Explore risks to pre-deployment generative AI artifacts
Defender Cloud Security Posture Management (CSPM) plan in Microsoft Defender for Cloud helps you to improve the security posture of generative AI apps, by identifying vulnerabilities in generative AI libraries that exist in your AI artifacts such as container images and code repositories. This article explains how to explore, identify security risks for those applications.
Prerequisites
Read about AI security posture management.
Learn more about investigating risks with the cloud security explorer and attack paths.
You need a Microsoft Azure subscription. If you don't have an Azure subscription, you can sign up for a free subscription.
Enable Defender Cloud Security Posture Management (CSPM) on your Azure subscription.
Have at least one Azure OpenAI resource, with at least one model deployment connected to it via Azure AI Studio.
Identify containers running on vulnerable generative AI container images
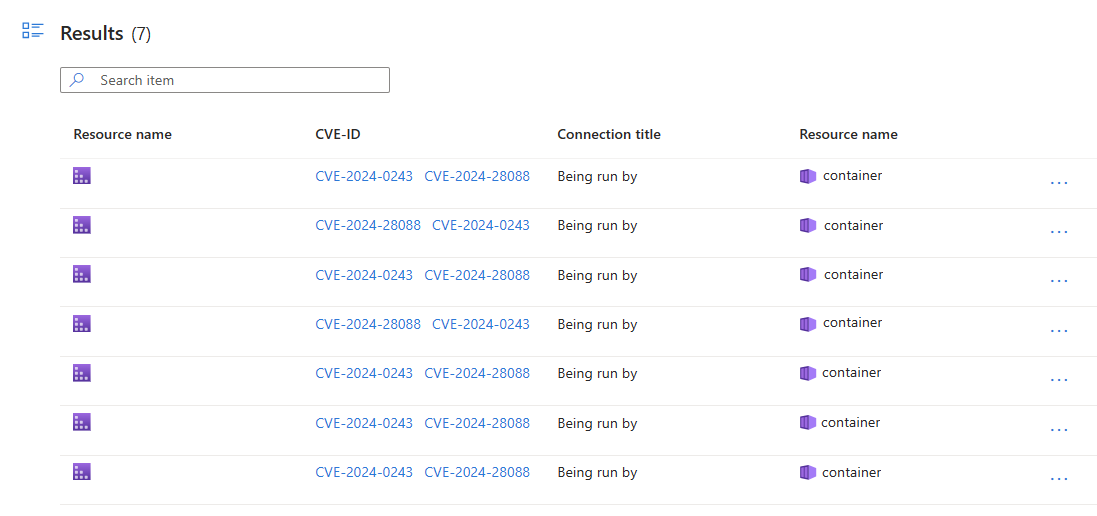
The cloud security explorer can be used to identify containers that are running generative AI container images with known vulnerabilities.
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud > Cloud Security Explorer.
Select the Container running container images with known Generative AI vulnerabilities query template.
Select Search.
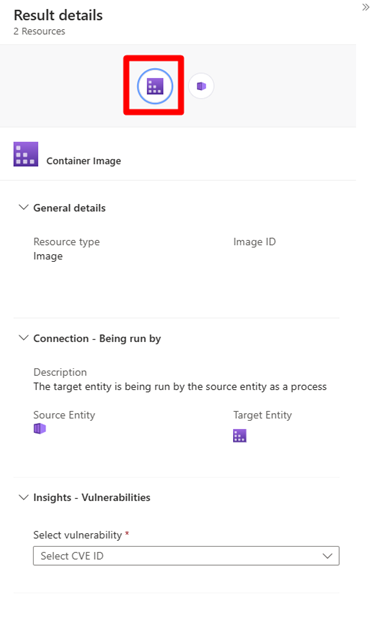
Select a result to review its details.
Select a node to review the findings.
In the insights section, select a CVE ID from the drop-down menu.
Select Open the vulnerability page.
Identify vulnerable generative AI code repositories
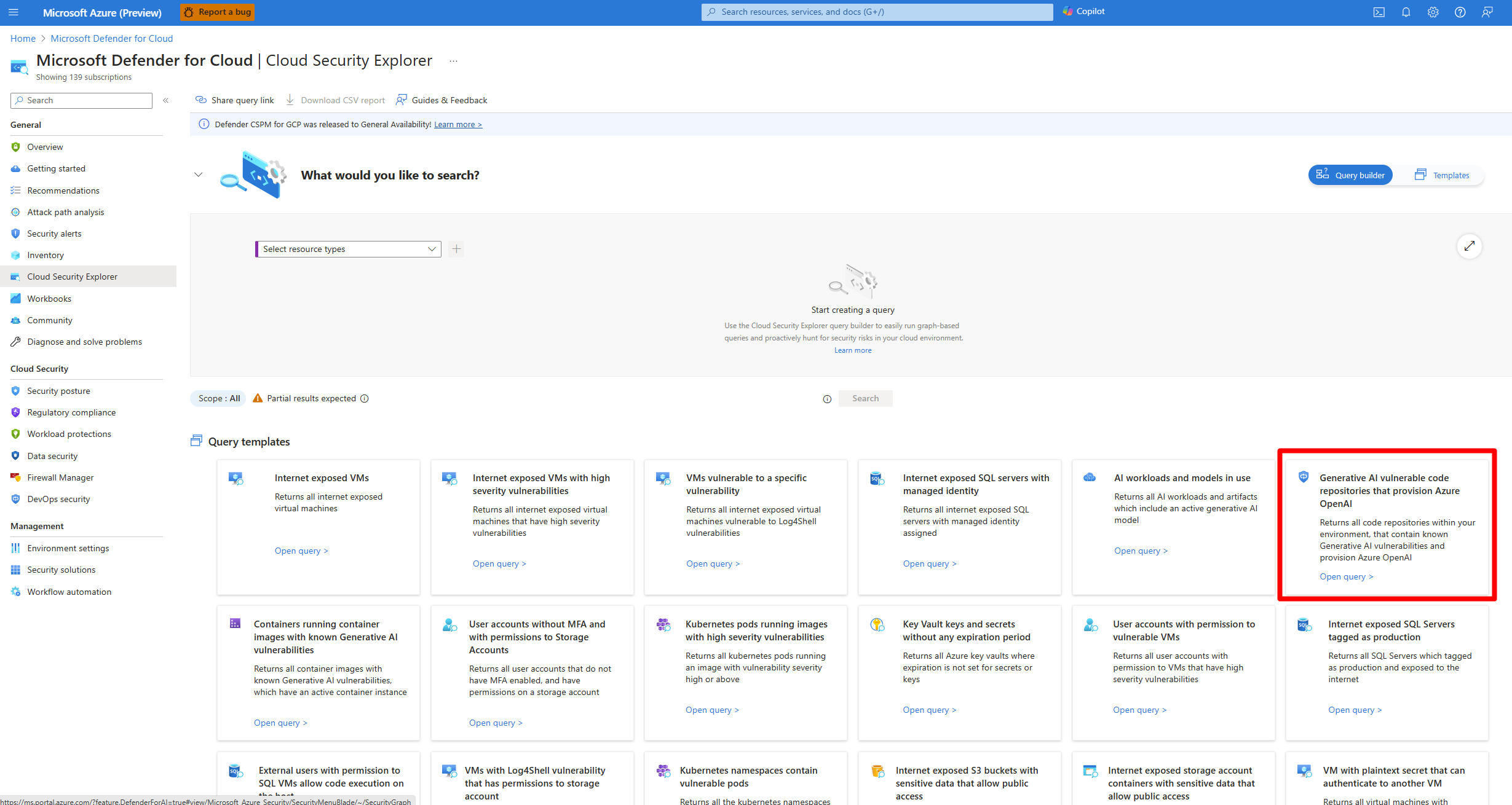
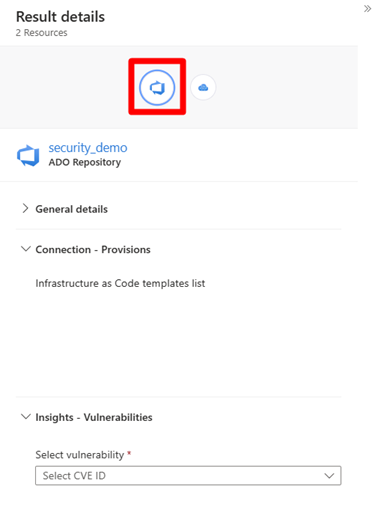
The cloud security explorer can be used to identify vulnerable generative AI code repositories, that provision Azure OpenAI.
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud > Cloud Security Explorer.
Select the Generative AI vulnerable code repositories that provision Azure OpenAI query template.
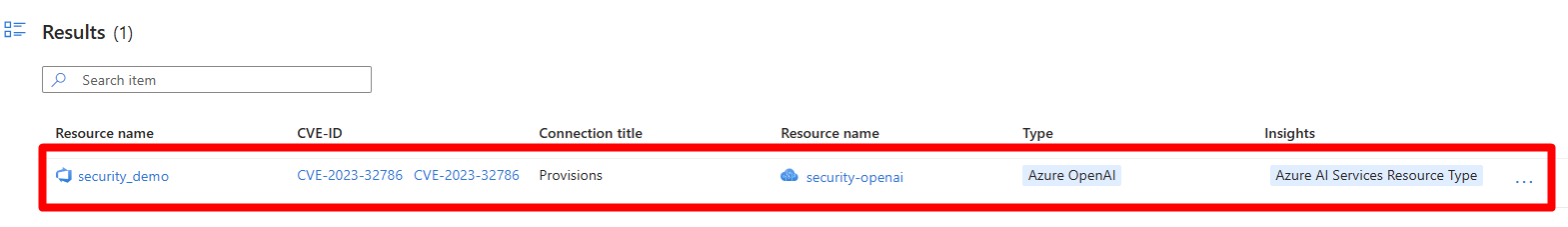
Select Search.
Select a result to review its details.
Select a node to review the findings.
In the insights section, select a CVE ID from the drop-down menu.
Select Open the vulnerability page.