Manually set an Azure Resource Manager workload identity service connection
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
Note
We are rolling out the new Azure service connection creation experience. Receiving it in your organization depends on various factors, and you may still see the older user experience.
When you troubleshoot an Azure Resource Manager workload identity service connection, you might need to manually configure the connection instead of using the automated tool that's available in Azure DevOps.
We recommend that you try the automated approach before you begin a manual configuration.
There are two options for authentication: use a managed identity or use an app registration. The advantage of the managed identity option is that you can use it if you don't have permissions to create service principals or if you're using a different Microsoft Entra tenant than your Azure DevOps user.
Set a workload identity service connection
To manually set up managed identity authentication for your Azure Pipelines, follow these steps to create a managed identity in the Azure portal, establish a service connection in Azure DevOps, add federated credentials, and grant the necessary permissions. You'll need to follow these steps in this order:
- Create the managed identity in Azure portal.
- Create the service connection in Azure DevOps and save as a draft.
- Add a federated credential to your managed identity in Azure portal.
- Grant permissions to the managed identity in Azure portal.
- Save your service connection in Azure DevOps.
You can also use the REST API for this process.
Prerequisites for managed identity authentication
- To create a user-assigned managed identity, your Azure account needs the Managed Identity Contributor or higher role assignment.
- To use a managed identity to access Azure resources in your pipeline, assign the managed identity access to the resource.
Create a managed identity in Azure portal
Sign in to the Azure portal.
In the search box, enter Managed Identities.
Select Create.
In the Create User Assigned Managed Identity pane, enter or select values for the following items:
- Subscription: Select the subscription in which to create the user-assigned managed identity.
- Resource group: Select a resource group to create the user-assigned managed identity in, or select Create new to create a new resource group.
- Region: Select a region to deploy the user-assigned managed identity (example: East US).
- Name: Enter the name for your user-assigned managed identity (example: UADEVOPS).
Select Review + create to create a new managed identity. When your deployment is complete, select Go to resource.
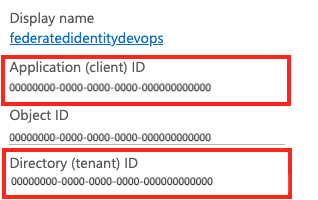
Copy the Subscription, Subscription ID, and Client ID values for your managed identity to use later.
Within your managed identity in Azure portal, go to Settings > Properties.
Copy the Tenant Id value to use later.
Create a service connection for managed identity authentication in Azure DevOps
In Azure DevOps, open your project and go to
 > Pipelines > Service connections.
> Pipelines > Service connections.Select New service connection.
Select Azure Resource Manager.
Select identity type App registration or Managed identity (manual) the Workload identity federation credential.
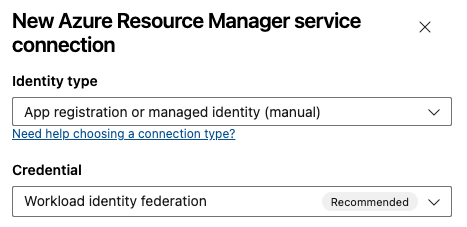
For Service connection name, enter a value such as
uamanagedidentity. You'll use this value in your federated credential subject identifier.Select Next.
In Step 2: App registration details:
Step 2: App registration details contains the following parameters. You can enter or select the following parameters:
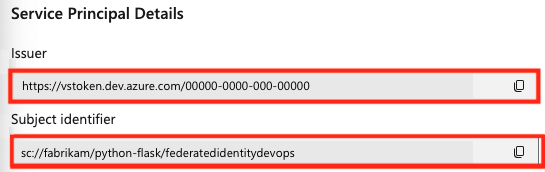
Parameter Description Issuer Required. DevOps automatically creates the issuer URL. Subject identifier Required. DevOps automatically creates the subject identifier. Environment Required. Choose a cloud environment to connect to. If you select Azure Stack, enter the environment URL, which is something like https://management.local.azurestack.external.Select the Scope Level. Select Subscription, Management Group, or Machine Learning Workspace. Management groups are containers that help you manage access, policy, and compliance across multiple subscriptions. A Machine Learning Workspace is place to create machine learning artifacts.
For the Subscription scope, enter the following parameters:
Parameter Description Subscription Id Required. Enter the Azure subscription ID. Subscription Name Required. Enter the Azure subscription name. For the Management Group scope, enter the following parameters:
Parameter Description Management Group Id Required. Enter the Azure management group ID. Management Group Name Required. Enter the Azure management group name. For the Machine Learning Workspace scope, enter the following parameters:
Parameter Description Subscription Id Required. Enter the Azure subscription ID. Subscription Name Required. Enter the Azure subscription name. Resource Group Required. Select the resource group containing the workspace. ML Workspace Name Required. Enter the name of the existing Azure Machine Learning workspace. ML Workspace Location Required. Enter the location of the existing Azure Machine Learning workspace.
In the Authentication section, enter or select the following parameters:
Parameter Description Application (client) ID Required. Enter the Client ID for your managed identity. Directory (tenant) ID Required. Enter the Tenant ID from your managed identity. In the Security section, select Grant access permission to all pipelines to allow all pipelines to use this service connection. If you don't select this option, you must manually grant access to each pipeline that uses this service connection.
In Azure DevOps, copy the generated values for Issuer and Subject identifier.
Select Keep as draft to save a draft credential. You can't complete setup until your managed identity has a federated credential in Azure portal.
Add a federated credential in Azure portal
In a new browser window, within your managed identity in Azure portal, go to Settings > Federated credentials.
Select Add credentials.
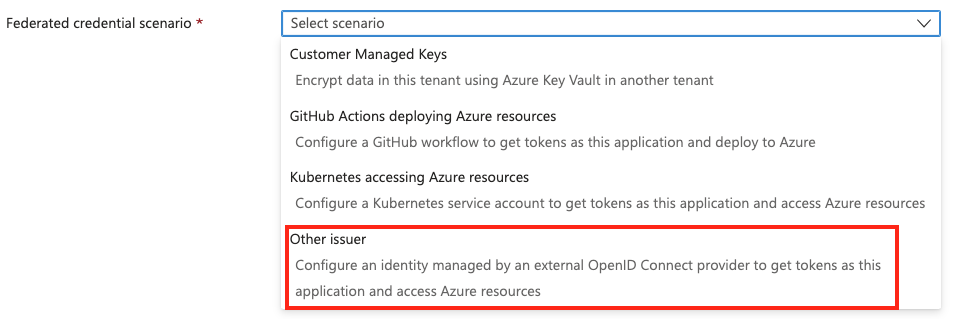
Select the Other issuer scenario.
Paste the values for Issuer and Subject identifier that you copied from your Azure DevOps project into your federated credentials in the Azure portal.
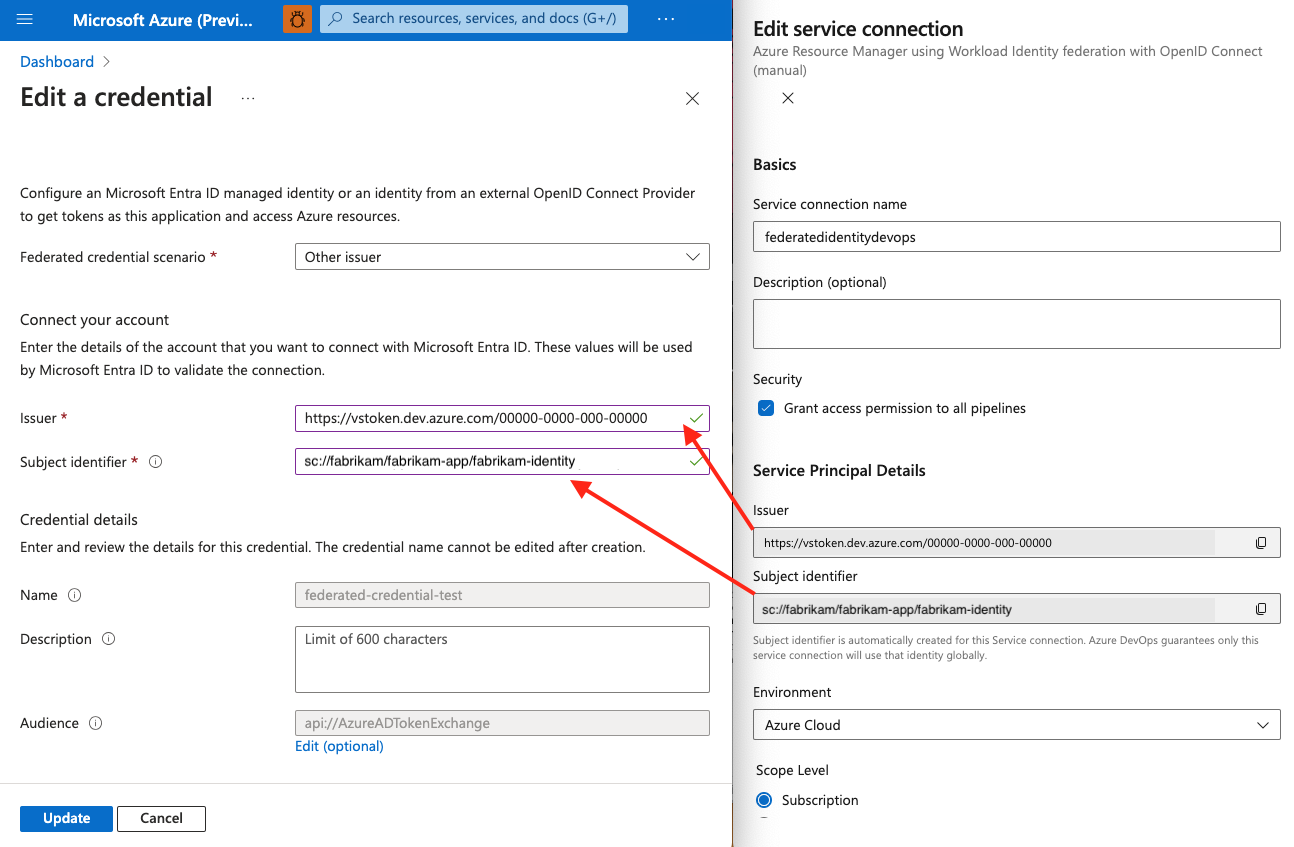
Enter the Name of your federated credential.
Select Add.
Grant permissions to the managed identity in Azure portal
In Azure portal, go to the Azure resource that you want to grant permissions for (for example, a resource group).
Select Access control (IAM).
Select Add role assignment. Assign the required role to your managed identity (for example, Contributor).
Select Review and assign.
Save your Azure DevOps service connection
In Azure DevOps, return to your draft service connection.
Select Finish setup.
Select Verify and save. Once this step successfully completes, your managed identity is fully configured.