ASP.NET Security Scenarios on Azure
As part of our patterns & practices Azure Security Guidance project, we’re putting together a series of Application Scenarios and Solutions. Our goal is to show the most common application scenarios on the Microsoft Azure platform. This is your chance to give us feedback on whether we have the right scenarios, and whether you agree with the baseline solution.
ASP.NET Security Scenarios on Windows Azure
We’re taking a crawl, walk, run approach and starting with the basic scenarios first. This is our application scenario set for ASP.NET:
- ASP.NET Forms Auth to Azure Storage
- ASP.NET Forms Auth to SQL Azure
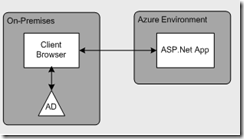
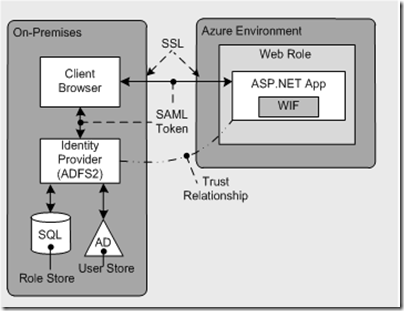
- ASP.NET to AD with Claims
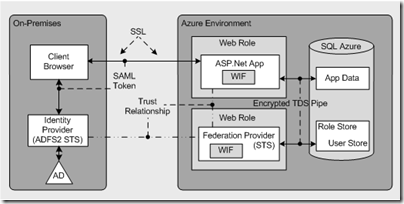
- ASP.NET to AD with Claims (Federation)
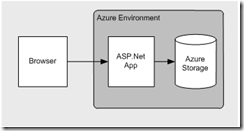
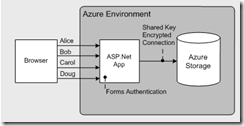
ASP.NET Forms Auth to Azure Storage
Scenario
Solution
Solution Summary Table
| Area | Notes |
|---|---|
| Authentication |
|
| Authorization |
|
| Communication |
|
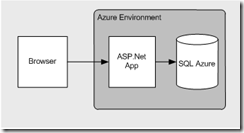
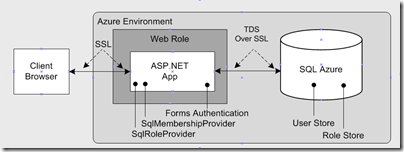
ASP.NET Forms Authentication to SQL Azure
Scenario
Solution
Solution Summary Table
| Area | Notes |
|---|---|
| Authentication |
|
| Authorization |
|
| Communication |
|
ASP.NET to AD with Claims
Scenario
Solution
Solution Summary Table
| Area | Notes |
|---|---|
| Authentication |
|
| Authorization |
|
| Communication |
|
ASP.NET to AD with Claims (Federation)
Scenario
Solution
Solution Summary Table
| Area | Notes |
|---|---|
| Authentication |
|
| Authorization |
|
| Communication |
|
Comments
Anonymous
May 12, 2010
JD this is great. One of the big concerns we hear from customers about moving to cloud computing in general is security and privacy etc. I think providiing this kind of guidance will help customers get more comfortable with the idea and get them further along the path.Anonymous
May 12, 2010
I agree with Rudolph this is much needed material for guidance around transitioning to and leveraging the cloud. 99.9% of the time I always hear about security being the largest barrier to entry to taking the first steps into the cloud. I believe this guidance from Microsoft and the well-known and respected P&P team will do volumes to remove this barrier. Of special importance to me given my role is the "ASP.NET to AD with Claims" model that enterprise solutions will almost certainly need and adhere to and much guidance is needed. Thanks for identifying this area and addressing it is an important one if Microsoft to tackle in order to promote Azure and stay ahead of the curve. I look forward to the blue book version!Anonymous
May 12, 2010
Using Azure introduces several new secrets (for connecting to Azure storage, SQL Azure etc). Prescriptive guidance on how to manage these secrets and store them securely is going to be very important. Looking forward to this guidance!Anonymous
May 13, 2010
Finally! This kind of guidance has been needed for a long time, looking forward to it.Anonymous
May 13, 2010
Thanks for posting this JD. Scenario-based guidance is the secret sauce that will help us and our customers build secure Azure apps. I'm really looking forward to seeing more. For instance when is each of these scenarios appropriate and under which conditions or constraints?Anonymous
May 14, 2010
The comment has been removedAnonymous
May 16, 2010
All these scenarios literally useless without detailed instructions on how to make them work. Don't post if you are not giving detailed instructions, it is causes confusion.Anonymous
May 16, 2010
@ john -- What specifically do you need instructions for? (we've covered step-by-steps before so give me a concrete example where you need help) Can you share an example of how you're confused?