Cryptography: From ancient science to Win7 and Bing!
Microsoft is continuing to improve the science of cryptography. There are a number of approaches to cryptography and its application to securing the identity of people, data and systems.
Historically, the first codes were used by the Spartans, by wrapping a piece of paper around a stick and writing the message and then taking the paper off in a spiral manner. It could only be read if you used the same diameter stick. In some ways this is similar to current methods.
Later, the playwright Francis Bacon wrote about encryption in his Advancement of Learning, The Sixth Book, Chapter I.:
“But the virtues of them whereby they are to be preferr'd are Three; That they be ready, and not laborious to write; That they be sure, and lie not open to Deciphering; And lastly, if it be possible, that they may be managed without suspition [sic].”
This is a fair definition of the modern science of cryptography, during World War II, encryption systems on both sides of the war were broken, mainly through poor discipline. The operators would not change keys at the correct time, send key information unencrypted, and use old map grids that would reveal information, etc.
Currently cryptography is supported inside of the Windows CLR via a
Cryptography is the use of codes to convert data so that only a specific recipient will be able to read it, using a key.
Cryptography is the use of codes to convert data so that only a specific recipient will be able to read it, using a key.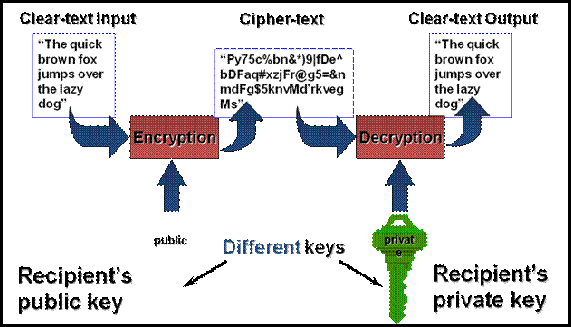
Windows 2008, Vista and Win7 use the latest versions of cryptography, and this isn’t just utilization of more codes and a slight modification of the first generation processes like RSA. What is the process used in the cryptography API?
Starting around 2006, Microsoft will support the Crypto API, but will utilize more advance processes such as Elliptic Curve Cryptography through the Cryptography Next Generation (CNG) in all systems like Win7.
I am digging into these “new” ways of doing cryptography, especially the elliptic curve approach. But if you don’t really care how the cryptographic engine runs, just that it does run, you will need to dig into the Crypto Next Generation, if you haven’t already.
I also have found an article titled: “On Parallelization of High-Speed Processors for
Elliptic Curve Cryptography” on the IEEE Digital Library, it gives a good overview of how the Elliptic Curve Cryptography works. Interesting enough, it really is an excellent review of your basic algebra and a few simple use of matrix.
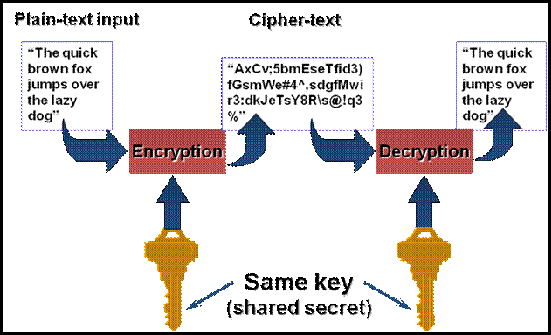
A little background, the top figure is the cryptographic process called Symmetric keys work.
The lower image is Public Key Encryption which many people think is the current crypto systems in use, this is hopefully the legacy system and most systems are switching to CNG
There are no images, right now, of how elliptic curve encryption, decryption works.
In conclusion, if you are building or upgrading existing systems you need to consider the CNG cryptography systems.
Comments
- Anonymous
June 10, 2009
The top figure is Public Key Encryption The lower image is the cryptographic process called Symmetric keys work. --rc