Manage IP access lists
This guide introduces IP access lists for the Azure Databricks account and workspaces.
IP access lists overview
Note
This feature requires the Premium plan.
By default, users can connect to Azure Databricks from any computer or IP address. IP access lists enable you to restrict access to your Azure Databricks account and workspaces based on a user’s IP address. For example, you can configure IP access lists to allow users to connect only through existing corporate networks with a secure perimeter. If the internal VPN network is authorized, users who are remote or traveling can use the VPN to connect to the corporate network. If a user attempts to connect to Azure Databricks from an insecure network, like from a coffee shop, access is blocked.
There are two IP access list features:
- IP access lists for the account console (Public Preview): Account admins can configure IP access lists for the account console to allow users to connect to the account console UI and account-level REST APIs only through a set of approved IP addresses. Account owners and account admins can use an account console UI or a REST API to configure allowed and blocked IP addresses and subnets. See Configure IP access lists for the account console.
- IP access lists for workspaces: Workspace admins can configure IP access lists for Azure Databricks workspaces to allow users to connect to the workspace or workspace-level APIs only through a set of approved IP addresses. Workspace admins use a REST API to configure allowed and blocked IP addresses and subnets. See Configure IP access lists for workspaces.
Note
If you use Private Link, IP access lists apply only to requests over the internet (public IP addresses). Private IP addresses from Private Link traffic cannot be blocked by IP access lists. To control who can access Azure Databricks using private link, you can check which private endpoints have been created See Enable Azure Private Link back-end and front-end connections.
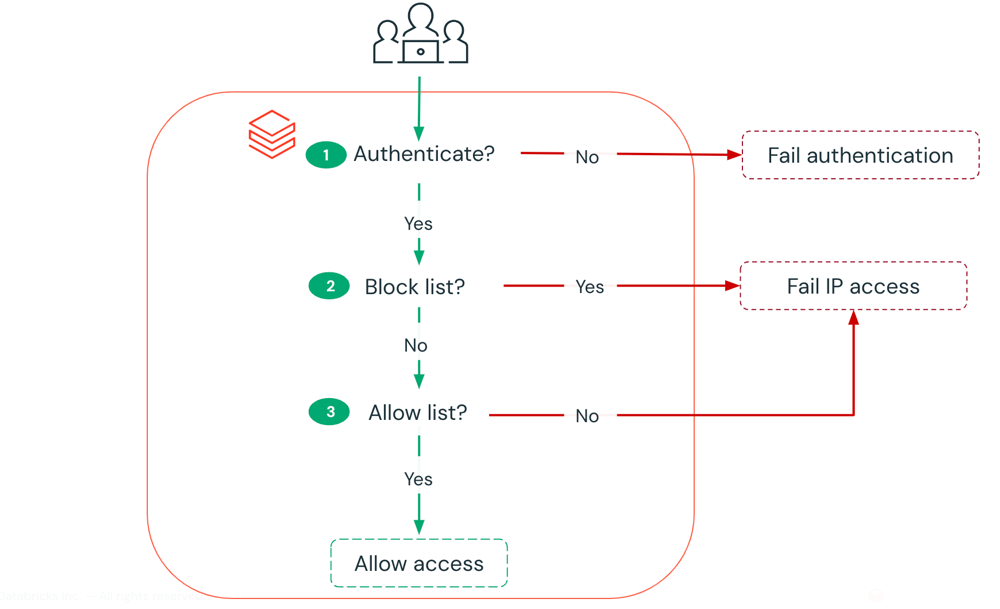
How is access checked?
The IP access lists feature allows you to configure allow lists and block lists for the Azure Databricks account console and workspaces:
- Allow lists contain the set of IP addresses on the public internet that are allowed access. Allow multiple IP addresses explicitly or as entire subnets (for example
216.58.195.78/28). - Block lists contain the IP addresses or subnets to block, even if they are included in the allow list. You might use this feature if an allowed IP address range includes a smaller range of infrastructure IP addresses that in practice are outside the actual secure network perimeter.
When a connection is attempted:
- First all block lists are checked. If the connection IP address matches any block list, the connection is rejected.
- If the connection was not rejected by block lists, the IP address is compared with the allow lists. If there is at least one allow list, the connection is allowed only if the IP address matches an allow list. If there are no allow lists, all IP addresses are allowed.
If the feature is disabled, all access is allowed to your account or workspace.
For all allow lists and block lists combined, the account console supports a maximum of 1000 IP/CIDR values, where one CIDR counts as a single value.
Changes to IP access lists can take a few minutes to take effect.