Use firewall to restrict outbound traffic using Azure portal
Important
Azure HDInsight on AKS retired on January 31, 2025. Learn more with this announcement.
You need to migrate your workloads to Microsoft Fabric or an equivalent Azure product to avoid abrupt termination of your workloads.
Important
This feature is currently in preview. The Supplemental Terms of Use for Microsoft Azure Previews include more legal terms that apply to Azure features that are in beta, in preview, or otherwise not yet released into general availability. For information about this specific preview, see Azure HDInsight on AKS preview information. For questions or feature suggestions, please submit a request on AskHDInsight with the details and follow us for more updates on Azure HDInsight Community.
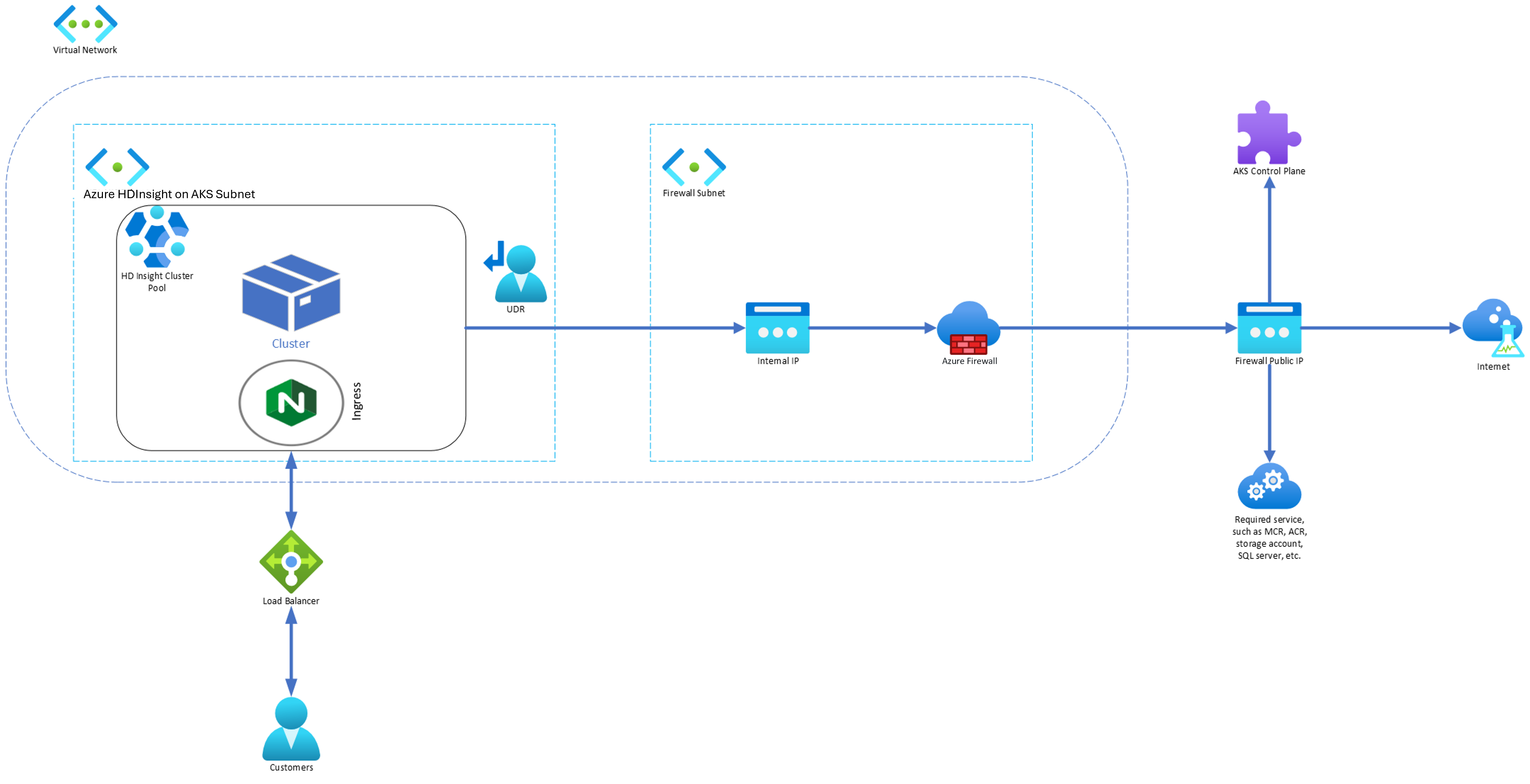
When an enterprise wants to use their own virtual network for the cluster deployments, securing the traffic of the virtual network becomes important. This article provides the steps to secure outbound traffic from your HDInsight on AKS cluster via Azure Firewall using Azure portal.
The following diagram illustrates the example used in this article to simulate an enterprise scenario:
Create a virtual network and subnets
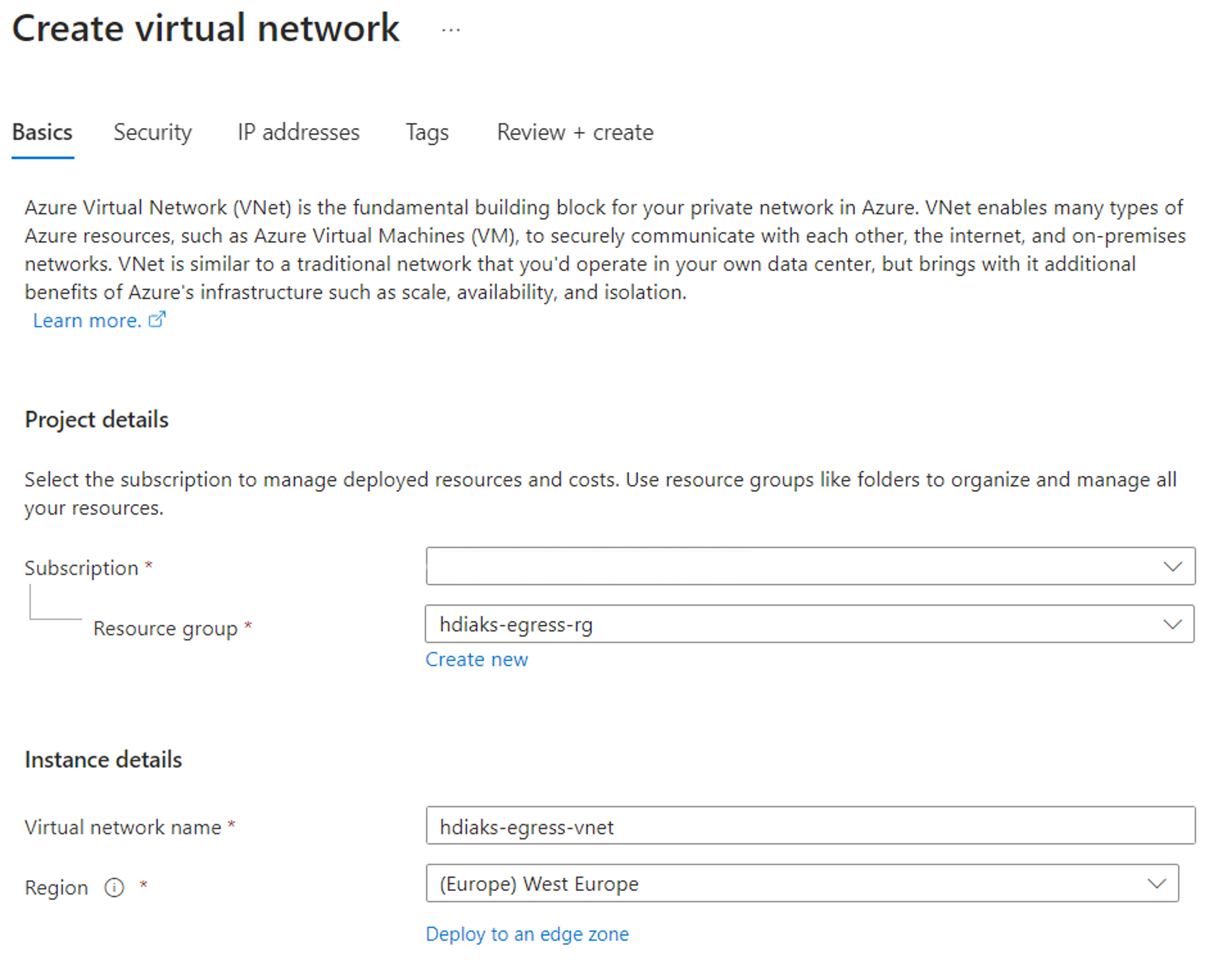
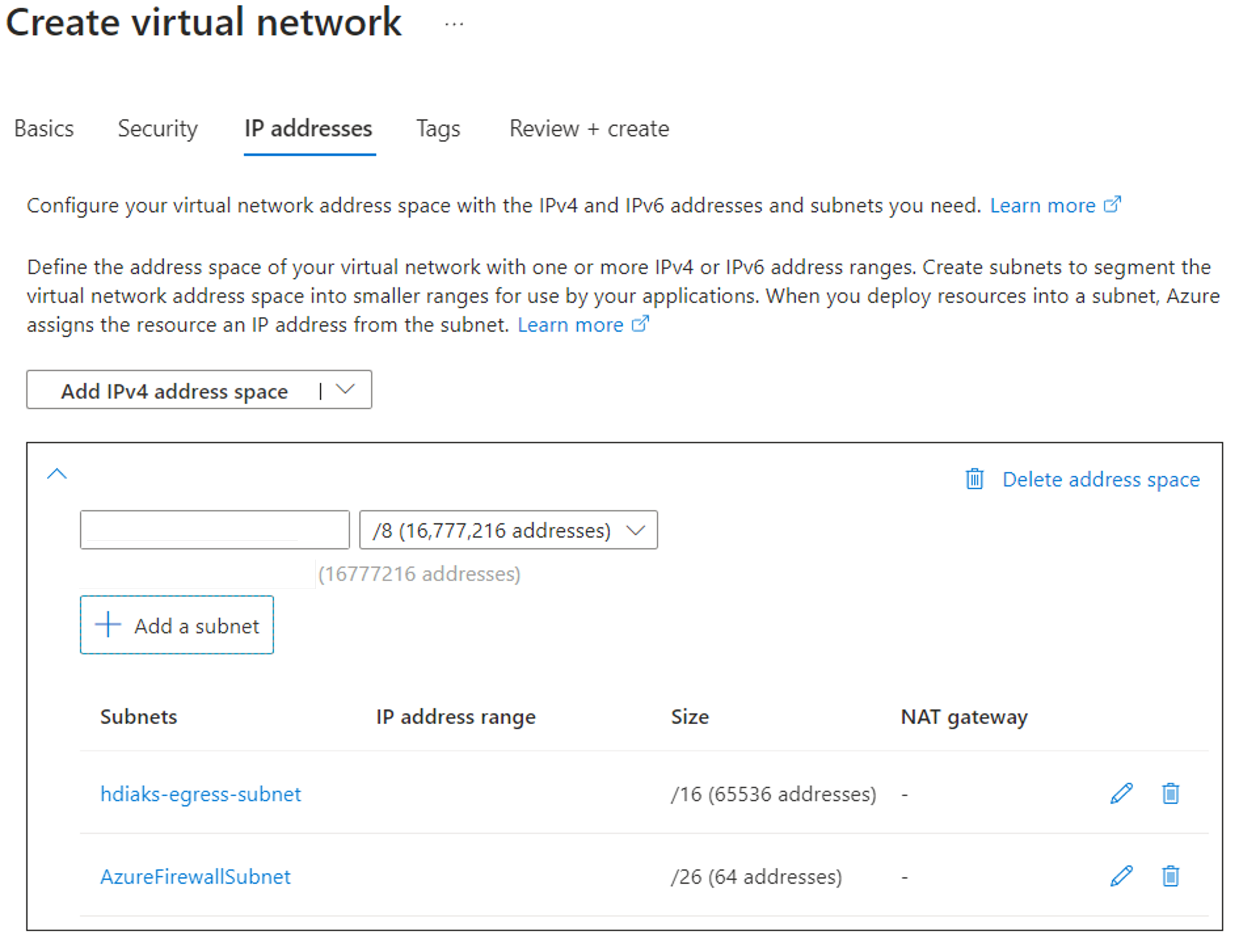
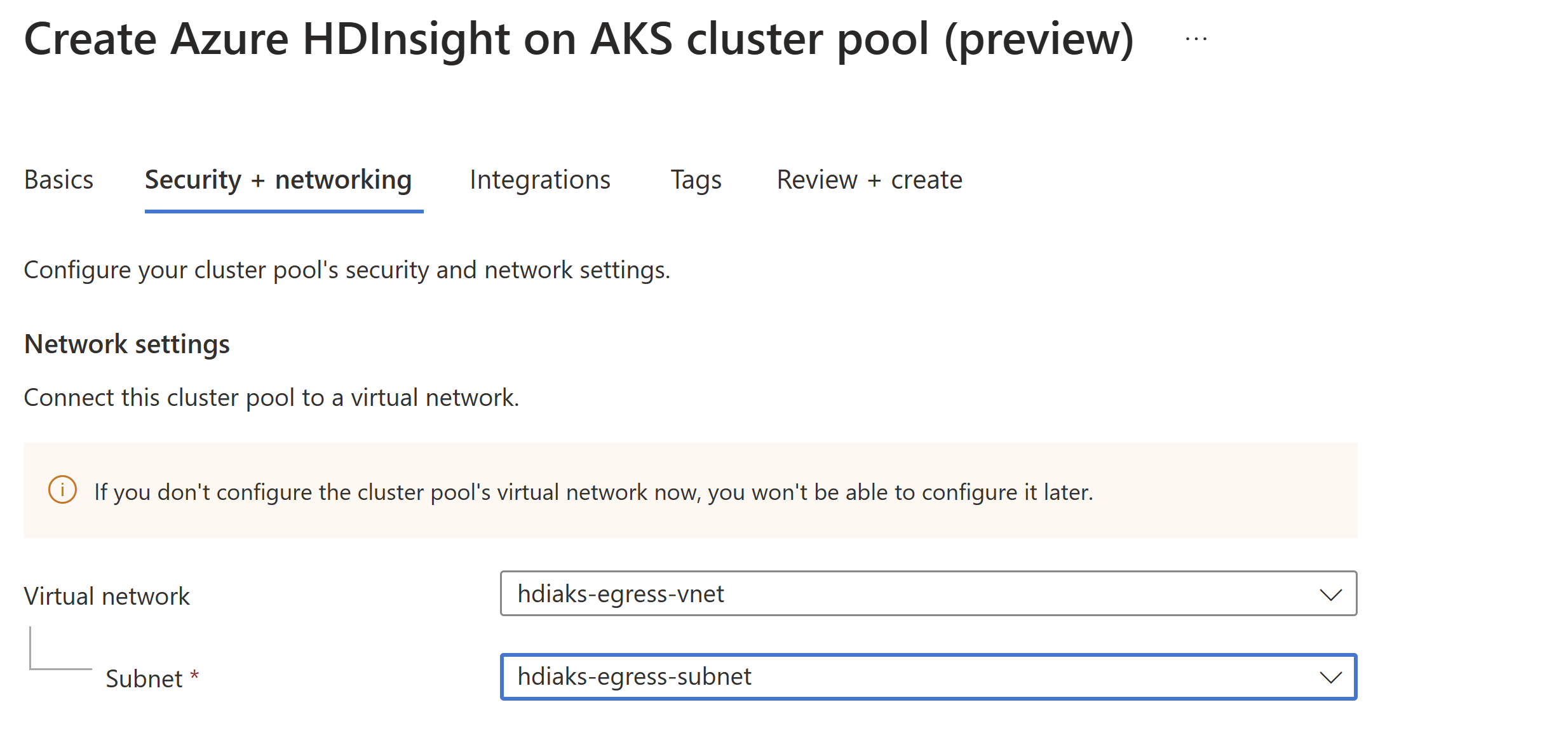
Create a virtual network and two subnets.
In this step, set up a virtual network and two subnets for configuring the egress specifically.
Important
- If you add NSG in subnet , you need to add certain outbound and inbound rules manually. Follow use NSG to restrict the traffic.
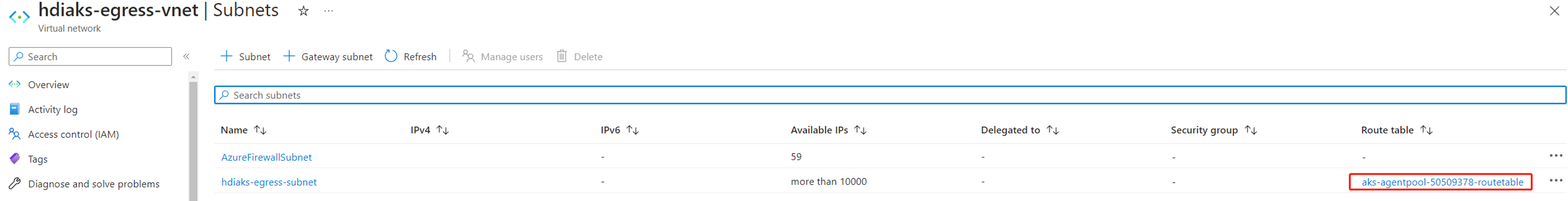
- Don't associate subnet
hdiaks-egress-subnetwith a route table because HDInsight on AKS creates cluster pool with default outbound type and can't create the cluster pool in a subnet already associated with a route table.
Create HDInsight on AKS cluster pool using Azure portal
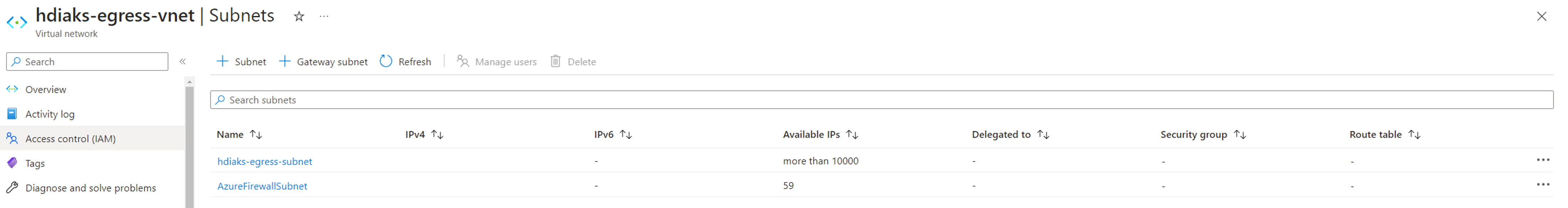
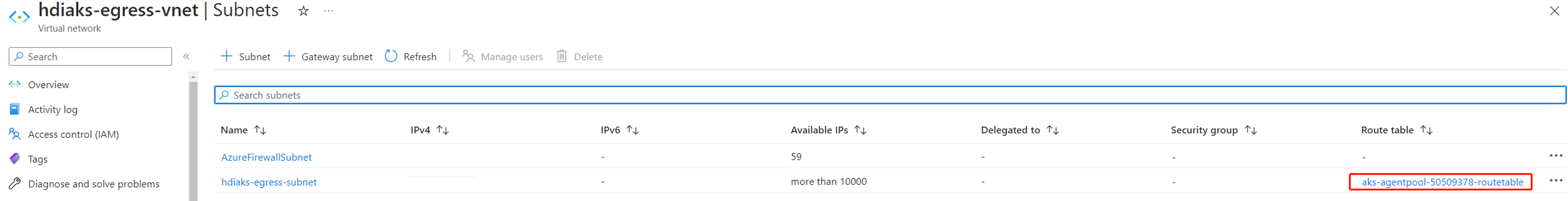
Create a cluster pool.
When HDInsight on AKS cluster pool is created, you can find a route table in subnet
hdiaks-egress-subnet.
Get AKS cluster details created behind the cluster pool
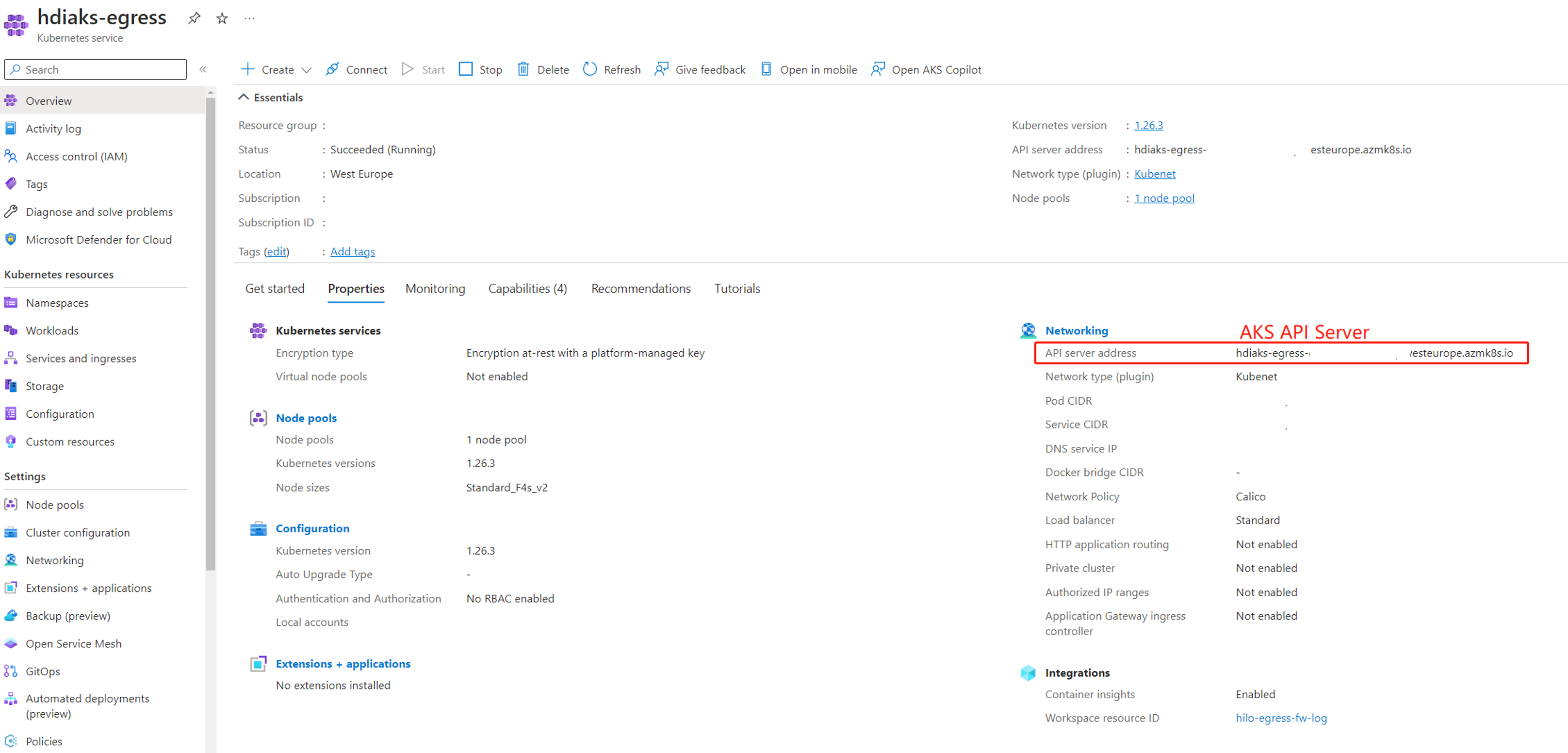
You can search your cluster pool name in portal, and go to AKS cluster. For example,
Get AKS API Server details.
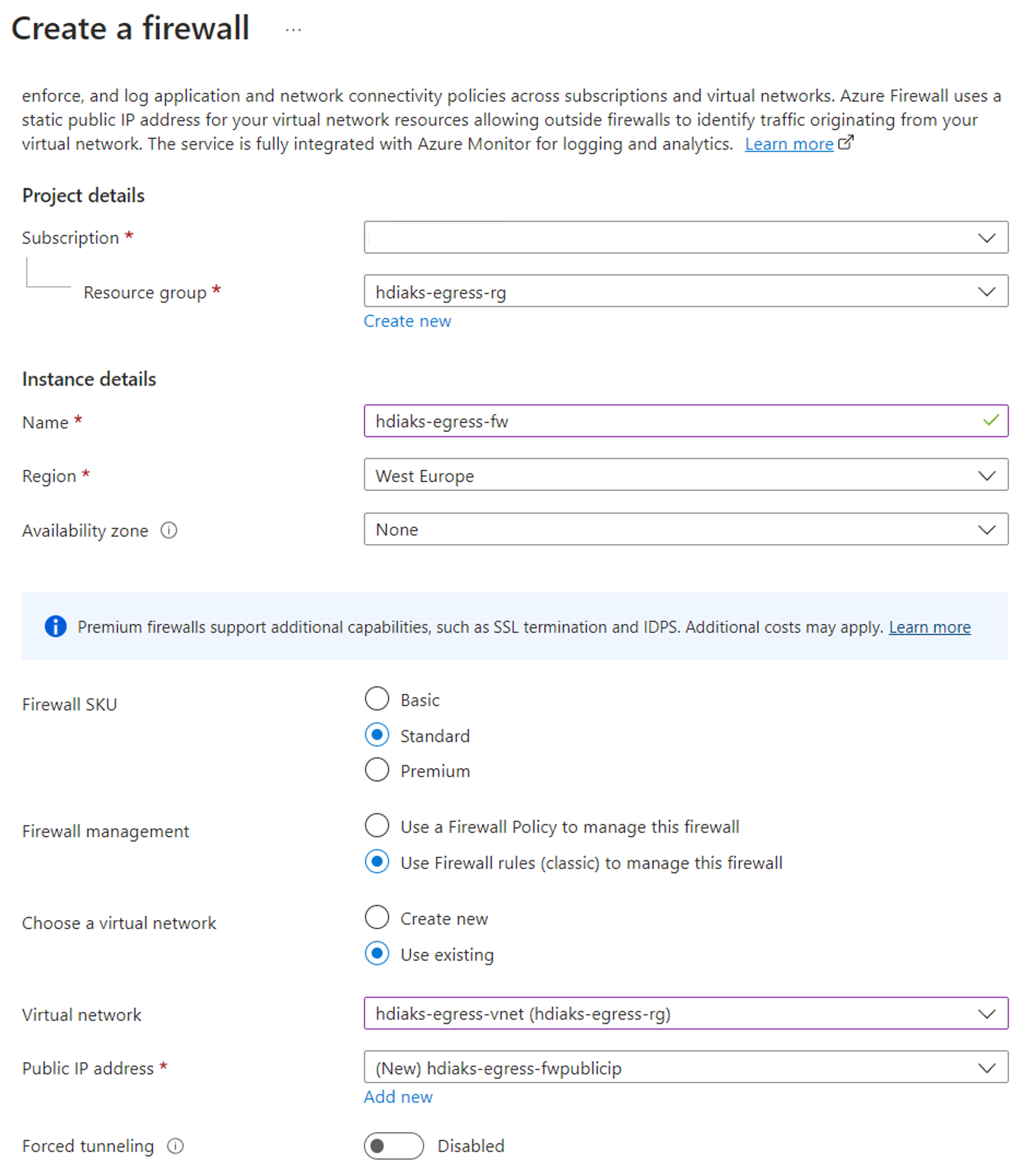
Create firewall
Create firewall using Azure portal.
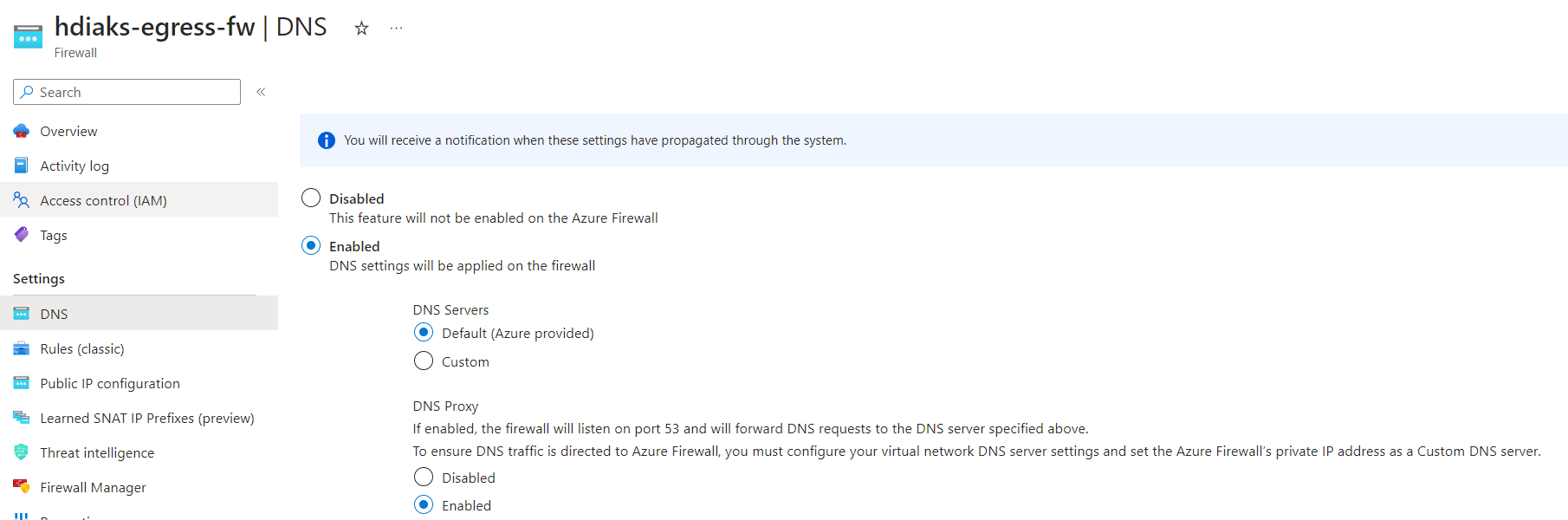
Enable DNS proxy server of firewall.
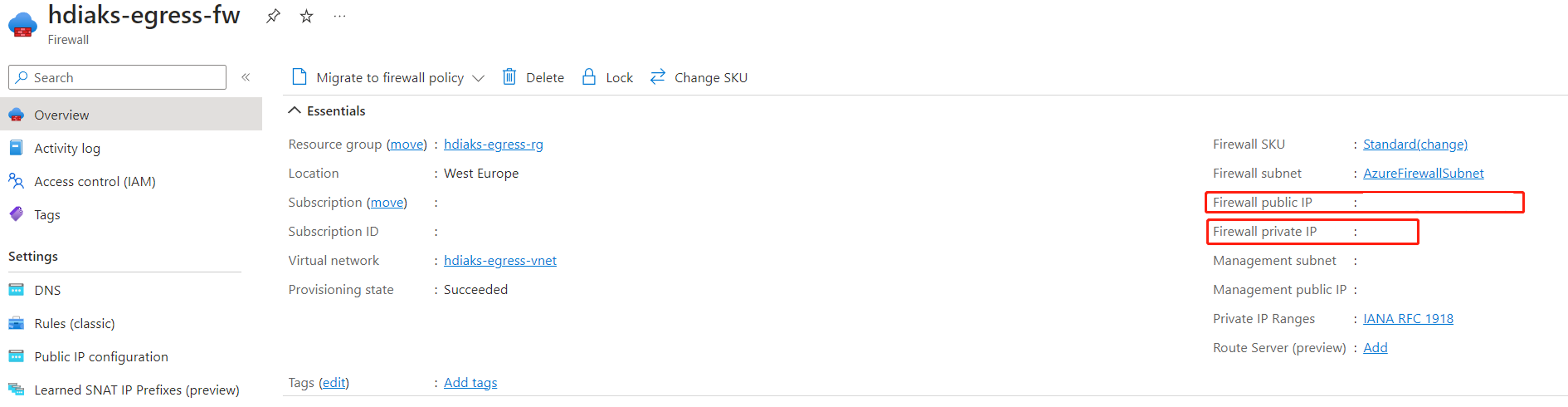
Once the firewall is created, find the firewall internal IP and public IP.
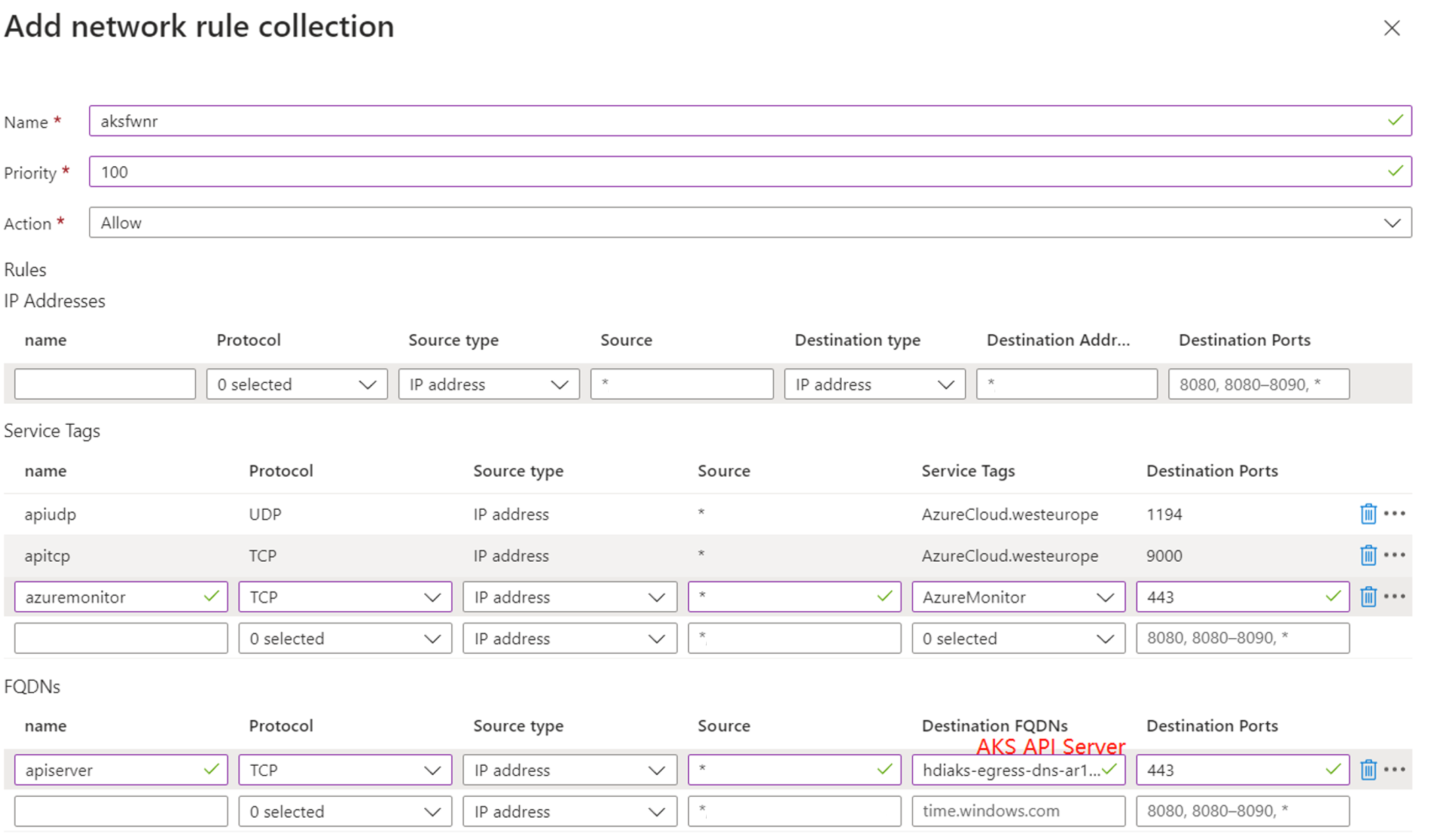
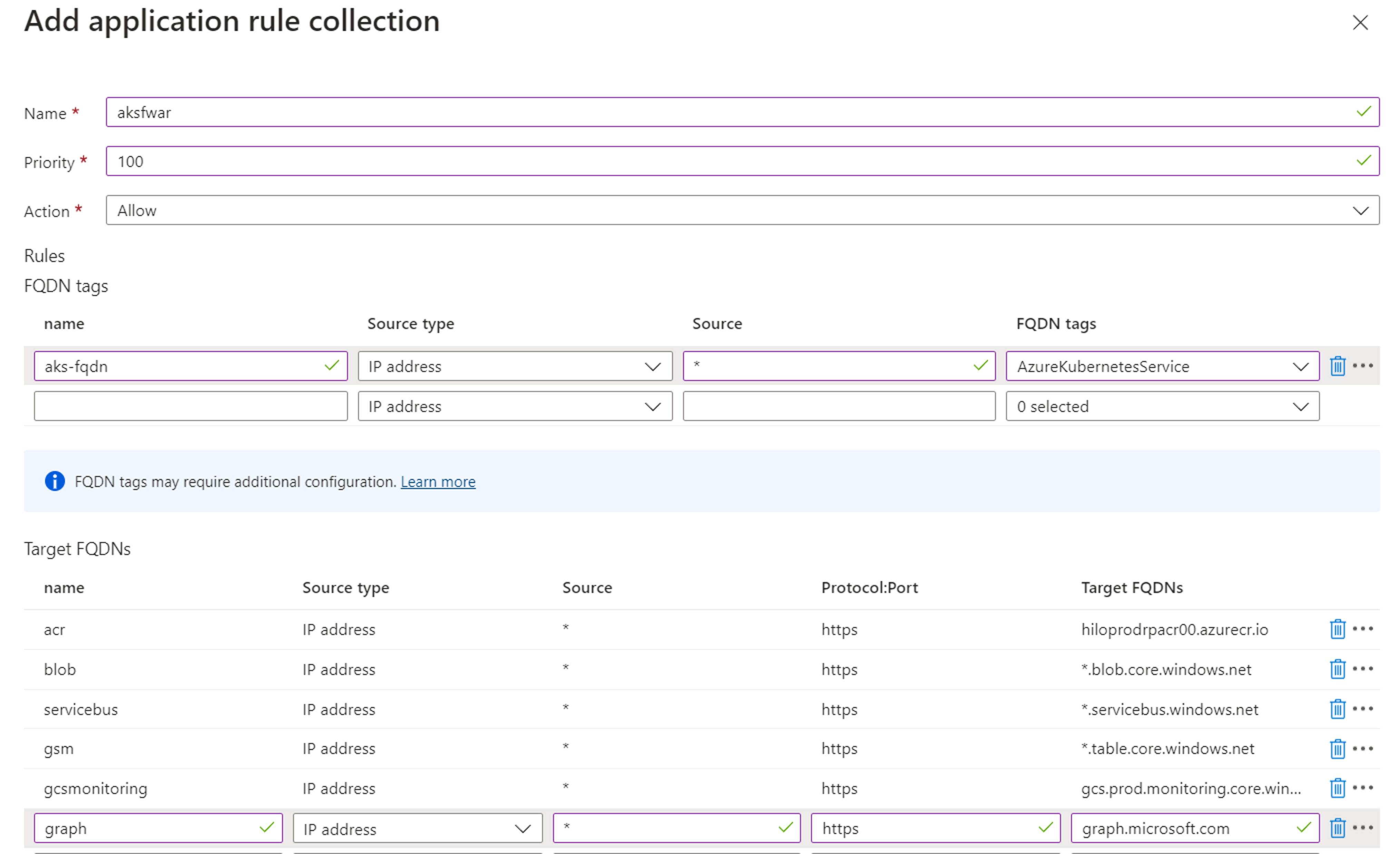
Add network and application rules to the firewall
Create the network rule collection with following rules.
Create the application rule collection with following rules.
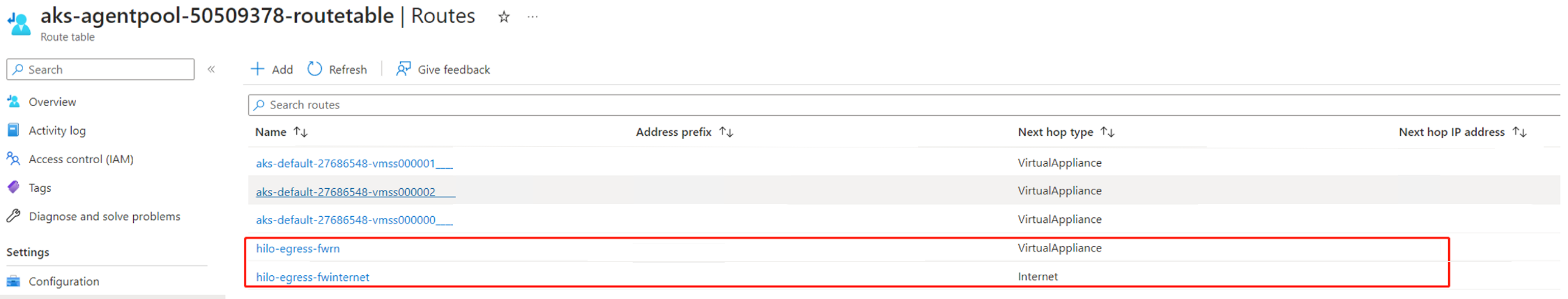
Create route in the route table to redirect the traffic to firewall
Add new routes to route table to redirect the traffic to the firewall.
Create cluster
In the previous steps, we have routed the traffic to firewall.
The following steps provide details about the specific network and application rules needed by each cluster type. You can refer to the cluster creation pages for creating Apache Flink, Trino, and Apache Spark clusters based on your need.
Important
Before creating the cluster, make sure to add the following cluster specific rules to allow the traffic.
Trino
Add the following rules to application rule collection
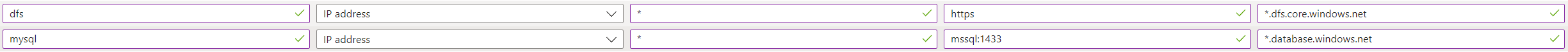
aksfwar.Add the following rule to network rule collection
aksfwnr.Note
Change the
Sql.<Region>to your region as per your requirement. For example:Sql.WestEurope
Apache Flink
Apache Spark
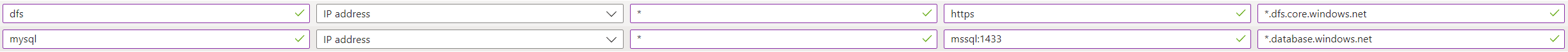
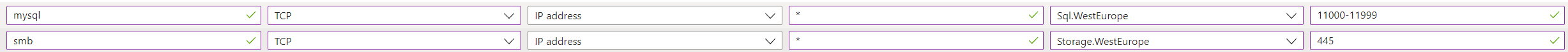
Add the following rules to application rule collection
aksfwar.Add the following rules to network rule collection
aksfwnr.Note
- Change the
Sql.<Region>to your region as per your requirement. For example:Sql.WestEurope - Change the
Storage.<Region>to your region as per your requirement. For example:Storage.WestEurope
- Change the
Solving symmetric routing issue
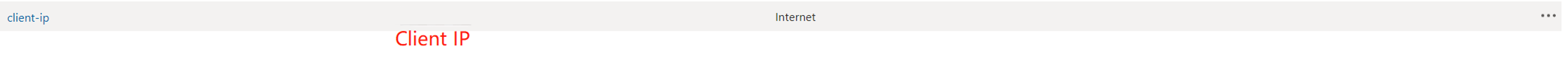
The following steps allow us to request cluster by cluster load balancer ingress service and ensure the network response traffic doesn't flow to firewall.
Add a route to the route table to redirect the response traffic to your client IP to Internet and then, you can reach the cluster directly.
If you can't reach the cluster and have configured NSG, follow use NSG to restrict the traffic to allow the traffic.
Tip
If you want to permit more traffic, you can configure it over the firewall.
How to Debug
If you find the cluster works unexpectedly, you can check the firewall logs to find which traffic is blocked.