Evaluación de vulnerabilidades de nodos de Kubernetes
Defender for Cloud puede examinar las máquinas virtuales de que hospedan nodos de Kubernetes para evaluar las vulnerabilidades tanto del sistema operativo como del software instalado. Se generan recomendaciones de corrección para que el equipo de seguridad del cliente las revise y corrija como parte de la responsabilidad compartida de mantener los nodos Kubernetes de un clúster.
Requisito previo
Para habilitar la evaluación de vulnerabilidades de los nodos se debe activar la opción Examen sin agente de máquinas en los planes Defender para contenedores, Administración de la posición de seguridad en la nube de Defender o Defender para servidores P2.
Examen de las recomendaciones de vulnerabilidades de los nodos de Kubernetes
Si se encuentran vulnerabilidades para un nodo de Kubernetes, se genera una recomendación para que el cliente la examine. Para examinar las recomendaciones de los nodos de Kubernetes para corregirlas en Azure Portal:
En el menú de Defender for Cloud, seleccione Recomendaciones.
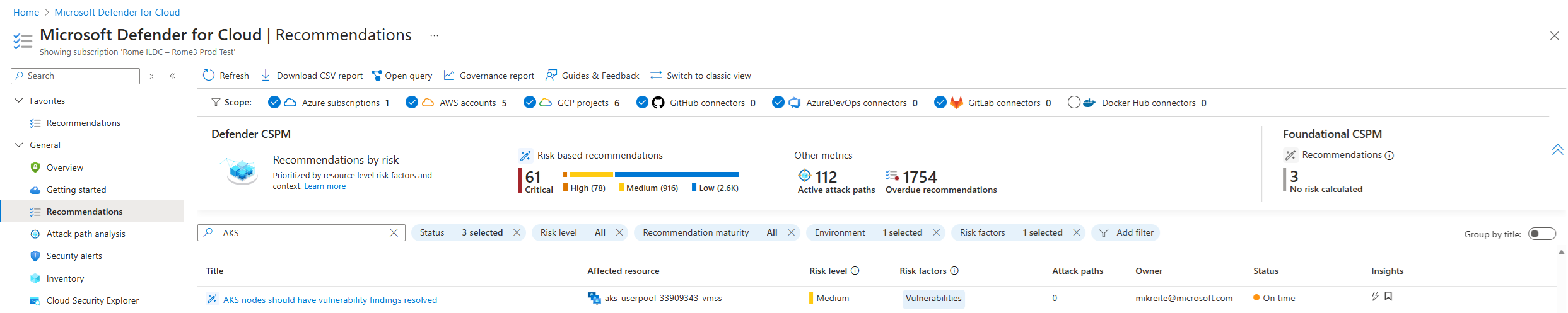
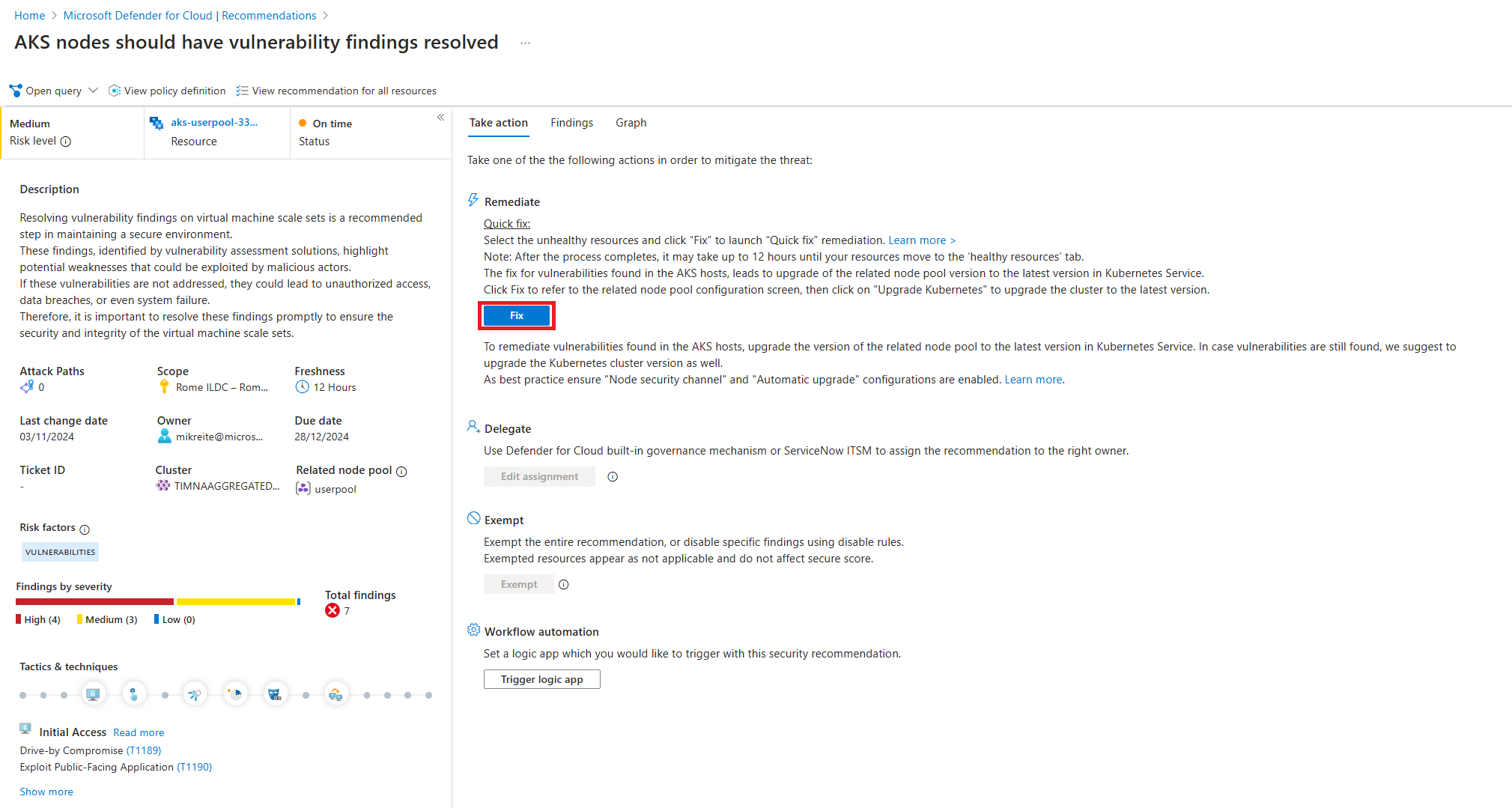
Seleccione la recomendación Los nodos de AKS deben tener resueltos los resultados de vulnerabilidades.
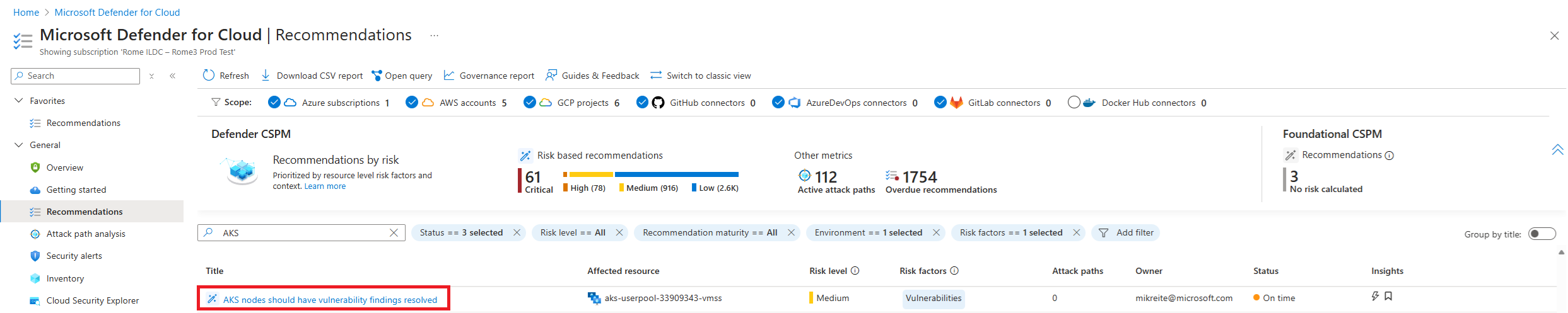
Se muestran todos los detalles de la recomendación del nodo de Kubernetes. Junto con una descripción completa de la vulnerabilidad, se presentan otros detalles, como el nombre del grupo de nodos de Kubernetes afectado y su clúster.
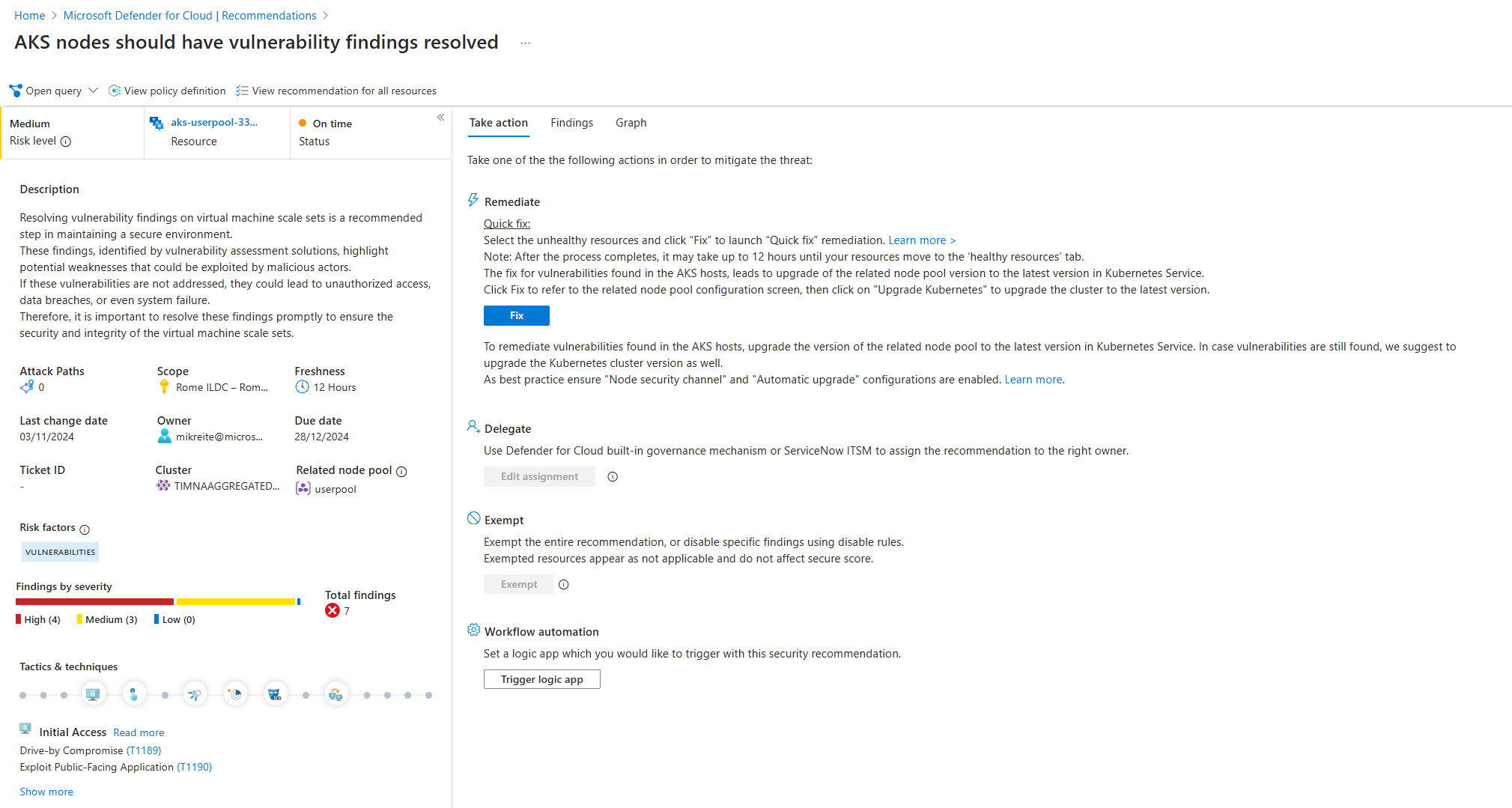
Seleccione la pestaña Conclusiones para ver una lista de los CVE relacionados con el nodo de Kubernetes.
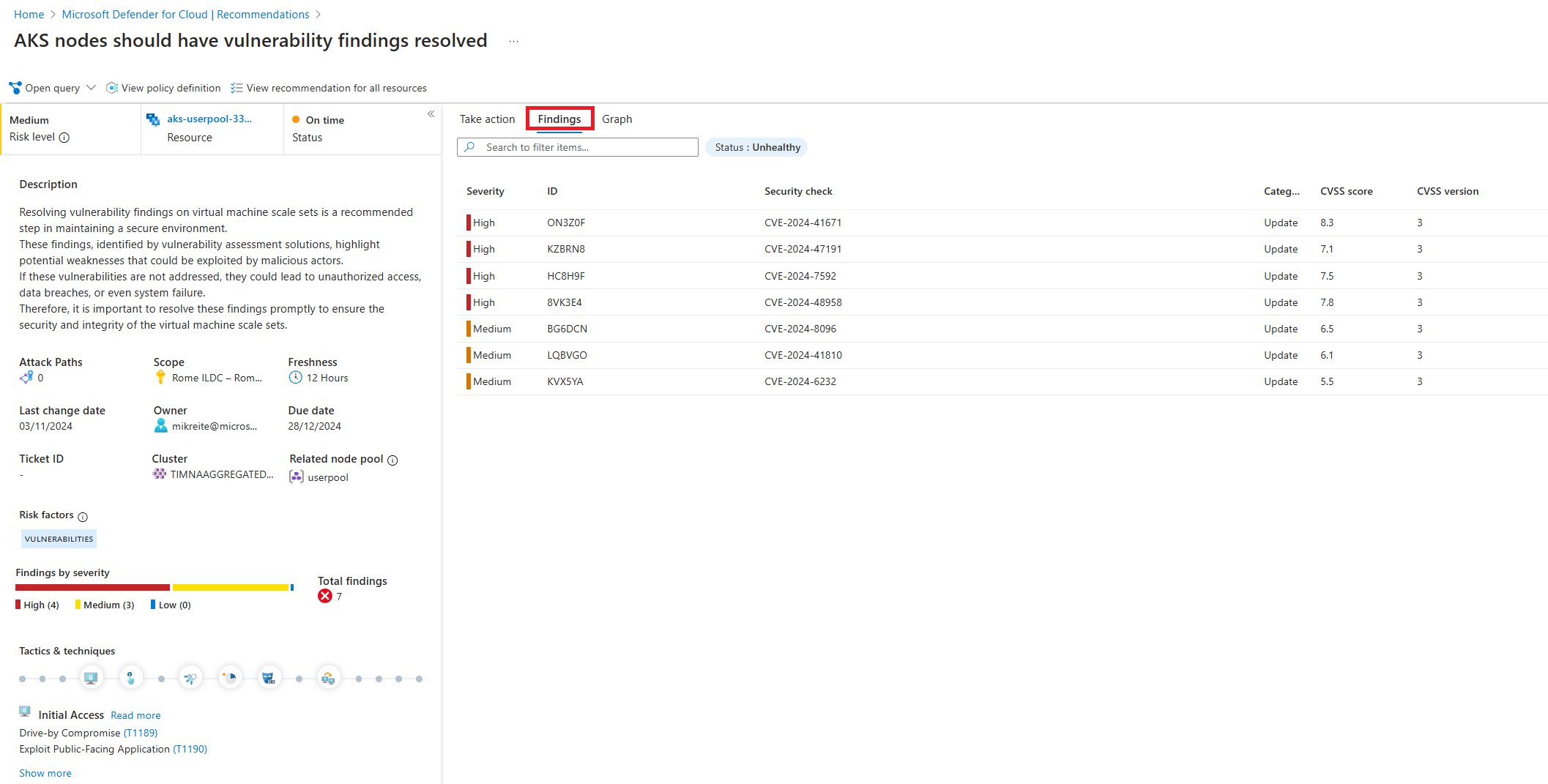
Al seleccionar una de las líneas de CVE, se abre un panel con todos los detalles sobre el CVE y todos los recursos del nodo de Kubernetes que también presentan esta vulnerabilidad.
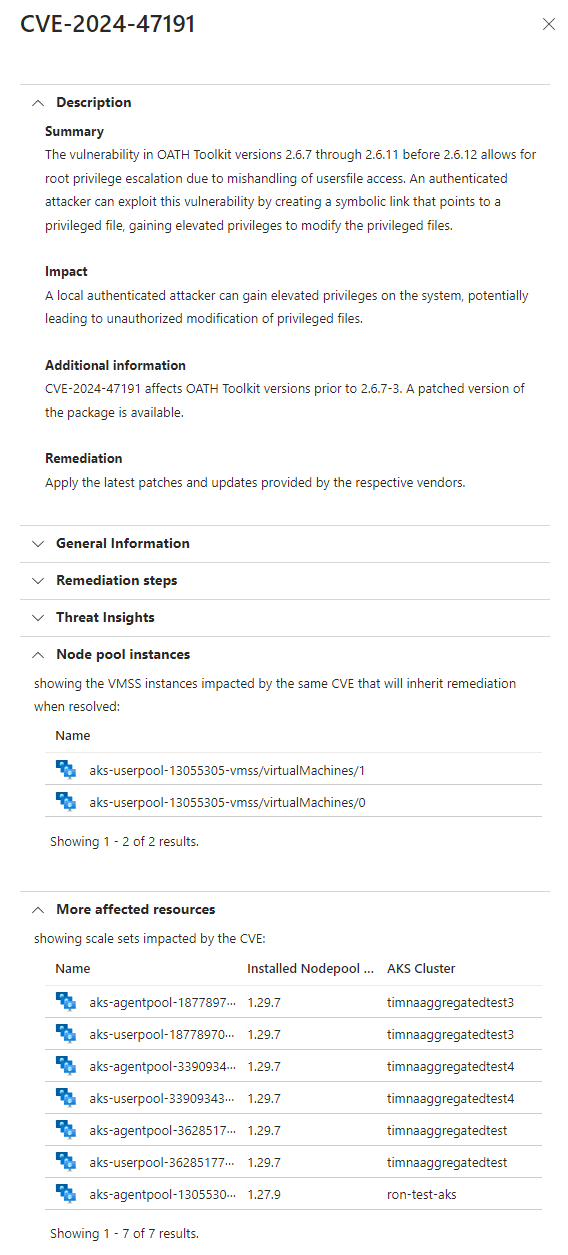
En el panel de detalles, la sección Instancias del grupo de nodos muestra los nodos que se verán afectados por la corrección. Recursos más afectados muestra otros nodos que tienen el mismo CVE y también se deben corregir.
Corrección de vulnerabilidades del nodo de Kubernetes
Las vulnerabilidades de nodo de Kubernetes se corrigen mediante la actualización de la versión de la imagen de máquina virtual del grupo de nodos. El cliente actualiza el grupo de nodos, como parte de la responsabilidad compartida entre el servicio Kubernetes y el cliente. El cliente actualiza el grupo de nodos de una de estas dos maneras: actualizar la imagen de máquina virtual del grupo de nodos o el servicio Kubernetes del clúster a una versión más reciente. Primero se recomienda actualizar la imagen de máquina virtual del grupo de nodos. En algunos casos, el cliente debe actualizar la versión del servicio Kubernetes del clúster y la versión de la imagen de máquina virtual del grupo de nodos para corregir la vulnerabilidad.
Importante
La versión de Kubernetes del clúster y la imagen de máquina virtual del grupo de nodos se pueden establecer en actualización automática. Estas versiones deben actualizarse periódicamente para proporcionar la máxima seguridad a los recursos de AKS.
Actualización de la imagen de máquina virtual del grupo de nodos
Para actualizar la imagen de máquina virtual del grupo de nodos, seleccione el botón Actualizar imagen, o bien seleccione Actualizar Kubernetes para actualizar la versión del servicio Kubernetes del clúster.

Pasos siguientes
Aprenda a usar Cloud Security Explorer para investigar vulnerabilidades en un nodo de clúster.