Work with near-real-time (NRT) detection analytics rules in Microsoft Sentinel
Microsoft Sentinel’s near-real-time analytics rules provide up-to-the-minute threat detection out-of-the-box. This type of rule was designed to be highly responsive by running its query at intervals just one minute apart.
For the time being, these templates have limited application as outlined below, but the technology is rapidly evolving and growing.
Important
Microsoft Sentinel is generally available within Microsoft's unified security operations platform in the Microsoft Defender portal. For preview, Microsoft Sentinel is available in the Defender portal without Microsoft Defender XDR or an E5 license. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
View near-real-time (NRT) rules
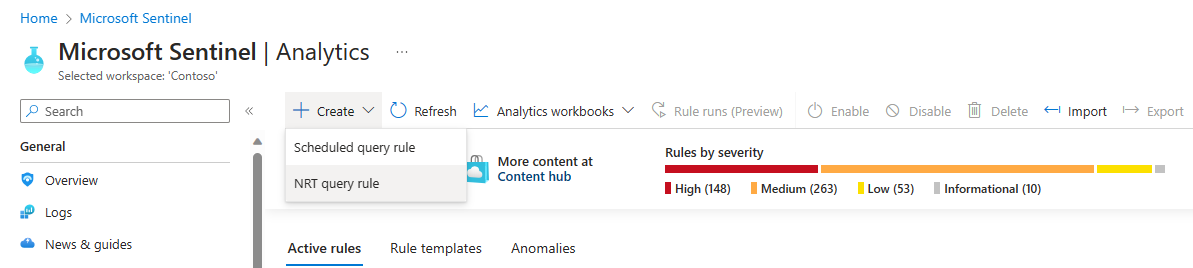
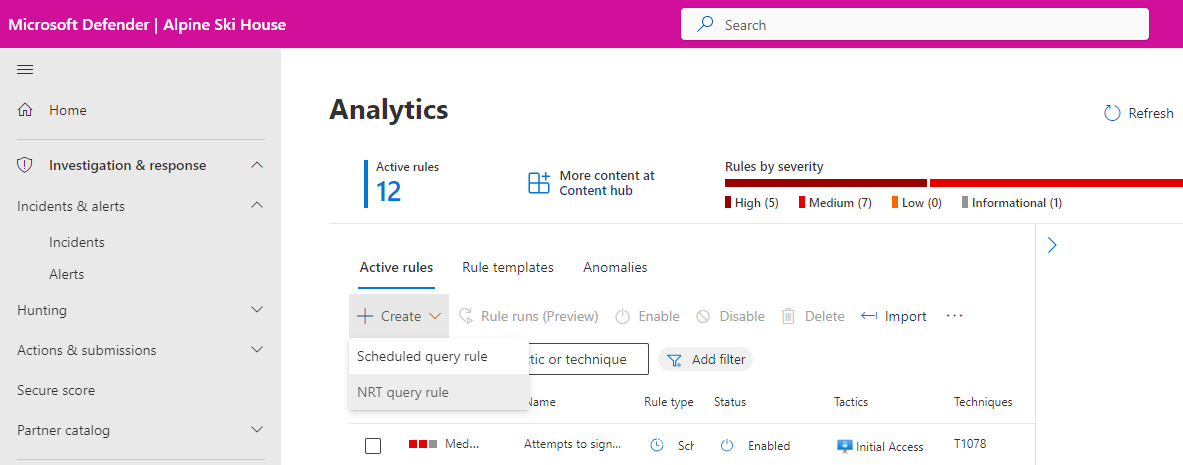
From the Configuration section of the Microsoft Sentinel navigation menu, select Analytics.
On the Analytics screen, with the Active rules tab selected, filter the list for NRT templates:
Select Add filter and choose Rule type from the list of filters.
From the resulting list, select NRT. Then select Apply.
Create NRT rules
You create NRT rules the same way you create regular scheduled-query analytics rules:
Follow the instructions of the analytics rule wizard.
The configuration of NRT rules is in most ways the same as that of scheduled analytics rules.
You can refer to multiple tables and watchlists in your query logic.
You can use all of the alert enrichment methods: entity mapping, custom details, and alert details.
You can choose how to group alerts into incidents, and to suppress a query when a particular result has been generated.
You can automate responses to both alerts and incidents.
You can run the rule query across multiple workspaces.
Because of the nature and limitations of NRT rules, however, the following features of scheduled analytics rules will not be available in the wizard:
- Query scheduling is not configurable, since queries are automatically scheduled to run once per minute with a one-minute lookback period.
- Alert threshold is irrelevant, since an alert is always generated.
- Event grouping configuration is now available to a limited degree. You can choose to have an NRT rule generate an alert for each event for up to 30 events. If you choose this option and the rule results in more than 30 events, single-event alerts will be generated for the first 29 events, and a 30th alert will summarize all the events in the result set.
In addition, due to the size limits of the alerts, your query should make use of
projectstatements to include only the necessary fields from your table. Otherwise, the information you want to surface could end up being truncated.
Next steps
In this document, you learned how to create near-real-time (NRT) analytics rules in Microsoft Sentinel.
- Learn more about near-real-time (NRT) analytics rules in Microsoft Sentinel.
- Explore other analytics rule types.