Use Azure Key Vault secrets in pipeline activities
APPLIES TO:  Azure Data Factory
Azure Data Factory  Azure Synapse Analytics
Azure Synapse Analytics
Tip
Try out Data Factory in Microsoft Fabric, an all-in-one analytics solution for enterprises. Microsoft Fabric covers everything from data movement to data science, real-time analytics, business intelligence, and reporting. Learn how to start a new trial for free!
You can store credentials or secret values in an Azure Key Vault and use them during pipeline execution to pass to your activities.
Prerequisites
This feature relies on the data factory managed identity. Learn how it works from Managed identity for Data Factory and make sure your data factory has one associated.
Steps
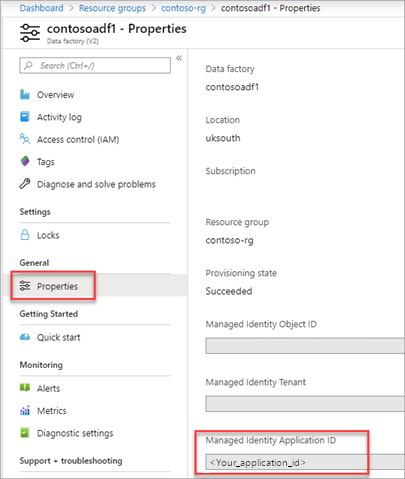
Open the properties of your data factory and copy the Managed Identity Application ID value.
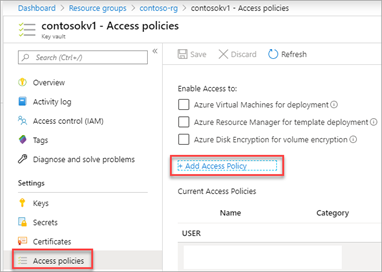
Open the key vault access policies and add the managed identity permissions to Get and List secrets.
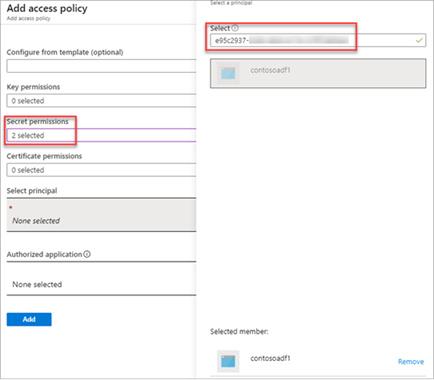
Click Add, then click Save.
Navigate to your Key Vault secret and copy the Secret Identifier.
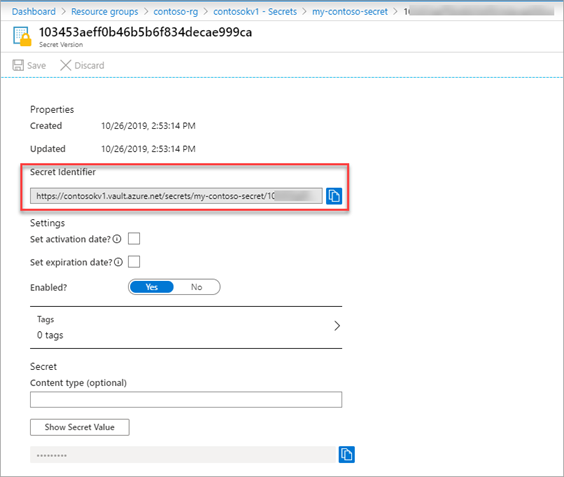
Make a note of your secret URI that you want to get during your data factory pipeline run.
Caution
The secret URI is structured like this:
{vaultBaseUrl}/secrets/{secret-name}/{secret-version}. The secret-version is optional; the latest version is returned when not specified. It is often desirable to specify a secret URI in a pipeline without a specific version so that the pipeline always uses the latest version of the secret.In your Data Factory pipeline, add a new Web activity and configure it as follows.
Property Value Secure Output True URL [Your secret URI value]?api-version=7.0 Method GET Authentication System Assigned Managed Identity Resource https://vault.azure.net 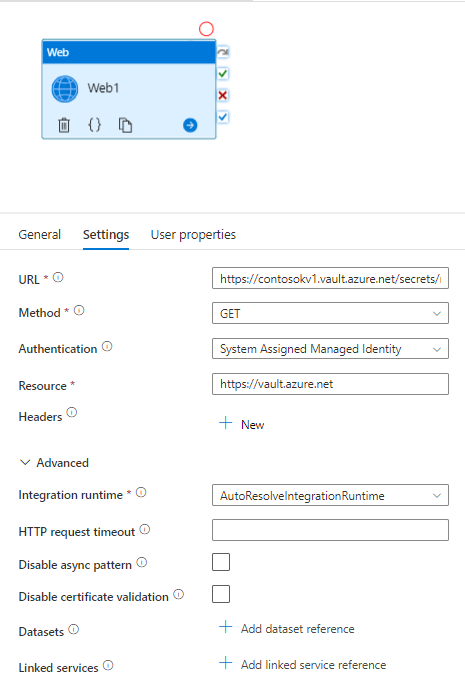
Important
You must add ?api-version=7.0 to the end of your secret URI.
Caution
Set the Secure Output option to true to prevent the secret value from being logged in plain text. Any further activities that consume this value should have their Secure Input option set to true.
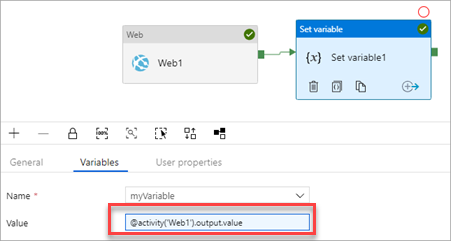
To use the value in another activity, use the following code expression @activity('Web1').output.value.
Related content
To learn how to use Azure Key Vault to store credentials for data stores and computes, see Store credentials in Azure Key Vault