Managing the "Launching Applications and Unsafe Files" Setting
Tuesday, November 27, 2007 6:30 AM
We are often asked about the centralized management of Internet Explorer configuration options for which there are no Group Policy settings included with the default IE GPO templates. One of the settings that we are asked about the most is the "Launching Applications and Unsafe Files" setting, since that setting is not defined in the IE Administrative Policy settings file (inetres.adm).
There are a number of different ways that you can manage this setting in an enterprise. The first is to use the Internet Explorer Maintenance Policies, which import from a source system's registry. The problem with this approach is that there is no granularity in what settings you are importing - it's an all or nothing solution, and you wind up deploying the entire collection of IE settings that are defined on the source system.
The second method to deploy this setting is to use a logon / startup script to deploy and modify the registry setting. This is perhaps the easiest method to deploy the setting. The registry key that controls this Internet Explorer security zone setting is stored under the following registry subkeys:
- User Policy: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones
- Computer Policy: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones
By default, security zones settings are stored in the HKEY_CURRENT_USER registry subtree. Because this subtree is dynamically loaded for each user, changing the settings for one user does not affect the settings for another user on the same machine. If computer policy is configured, only the local computer settings are used and all users have the same security settings. In that case the settings are retrieved from the HKEY_LOCAL_MACHINE tree as listed above.
The Zones key contains keys that represent each security zone defined for the computer. By default, the following five zones are defined:
Value Zone Name
0 My Computer
1 Local Intranet
2 Trusted Sites
3 Internet
4 Restricted Sites
Under each of these Zones, there are different values that represent the individual settings. The value 1806 represents the setting for "Launching Applications and Unsafe Files". The value data for 1806 represents the corresponding settings on the Custom Security Tab. The permissible values are shown below:
Value Setting
0 Sets a specific action as Permitted
1 Causes a prompt to appear
3 Prohibits the specific action
As you can see, using a login script to deploy the setting is not terribly complicated. However, the concern with login scripts is that they tend to grow over time, and maintaining a change history becomes increasingly important especially with login scripts that contain multiple settings, nested logic based on group membership etc.
This third method that we can use to manage this setting is to create a custom ADM template and manage this setting via Group Policy. ADM files are template files that are used by Group Policies to describe where registry-based policy settings are stored in the registry. ADM files also describe the user interface that administrators see in the Group Policy Object Editor snap-in. Group Policy Object Editor is used by administrators when they create or modify Group Policy objects (GPO's). There are a standard set of ADM files included with the operating system that are loaded by the Group Policy Editor. For example, Windows Server 2003 includes the following ADM files:
- System.adm
- Inetres.adm
- Conf.adm
- WMPlayer.adm
- WUAU.adm
We're not going to get into the nuts and bolts of creating custom ADM files in this post. There's a detailed document regarding the creation of custom ADM files available from the Microsoft site. Once you have your ADM file created, the first thing you have to do is import it into Group Policy Editor. We've included a SAMPLE ADM file to manage the "Launching Applications and Unsafe Files" setting as a text file (see the attachment at the end of this post). Rename this file with a .ADM extension and save it to your system. Please note that the standard Script Disclaimer listed below applies to this sample template.
**** SCRIPT DISCLAIMER****
The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages
Open Group Policy Editor and navigate to the OU or Domain Policy you want to Edit
Navigate to the Administrative Templates option under the User Configuration or Computer Configuration as applicable
Right-click on Administrative Templates and click on Add/Remove Templates as shown below:
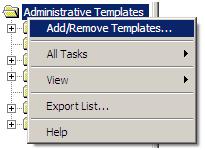
Click on Add and browse to the location where your custom ADM file is stored, and select the file.
Now the custom ADM file should appear in the list of templates.
Click Close to exit the dialog
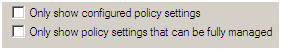
Now, right-click on Administrative templates again, and select View, then Filtering
Make sure that the check boxes shown below are unchecked than click OK
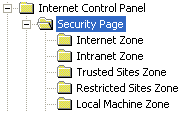
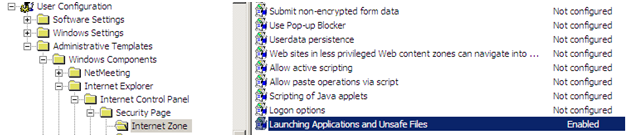
Navigate to Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page.
Under each of the following zones, you should have the setting "Launching Applications and Unsafe Files"
- Internet Zone
- Intranet Zone
- Trusted Sites Zone
- Restricted Sites Zone
- Local Machine Zone
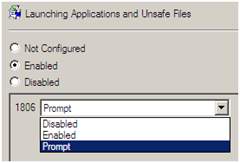
Double-click the policy and enable it. This will allow you to configure the policy as shown below:
Select one of the three options:
- Enabled: [1806=0] - This setting enables the Launching of Applications and Unsafe Files, in the specific zone
- Prompt: [1806=1] - This setting causes a prompt to appear before Launching of Applications and Unsafe Files, in the specific zone
- Disabled: [1806=3] - This setting disables the Launching of Applications and Unsafe Files, in the specific zone
Once you have made your selection, click OK
Refresh the Group Policy on the client machines, and you should now have centralized management of the "Launch Applications and Unsafe Files" setting.
One quick note here: If you want to use the ADM for computer policy, you have to replace the keyword “CLASS USER” in line 1 with “CLASS MACHINE” in the sample ADM.
And that brings us to the end of this post. Hopefully you find this information useful.
Additional Resources:
- KB 323639: How to create custom administrative templates in Windows 2000
- KB 225087: Writing Custom ADM files for System Policy Editor
- KB 182569: Description of Internet Explorer Security Zones registry entries
- Technet: Using Administrative Template Files with Registry-Based Group Policy
- Sumesh P.
Attachment(s): Sample_ADM_Launching_Applications_and_Unsafe_Files.txt