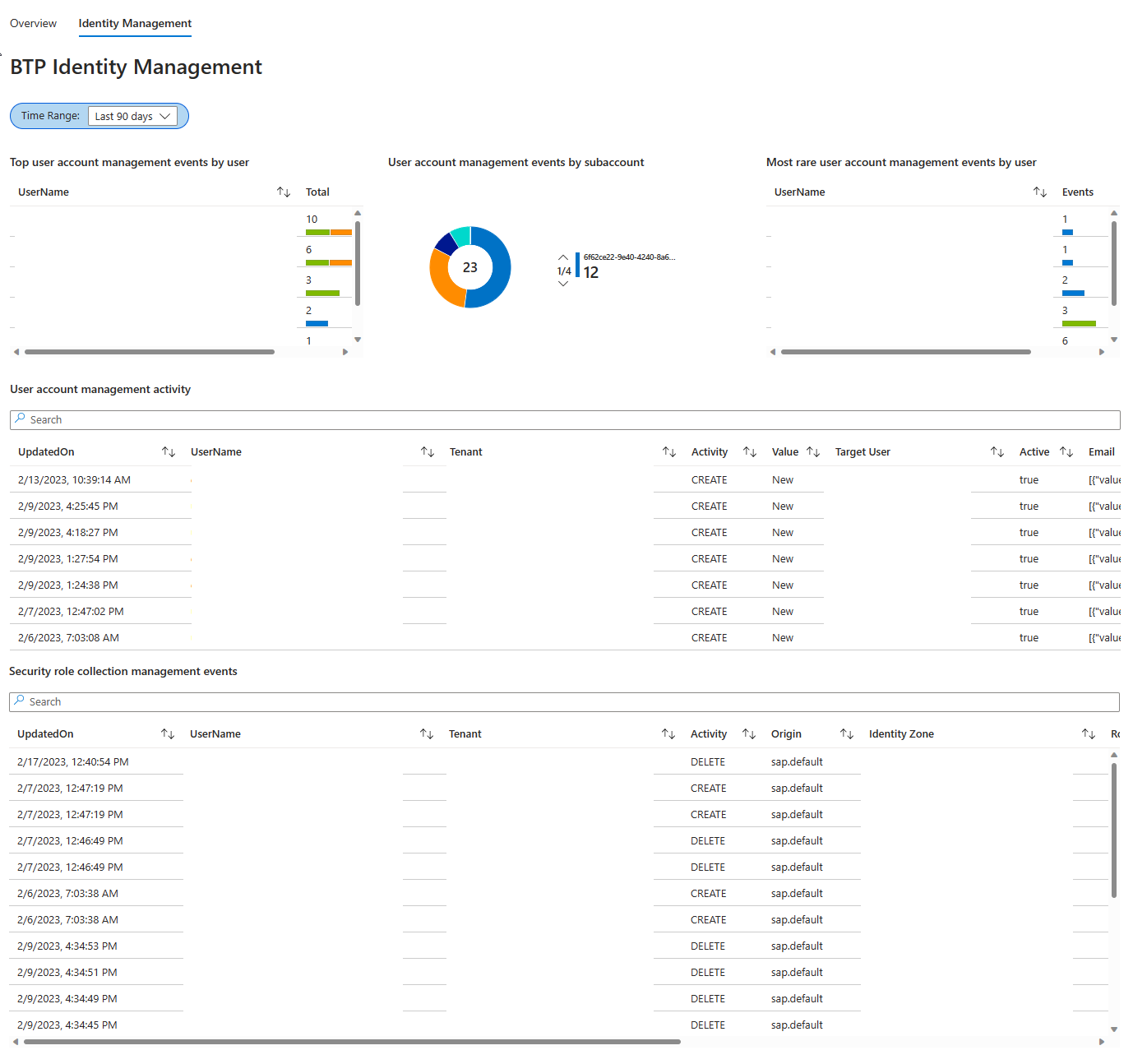
The Identity Management tab shows a grid of identity management events, such as user and security role changes, in a human-readable format. The search bar lets you quickly find specific changes.
For more information, see Tutorial: Visualize and monitor your data and Deploy Microsoft Sentinel Solution for SAP BTP.
Built-in analytics rules
| Rule name | Description | Source action | Tactics |
|---|---|---|---|
| BTP - Failed access attempts across multiple BAS subaccounts | Identifies failed Business Application Studio (BAS) access attempts over a predefined number of subaccounts. Default threshold: 3 |
Run failed sign-in attempts to BAS over the defined threshold number of subaccounts. Data sources: SAPBTPAuditLog_CL |
Discovery, Reconnaissance |
| BTP - Malware detected in BAS dev space | Identifies instances of malware detected by the SAP internal malware agent within BAS developer spaces. | Copy or create a malware file in a BAS developer space. Data sources: SAPBTPAuditLog_CL |
Execution, Persistence, Resource Development |
| BTP - User added to sensitive privileged role collection | Identifies identity management actions where a user is added to a set of monitored privileged role collections. | Assign one of the following role collections to a user: - Subaccount Service Administrator- Subaccount Administrator- Connectivity and Destination Administrator- Destination Administrator- Cloud Connector Administrator Data sources: SAPBTPAuditLog_CL |
Lateral Movement, Privilege Escalation |
| BTP - Trust and authorization Identity Provider monitor | Identifies create, read, update, and delete (CRUD) operations on Identity Provider settings within a subaccount. | Change, read, update, or delete any of the identity provider settings within a subaccount. Data sources: SAPBTPAuditLog_CL |
Credential Access, Privilege Escalation |
| BTP - Mass user deletion in a subaccount | Identifies user account deletion activity where the number of deleted users exceeds a predefined threshold. Default threshold: 10 |
Delete count of user accounts over the defined threshold. Data sources: SAPBTPAuditLog_CL |
Impact |
Next steps
In this article, you learned about the security content provided with the Microsoft Sentinel Solution for SAP BTP.