Authorize an application request by using Microsoft Entra ID
Azure Web PubSub supports Microsoft Entra ID for authorizing requests from applications.
This article shows you how to configure your Web PubSub resource and code to authorize a request to a Web PubSub resource from an Azure application.
Register an application
The first step is to register an Azure application.
- In the Azure portal, search for and then select Microsoft Entra ID.
- On the left menu under Manage, select App registrations.
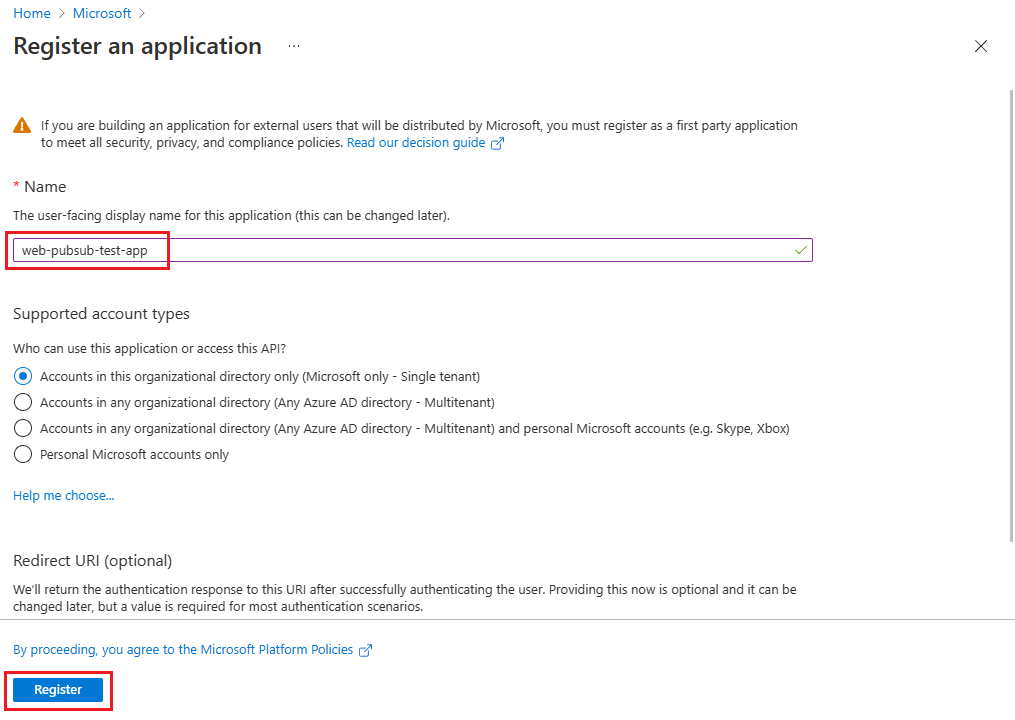
- Select New registration.
- For Name, enter a name to use for your application.
- Select Register to confirm the application registration.
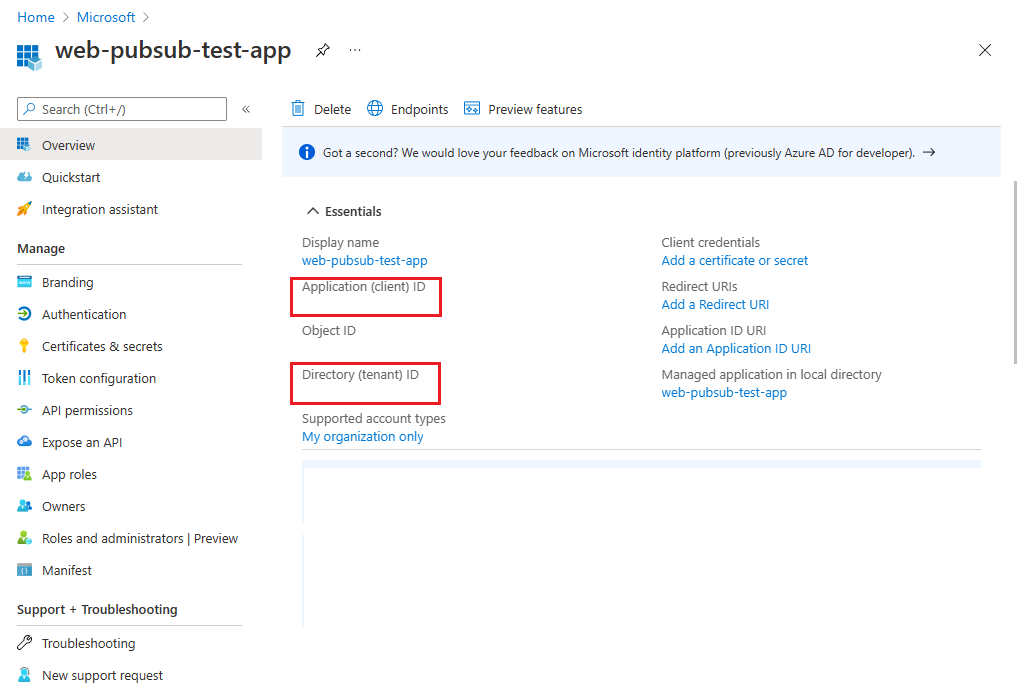
When your application is registered, go to the application overview to view the values for Application (client) ID and Directory (tenant) ID. You use these values in the following sections.
For more information about registering an application, see the quickstart Register an application by using the Microsoft identity platform.
Add credentials
You can add both certificates and client secrets (a string) as credentials to your confidential client app registration.
For more information about adding credentials, see Add credentials.
Add a client secret
The application requires a client secret for a client to prove its identity when it requests a token.
To create a client secret:
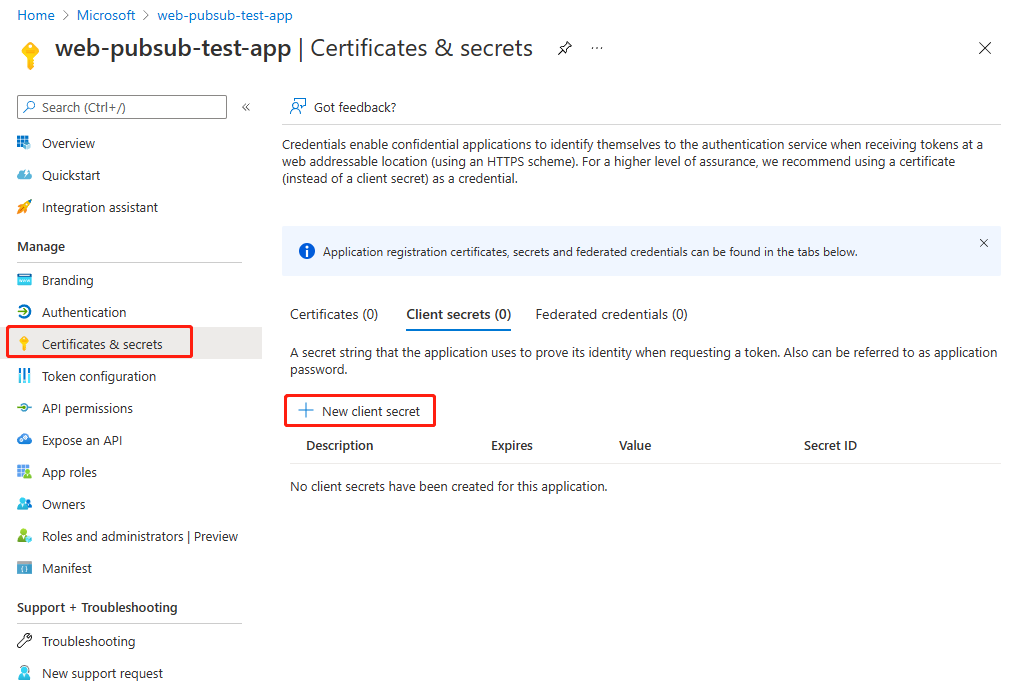
On the left menu under Manage, select Certificates & secrets.
On the Client secrets tab, select New client secret.
Enter a description for the client secret, and then choose an Expires time for the secret.
Copy the value of the client secret and paste it in a secure location for later use.
Note
The secret is visible only when you create the secret. You can't view the client secret in the portal later.
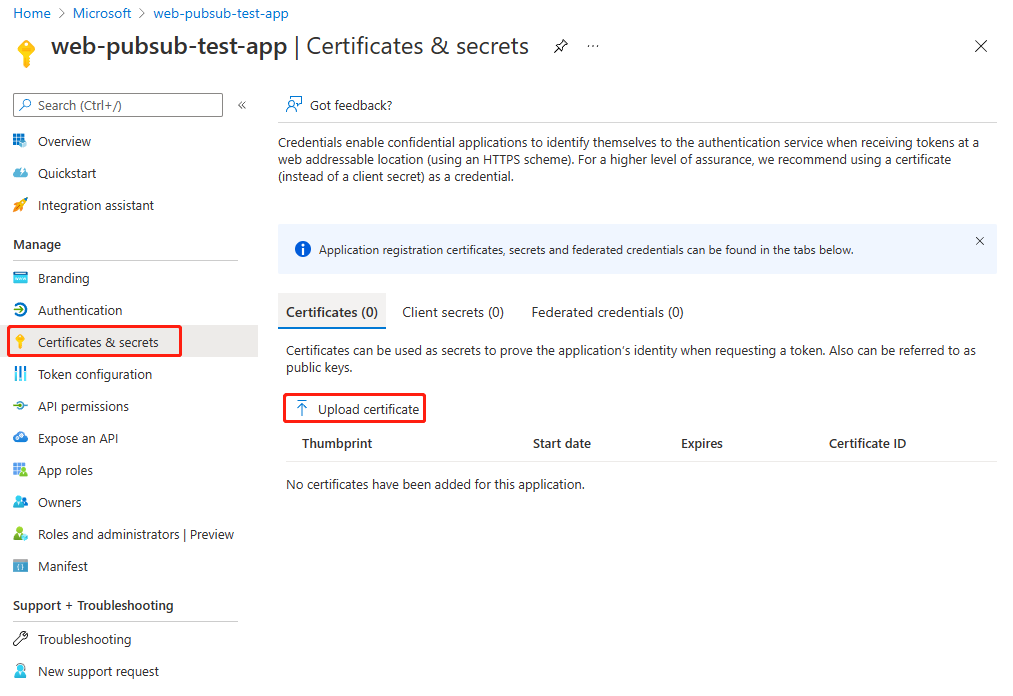
Add a certificate
You can upload a certificate instead of creating a client secret.
Add a role assignment in the Azure portal
This section demonstrates how to assign a Web PubSub Service Owner role to a service principal (application) for a Web PubSub resource.
Note
You can assign a role to any scope, including management group, subscription, resource group, and single resource. For more information about scope, see Understand scope for Azure role-based access control.
In the Azure portal, go to your Web PubSub resource.
On the left menu, select Access control (IAM) to display access control settings for the resource.
Select the Role assignments tab and view the role assignments at this scope.
The following figure shows an example of the Access control (IAM) pane for a Web PubSub resource:
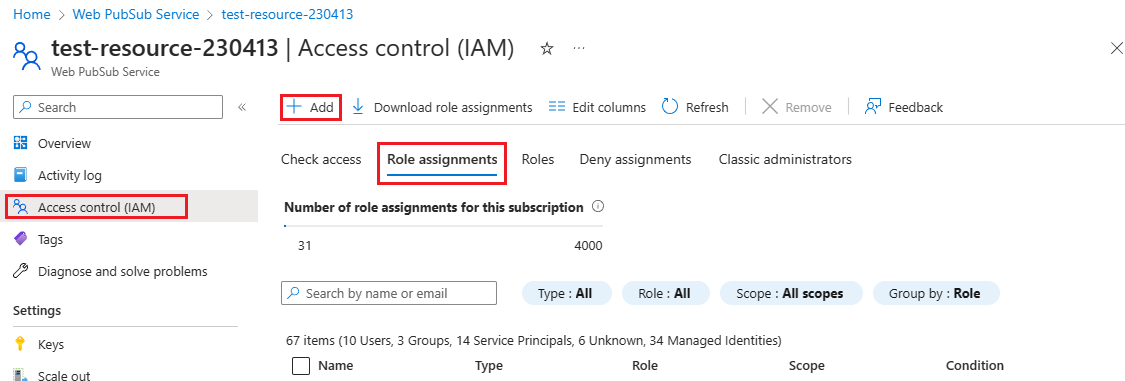
Select Add > Add role assignment.
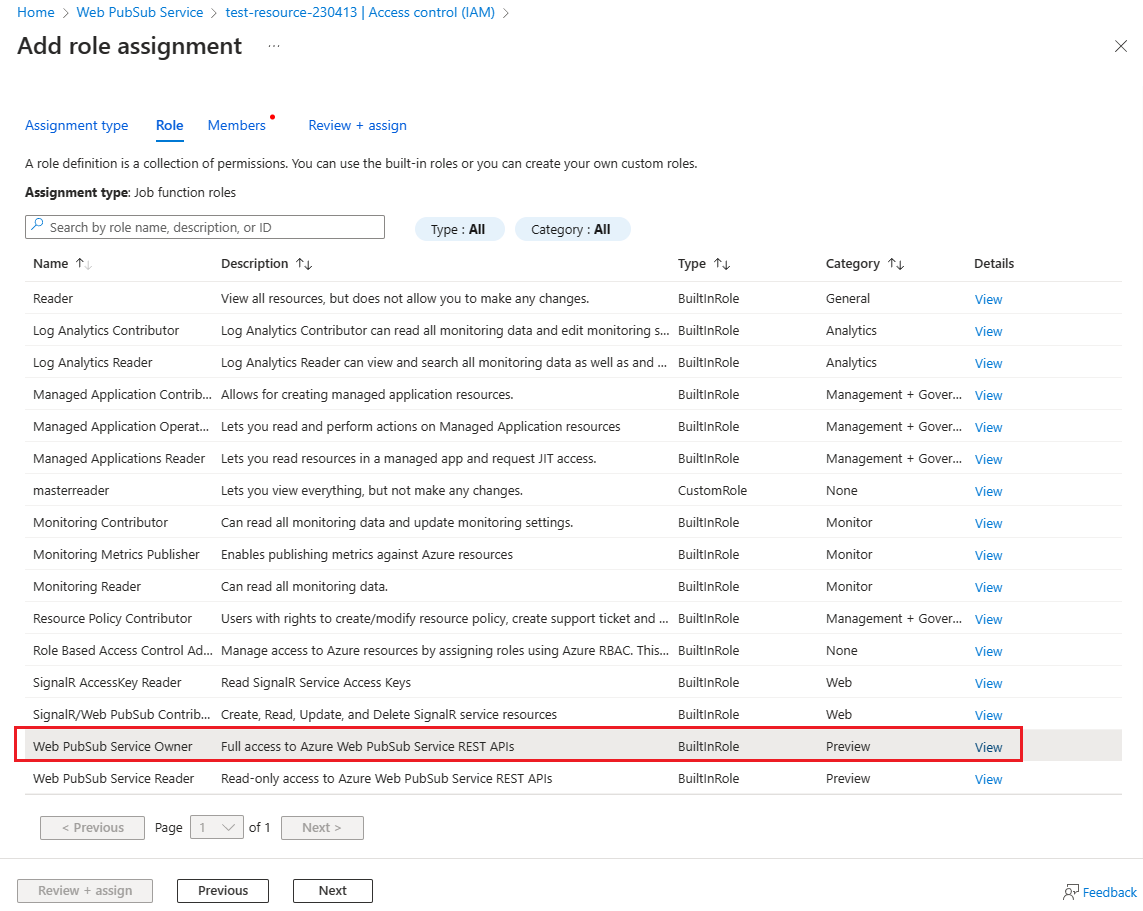
Select the Roles tab, and then select Web PubSub Service Owner.
Select Next.
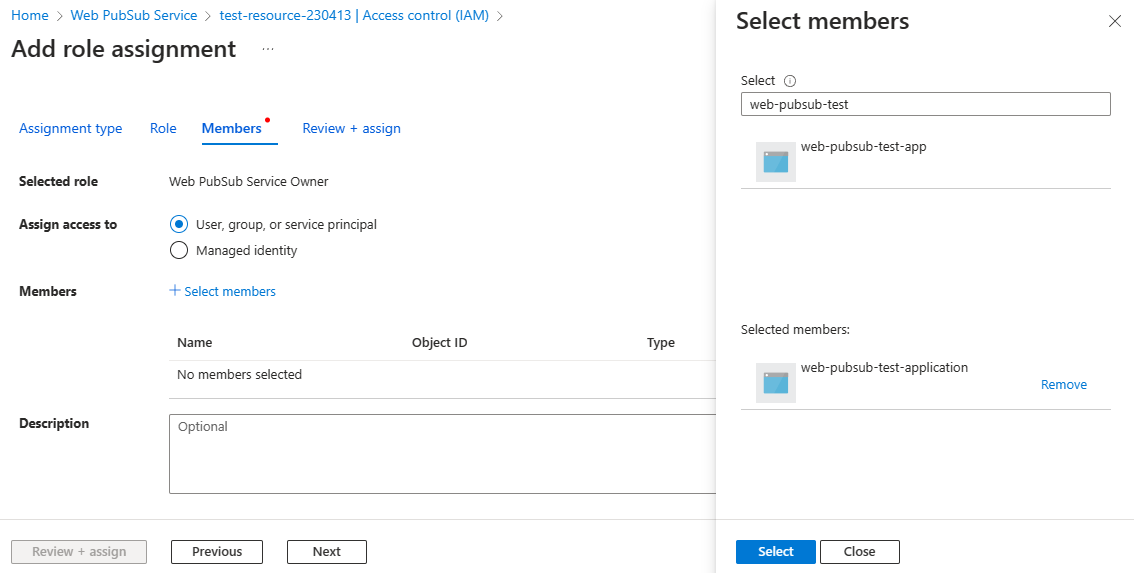
Select the Members tab. Under Assign access to, select User, group, or service principal.
Choose Select members.
Search for and select the application to assign the role to.
Choose Select to confirm the selection.
Select Next.
Select Review + assign to confirm the change.
Important
Azure role assignments might take up to 30 minutes to propagate.
To learn more about how to assign and manage Azure role assignments, see these articles:
- Assign Azure roles by using the Azure portal
- Assign Azure roles by using REST API
- Assign Azure roles by using Azure PowerShell
- Assign Azure roles by using the Azure CLI
- Assign Azure roles by using an Azure Resource Manager template
Code samples that use Microsoft Entra authorization
Get samples that use Microsoft Entra authorization in our four officially supported programming languages: