Kubernetes node vulnerability assessment
Defender for Cloud can scan the VMs that host Kubernetes nodes to assess vulnerabilities to the OS and installed software. Recommendations for remediation are generated for the customer security team to review and remediate as part of the shared responsibility to maintain the Kubernetes nodes of a cluster.
Prerequisite
Vulnerability assessment of the nodes must be enabled by turning on the Agentless scanning for machines option in the Defender for Containers, Defender Cloud Security Posture Management, or Defender for Servers P2 plan.
Review the Kubernetes node vulnerability recommendations
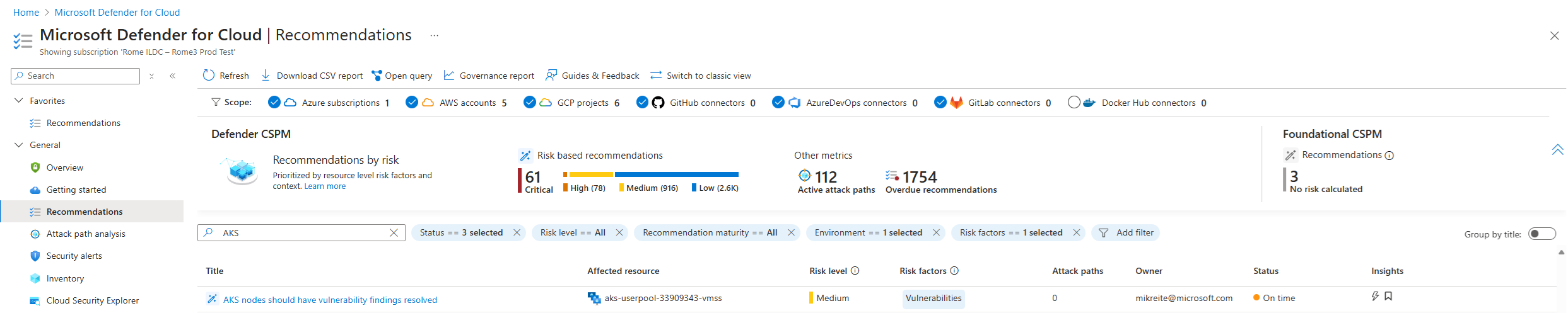
If vulnerabilities are found for a Kubernetes node, a recommendation is generated for the customer to review. To review Kubernetes node recommendations for remediation in the Azure portal:
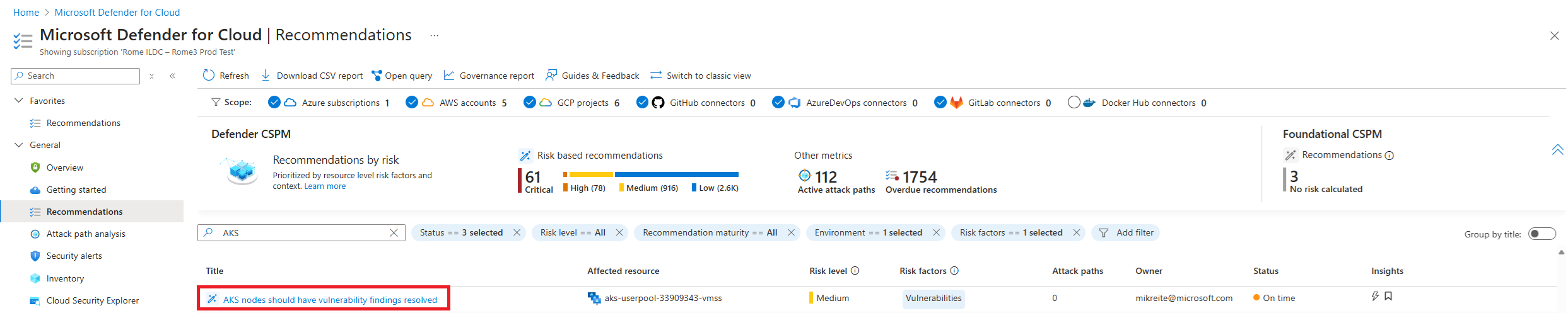
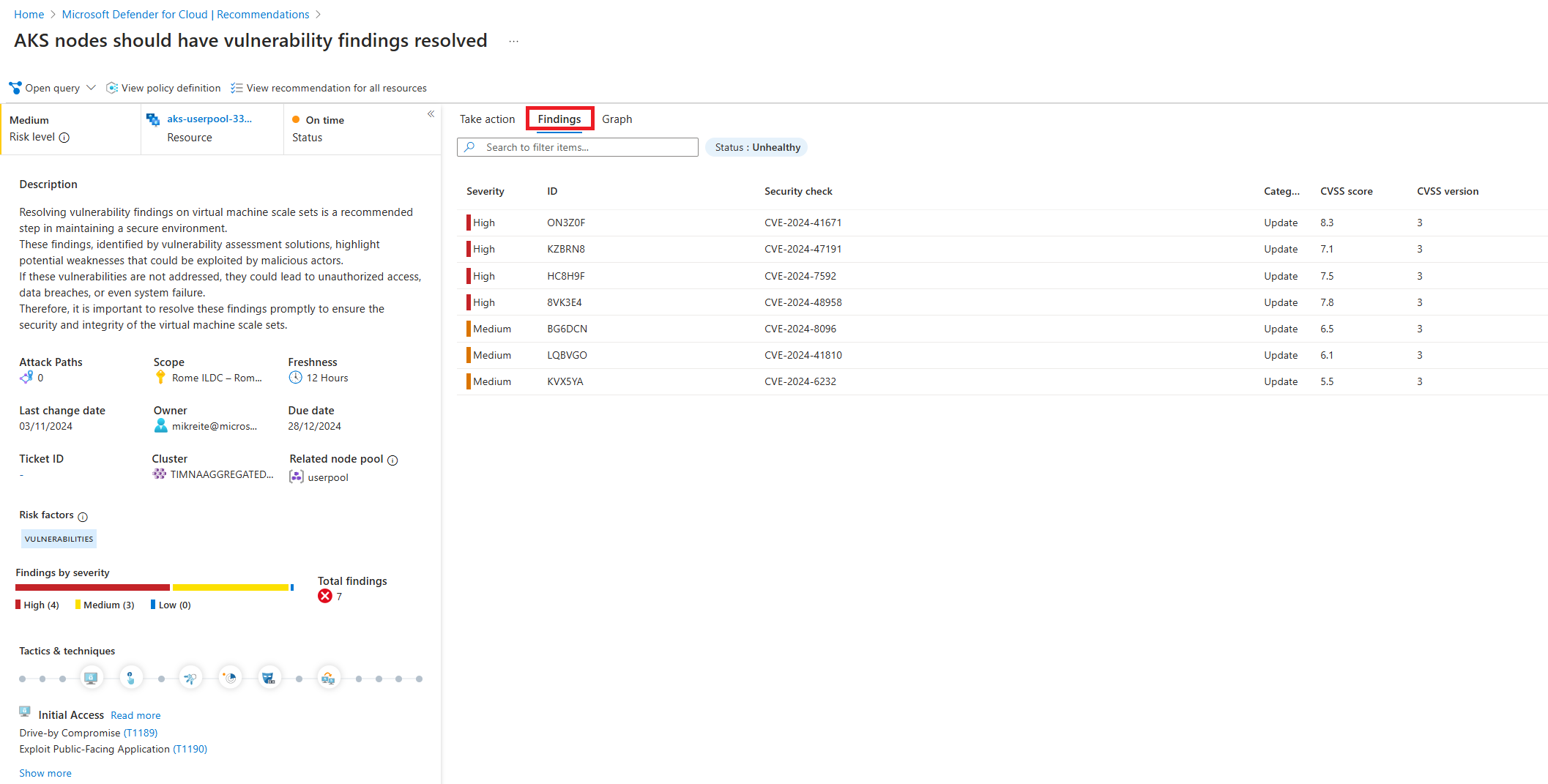
Select the AKS nodes should have vulnerability findings resolved recommendation.
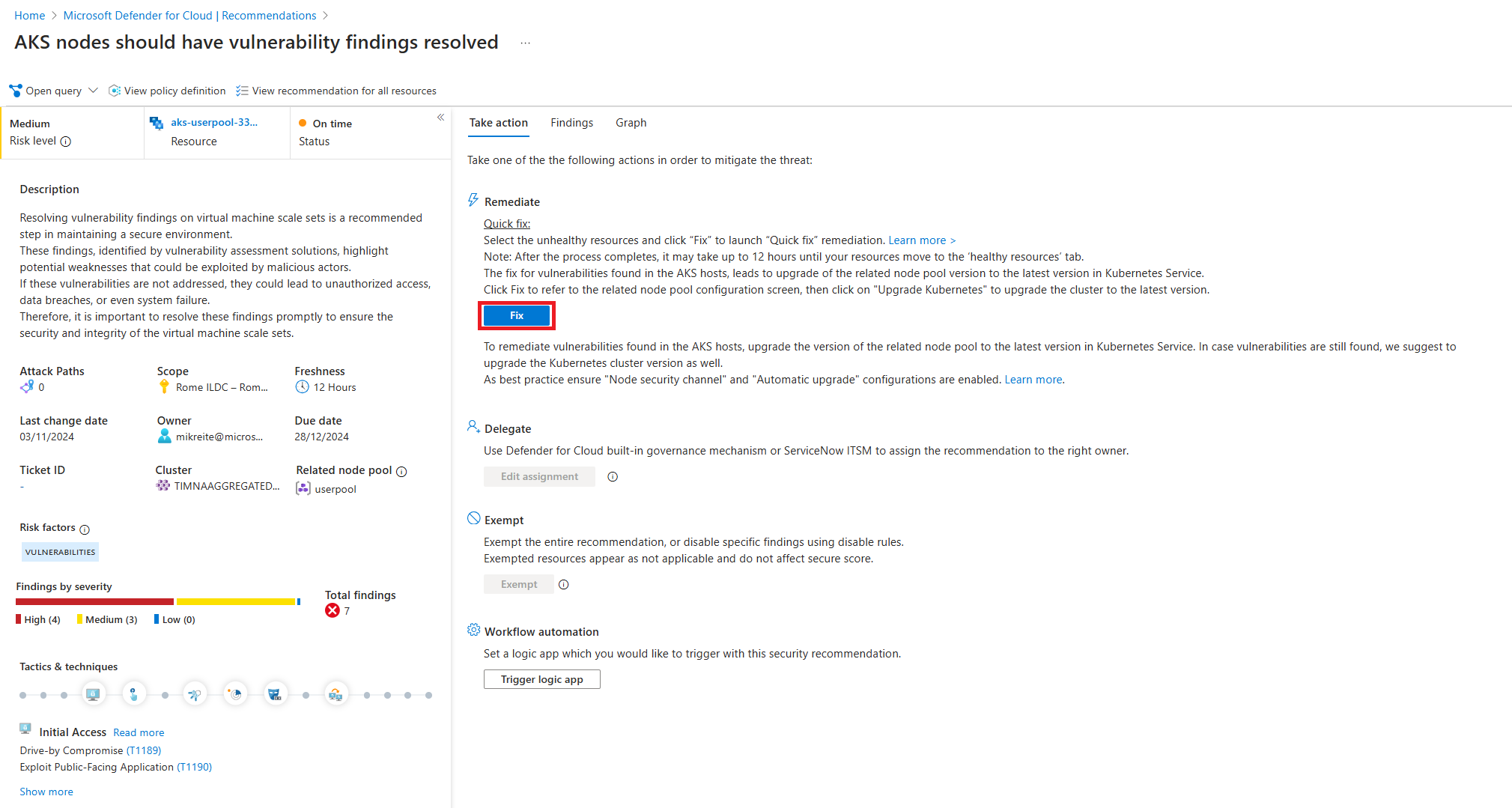
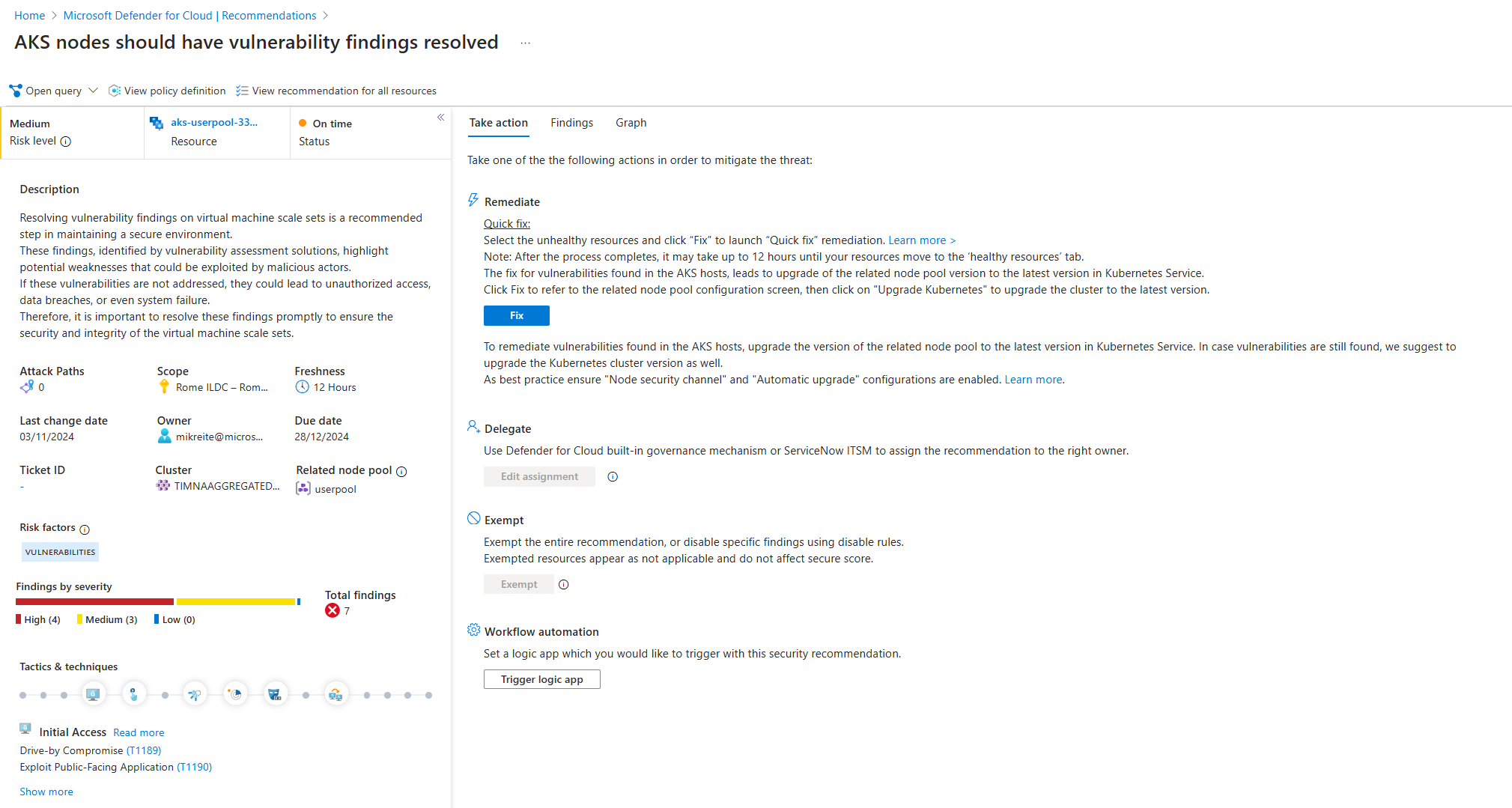
The full details of the Kubernetes node recommendation are shown. Along with a full description of the vulnerability, other details such as the name of the affected Kubernetes node pool and its cluster are presented.
Select the Findings tab to view a list of CVEs relating to the Kubernetes node.
Selecting one of the CVE lines opens a pane giving full details about the CVE and all the Kubernetes node resources that also have this vulnerability.
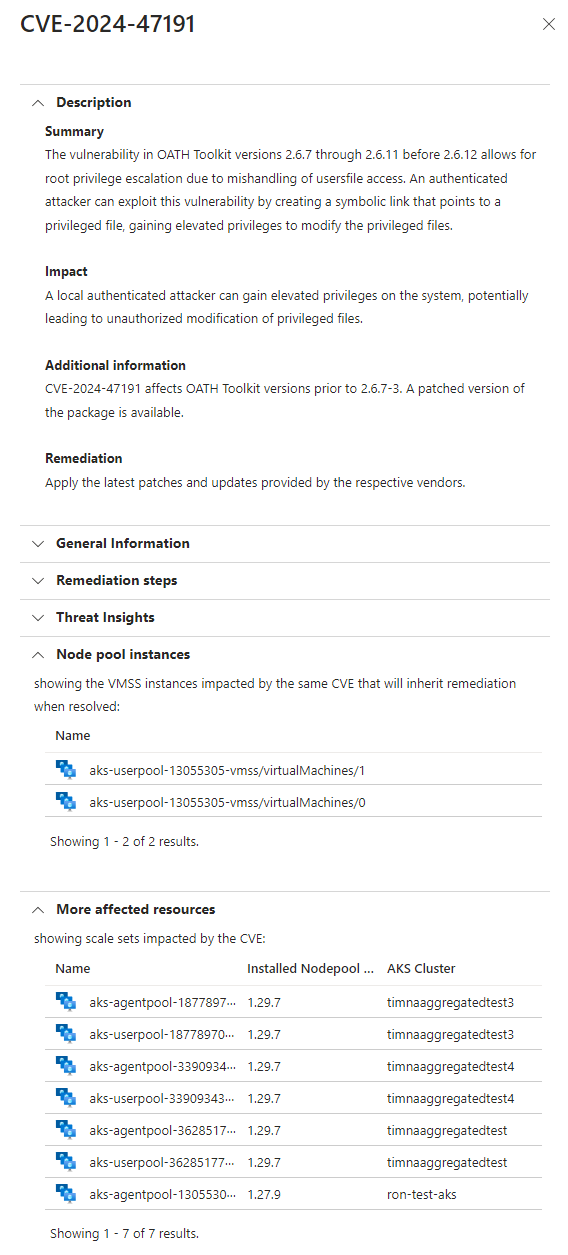
In the details pane, the Node pool instances section shows the nodes to be affected by the remediation. The More affected resources shows other nodes that have the same CVE and should be remediated as well.
Remediate Kubernetes node vulnerabilities
Kubernetes node vulnerabilities are remediated by updating the node pool VM image version. The customer upgrades the node pool, as part of the shared responsibility between the Kubernetes service and the customer. The customer upgrades the node pool in one of two ways - either upgrade the node pool VM image and/or the cluster's Kubernetes service, to a newer version. It is recommended to upgrade the node pool VM image first. In some cases, the customer needs to upgrade the cluster's Kubernetes service version and the node pool VM image version to remediate the vulnerability.
Important
The cluster's Kubernetes version and the node pool VM image can be set to auto-upgrade. These versions should be regularly upgraded to provide maximum security for you AKS resources.
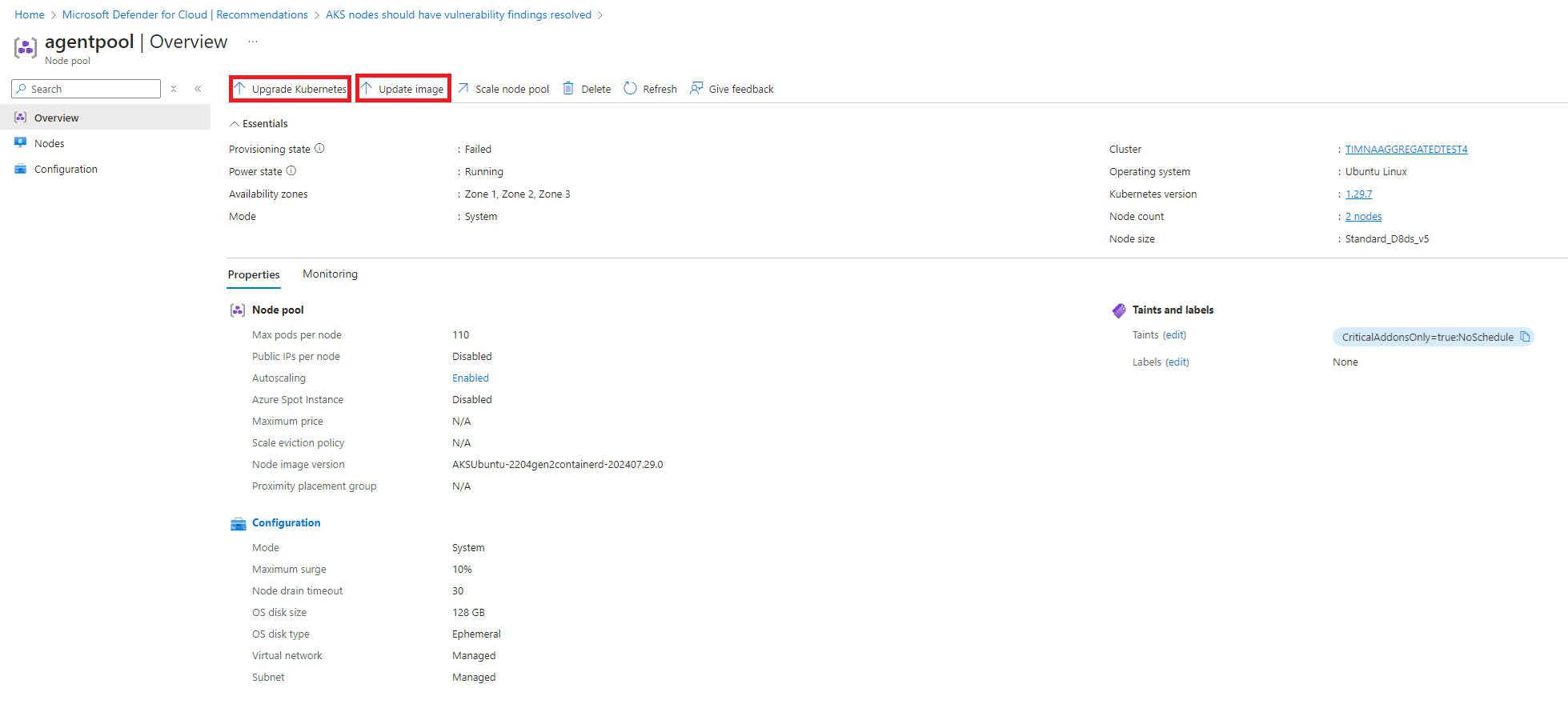
Upgrade the node pool VM image
To upgrade the node pool VM image, select the Update Image button or select Upgrade Kubernetes to upgrade the cluster Kubernetes service version.
Next steps
Learn how to use the Cloud Security Explorer to investigate vulnerabilities in a cluster node.