Use asset inventory to manage your resources' security posture
The asset inventory page of Microsoft Defender for Cloud shows the security posture of the resources you connected to Defender for Cloud. Defender for Cloud periodically analyzes the security state of resources connected to your subscriptions to identify potential security issues and provides you with active recommendations. Active recommendations are recommendations that can be resolved to improve your security posture.
Use this view and its filters to address such questions as:
- Which of my subscriptions with Defender plans enabled have outstanding recommendations?
- Which of my machines with the tag 'Production' are missing the Log Analytics agent?
- How many of my machines tagged with a specific tag have outstanding recommendations?
- Which machines in a specific resource group have a known vulnerability (using a CVE number)?
The security recommendations on the asset inventory page are also shown in the Recommendations page, but here they're shown according to the affected resource. Learn more about implementing security recommendations.
Availability
| Aspect | Details |
|---|---|
| Release state: | General availability (GA) |
| Pricing: | Free Some features of the inventory page, such as the software inventory require paid solutions to be in-place |
| Required roles and permissions: | All users |
| Clouds: | Software inventory isn't currently supported in national clouds. |
What are the key features of asset inventory?
The inventory page provides the following tools:
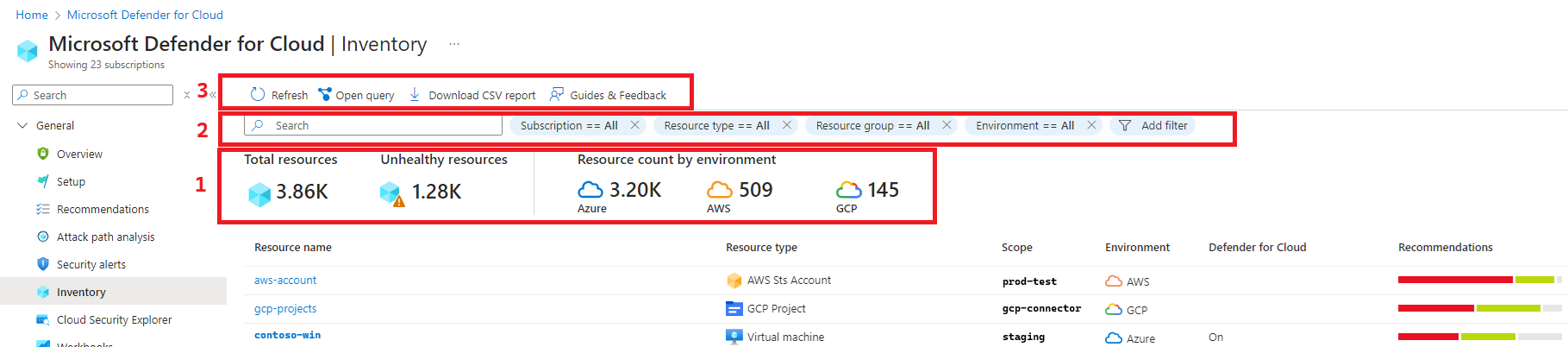
1 - Summaries
Before you define any filters, a prominent strip of values at the top of the inventory view shows:
- Total resources: The total number of resources connected to Defender for Cloud.
- Unhealthy resources: Resources with active security recommendations that you can implement. Learn more about implementing security recommendations.
- Resource count by environment: The number of resources in each environment.
- Unregistered subscriptions: Any subscription in the selected scope that hasn't yet been connected to Microsoft Defender for Cloud.
2 - Filters
The multiple filters at the top of the page provide a way to quickly refine the list of resources according to the question you're trying to answer. For example, if you wanted to know which of your machines with the tag 'Production' are missing the Log Analytics agent, you can filter the list for Agent monitoring:"Not installed" and Tags:"Production".
As soon as you apply filters, the summary values are updated to relate to the query results.
3 - Export tools
Download CSV report - Export the results of your selected filter options to a CSV file.
Open query - Export the query itself to Azure Resource Graph (ARG) to further refine, save, or modify the Kusto Query Language (KQL) query.
Tip
The KQL documentation provides a database with some sample data together with some simple queries to get the "feel" for the language. Learn more in this KQL tutorial.
How does asset inventory work?
Asset inventory utilizes Azure Resource Graph (ARG), an Azure service that lets you query Defender for Cloud's security posture data across multiple subscriptions.
ARG is designed to provide efficient resource exploration with the ability to query at scale.
You can use Kusto Query Language (KQL) in the asset inventory to quickly produce deep insights by cross-referencing Defender for Cloud data with other resource properties.
How to use asset inventory
From Defender for Cloud's sidebar, select Inventory.
Use the Filter by name box to display a specific resource, or use the filters to focus on specific resources.
By default, the resources are sorted by the number of active security recommendations.
Important
The options in each filter are specific to the resources in the currently selected subscriptions and your selections in the other filters.
For example, if you've selected only one subscription, and the subscription has no resources with outstanding security recommendations to remediate (0 unhealthy resources), the Recommendations filter will have no options.
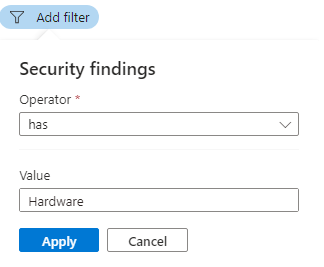
To use the Security findings filter, enter free text from the ID, security check, or CVE name of a vulnerability finding to filter to the affected resources:
Tip
The Security findings and Tags filters only accept a single value. To filter by more than one, use Add filters.
To view the current selected filter options as a query in Resource Graph Explorer, select Open query.
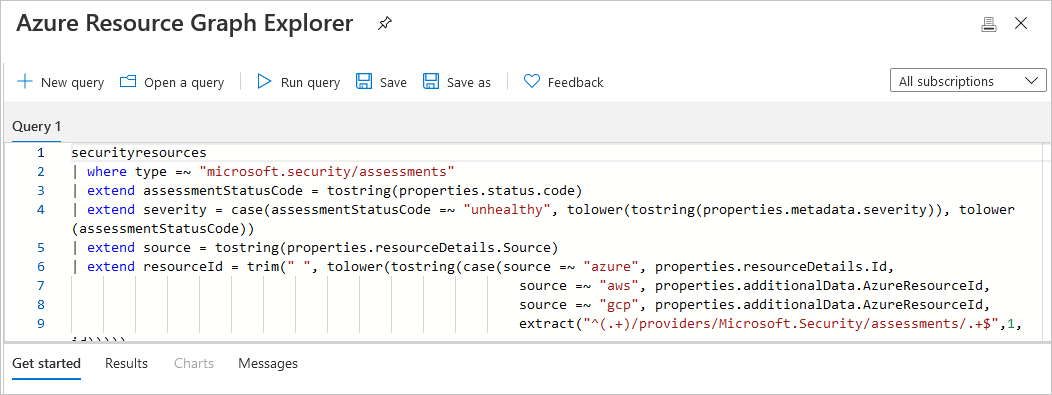
If you defined some filters and left the page open, Defender for Cloud doesn't update the results automatically. Any changes to resources won't impact the displayed results unless you manually reload the page or select Refresh.
Access a software inventory
To access the software inventory, you need one of the following paid solutions:
- Agentless machine scanning from Defender Cloud Security Posture Management (CSPM).
- Agentless machine scanning from Defender for Servers P2.
- Microsoft Defender for Endpoint integration from Defender for Servers.
Examples using Azure Resource Graph Explorer to access and explore software inventory data
Open Azure Resource Graph Explorer.
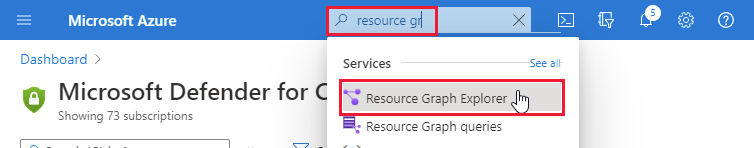
Select the following subscription scope: securityresources/softwareinventories
Enter any of the following queries (or customize them or write your own!) and select Run query.
To generate a basic list of installed software:
securityresources | where type == "microsoft.security/softwareinventories" | project id, Vendor=properties.vendor, Software=properties.softwareName, Version=properties.versionTo filter by version numbers:
securityresources | where type == "microsoft.security/softwareinventories" | project id, Vendor=properties.vendor, Software=properties.softwareName, Version=tostring(properties. version) | where Software=="windows_server_2019" and parse_version(Version)<=parse_version("10.0.17763.1999")To find machines with a combination of software products:
securityresources | where type == "microsoft.security/softwareinventories" | extend vmId = properties.azureVmId | where properties.softwareName == "apache_http_server" or properties.softwareName == "mysql" | summarize count() by tostring(vmId) | where count_ > 1Combination of a software product with another security recommendation:
(In this example – machines having MySQL installed and exposed management ports)
securityresources | where type == "microsoft.security/softwareinventories" | extend vmId = tolower(properties.azureVmId) | where properties.softwareName == "mysql" | join ( securityresources | where type == "microsoft.security/assessments" | where properties.displayName == "Management ports should be closed on your virtual machines" and properties.status.code == "Unhealthy" | extend vmId = tolower(properties.resourceDetails.Id) ) on vmId
Next steps
This article described the asset inventory page of Microsoft Defender for Cloud.
For more information on related tools, see the following pages:
- Azure Resource Graph (ARG)
- Kusto Query Language (KQL)
- View common question about asset inventory