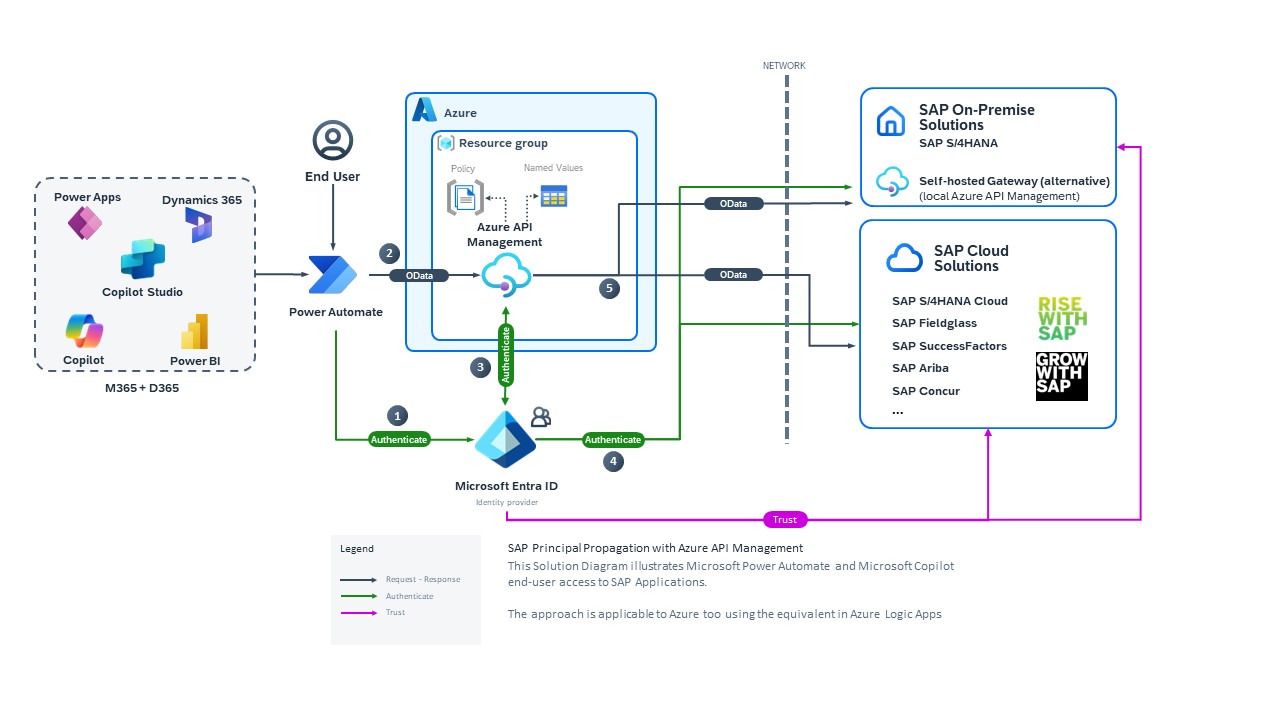
Configurar Microsoft Entra ID, Azure API Management y SAP para SSO desde el conector OData de SAP
Puede configurar el conector SAP OData de Power Platform para usar las credenciales de Microsoft Entra ID para el inicio de sesión único (SSO) en SAP. Esto permite a sus usuarios acceder a los datos de SAP en soluciones Power Platform sin tener que iniciar sesión varias veces en varios servicios, al tiempo que respeta sus autorizaciones y roles asignados en SAP.
Este artículo le guía a través del proceso, incluida la configuración de una relación de confianza entre SAP e Microsoft Entra ID y la configuración de Azure API Management para convertir el token de OAuth de Microsoft Entra ID en un token SAML que se usa para realizar llamadas OData a SAP.
También puede obtener información adicional y contexto sobre el proceso de configuración en la publicación del blog, ¡Hurra! El conector OData de SAP ahora es compatible con OAuth2 y la propagación de la entidad de seguridad de SAP.
Requisitos previos
- Instancia de SAP
- Recursos Azure API Management
Descargar metadatos SAML del proveedor local de SAP
Para configurar una relación de confianza entre SAP e Microsoft Entra ID mediante SAML 2.0, primero descargue el archivo xml de metadatos de SAP.
Realice estos pasos como administrador de SAP Basis en la GUI de SAP.
En la GUI de SAP, ejecute la transacción SAML2 para abrir el asistente dependiente de cliente SAP correspondiente y elija la pestaña Proveedor local.
Seleccione Metadatos y después seleccione Descargar Metadatos. Subirá los metadatos de SAML de SAP a Microsoft Entra ID en un paso posterior.
Anote el nombre Nombre de proveedor compatible con URI.
Nota
Microsoft Entra ID requiere que este valor sea compatible con URI. Si Nombre del Proveedor ya está configurado y no es compatible con URI, no lo cambie sin consultar primero a su equipo de SAP Basis. Cambiar el Nombre del Proveedor puede romper las configuraciones SAML existentes. Los pasos para cambiarlo están fuera del alcance de este artículo. Consulte con su equipo de Basis de SAML para obtener orientación.
Consulte la documentación oficial de SAP para obtener información adicional.
Importar metadatos de SAP en la aplicación empresarial de Microsoft Entra ID
Realice estos pasos como administrador de Microsoft Entra ID en el Azure Portal.
Seleccione Microsoft Entra ID>Aplicaciones empresariales.
Seleccione Nueva aplicación.
Busque SAP Netweaver.
Asigne un nombre a la aplicación empresarial y, después, seleccione Crear.
Vaya a Inicio de sesión único y seleccione SAML.
Seleccione Subir archivo de metadatos y seleccione el archivo de metadatos que descargó de SAP.
Seleccione Agregar.
Cambie la URL de respuesta (URL del servicio de consumidor de aserciones) al punto de conexión del token de SAP OAuth. La dirección URL está en el formato
https://<SAP server>:<port>/sap/bc/sec/oauth2/token.Cambie la URL de inicio de sesión a un valor compatible con URI. Este parámetro no se usa y se puede establecer en cualquier valor que sea compatible con URI.
Seleccione Guardar.
En Atributos y reclamaciones, seleccione Editar.
Confirme que Nombre de la reclamación Identificador único de usuario (ID de nombre) esté establecido en user.userprincipalname [nameid=format:emailAddress].
En Certificados SAML, seleccione Descargar para Certificado (Base64) y XML de metadatos de federación.
Configurar Microsoft Entra ID como proveedor de identidades de confianza para OAuth 2.0 en SAP
Siga los pasos descritos en la sección Documentación de Microsoft Entra e ID para SAP NetWeaver y OAuth2.
Vuelva a este artículo una vez creado el cliente OAuth2 en SAP.
Consulte la documentación oficial de SAP sobre SAP NETWEAVER para obtener más información. Tenga en cuenta que debe ser administrador de SAP para acceder a la información.
Crear una aplicación de Microsoft Entra que representa el recurso de Azure API Management
Configure una aplicación de Microsoft Entra ID que otorgue acceso al conector OData de Microsoft Power Platform SAP. Esta aplicación permite que un recurso de Azure API Management convierta tokens de OAuth en tokens SAML.
Siga estos pasos como administrador de Microsoft Entra ID en el Azure Portal.
Seleccione Microsoft Entra ID>Registros de aplicaciones>Registro nuevo.
Introduzca un Nombre y después seleccione Registro.
Seleccione Certificados y secretos>Nuevo secretos de cliente.
Introduzca una Descripción y después seleccione Agregar.
Copie y guarde este secreto en un lugar seguro.
Seleccione Permisos de API>Agregar un permiso.
Seleccione Microsoft Graph>Permisos delegados.
Busque y seleccione openid.
Seleccione Agregar permisos.
Seleccione Autenticación>Agregar una plataforma>Web.
Establezca el URI de redireccionamiento como
https://localhost:44326/signin-oidc.Seleccione Tokens de acceso y Tokens de identificador y, a continuación, seleccione Configurar.
Seleccione Exponer una API.
Junto a URI de id. de la aplicación, seleccione Agregar.
Acepte el valor predeterminado y seleccione Guardar.
Seleccione Agregar un ámbito.
Establezca Nombre del ámbito a user_impersonation.
Establezca ¿Quién puede dar su consentimiento? a Administradores y usuarios.
Seleccione Agregar un ámbito.
Copie el Id. de aplicación (cliente) .
Autorizar al recurso de Azure API Management para acceder a SAP Netweaver mediante la aplicación empresarial Microsoft Entra ID
Cuando se crea una aplicación empresarial de Microsoft Entra ID, se crea un registro de aplicación coincidente. Busque el registro de aplicación que coincida con la aplicación empresarial de Microsoft Entra ID que creó para SAP NetWeaver.
Seleccione Exponer una API>Agregar una aplicación de cliente.
Pegue la Id. de aplicación (cliente) del registro de aplicación de Microsoft Entra ID de su instancia de API Management de Azure en Id. de cliente.
Seleccione el ámbito user_impersonation y, a continuación, seleccione Agregar aplicación.
Autorizar al conector OData de SAP para acceder a las Microsoft Power Platform API expuestas por Azure API Management
En el registro de la aplicación de Microsoft Entra ID de API Management de Azure, seleccione Exponer una API>Agregar el id. de cliente del conector SAP OData de Power Platform
6bee4d13-fd19-43de-b82c-4b6401d174c3en las aplicaciones cliente autorizadas.Seleccione el ámbito de user_impersonation y luego seleccione Guardar.
Configurar SAP OAuth
Cree un cliente OAuth 2.0 en SAP que permita a Azure API Management obtener tokens en nombre de los usuarios.
Consulte la documentación oficial de SAP para obtener más información.
Realice estos pasos como administrador de SAP Basis en la GUI de SAP.
Ejecute la transacción SOAUTH2.
Seleccione Crear.
En la página ID de cliente:
- Para ID de cliente OAuth 2.0, seleccione un usuario del sistema SAP.
- Introduzca una Descripción y después seleccione Siguiente.
En la página Autenticación de cliente, seleccione Siguiente.
En la página Configuración de tipo de concesión:
- Para IdP de confianza OAuth 2.0, seleccione la entrada Microsoft Entra ID.
- Seleccione Actualización permitida y, después, seleccione Siguiente.
En la página de Asignación de ámbito, seleccione Agregar, seleccione los servicios de OData que usa Azure API Management (por ejemplo, ZAPI_BUSINESS_PARTNER_0001) y, a continuación, seleccione Siguiente.
Seleccione Finalizar.
Configurar Azure API Management
Importe los metadatos XML de SAP OData en su instancia de Azure API Management. A continuación, aplique una directiva de Azure API Management para convertir los tokens.
Abra su instancia de Azure API Management y siga los pasos para crear una API de SAP OData.
En API, seleccione Valores con nombre.
Agregue los siguientes pares clave-valor:
| Llave | valor |
|---|---|
| AADSAPResource | URI del proveedor local de SAP |
| AADTenantId | Sul inquilino GUID |
| APIMAADRegisteredAppClientId | GUID de aplicación Microsoft Entra ID |
| APIMAADRegisteredAppClientSecret | Secreto de cliente del paso anterior |
| SAPOAuthClientID | Usuario de sistema SAP |
| SAPOAuthClientSecret | Contraseña de usuario del sistema SAP |
| SAPOAuthRefreshExpiry | Token de vencimiento de actualización |
| SAPOAuthScope | Ámbitos de OData seleccionados durante la configuración de SAP OAuth |
| SAPOAuthServerAddressForTokenEndpoint | Punto de conexión de SAP para Azure API Management al que se llamará para realizar la adquisición de tokens |
Nota
Tenga en cuenta que la configuración difiere ligeramente para SAP SuccessFactors. Para obtener más información, consulte la directiva de administración de API de Azure para SAP SuccessFactors.
Aplicar la directiva de token de Azure API Management
Use directivas Azure API Management para convertir un token emitido por Microsoft Entra en uno que SAP NetWeaver acepte. Esto se hace mediante el flujo OAuth2SAMLBearer. Consulte la documentación oficial de SAP para obtener más información.
Copie la directiva de Azure API Management de la página GitHub oficial de Microsoft.
Abra el Azure Portal.
Vaya a su recurso de Azure API Management.
Seleccione API y después seleccione la API de OData que ha creado.
Seleccione Todas las operaciones.
En Procesamiento de entrada, seleccione Directivas </>.
Elimine la directiva existente y pegue la que copió.
Seleccione Guardar.
Contenido relacionado
- Conector de datos SAP OData
- El conector OData de SAP ahora es compatible con OAuth2 y la Propagación de Principal | Blog de la comunidad de Power Automate
- Directiva de API Management de Azure para SAP SuccessFactors | GitHub
- Conector de SAP OData para SAP SuccessFactors | Blog de la comunidad de SAP
- SAP Business Accelerator Hub también ofrece contenido relacionado con la política de la suite de integración de SAP para SuccessFactors y NetWeaver. Debe tener una cuenta de SAP para acceder a este contenido.