Quickstart: Create a Linux server VM by using PowerShell in Azure Stack Hub
You can create an Ubuntu Server 20.04 LTS virtual machine (VM) by using Azure Stack Hub PowerShell. In this article, you create and use a virtual machine. This article also shows you how to:
- Connect to the VM with a remote client.
- Install an NGINX web server and view the default home page.
- Clean up unused resources.
Prerequisites
A Linux image in the Azure Stack Hub Marketplace. The Azure Stack Hub Marketplace doesn't have a Linux image by default. Have the Azure Stack Hub operator provide the Ubuntu Server 20.04 LTS image you need. The operator can use the instructions in Download Marketplace items from Azure to Azure Stack Hub.
Azure Stack Hub requires a specific version of the Azure CLI to create and manage its resources.
- If you don't have PowerShell configured for Azure Stack Hub, see Install PowerShell for Azure Stack Hub.
- After Azure Stack Hub PowerShell is set up, you'll connect to your Azure Stack Hub environment. For instructions, see Connect to Azure Stack Hub with PowerShell as a user.
A public Secure Shell (SSH) key with the name id_rsa.pub saved in the .ssh directory of your Windows user profile. For detailed information about creating SSH keys, see Use an SSH key pair with Azure Stack Hub.
Create a resource group
A resource group is a logical container where you can deploy and manage Azure Stack Hub resources. To create a resource group, run the following code block:
Note
We've assigned values for all variables in the following code examples. However, you can assign your own values.
# Create variables to store the location and resource group names.
$location = "local"
$ResourceGroupName = "myResourceGroup"
New-AzResourceGroup `
-Name $ResourceGroupName `
-Location $location
Create storage resources
Create a storage account that will be used for storing the boot diagnostics output.
# Create variables to store the storage account name and the storage account SKU information
$StorageAccountName = "mystorageaccount"
$SkuName = "Standard_LRS"
# Create a new storage account
$StorageAccount = New-AzStorageAccount `
-Location $location `
-ResourceGroupName $ResourceGroupName `
-Type $SkuName `
-Name $StorageAccountName
Set-AzCurrentStorageAccount `
-StorageAccountName $storageAccountName `
-ResourceGroupName $resourceGroupName
Create networking resources
Create a virtual network, a subnet, and a public IP address. These resources are used to provide network connectivity to the VM.
# Create a subnet configuration
$subnetConfig = New-AzVirtualNetworkSubnetConfig `
-Name mySubnet `
-AddressPrefix 192.168.1.0/24
# Create a virtual network
$vnet = New-AzVirtualNetwork `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-Name MyVnet `
-AddressPrefix 192.168.0.0/16 `
-Subnet $subnetConfig
# Create a public IP address and specify a DNS name
$pip = New-AzPublicIpAddress `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-AllocationMethod Static `
-IdleTimeoutInMinutes 4 `
-Name "mypublicdns$(Get-Random)"
Create a network security group and a network security group rule
The network security group secures the VM by using inbound and outbound rules. Create an inbound rule for port 3389 to allow incoming Remote Desktop connections and an inbound rule for port 80 to allow incoming web traffic.
# Create variables to store the network security group and rules names.
$nsgName = "myNetworkSecurityGroup"
$nsgRuleSSHName = "myNetworkSecurityGroupRuleSSH"
$nsgRuleWebName = "myNetworkSecurityGroupRuleWeb"
# Create an inbound network security group rule for port 22
$nsgRuleSSH = New-AzNetworkSecurityRuleConfig -Name $nsgRuleSSHName -Protocol Tcp `
-Direction Inbound -Priority 1000 -SourceAddressPrefix * -SourcePortRange * -DestinationAddressPrefix * `
-DestinationPortRange 22 -Access Allow
# Create an inbound network security group rule for port 80
$nsgRuleWeb = New-AzNetworkSecurityRuleConfig -Name $nsgRuleWebName -Protocol Tcp `
-Direction Inbound -Priority 1001 -SourceAddressPrefix * -SourcePortRange * -DestinationAddressPrefix * `
-DestinationPortRange 80 -Access Allow
# Create a network security group
$nsg = New-AzNetworkSecurityGroup -ResourceGroupName $ResourceGroupName -Location $location `
-Name $nsgName -SecurityRules $nsgRuleSSH,$nsgRuleWeb
Create a network card for the VM
The network card connects the VM to a subnet, network security group, and public IP address.
# Create a virtual network card and associate it with public IP address and NSG
$nic = New-AzNetworkInterface `
-Name myNic `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-SubnetId $vnet.Subnets[0].Id `
-PublicIpAddressId $pip.Id `
-NetworkSecurityGroupId $nsg.Id
Create a VM
Create a VM configuration. This configuration includes the settings to use when you deploy the VM (for example, user credentials, size, and the VM image).
# Define a credential object
$UserName='demouser'
$securePassword = ConvertTo-SecureString ' ' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ($UserName, $securePassword)
# Create the VM configuration object
$VmName = "VirtualMachinelatest"
$VmSize = "Standard_D1"
$VirtualMachine = New-AzVMConfig `
-VMName $VmName `
-VMSize $VmSize
$VirtualMachine = Set-AzVMOperatingSystem `
-VM $VirtualMachine `
-Linux `
-ComputerName "MainComputer" `
-Credential $cred
$VirtualMachine = Set-AzVMSourceImage `
-VM $VirtualMachine `
-PublisherName "Canonical" `
-Offer "UbuntuServer" `
-Skus "20.04-LTS" `
-Version "latest"
# Set the operating system disk properties on a VM
$VirtualMachine = Set-AzVMOSDisk `
-VM $VirtualMachine `
-CreateOption FromImage | `
Set-AzVMBootDiagnostic -ResourceGroupName $ResourceGroupName `
-StorageAccountName $StorageAccountName -Enable |`
Add-AzVMNetworkInterface -Id $nic.Id
# Configure SSH keys
$sshPublicKey = Get-Content "$env:USERPROFILE\.ssh\id_rsa.pub"
# Add the SSH key to the VM
Add-AzVMSshPublicKey -VM $VirtualMachine `
-KeyData $sshPublicKey `
-Path "/home/$UserName/.ssh/authorized_keys"
# Create the VM
New-AzVM `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-VM $VirtualMachine
VM Quick Create: Full script
Note
This step is essentially the preceding code merged together, but with a password rather than an SSH key for authentication.
## Create a resource group
<#
A resource group is a logical container where you can deploy and manage Azure Stack Hub resources. From your development kit or the Azure Stack Hub integrated system, run the following code block to create a resource group. Though we've assigned values for all the variables in this article, you can use these values or assign new ones.
#>
# Edit your variables, if required
# Create variables to store the location and resource group names
$location = "local"
$ResourceGroupName = "myResourceGroup"
# Create variables to store the storage account name and the storage account SKU information
$StorageAccountName = "mystorageaccount"
$SkuName = "Standard_LRS"
# Create variables to store the network security group and rules names
$nsgName = "myNetworkSecurityGroup"
$nsgRuleSSHName = "myNetworkSecurityGroupRuleSSH"
$nsgRuleWebName = "myNetworkSecurityGroupRuleWeb"
# Create variable for VM password
$VMPassword = 'Password123!'
# End of variables - no need to edit anything past that point to deploy a single VM
# Create a resource group
New-AzResourceGroup `
-Name $ResourceGroupName `
-Location $location
## Create storage resources
# Create a storage account, and then create a storage container for the Ubuntu Server 20.04 LTS image
# Create a new storage account
$StorageAccount = New-AzStorageAccount `
-Location $location `
-ResourceGroupName $ResourceGroupName `
-Type $SkuName `
-Name $StorageAccountName
Set-AzCurrentStorageAccount `
-StorageAccountName $storageAccountName `
-ResourceGroupName $resourceGroupName
# Create a storage container to store the VM image
$containerName = 'osdisks'
$container = New-AzureStorageContainer `
-Name $containerName `
-Permission Blob
## Create networking resources
# Create a virtual network, a subnet, and a public IP address, resources that are used provide network connectivity to the VM
# Create a subnet configuration
$subnetConfig = New-AzVirtualNetworkSubnetConfig `
-Name mySubnet `
-AddressPrefix 192.168.1.0/24
# Create a virtual network
$vnet = New-AzVirtualNetwork `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-Name MyVnet `
-AddressPrefix 192.168.0.0/16 `
-Subnet $subnetConfig
# Create a public IP address and specify a DNS name
$pip = New-AzPublicIpAddress `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-AllocationMethod Static `
-IdleTimeoutInMinutes 4 `
-Name "mypublicdns$(Get-Random)"
### Create a network security group and a network security group rule
<#
The network security group secures the VM by using inbound and outbound rules. Create an inbound rule for port 3389 to allow incoming Remote Desktop connections and an inbound rule for port 80 to allow incoming web traffic.
#>
# Create an inbound network security group rule for port 22
$nsgRuleSSH = New-AzNetworkSecurityRuleConfig -Name $nsgRuleSSHName -Protocol Tcp `
-Direction Inbound -Priority 1000 -SourceAddressPrefix * -SourcePortRange * -DestinationAddressPrefix * `
-DestinationPortRange 22 -Access Allow
# Create an inbound network security group rule for port 80
$nsgRuleWeb = New-AzNetworkSecurityRuleConfig -Name $nsgRuleWebName -Protocol Tcp `
-Direction Inbound -Priority 1001 -SourceAddressPrefix * -SourcePortRange * -DestinationAddressPrefix * `
-DestinationPortRange 80 -Access Allow
# Create a network security group
$nsg = New-AzNetworkSecurityGroup -ResourceGroupName $ResourceGroupName -Location $location `
-Name $nsgName -SecurityRules $nsgRuleSSH,$nsgRuleWeb
### Create a network card for the VM
# The network card connects the VM to a subnet, network security group, and public IP address.
# Create a virtual network card and associate it with public IP address and NSG
$nic = New-AzNetworkInterface `
-Name myNic `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-SubnetId $vnet.Subnets[0].Id `
-PublicIpAddressId $pip.Id `
-NetworkSecurityGroupId $nsg.Id
## Create a VM
<#
Create a VM configuration. This configuration includes the settings used when deploying the VM. For example: user credentials, size, and the VM image.
#>
# Define a credential object
$UserName='demouser'
$securePassword = ConvertTo-SecureString $VMPassword -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ($UserName, $securePassword)
# Create the VM configuration object
$VmName = "VirtualMachinelatest"
$VmSize = "Standard_D1"
$VirtualMachine = New-AzVMConfig `
-VMName $VmName `
-VMSize $VmSize
$VirtualMachine = Set-AzVMOperatingSystem `
-VM $VirtualMachine `
-Linux `
-ComputerName "MainComputer" `
-Credential $cred
$VirtualMachine = Set-AzVMSourceImage `
-VM $VirtualMachine `
-PublisherName "Canonical" `
-Offer "UbuntuServer" `
-Skus "20.04-LTS" `
-Version "latest"
$osDiskName = "OsDisk"
$osDiskUri = '{0}vhds/{1}-{2}.vhd' -f `
$StorageAccount.PrimaryEndpoints.Blob.ToString(),`
$vmName.ToLower(), `
$osDiskName
# Set the operating system disk properties on a VM
$VirtualMachine = Set-AzVMOSDisk `
-VM $VirtualMachine `
-Name $osDiskName `
-VhdUri $OsDiskUri `
-CreateOption FromImage | `
Add-AzVMNetworkInterface -Id $nic.Id
# Create the VM
New-AzVM `
-ResourceGroupName $ResourceGroupName `
-Location $location `
-VM $VirtualMachine
Connect to the VM
After you've deployed the VM, configure an SSH connection for it. To get the public IP address of the VM, use the Get-AzPublicIpAddress command:
Get-AzPublicIpAddress -ResourceGroupName myResourceGroup | Select IpAddress
From a client system with SSH installed, use the following command to connect to the VM. If you're working on Windows, you can use PuTTY to create the connection.
ssh <Public IP Address>
When you're prompted, sign in as azureuser. If you used a passphrase when you created the SSH keys, you'll have to provide the passphrase.
Install the NGINX web server
To update package resources and install the latest NGINX package, run the following script:
#!/bin/bash
# update package source
apt-get -y update
# install NGINX
apt-get -y install nginx
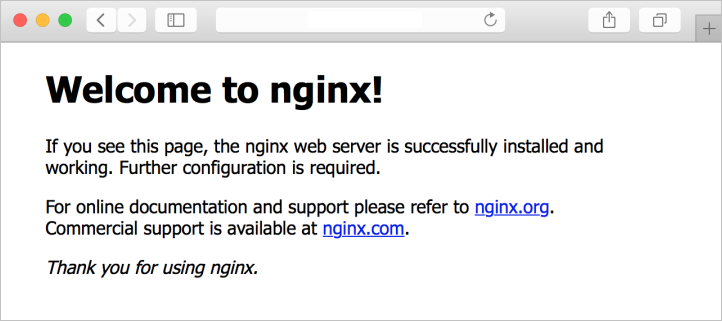
View the NGINX welcome page
With the NGINX web server installed, and port 80 open on your VM, you can access the web server by using the VM's public IP address. Open a web browser, and go to http://<public IP address>.
Clean up resources
You can clean up the resources that you don't need any longer by using the Remove-AzResourceGroup command. To delete the resource group and all its resources, run the following command:
Remove-AzResourceGroup -Name myResourceGroup
Next steps
In this quickstart, you deployed a basic Linux server VM. To learn more about Azure Stack Hub VMs, go to Considerations for VMs in Azure Stack Hub.