View and remediate vulnerabilities for registry images (secure score)
Note
This page describes the classic secure score approach to vulnerability management in Defender for Cloud. Customers using Defender CSPM should use the new risk-based approach: View and remediate vulnerabilities for images running on your Kubernetes clusters (Risk based).
Defender for Cloud gives its customers the ability to remediate vulnerabilities in container images while still stored in the registry by using the Container registry images should have vulnerability findings resolved (powered by MDVM) recommendation.
Within the recommendation, resources are grouped into tabs:
- Healthy resources – relevant resources, which either aren't impacted or on which you've already remediated the issue.
- Unhealthy resources – resources that are still impacted by the identified issue.
- Not applicable resources – resources for which the recommendation can't give a definitive answer. The not applicable tab also includes reasons for each resource.
View vulnerabilities on a specific container registry
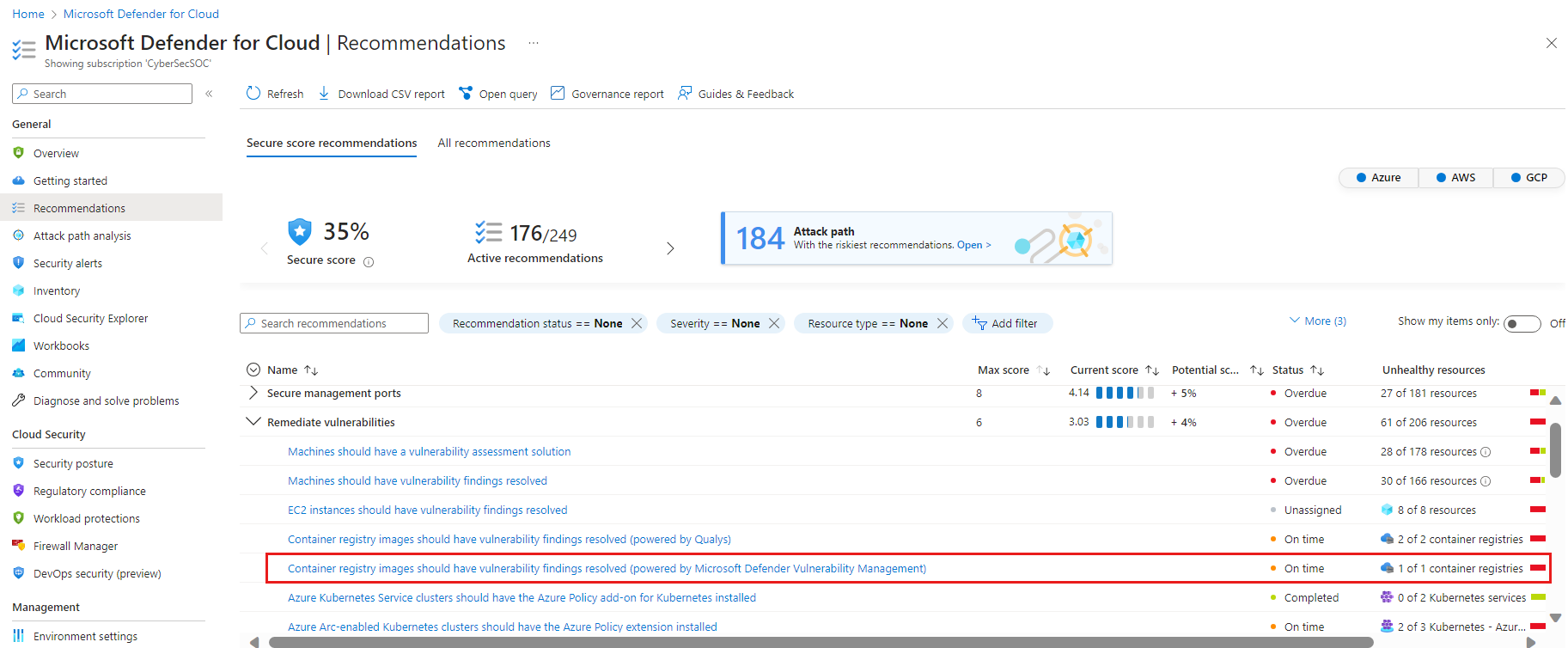
Open the Recommendations page. If you are on the new risk-based page, select Switch to classic view in the menu item on the top of the page. Use the > arrow to open the sublevels. If issues were found, you'll see the recommendation Container registry images should have vulnerability findings resolved (powered by MDVM). Select the recommendation.
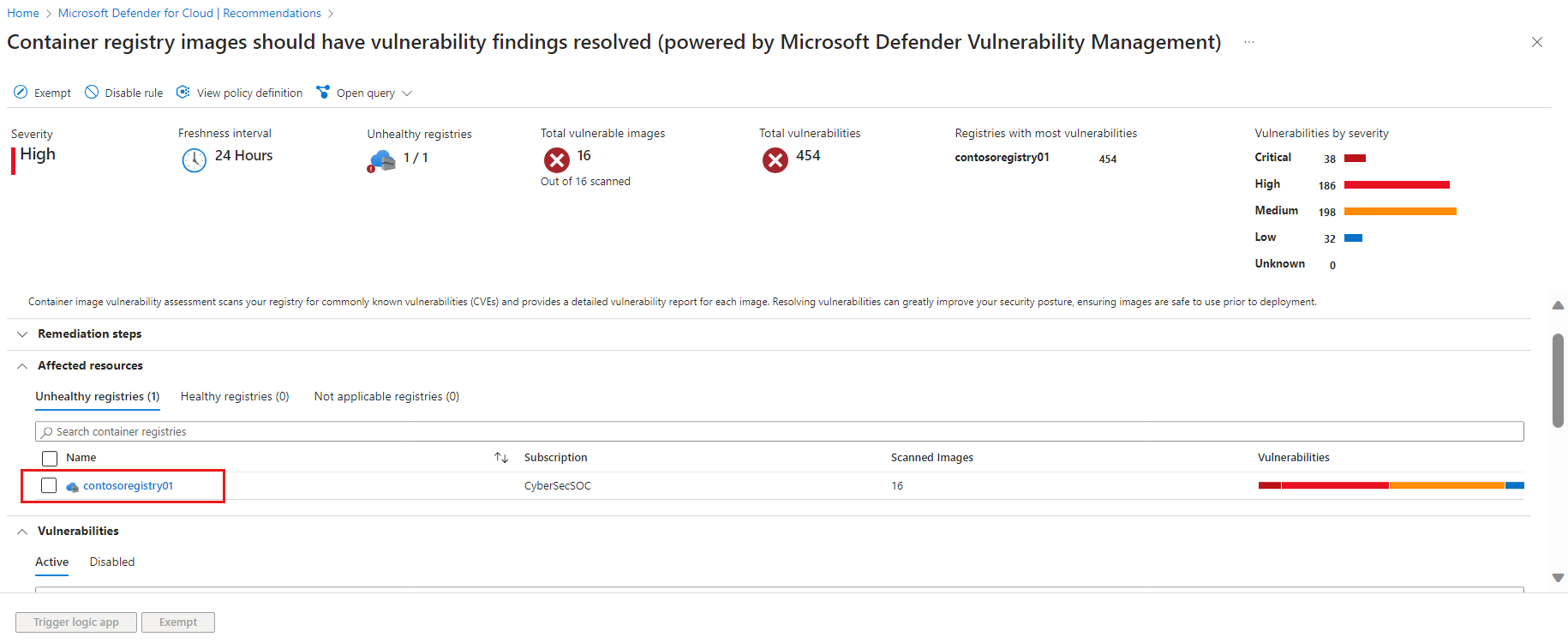
The recommendation details page opens with additional information. This information includes the list of registries with vulnerable images ("affected resources") and the remediation steps. Select the affected registry.
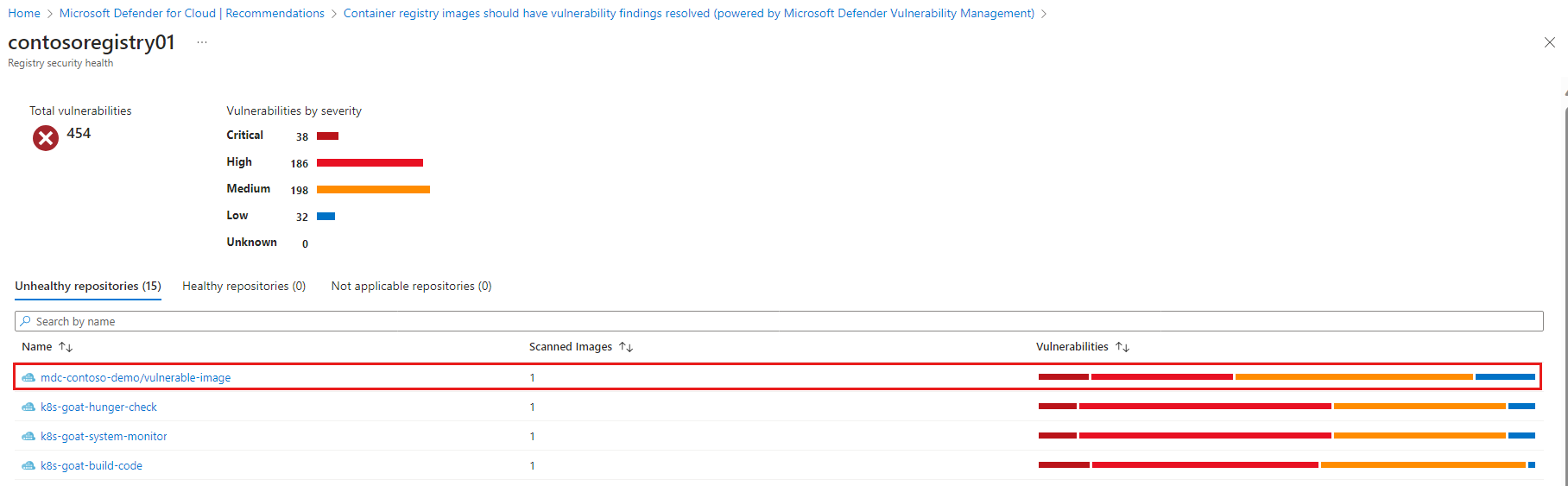
This opens the registry details with a list of repositories in it that have vulnerable images. Select the affected repository to see the images in it that are vulnerable.
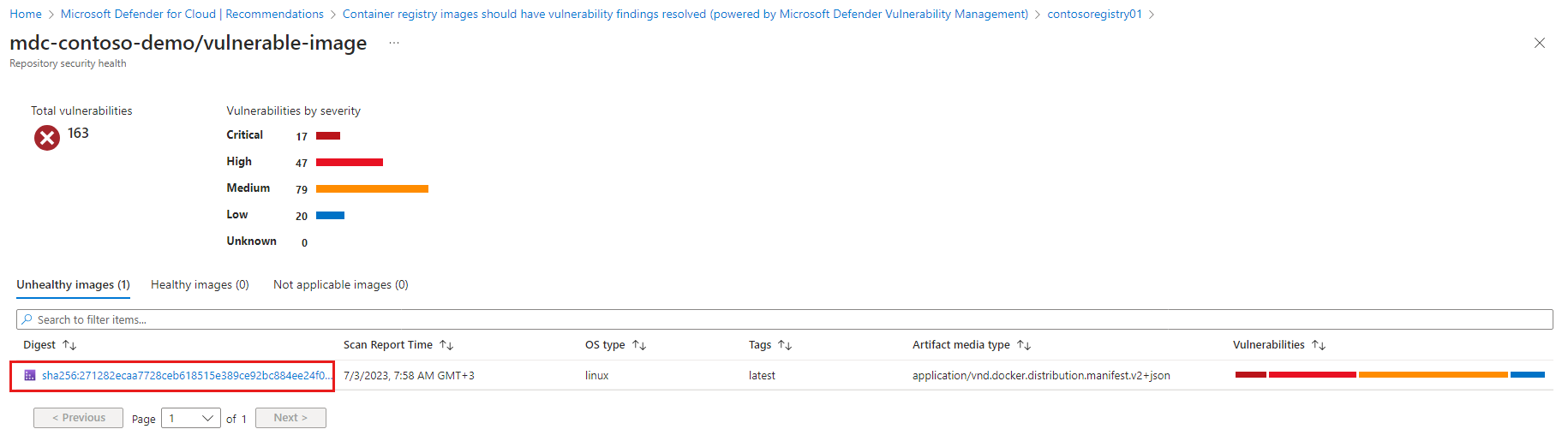
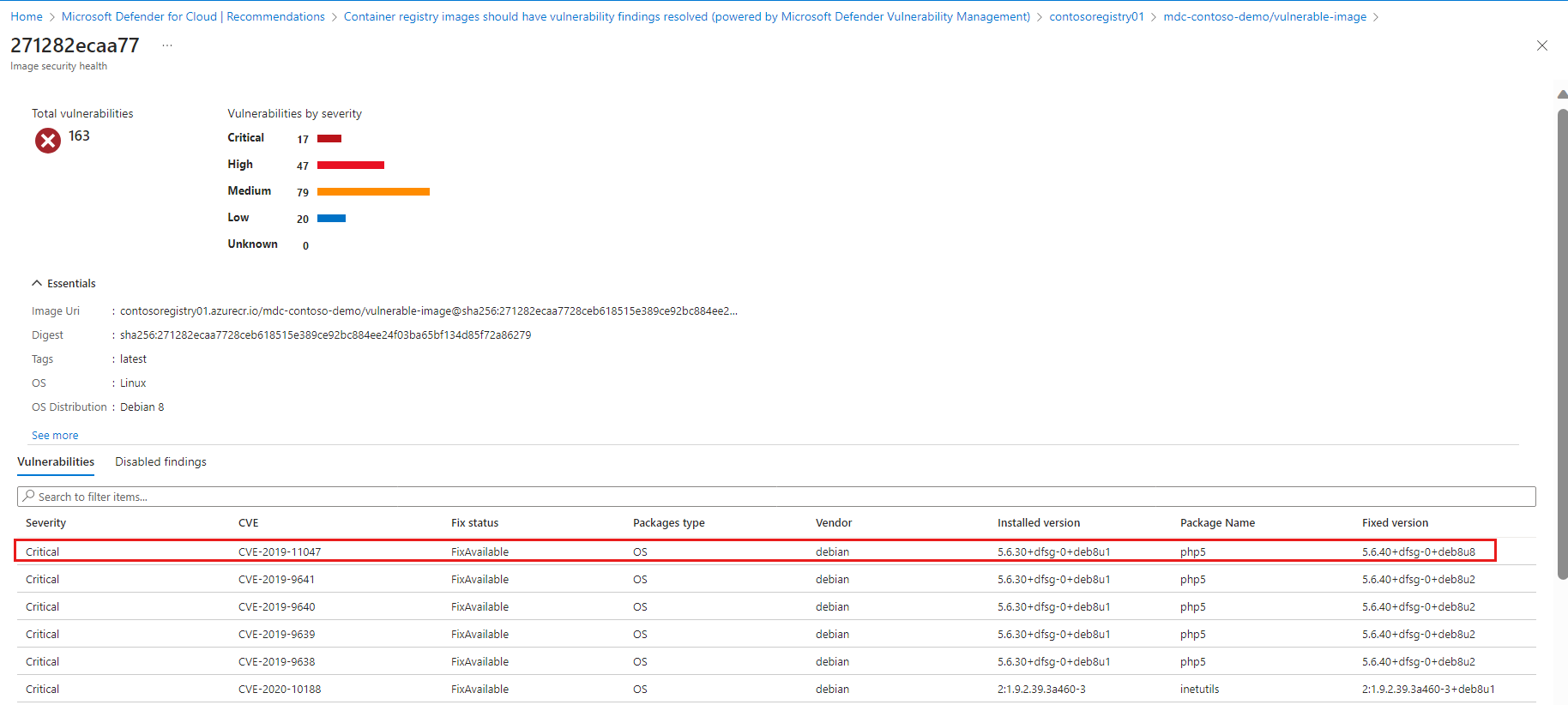
The repository details page opens. It lists all vulnerable images on that repository with distribution of the severity of vulnerabilities per image. Select the unhealthy image to see the vulnerabilities.
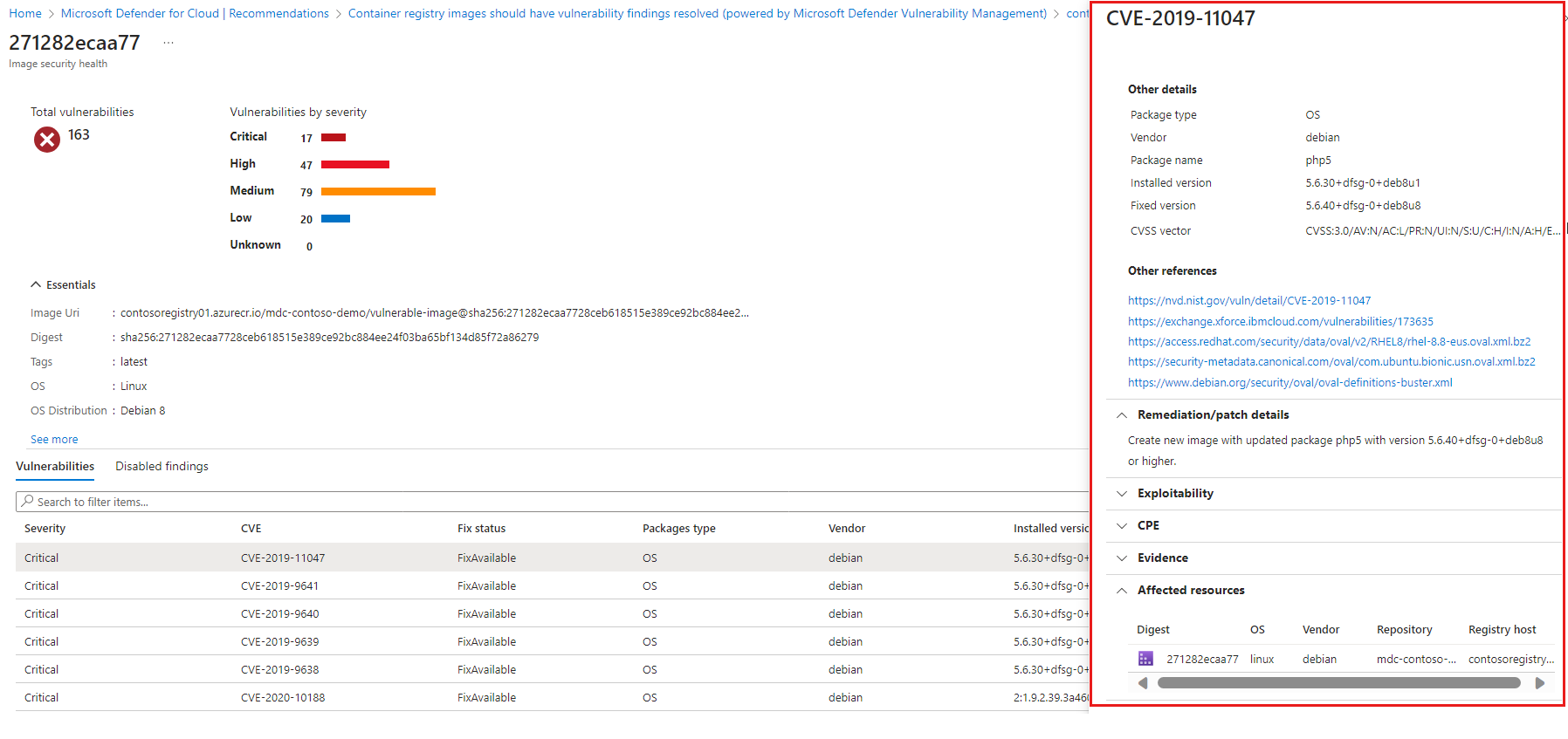
The list of vulnerabilities for the selected image opens. To learn more about a finding, select the finding.
The vulnerabilities details pane opens. This pane includes a detailed description of the issue and links to external resources to help mitigate the threats, affected resources, and information on the software version that contributes to resolving the vulnerability.
View images affected by a specific vulnerability
Open the Recommendations page. If issues were found, you'll see the recommendation Container registry images should have vulnerability findings resolved (powered by MDVM). Select the recommendation.
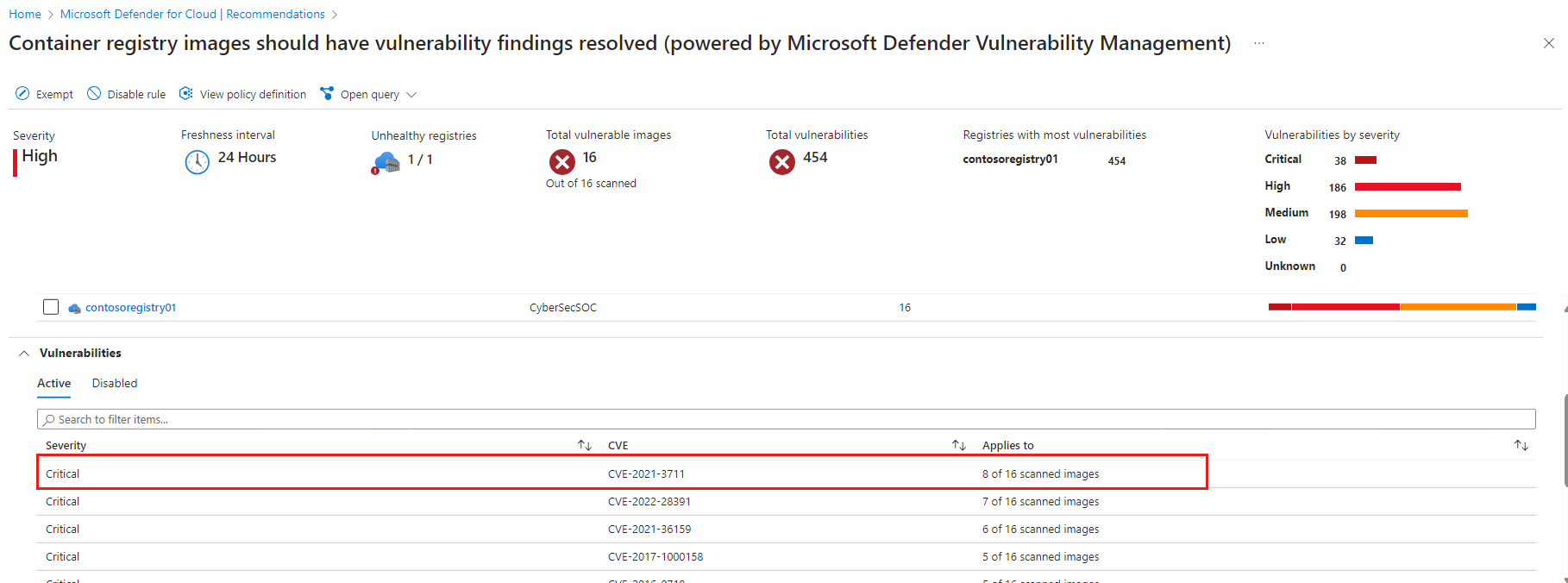
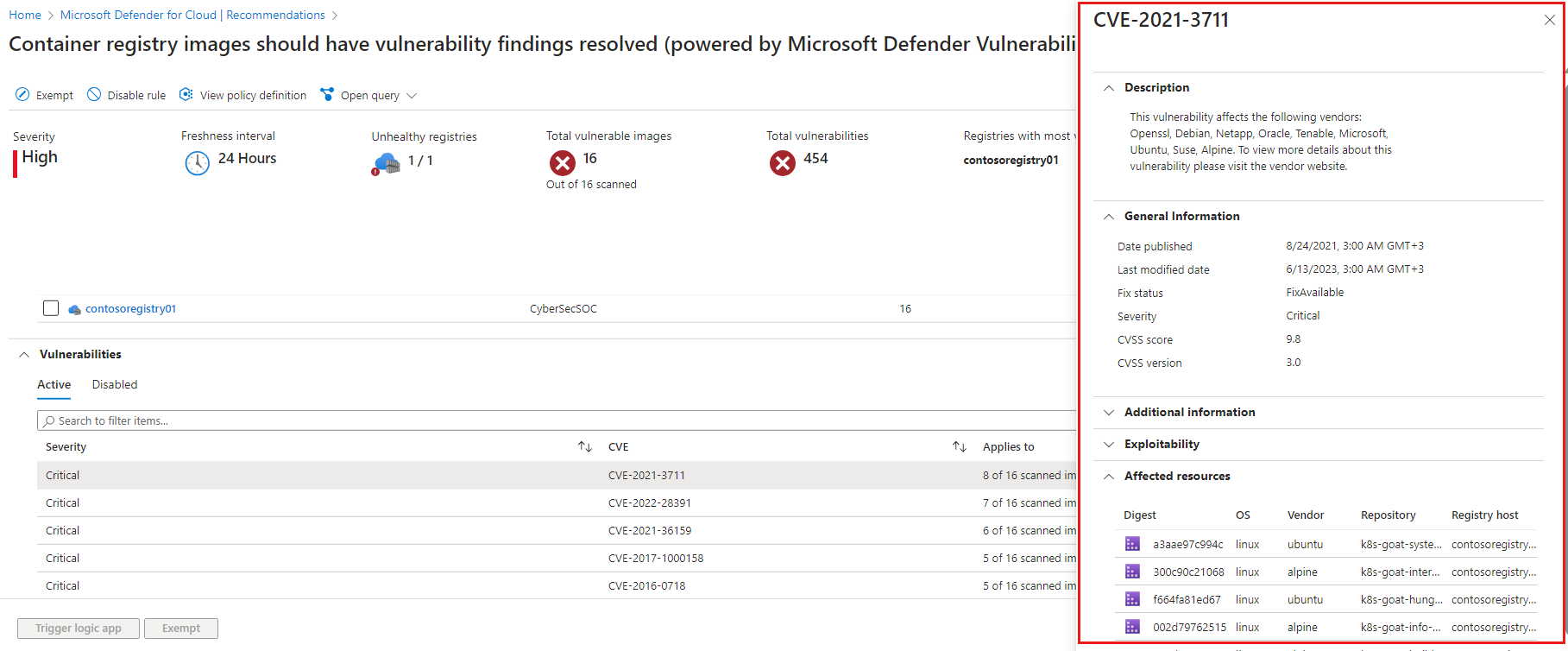
The recommendation details page opens with additional information. This information includes the list of vulnerabilities impacting the images. Select the specific vulnerability.
The vulnerability finding details pane opens. This pane includes a detailed description of the vulnerability, images affected by that vulnerability, and links to external resources to help mitigate the threats, affected resources, and information on the software version that contributes to resolving the vulnerability.
Remediate vulnerabilities
Use these steps to remediate each of the affected images found either in a specific cluster or for a specific vulnerability:
Follow the steps in the remediation section of the recommendation pane.
When you've completed the steps required to remediate the security issue, replace each affected image in your registry or replace each affected image for a specific vulnerability:
- Build a new image (including updates for each of the packages) that resolves the vulnerability according to the remediation details.
- Push the updated image to trigger a scan and delete the old image. It might take up to 24 hours for the previous image to be removed from the results, and for the new image to be included in the results.
Check the recommendations page for the recommendation Container registry images should have vulnerability findings resolved (powered by MDVM). If the recommendation still appears and the image you've handled still appears in the list of vulnerable images, check the remediation steps again.
Next steps
- Learn how to view and remediate vulnerabilities for images running on Kubernetes clusters.
- Learn more about the Defender for Cloud Defender plans.