Tutorial: Create a policy assignment to identify non-compliant resources
The first step in understanding compliance in Azure is to identify the status of your resources. Azure Policy supports auditing the state of your Azure Arc-enabled server with machine configuration policies. Azure Policy's machine configuration definitions can audit or apply settings inside the machine.
This tutorial steps you through the process of creating and assigning a policy in order to identify which of your Azure Arc-enabled servers don't have Microsoft Defender for Servers enabled.
In this tutorial, you'll learn how to:
- Create policy assignment and assign a definition to it
- Identify resources that aren't compliant with the new policy
- Remove the policy from non-compliant resources
Prerequisites
If you don't have an Azure subscription, create a free account before you begin.
Create a policy assignment
Use the following procedure to create a policy assignment and assign the policy definition Azure Defender for servers should be enabled.
Launch the Azure Policy service in the Azure portal by selecting All services, then searching for and selecting Policy.
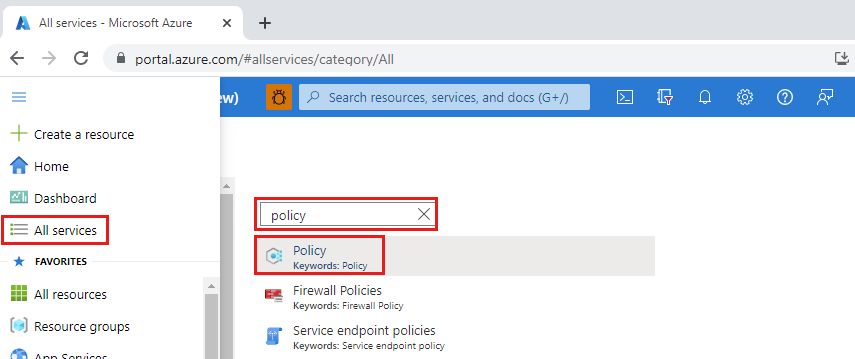
Select Assignments on the left side of the Azure Policy page. An assignment is a policy assigned to take place within a specific scope.
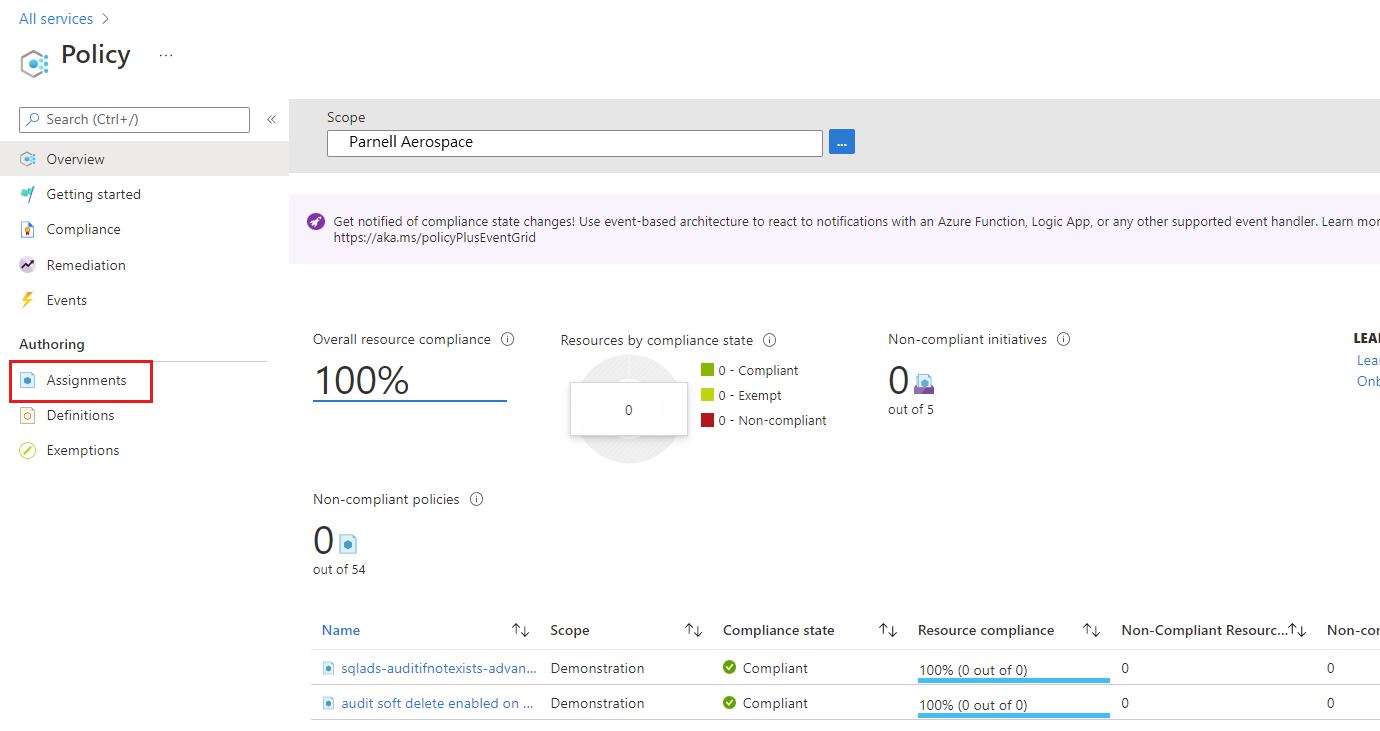
Select Assign Policy from the top of the Policy | Assignments page.
On the Assign Policy page, select the Scope by clicking the ellipsis and selecting either a management group or subscription. Optionally, select a resource group. A scope determines what resources or grouping of resources the policy assignment gets enforced on. Then select Select at the bottom of the Scope page.
This example uses the Parnell Aerospace subscription. Your subscription will differ.
Resources can be excluded based on the Scope. Exclusions start at one level lower than the level of the Scope. Exclusions are optional, so leave it blank for now.
Select the Policy definition ellipsis to open the list of available definitions. Azure Policy comes with built-in policy definitions you can use. Many are available, such as:
- Enforce tag and its value
- Apply tag and its value
- Inherit a tag from the resource group if missing
For a partial list of available built-in policies, see Azure Policy samples.
Search through the policy definitions list to find the Azure Defender for servers should be enabled definition. Choose that policy and select Add.
The Assignment name is automatically populated with the policy name you selected, but you can change it. For this example, leave the policy name as is, and don't change any of the remaining options on the page.
For this example, we don't need to change any settings on the other tabs. Select Review + Create to review your new policy assignment, then select Create.
You're now ready to identify non-compliant resources to understand the compliance state of your environment.
Identify non-compliant resources
Select Compliance in the left side of the page. Then locate the Azure Defender for servers should be enabled policy assignment you created.
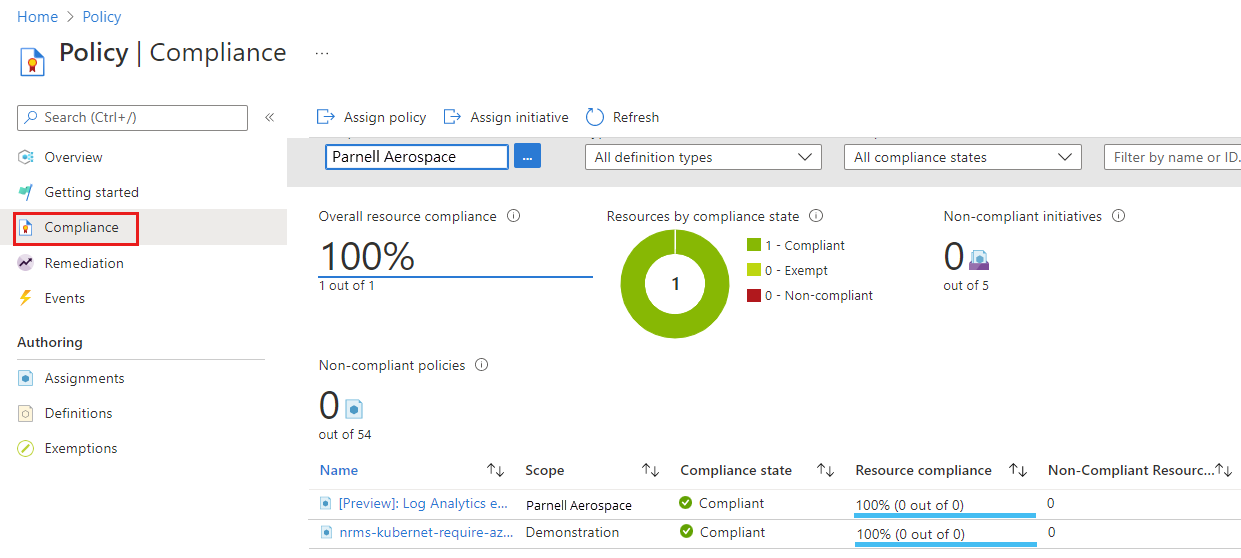
If there are any existing resources that aren't compliant with this new assignment, they appear under Non-compliant resources.
When a condition is evaluated against your existing resources and found true, those resources are marked as non-compliant with the policy. The following table shows how different policy effects work with the condition evaluation for the resulting compliance state. Although you don't see the evaluation logic in the Azure portal, the compliance state results are shown. The compliance state result is either compliant or non-compliant.
| Resource state | Effect | Policy evaluation | Compliance state |
|---|---|---|---|
| Exists | Deny, Audit, Append*, DeployIfNotExist*, AuditIfNotExist* | True | Non-compliant |
| Exists | Deny, Audit, Append*, DeployIfNotExist*, AuditIfNotExist* | False | Compliant |
| New | Audit, AuditIfNotExist* | True | Non-compliant |
| New | Audit, AuditIfNotExist* | False | Compliant |
* The Append, DeployIfNotExist, and AuditIfNotExist effects require the IF statement to be TRUE. The effects also require the existence condition to be FALSE to be non-compliant. When TRUE, the IF condition triggers evaluation of the existence condition for the related resources.
Clean up resources
To remove the assignment created, follow these steps:
Select Compliance (or Assignments) in the left side of the Azure Policy page and locate the Azure Defender for servers should be enabled policy assignment you created.
Right-click the policy assignment and select Delete assignment.
Next steps
In this tutorial, you assigned a policy definition to a scope and evaluated its compliance report. The policy definition validates that all the resources in the scope are compliant and identifies which ones aren't. Now you're ready to monitor your Azure Arc-enabled servers machine by enabling VM insights.
To learn how to monitor and view the performance, running process and their dependencies from your machine, continue to the tutorial: