Configure deployment sources for App Services on Azure Stack Hub
App Service on Azure Stack Hub supports on-demand deployment from multiple source control providers. This feature lets app developers deploy directly from their source control repositories. If users want to configure App Service to connect to their repositories, a cloud operator must first configure the integration between App Service on Azure Stack Hub and the source control provider.
In addition to local Git, the following source control providers are supported:
- GitHub
- BitBucket
- OneDrive
- DropBox
View deployment sources in App Service administration
Sign in to the Azure Stack Hub administrator portal as the service admin.
Browse to All Services and select the App Service.
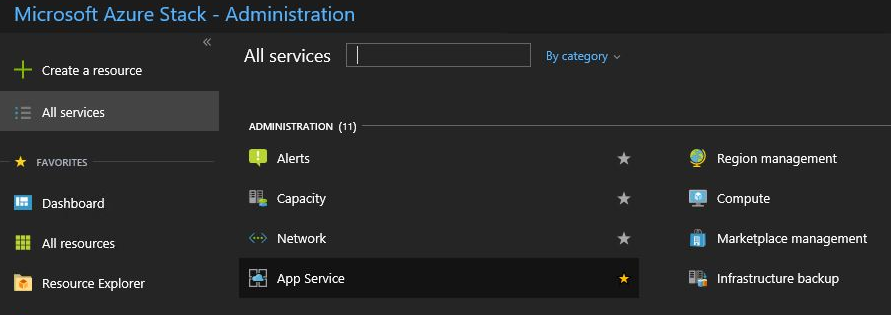
Select Source control configuration. You can see the list of all configured deployment sources.
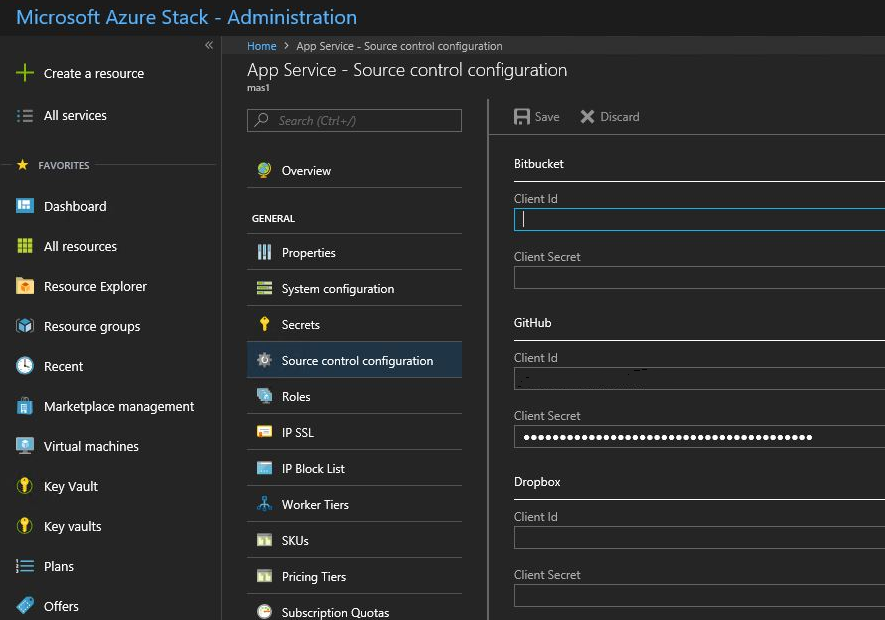
Configure GitHub
You must have a GitHub account to complete this task. You might want to use an account for your organization rather than a personal account.
Sign in to GitHub, go to https://www.github.com/settings/developers, and then select Register a new application.
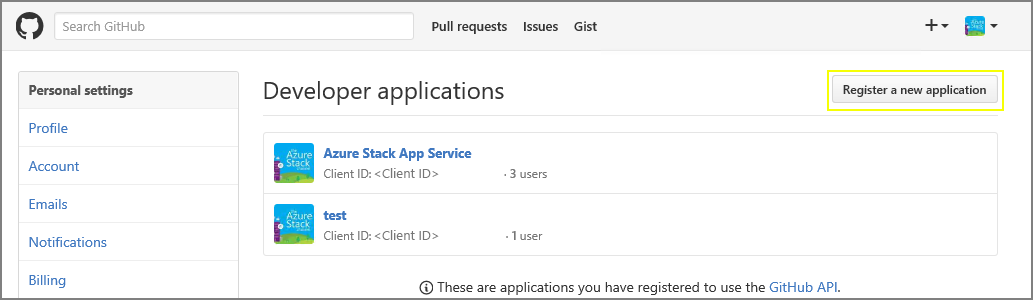
Enter an Application name. For example, App Service on Azure Stack Hub.
Enter the Homepage URL. The Homepage URL must be the Azure Stack Hub portal address. For example,
https://portal.<region>.<FQDN>. For more information on the Azure Stack Hub fully qualified domain name (FQDN), see Azure Stack Hub DNS namespace.Enter an Application Description.
Enter the Authorization callback URL. In a default Azure Stack Hub deployment, the URL is in the form
https://portal.<region>.<FQDN>/TokenAuthorize.Select Register application. A page is displayed listing the Client ID and Client Secret for the app.
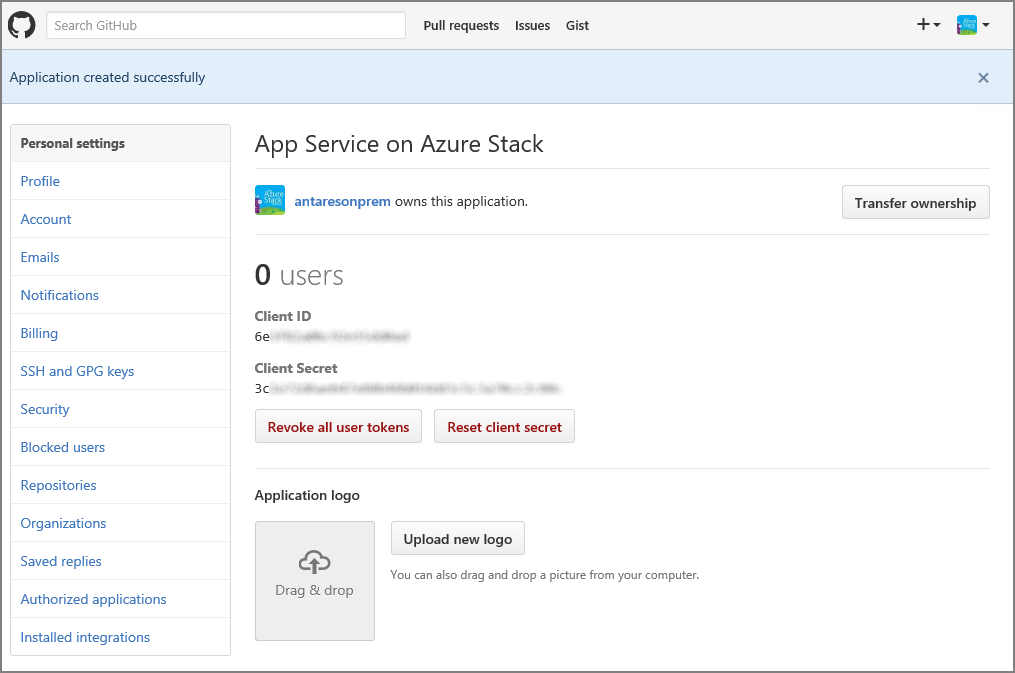
In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Client ID and Client Secret into the corresponding input boxes for GitHub.
Select Save.
Configure BitBucket
You must have a BitBucket account to complete this task. You might want to use an account for your organization rather than a personal account.
Sign in to BitBucket and go to Integrations under your account.
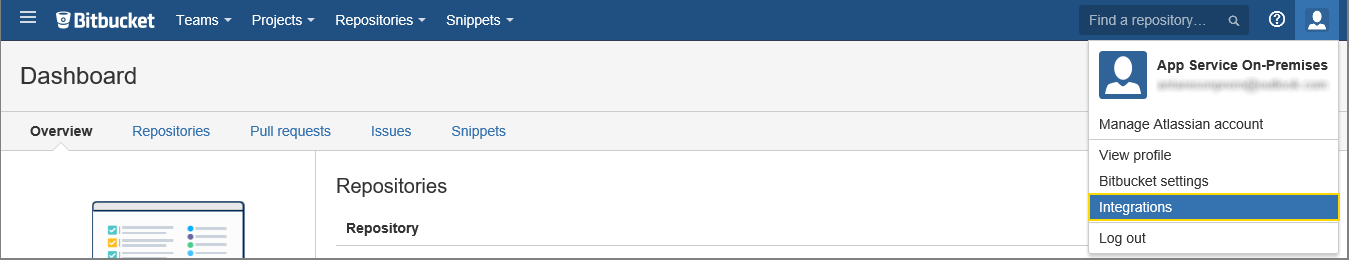
Select OAuth under Access Management and Add consumer.
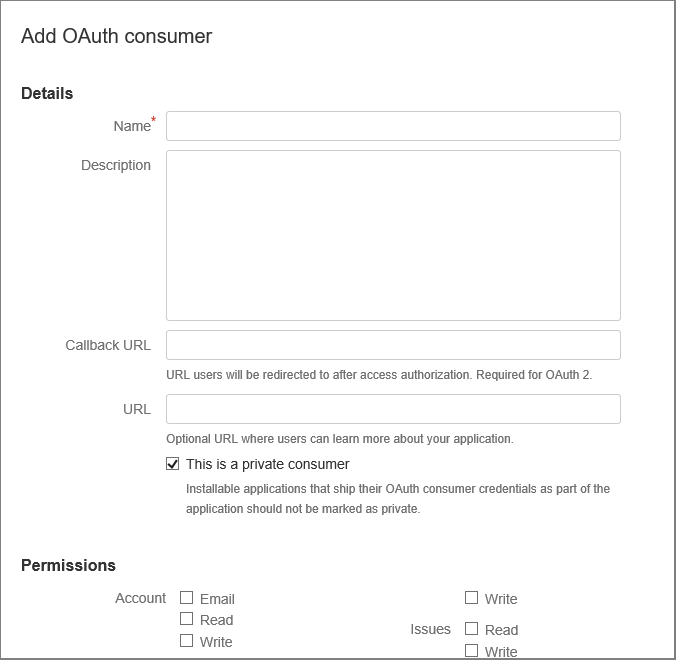
Enter a Name for the consumer. For example, App Service on Azure Stack Hub.
Enter a Description for the app.
Enter the Callback URL. In a default Azure Stack Hub deployment, the callback URL is in the form
https://portal.<region>.<FQDN>/TokenAuthorize. For BitBucket integration to succeed, the URL must follow the capitalization listed here.Enter the URL. This URL should be the Azure Stack Hub portal URL. For example,
https://portal.<region>.<FQDN>.Select the Permissions required:
- Repositories: Read
- Webhooks: Read and write
Select Save. You now see this new app, along with the Key and Secret, under OAuth consumers.
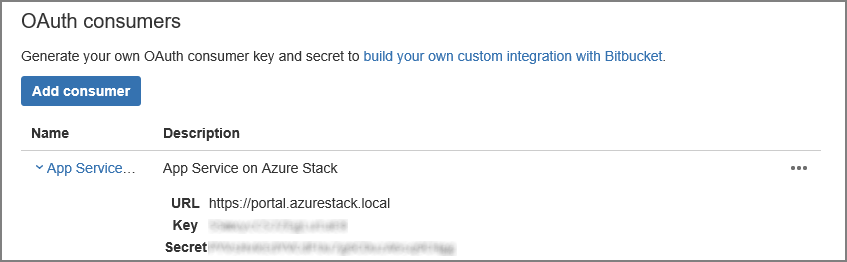
In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Key into the Client ID input box and Secret into the Client Secret input box for BitBucket.
Select Save.
Configure OneDrive
You must have a Microsoft account linked to a OneDrive account to complete this task. You might want to use an account for your organization rather than a personal account.
Note
OneDrive for business accounts are currently not supported.
Go to https://portal.azure.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade and sign in using your Microsoft account.
Under App registrations, select New registration.
Enter a Name for the new app registration: for example, enter App Service on Azure Stack Hub.
Under Supported account types, select Personal Microsoft accounts only.
Enter the Redirect URI. Choose platform - Web and in a default Azure Stack Hub deployment, the redirect URI is in the form -
https://portal.<region>.<FQDN>/TokenAuthorize.Select Register.
The next screen lists the properties of your new app. Save the Application (client) ID to a temporary location.
Under Certificates & secrets, choose Client Secrets and select New client secret. Provide a description and choose the expiration length for the new secret and select Add.
Make a note of the value of the new secret.
Under API Permissions, select Add a permission.
Add the Microsoft Graph Permissions - Delegated Permissions.
- Files.ReadWrite.AppFolder
- User. Read
In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Application (client) ID into the Client ID input box and Secret into the Client Secret input box for OneDrive.
Select Save.
Configure DropBox
Note
You must have a DropBox account to complete this task. You might want to use an account for your organization rather than a personal account.
Go to https://www.dropbox.com/developers/apps and sign in using your DropBox account credentials.
Select Create app.

Select DropBox API.
Set the access level to App Folder.
Enter a Name for your app.
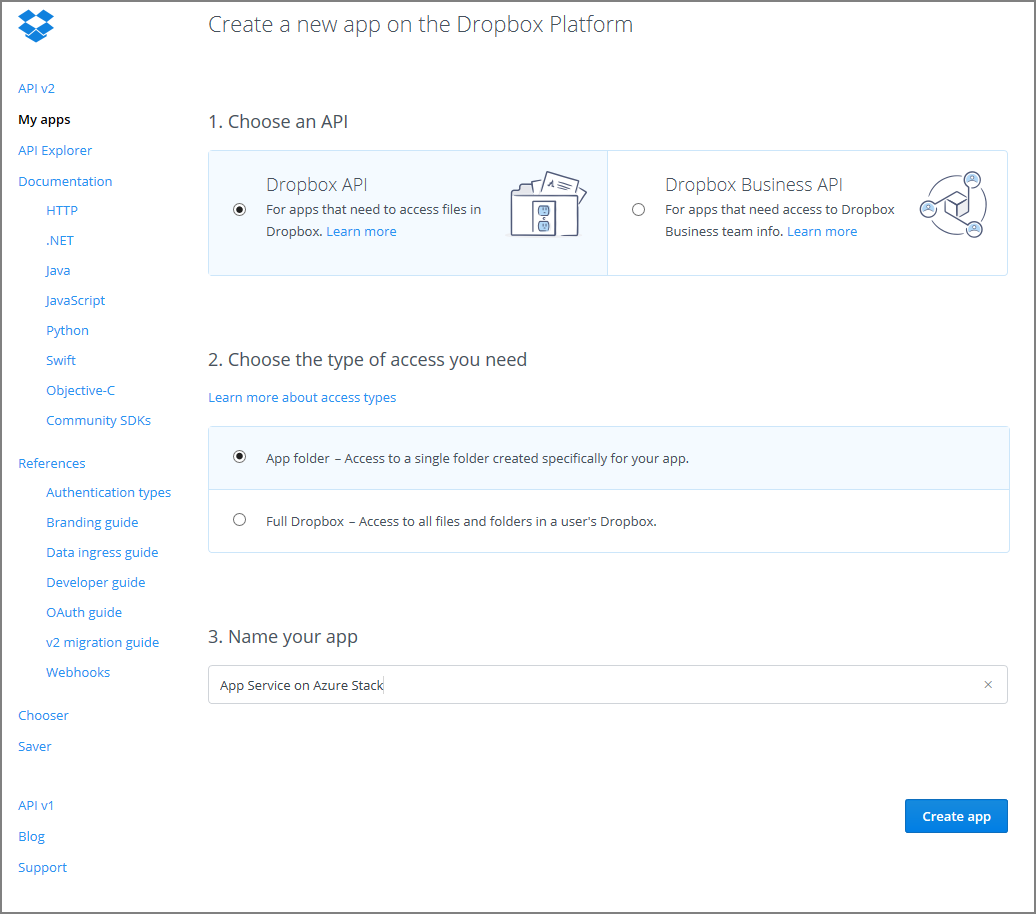
Select Create App. You're presented with a page listing the settings for the app, including App key and App secret.
Make sure that the App folder name is set to App Service on Azure Stack Hub.
Set the OAuth 2 Redirect URI and then select Add. In a default Azure Stack Hub deployment, the redirect URI is in the form
https://portal.<region>.<FQDN>/TokenAuthorize.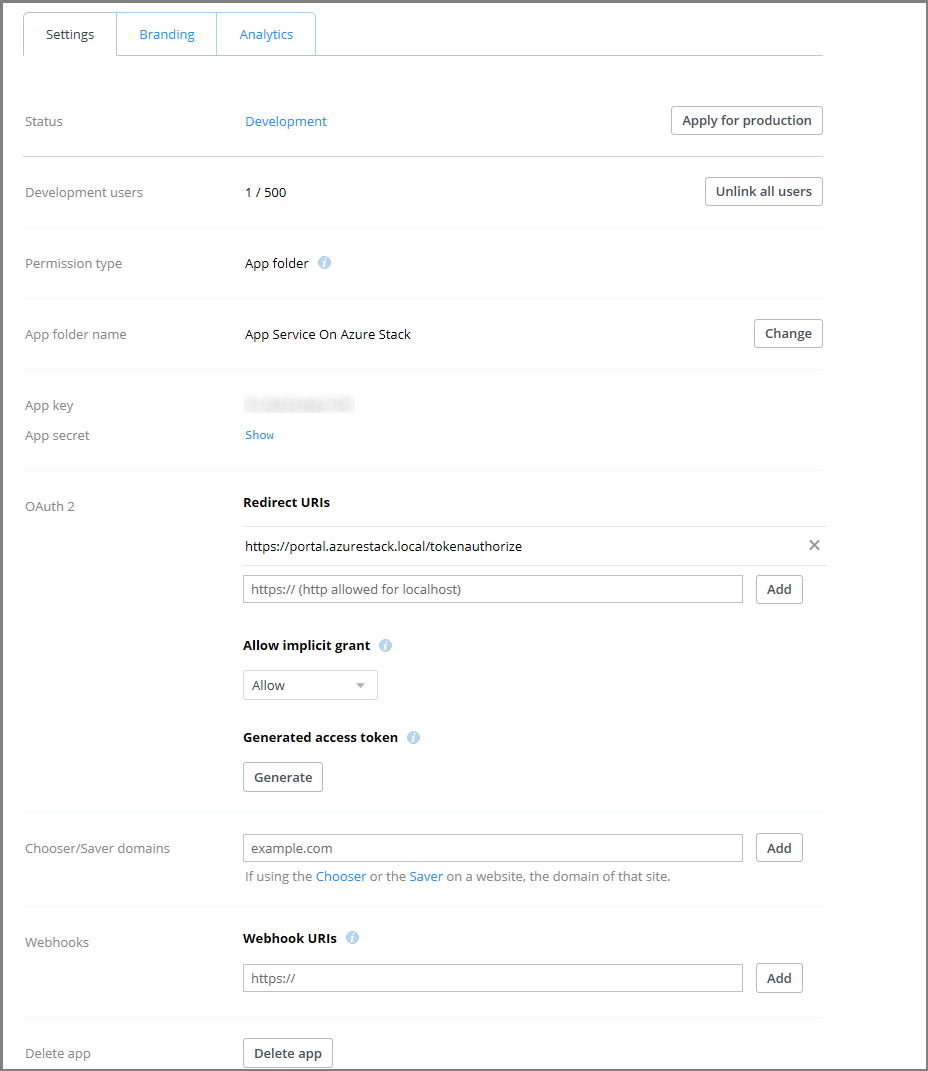
In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Application Key into the Client ID input box and App secret into the Client Secret input box for DropBox.
Select Save.
Important
If you are reconfiguring existing applications after upgrading to Azure App Service on Azure Stack Hub 2022 H1 you must revoke all tokens and your end users will need to reauthorize with the providers on their applications to enable synchronisation from source control providers
Configure GitHub
You must have a GitHub account to complete this task. You might want to use an account for your organization rather than a personal account.
Sign in to GitHub, go to https://www.github.com/settings/developers, and then select Register a new application.

Enter an Application name. For example, App Service on Azure Stack Hub.
Enter the Homepage URL. The Homepage URL must be the Azure Stack Hub portal address. For example,
https://portal.<region>.<FQDN>. For more information on the Azure Stack Hub fully qualified domain name (FQDN), see Azure Stack Hub DNS namespace.Enter an Application Description.
Enter the Authorization callback URL. In a default Azure Stack Hub deployment, the URL is in the form
https://api.appservice.<region>.<FQDN>:44300/auth/github/callback.Select Register application. A page is displayed listing the Client ID and Client Secret for the app.

In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Client ID and Client Secret into the corresponding input boxes for GitHub.
Select Save.
Configure BitBucket
You must have a BitBucket account to complete this task. You might want to use an account for your organization rather than a personal account.
Sign in to BitBucket and go to Integrations under your account.

Select OAuth under Access Management and Add consumer.

Enter a Name for the consumer. For example, App Service on Azure Stack Hub.
Enter a Description for the app.
Enter the Callback URL. In a default Azure Stack Hub deployment, the callback URL is in the form
https://api.appservice.<region>.<FQDN>:44300/auth/bitbucket/callback. For BitBucket integration to succeed, the URL must follow the capitalization listed here.Enter the URL. This URL should be the Azure Stack Hub portal URL. For example,
https://portal.<region>.<FQDN>.Select the Permissions required:
- Repositories: Read
- Webhooks: Read and write
Select Save. You now see this new app, along with the Key and Secret, under OAuth consumers.

In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Key into the Client ID input box and Secret into the Client Secret input box for BitBucket.
Select Save.
Configure OneDrive
You must have a Microsoft account linked to a OneDrive account to complete this task. You might want to use an account for your organization rather than a personal account.
Note
OneDrive for business accounts are currently not supported.
Go to https://portal.azure.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade and sign in using your Microsoft account.
Under App registrations, select New registration.
Enter a Name for the new app registration: for example, enter App Service on Azure Stack Hub.
Under Supported account types, select Personal Microsoft accounts only
Enter the Redirect URI. Choose platform - Web and in a default Azure Stack Hub deployment, the redirect URI is in the form -
https://api.appservice.<region>.<FQDN>:44300/auth/onedrive/callback.Select Register
The next screen lists the properties of your new app. Save the Application (client) ID to a temporary location.
Under Certificates & secrets, choose Client Secrets and select New client secret. Provide a description and choose the expiration length for the new secret and select Add.
Make a note of the value of the new secret.
Under API Permissions, select Add a permission
Add the Microsoft Graph Permissions - Delegated Permissions.
- Files.ReadWrite.AppFolder
- User. Read
In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Application (client) ID into the Client ID input box and Secret into the Client Secret input box for OneDrive.
Select Save.
Configure DropBox
Note
You must have a DropBox account to complete this task. You might want to use an account for your organization rather than a personal account.
Go to https://www.dropbox.com/developers/apps and sign in using your DropBox account credentials.
Select Create app.

Select DropBox API.
Set the access level to App Folder.
Enter a Name for your app.

Select Create App. You're presented with a page listing the settings for the app, including App key and App secret.
Make sure that the App folder name is set to App Service on Azure Stack Hub.
Set the OAuth 2 Redirect URI and then select Add. In a default Azure Stack Hub deployment, the redirect URI is in the form
https://api.appservice.<region>.<FQDN>:44300/auth/dropbox/callback.
In a new browser tab or window, sign in to the Azure Stack Hub administrator portal as the service admin.
Go to Resource Providers and select the App Service Resource Provider Admin.
Select Source control configuration.
Copy and paste the Application Key into the Client ID input box and App secret into the Client Secret input box for DropBox.
Select Save.
Next steps
Users can now use the deployment sources for things like continuous deployment, local Git deployment, and cloud folder synchronization.