Add advanced conditions to Microsoft Sentinel automation rules
This article explains how to add advanced "Or" conditions to automation rules in Microsoft Sentinel, for more effective triage of incidents.
Add "Or" conditions in the form of condition groups in the Conditions section of your automation rule.
Condition groups can contain two levels of conditions:
Simple: At least two conditions, each separated by an
ORoperator:- A
ORB - A
ORBORC (See Example 1B below.) - and so on.
- A
Compound: More than two conditions, with at least two conditions on at least one side of an
ORoperator:- (A
andB)ORC - (A
andB)OR(CandD) - (A
andB)OR(CandDandE) - (A
andB)OR(CandD)OR(EandF) - and so on.
- (A
You can see that this capability affords you great power and flexibility in determining when rules will run. It can also greatly increase your efficiency by enabling you to combine many old automation rules into one new rule.
Important
Microsoft Sentinel is generally available within Microsoft's unified security operations platform in the Microsoft Defender portal. For preview, Microsoft Sentinel is available in the Defender portal without Microsoft Defender XDR or an E5 license. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
Add a condition group
Since condition groups offer a lot more power and flexibility in creating automation rules, the best way to explain how to do this is by presenting some examples.
Let's create a rule that will change the severity of an incoming incident from whatever it is to High, assuming it meets the conditions we'll set.
For Microsoft Sentinel in the Azure portal, select the Configuration > Automation page. For Microsoft Sentinel in the Defender portal, select Microsoft Sentinel > Configuration > Automation.
From the Automation page, select Create > Automation rule from the button bar at the top.
See the general instructions for creating an automation rule for details.
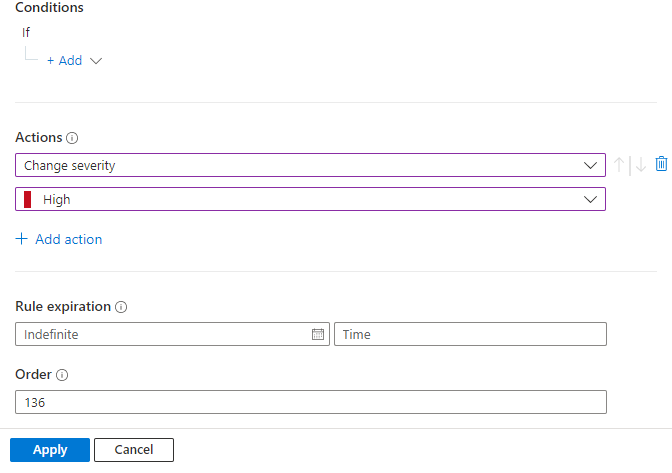
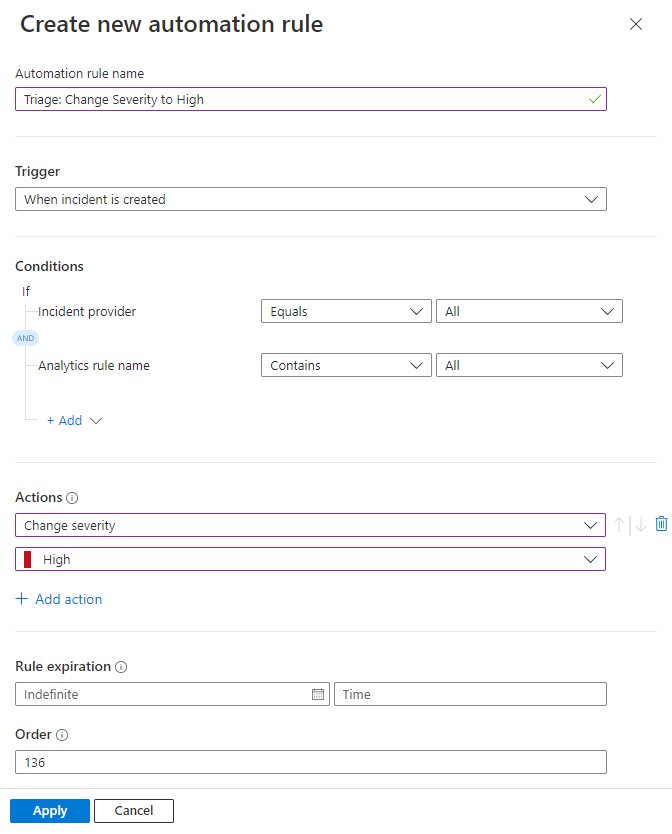
Give the rule a name: "Triage: Change Severity to High"
Select the trigger When incident is created.
Under Conditions, if you see the Incident provider and Analytics rule name conditions, leave them as they are. These conditions aren't available if your workspace is onboarded to the Microsoft Defender portal. In either case, we'll add more conditions later in this process.
Under Actions, select Change severity from the drop-down list.
Select High from the drop-down list that appears below Change severity.
For example, the following tabs show samples from a workspace that's onboarded to the Defender portal, in either the Azure or Defender portals, and a workspace that isn't:
Example 1: simple conditions
In this first example, we'll create a simple condition group: If either condition A or condition B is true, the rule will run and the incident's severity will be set to High.
Select the + Add expander and choose Condition group (Or) from the drop-down list.

See that two sets of condition fields are displayed, separated by an
ORoperator. These are the "A" and "B" conditions we mentioned above: If A or B is true, the rule will run.
(Don't be confused by all the different layers of "Add" links - these will all be explained.)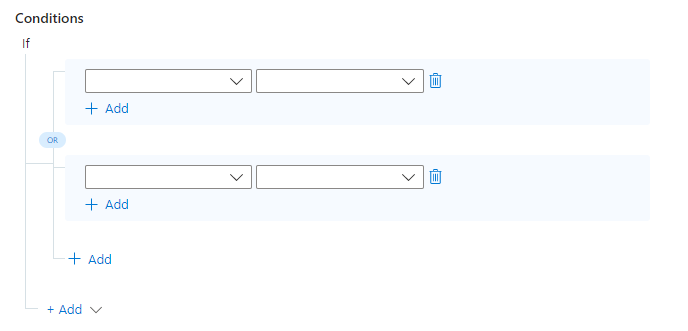
Let's decide what these conditions will be. That is, what two different conditions will cause the incident severity to be changed to High? Let's suggest the following:
If the incident's associated MITRE ATT&CK Tactics include any of the four we've selected from the drop-down (see the image below), the severity should be raised to High.
If the incident contains a Host name entity named "SUPER_SECURE_STATION", the severity should be raised to High.
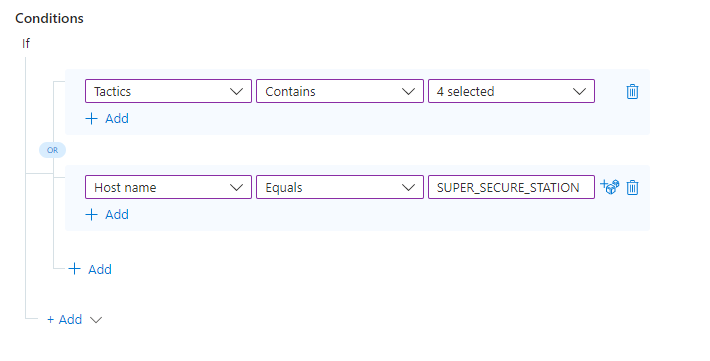
As long as at least ONE of these conditions is true, the actions we define in the rule will run, changing the severity of the incident to High.
Example 1A: Add an OR value within a single condition
Let's say we have not one, but two super-sensitive workstations whose incidents we want to make high-severity. We can add another value to an existing condition (for any conditions based on entity properties) by selecting the dice icon to the right of the existing value and adding the new value below.
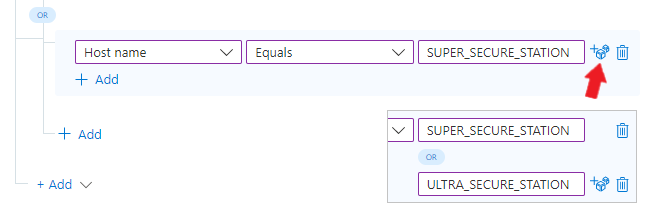
Example 1B: Add more OR conditions
Let's say we want to have this rule run if one of THREE (or more) conditions is true. If A or B or C is true, the rule will run.
Remember all those "Add" links? To add another OR condition, select the + Add connected by a line to the
ORoperator.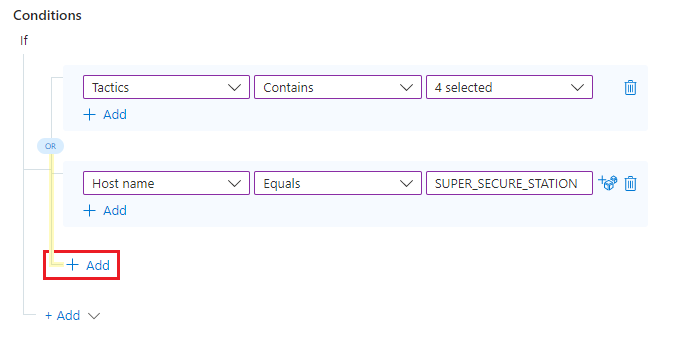
Now, fill in the parameters and values of this condition the same way you did the first two.
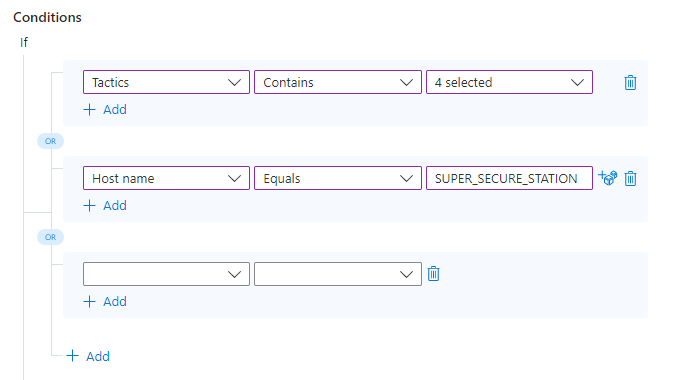
Example 2: compound conditions
Now we decide we're going to be a little more picky. We want to add more conditions to each side of our original OR condition. That is, we want the rule to run if A and B are true, OR if C and D are true.
To add a condition to one side of an OR condition group, select the + Add link immediately below the existing condition, on the same side of the
ORoperator (in the same blue-shaded area) to which you want to add the new condition.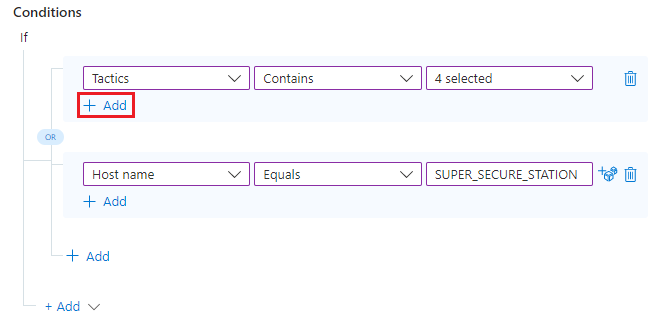
You'll see a new row added under the existing condition (in the same blue-shaded area), linked to it by an
ANDoperator.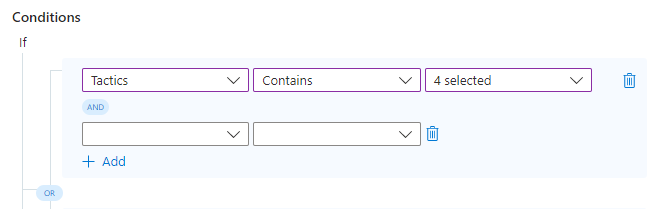
Fill in the parameters and values of this condition the same way you did the others.
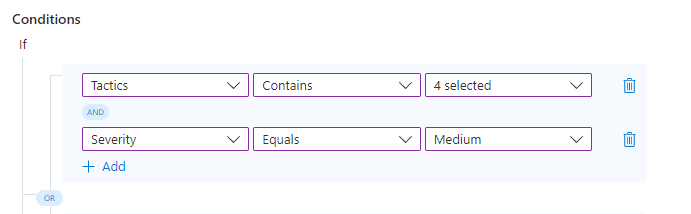
Repeat the previous two steps to add an AND condition to either side of the OR condition group.
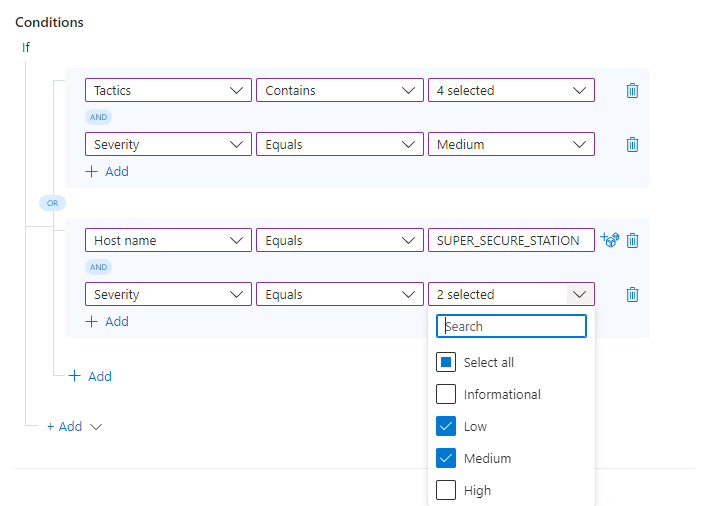
That's it! You can use what you've learned here to add more conditions and condition groups, using different combinations of AND and OR operators, to create powerful, flexible, and efficient automation rules to really help your SOC run smoothly and lower your response and resolution times.
Next steps
In this document, you learned how to add condition groups using OR operators to automation rules.
- For instructions on creating basic automation rules, see Create and use Microsoft Sentinel automation rules to manage response.
- To learn more about automation rules, see Automate incident handling in Microsoft Sentinel with automation rules
- To learn more about advanced automation options, see Automate threat response with playbooks in Microsoft Sentinel.
- For help with implementing automation rules and playbooks, see Tutorial: Use playbooks to automate threat responses in Microsoft Sentinel.