Tutorial: Configure security analytics for Azure Active Directory B2C data with Microsoft Sentinel
Increase the security of your Azure Active Directory B2C (Azure AD B2C) environment by routing logs and audit information to Microsoft Sentinel. The scalable Microsoft Sentinel is a cloud-native, security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. Use the solution for alert detection, threat visibility, proactive hunting, and threat response for Azure AD B2C.
Learn more:
More uses for Microsoft Sentinel, with Azure AD B2C, are:
- Detect previously undetected threats and minimize false positives with analytics and threat intelligence features
- Investigate threats with artificial intelligence (AI)
- Hunt for suspicious activities at scale, and benefit from the experience of years of cybersecurity work at Microsoft
- Respond to incidents rapidly with common task orchestration and automation
- Meet your organization's security and compliance requirements
In this tutorial, learn how to:
- Transfer Azure AD B2C logs to a Log Analytics workspace
- Enable Microsoft Sentinel in a Log Analytics workspace
- Create a sample rule in Microsoft Sentinel to trigger an incident
- Configure an automated response
Configure Azure AD B2C with Azure Monitor Log Analytics
To define where logs and metrics for a resource are sent,
- Enable Diagnostic settings in Microsoft Entra ID, in your Azure AD B2C tenant.
- Configure Azure AD B2C to send logs to Azure Monitor.
Learn more, Monitor Azure AD B2C with Azure Monitor.
Deploy a Microsoft Sentinel instance
After you configure your Azure AD B2C instance to send logs to Azure Monitor, enable an instance of Microsoft Sentinel.
Important
To enable Microsoft Sentinel, obtain Contributor permissions to the subscription in which the Microsoft Sentinel workspace resides. To use Microsoft Sentinel, use Contributor or Reader permissions on the resource group to which the workspace belongs.
Sign in to the Azure portal.
Select the subscription where the Log Analytics workspace is created.
Search for and select Microsoft Sentinel.
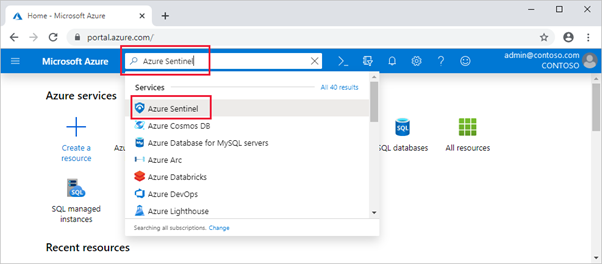
Select Add.
In the search workspaces field, select the new workspace.
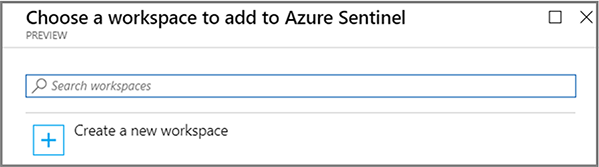
Select Add Microsoft Sentinel.
Note
It's possible to run Microsoft Sentinel on more than one workspace, however data is isolated in a single workspace.
See, Quickstart: Onboard Microsoft Sentinel
Create a Microsoft Sentinel rule
After you enable Microsoft Sentinel, get notified when something suspicious occurs in your Azure AD B2C tenant.
You can create custom analytics rules to discover threats and anomalous behaviors in your environment. These rules search for specific events, or event sets, and alert you when event thresholds or conditions are met. Then incidents are generated for investigation.
See, Create custom analytics rules to detect threats
Note
Microsoft Sentinel has templates to create threat detection rules that search your data for suspicious activity. For this tutorial, you create a rule.
Notification rule for unsuccessful forced access
Use the following steps to receive notification about two or more unsuccessful, forced access attempts into your environment. An example is brute-force attack.
In Microsoft Sentinel, from the left menu, select Analytics.
On the top bar, select + Create > Scheduled query rule.
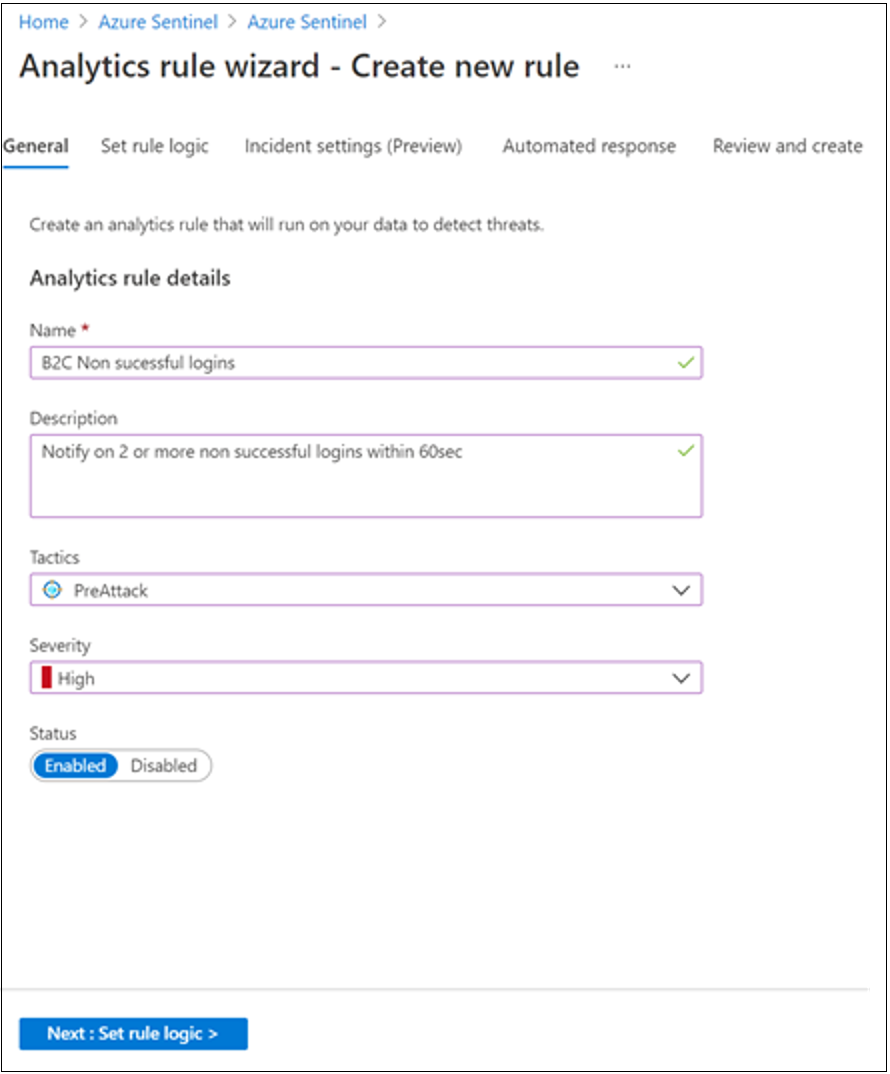
In the Analytics Rule wizard, go to General.
For Name, enter a name for unsuccessful logins.
For Description, indicate the rule notifies for two or more unsuccessful sign-ins, within 60 seconds.
For Tactics, select a category. For example, select PreAttack.
For Severity, select a severity level.
Status is Enabled by default. To change a rule, go to the Active rules tab.
Select the Set rule logic tab.
Enter a query in the Rule query field. The query example organizes the sign-ins by
UserPrincipalName.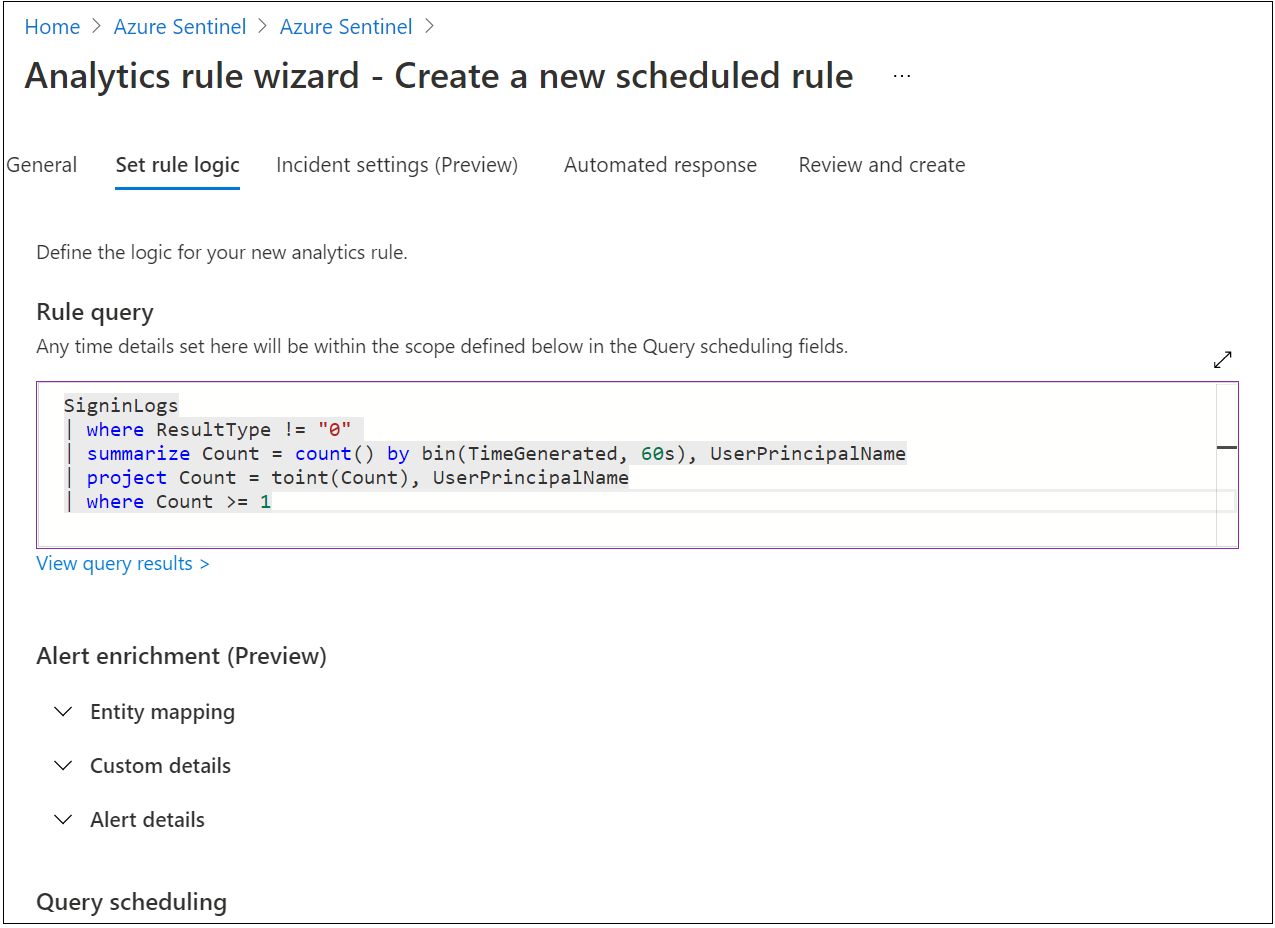
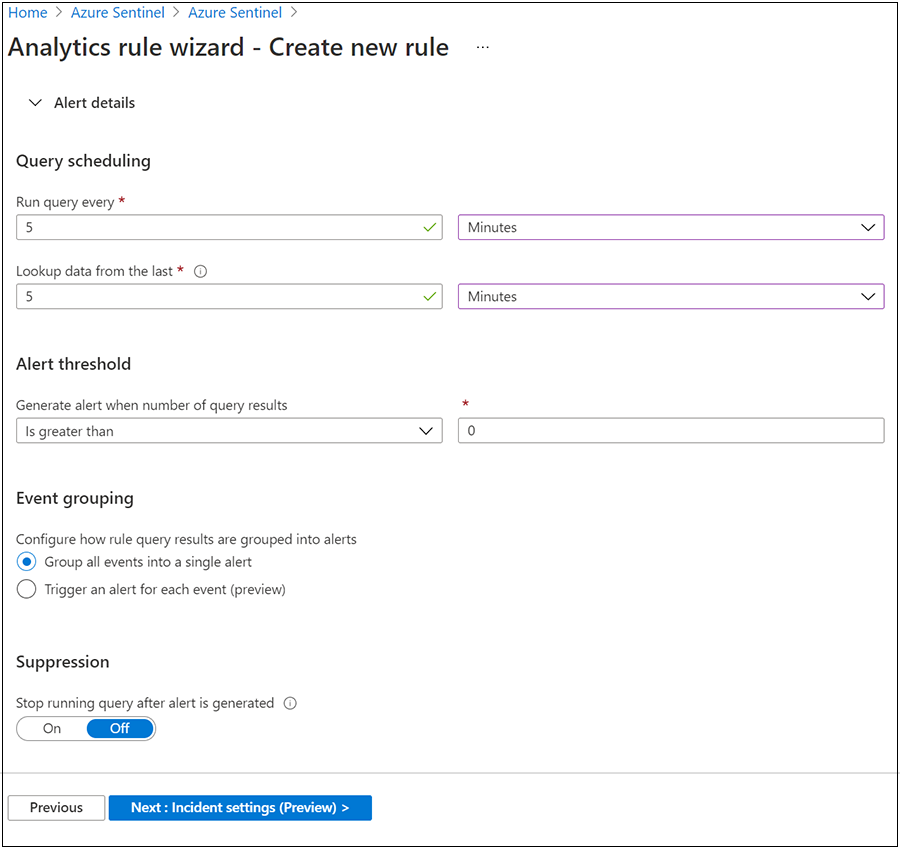
Go to Query scheduling.
For Run query every, enter 5 and Minutes.
For Lookup data from the last, enter 5 and Minutes.
For Generate alert when number of query results, select Is greater than, and 0.
For Event grouping, select Group all events into a single alert.
For Stop running query after alert is generated, select Off.
Select Next: Incident settings (Preview).
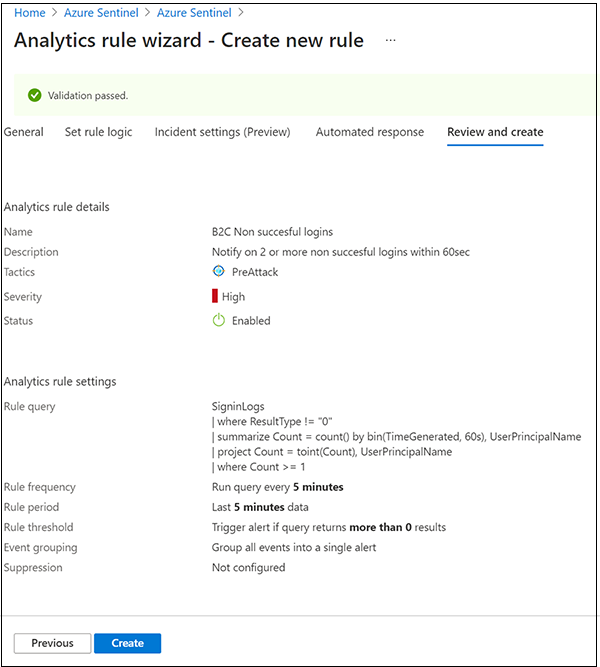
Go to the Review and create tab to review rule settings.
When the Validation passed banner appears, select Create.
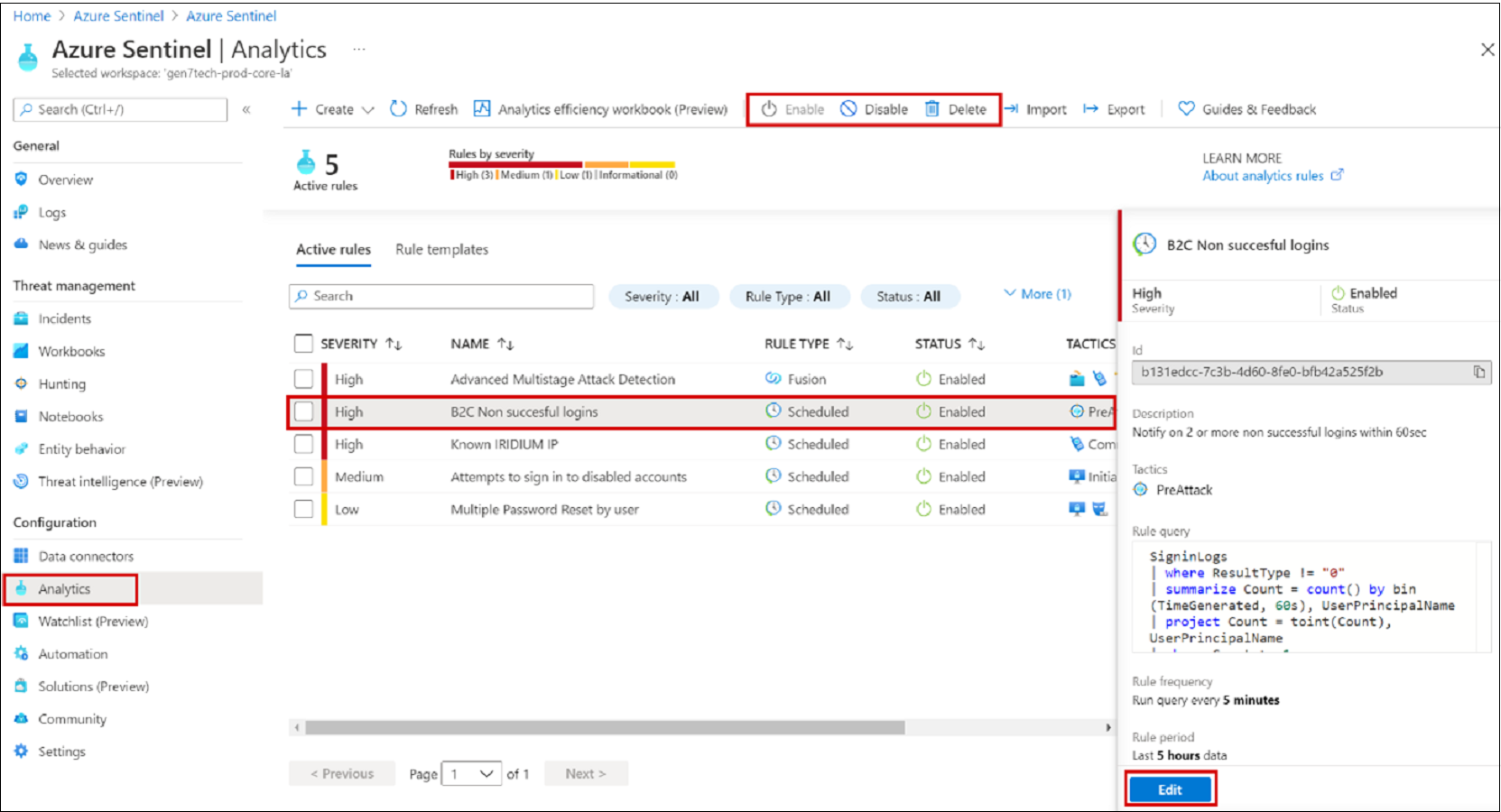
View a rule and related incidents
View the rule and the incidents it generates. Find your newly created custom rule of type Scheduled in the table under the Active rules tab on the main
- Go to the Analytics screen.
- Select the Active rules tab.
- In the table, under Scheduled, find the rule.
You can edit, enable, disable, or delete the rule.
Triage, investigate, and remediate incidents
An incident can include multiple alerts, and is an aggregation of relevant evidence for an investigation. At the incident level, you can set properties such as Severity and Status.
Learn more: Investigate incidents with Microsoft Sentinel.
Go to the Incidents page.
Select an incident.
On the right, detailed incident information appears, including severity, entities, events, and the incident ID.
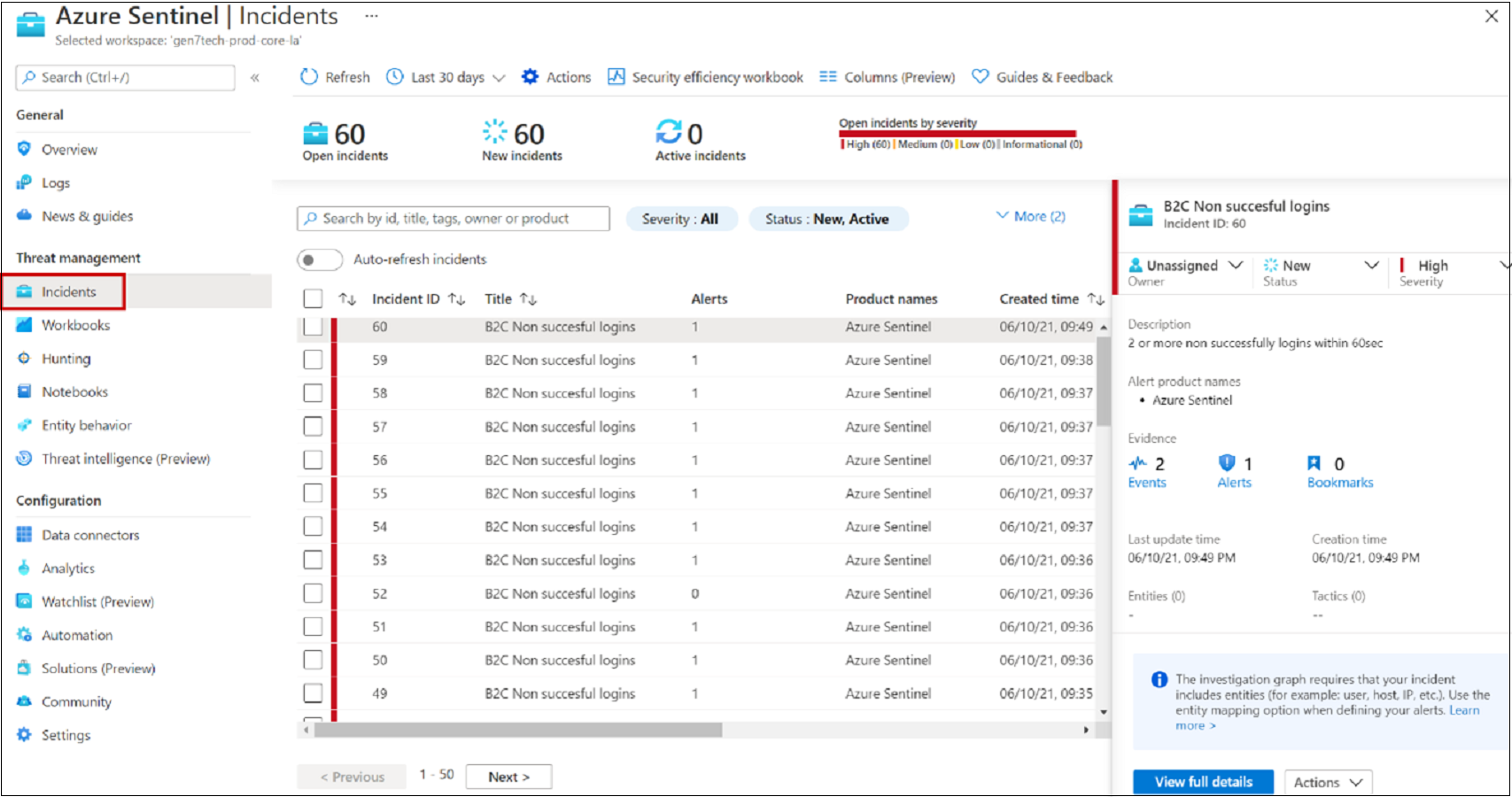
On the Incidents pane, elect View full details.
Review tabs that summarize the incident.
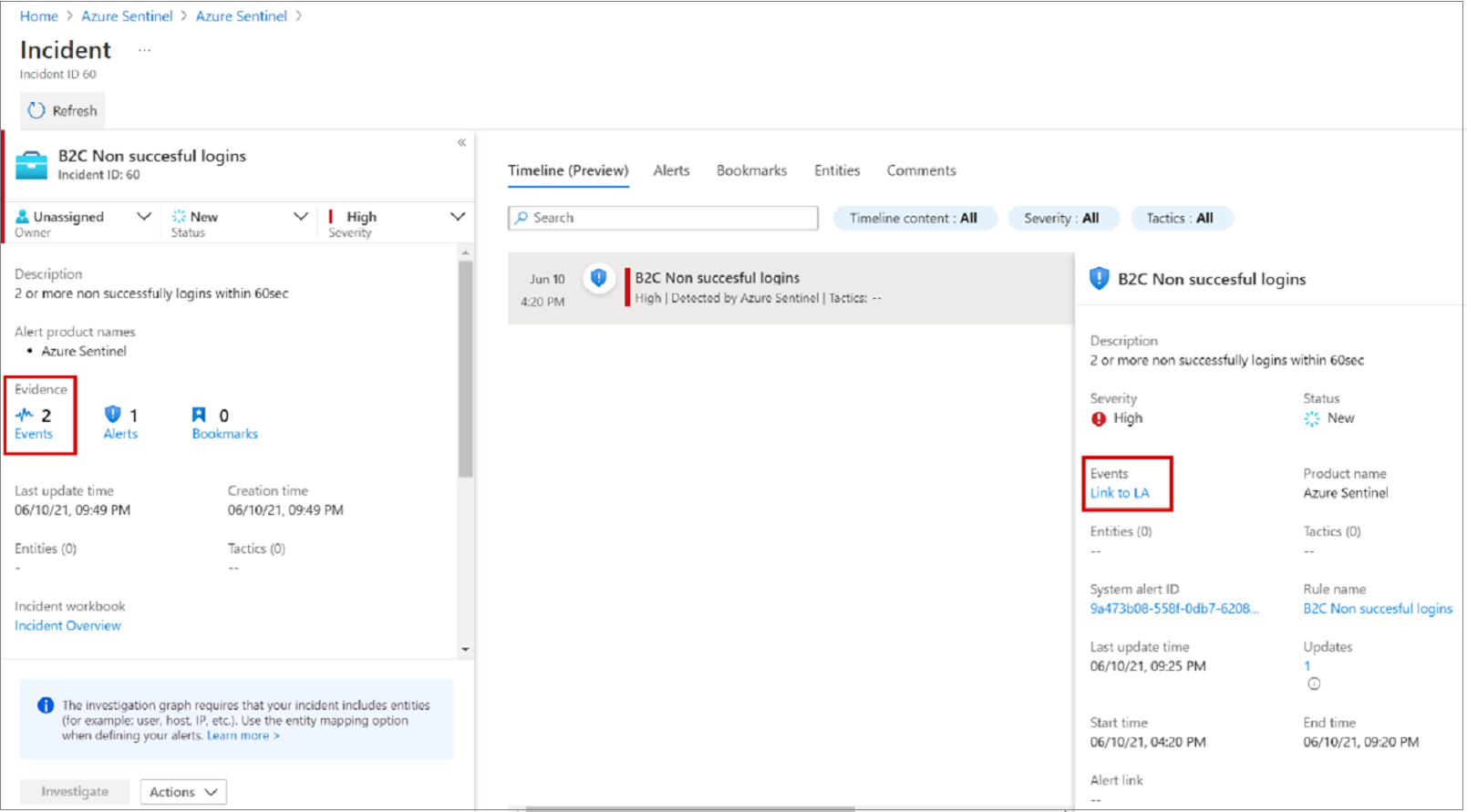
Select Evidence > Events > Link to Log Analytics.
In the results, see the identity
UserPrincipalNamevalue attempting sign-in.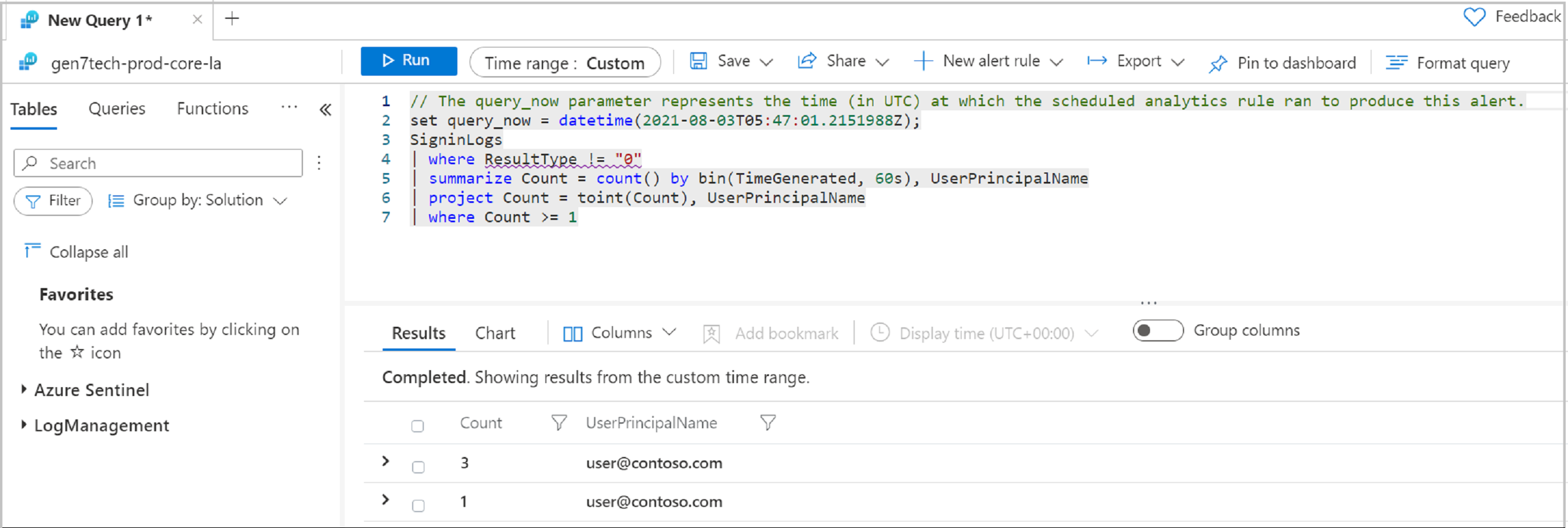
Automated response
Microsoft Sentinel has security orchestration, automation, and response (SOAR) functions. Attach automated actions, or a playbook, to analytics rules.
See, What is SOAR?
Email notification for an incident
For this task, use a playbook from the Microsoft Sentinel GitHub repository.
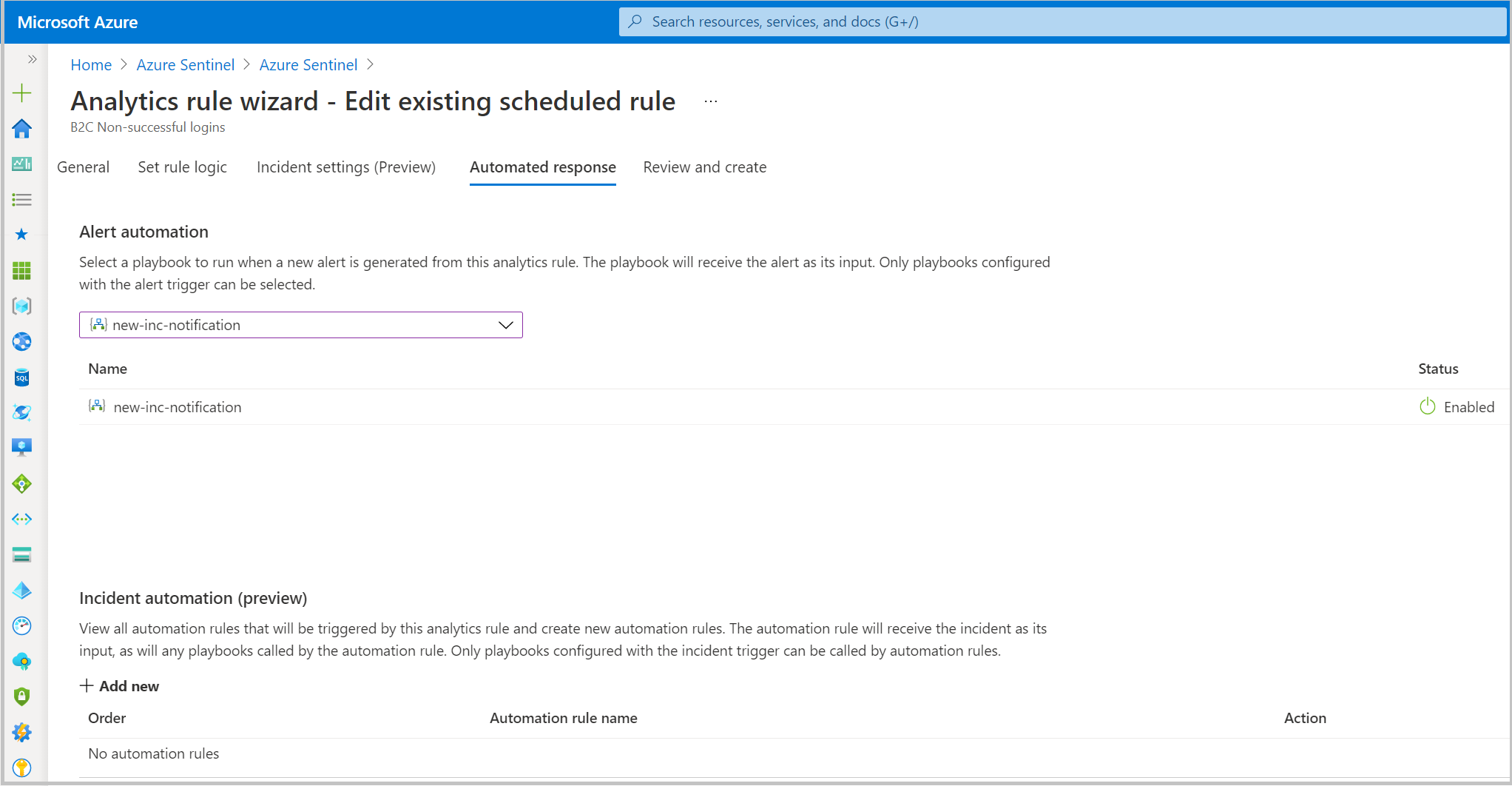
- Go to a configured playbook.
- Edit the rule.
- On the Automated response tab, select the playbook.
Learn more: Incident-Email-Notification
Resources
For more information about Microsoft Sentinel and Azure AD B2C, see: