Remediate OS misconfigurations
Microsoft Defender for Cloud provides security recommendations to improve organizational security posture and reduce risk. An important element in risk reduction is machine hardening.
Defender for Cloud assesses operating system settings against compute security baselines provided by the Microsoft Cloud Security Benchmark (MCSB). Machine information is gathered for assessment using the Azure Policy machine configuration extension (formerly known as the guest configuration) on the machine. Learn more
This article describes how to review recommendations made by the assessment.
Prerequisites
| Requirements | Details |
|---|---|
| Plan | Defender for Servers Plan 2 must be enabled |
| Extension | The Azure Policy machine configuration must be installed on machines. |
This feature previously used the Log Analytics agent (also known as the Microsoft Monitoring agent (MMA)) to collect information. If you still have the MMA in use, you might receive duplicate recommendations for the same machine. To avoid this, you can disable the MMA on the machine.
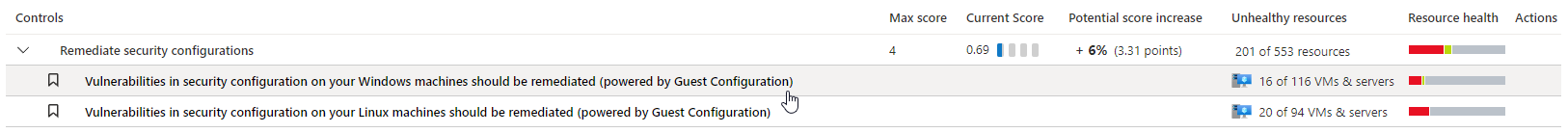
Review and remediate OS baseline recommendations
In Defender for Cloud, open the Recommendations page.
Select the relevant recommendation.
On the recommendation details page you can see the affected resources, and specific security findings. Remediate the recommendation.
Query recommendations
Defender for Cloud uses Azure Resource Graph for API, and portal queries, to query recommendation information. You can utilize these resources to create your own queries to retrieve information.
You can learn how to review recommendations in Azure Resource Graph.
Here are two sample queries you can use:
Query all unhealthy rules for a specific resource
Securityresources | where type == "microsoft.security/assessments/subassessments" | extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id) | where assessmentKey == '1f655fb7-63ca-4980-91a3-56dbc2b715c6' or assessmentKey == '8c3d9ad0-3639-4686-9cd2-2b2ab2609bda' | parse-where id with machineId:string '/providers/Microsoft.Security/' * | where machineId == '{machineId}'All Unhealthy Rules and the amount if Unhealthy machines for each
securityresources | where type == "microsoft.security/assessments/subassessments" | extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id) | where assessmentKey == '1f655fb7-63ca-4980-91a3-56dbc2b715c6' or assessmentKey == '8c3d9ad0-3639-4686-9cd2-2b2ab2609bda' | parse-where id with * '/subassessments/' subAssessmentId:string | parse-where id with machineId:string '/providers/Microsoft.Security/' * | extend status = tostring(properties.status.code) | summarize count() by subAssessmentId, status
Next steps
Learn more about Azure Resource Graph's query language.