Deny Public Network Access in Azure Database for MySQL - Flexible Server by using the Azure portal
This article describes how you can configure an Azure Database for MySQL Flexible Server instance to deny all public configurations and allow only connections through private endpoints to enhance network security further.
Deny public access during the creation of MySQL flexible server
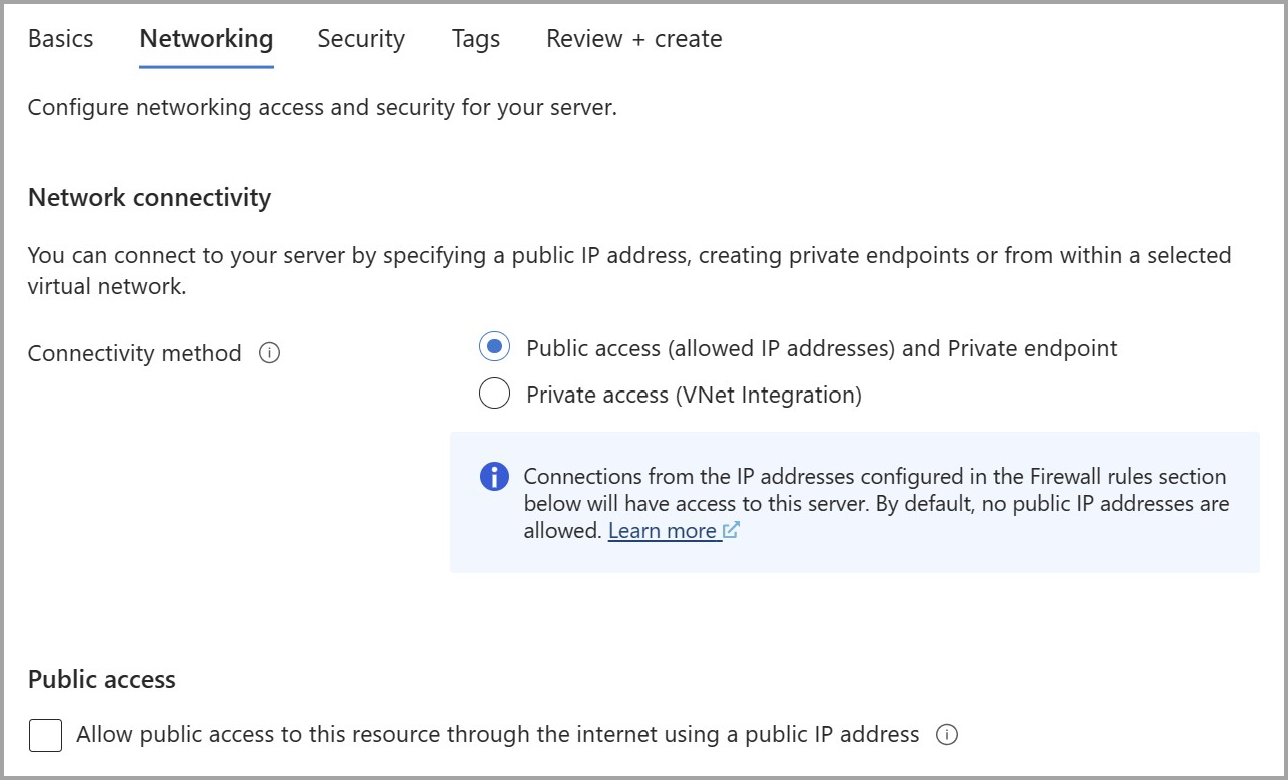
When creating an Quickstart: Create an instance of Azure Database for MySQL with the Azure portal in the Networking tab, choose Public access (allowed IP addresses) and Private endpoint as the connectivity method.
To disable public access on the Azure Database for MySQL Flexible Server instance you are creating, uncheck Allow public access to this resource through the internet using a public IP address under Public access.
After entering the remaining information in the other tabs, select Review + Create to deploy the Azure Database for MySQL Flexible Server instance without public access.
Deny public access to an existing MySQL flexible server
Note
The Azure Database for MySQL Flexible Server instance must have been deployed with Public access (allowed IP addresses) and Private endpoint as the connectivity method to implement this.
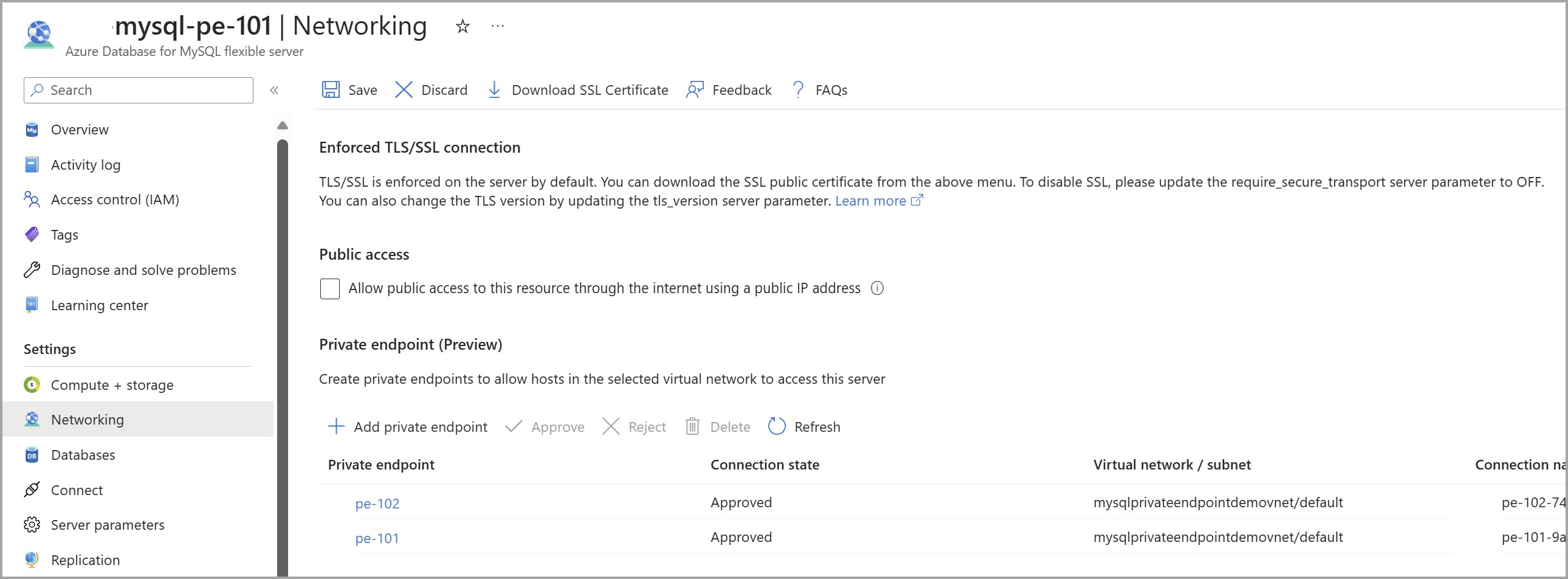
On the Azure Database for MySQL Flexible Server page, under Settings, select Networking.
To disable public access on the Azure Database for MySQL Flexible Server instance, uncheck Allow public access to this resource through the internet using a public IP address under Public access.
Select Save to save the changes.
A notification will confirm that the connection security setting was successfully enabled.
Related content
- configure private link for Azure Database for MySQL Flexible Server from the Azure portal
- manage connectivity
- add another layer of encryption to your Azure Database for MySQL Flexible Server instance using Customer Managed Keys
- Microsoft Entra authentication for Azure Database for MySQL - Flexible Server