Configure an OpenVPN client for Azure Virtual WAN
This article helps you configure OpenVPN ® Protocol clients. You can also use the Azure VPN Client to connect via OpenVPN protocol. For more information, see Configure a VPN client for P2S OpenVPN connections.
Before you begin
Create a User VPN (point-to-site) configuration. Make sure that you select "OpenVPN" for tunnel type. For steps, see Create a P2S configuration for Azure Virtual WAN.
Windows clients
Download and install the OpenVPN client (version 2.4 or higher) from the official OpenVPN website.
Locate the VPN client profile configuration package that you generated and downloaded to your computer. Extract the package. Go to the OpenVPN folder and open the vpnconfig.ovpn configuration file using Notepad.
Next, locate the child certificate you created. If you don't have the certificate, use one of the following links for steps to export the certificate. You'll use the certificate information in the next step.
- VPN Gateway instructions
- Virtual WAN instructions
From the child certificate, extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your computer is one way. The profileinfo.txt file contains the private key and the thumbprint for the CA and the Client certificate. Be sure to use the thumbprint of the client certificate.
openssl pkcs12 -in "filename.pfx" -nodes -out "profileinfo.txt"Switch to the vpnconfig.ovpn file you opened in Notepad. Fill in the section between
<cert>and</cert>, getting the values for$CLIENT_CERTIFICATE,$INTERMEDIATE_CERTIFICATE, and$ROOT_CERTIFICATEas shown in the following example.# P2S client certificate # please fill this field with a PEM formatted cert <cert> $CLIENT_CERTIFICATE $INTERMEDIATE_CERTIFICATE (optional) $ROOT_CERTIFICATE </cert>- Open profileinfo.txt from the previous step in Notepad. You can identify each certificate by looking at the
subject=line. For example, if your child certificate is called P2SChildCert, your client certificate will be after thesubject=CN = P2SChildCertattribute. - For each certificate in the chain, copy the text (including and between) "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----".
- Only include an
$INTERMEDIATE_CERTIFICATEvalue if you have an intermediate certificate in your profileinfo.txt file.
- Open profileinfo.txt from the previous step in Notepad. You can identify each certificate by looking at the
Open the profileinfo.txt in Notepad. To get the private key, select the text (including and between) "-----BEGIN PRIVATE KEY-----" and "-----END PRIVATE KEY-----" and copy it.
Go back to the vpnconfig.ovpn file in Notepad and find this section. Paste the private key replacing everything between and
<key>and</key>.# P2S client root certificate private key # please fill this field with a PEM formatted key <key> $PRIVATEKEY </key>If you're using the 2.6 version of the OpenVPN client, add the "disable-dco" option to the profile. This option doesn't seem to be backward compatible with previous versions, so it should only be added to OpenVPN client version 2.6.
Don't change any other fields. Use the filled in configuration in client input to connect to the VPN.
Copy the vpnconfig.ovpn file to C:\Program Files\OpenVPN\config folder.
Right-click the OpenVPN icon in the system tray and click Connect.
macOS clients
Important
Only macOS 10.13 and above is supported with OpenVPN protocol.
Note
OpenVPN Client version 2.6 is not yet supported.
Download and install an OpenVPN client, such as TunnelBlick.
If you haven't already done so, download the VPN client profile package from the Azure portal.
Unzip the profile. Open the vpnconfig.ovpn configuration file from the OpenVPN folder in a text editor.
Fill in the P2S client certificate section with the P2S client certificate public key in base64. In a PEM formatted certificate, you can open the .cer file and copy over the base64 key between the certificate headers.
Fill in the private key section with the P2S client certificate private key in base64. See Export your private key on the OpenVPN site for information about how to extract a private key.
Don't change any other fields. Use the filled in configuration in client input to connect to the VPN.
Double-click the profile file to create the profile in Tunnelblick.
Launch Tunnelblick from the applications folder.
Click on the Tunnelblick icon in the system tray and pick connect.
iOS clients
Important
Only iOS 11.0 and above is supported with OpenVPN protocol.
Note
OpenVPN Client version 2.6 is not yet supported.
Install the OpenVPN client (version 2.4 or higher) from the App store. Version 2.6 is not yet supported.
If you haven't already done so, download the VPN client profile package from the Azure portal.
Unzip the profile. Open the vpnconfig.ovpn configuration file from the OpenVPN folder in a text editor.
Fill in the P2S client certificate section with the P2S client certificate public key in base64. In a PEM formatted certificate, you can open the .cer file and copy over the base64 key between the certificate headers.
Fill in the private key section with the P2S client certificate private key in base64. See Export your private key on the OpenVPN site for information about how to extract a private key.
Don't change any other fields.
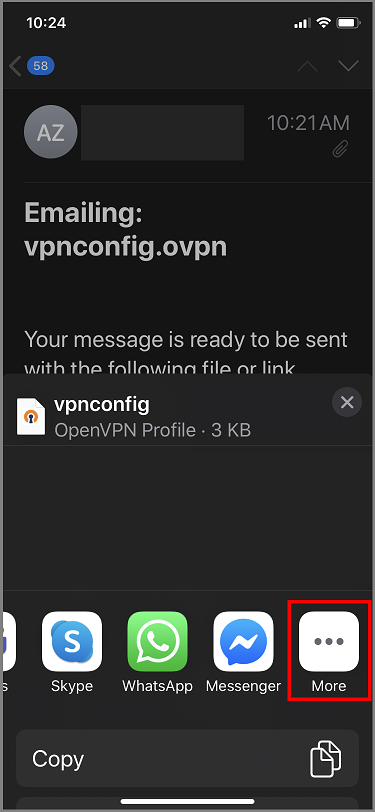
E-mail the profile file (.ovpn) to your email account that is configured in the mail app on your iPhone.
Open the e-mail in the mail app on the iPhone, and tap the attached file.
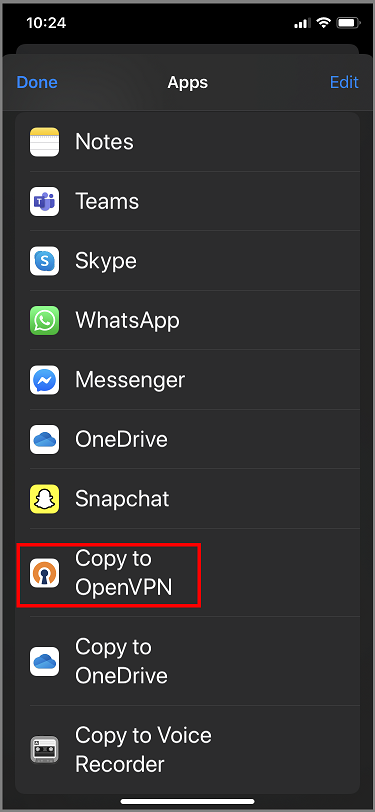
Tap More if you don't see Copy to OpenVPN option.
Tap Copy to OpenVPN.
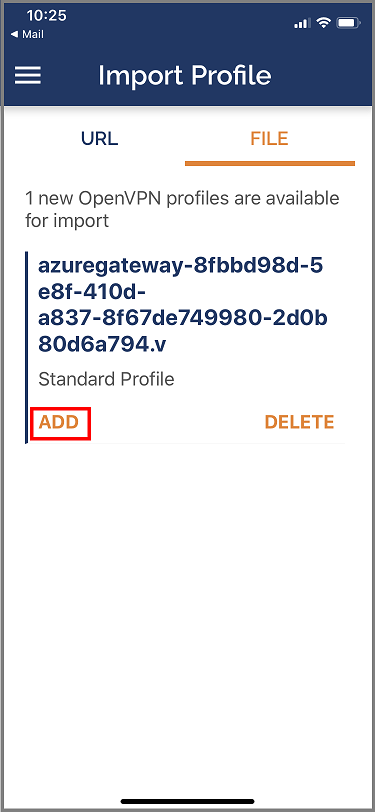
Tap on ADD in the Import Profile page
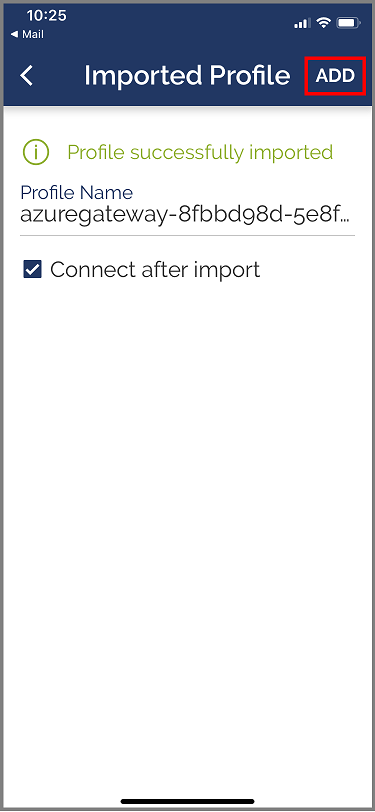
Tap on ADD in the Imported Profile page
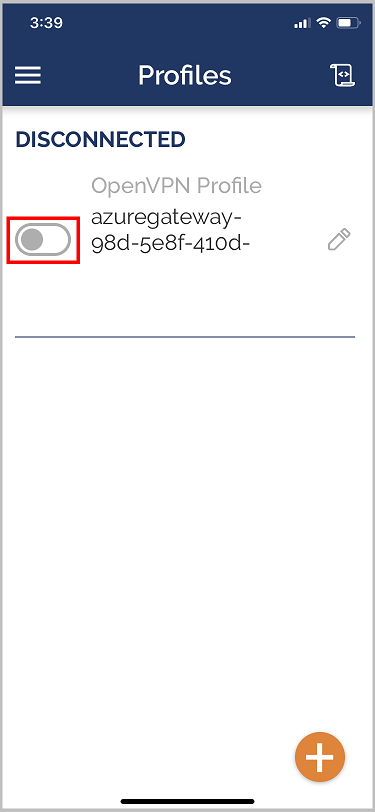
Launch the OpenVPN app and slide the switch in the Profile page right to connect
Linux clients
Note
OpenVPN Client version 2.6 is not yet supported.
Open a new Terminal session. You can open a new session by pressing 'Ctrl + Alt + t' at the same time.
Enter the following command to install needed components:
sudo apt-get install openvpn sudo apt-get -y install network-manager-openvpn sudo service network-manager restartDownload the VPN profile for the gateway. This can be done from the Point-to-site configuration tab in the Azure portal.
Export the P2S client certificate you created and uploaded to your P2S configuration on the gateway. See Virtual WAN point-to-site for instructions.
Extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your computer is one way.
openssl pkcs12 -in "filename.pfx" -nodes -out "profileinfo.txt"The profileinfo.txt file will contain the private key and the thumbprint for the CA, and the Client certificate. Be sure to use the thumbprint of the client certificate.
Open profileinfo.txt in a text editor. To get the thumbprint of the client (child) certificate, select the text including and between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" for the child certificate and copy it. You can identify the child certificate by looking at the subject=/ line.
Open the vpnconfig.ovpn file and find the section shown below. Replace everything between "cert" and "/cert".
# P2S client certificate # please fill this field with a PEM formatted cert <cert> $CLIENTCERTIFICATE </cert>Open the profileinfo.txt in a text editor. To get the private key, select the text including and between "-----BEGIN PRIVATE KEY-----" and "-----END PRIVATE KEY-----" and copy it.
Open the vpnconfig.ovpn file in a text editor and find this section. Paste the private key replacing everything between "key" and "/key".
# P2S client root certificate private key # please fill this field with a PEM formatted key <key> $PRIVATEKEY </key>Don't change any other fields. Use the filled in configuration in client input to connect to the VPN.
To connect using the command line, type the following command:
sudo openvpn --config <name and path of your VPN profile file>&To connect using the GUI, go to system settings.
Click + to add a new VPN connection.
Under Add VPN, pick Import from file….
Browse to the profile file and double-click or pick Open.
Click Add on the Add VPN window.
You can connect by turning the VPN ON on the Network Settings page, or under the network icon in the system tray.
Next steps
For more information about User VPN (point-to-site), see Create User VPN connections.
"OpenVPN" is a trademark of OpenVPN Inc.