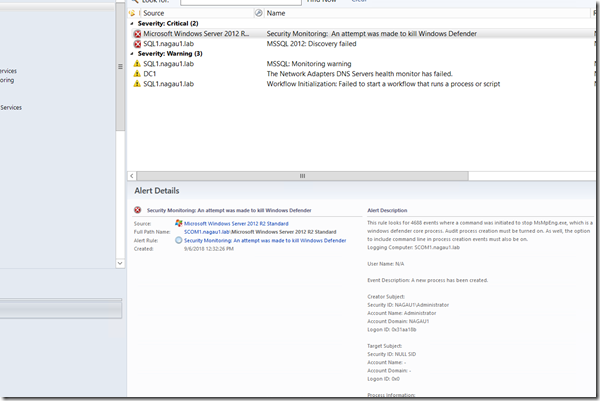
Security Monitoring–Configuring SCOM to alert on attempts to kill Windows Defender
Disclaimer: Due to changes in the MSFT corporate
blogging policy, I’m moving all of my content to the following location. Please reference all future content from that
location. Thanks.
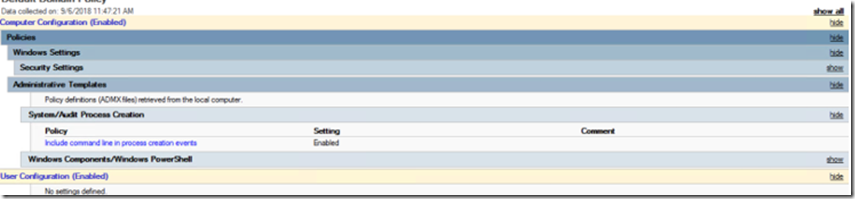
This is just a quick update to the next revision of Security Monitoring. If you don’t use Windows Defender, this will not generate any alerts, and in general it should be quiet even if you do use Window Defender. This will only work if you have the audit process creation GPO set. I’d also note, that you need to have command line auditing turned on as well. I’ve referenced that in other places, but here’s a screenshot if you’re unsure:
If these are set, there is now a new rule that will look for 4688 events with various kill switches meant to stop that process. This alert will also be available if you’re using Windows Event Collectors.