2.5.3.4 Algorithm for Creating a Security Descriptor
An important element of the overall security model is the manner in which security descriptors are created for new objects. In the trivial case, the creator of a new object simply supplies a new security descriptor for the new object, and the two are associated by the resource manager or server that owns the object. The trivial case is not the common case, however, and the security model has specific behavior involved in deriving the security descriptor for a new object from the security descriptors for existing objects.
The derivation of a new security descriptor in this security model is called inheritance, and refers to the concept that the new security descriptor inherits some or all of its characteristics from the security descriptor of a parent or container object. Individual ACEs can contain indicators that specify whether it can be passed on to child objects, this indicator is called inheritable. Additionally, they can have an indicator as to whether the ACE was derived from a parent during its creation, this indicator is called inherited.
In overview, the process is fairly straightforward. During the creation of a new security descriptor where inheritance is possible, the parent security descriptor is examined. For each ACE in the parent security descriptor, the process checks whether it is marked as inheritable. If so, it is included in the new security descriptor. This is done for both the DACL and SACL portions of the security descriptor.
The algorithm for computing the system and discretionary ACL (SACL and DACL respectively) in the security descriptor for the new object is governed by the logic that is illustrated in the following figure.
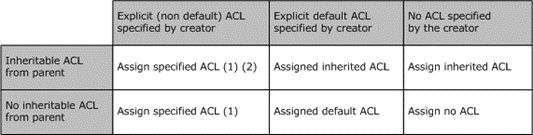
Figure 11: ACL inheritance logic
Any ACEs with the INHERITED_ACE bit set are NOT copied to the assigned security descriptor.
If AutoInheritFlags, as specified in section 2.5.3.4.1, is set to automatically inherit ACEs from the parent (DACL_AUTO_INHERIT or SACL_AUTO_INHERIT), inherited ACEs from the parent are appended after explicit ACEs from the CreatorDescriptor. For further details, see the parameter list for CreateSecurityDescriptor (section 2.5.3.4.1).
The preceding table describing ACL inheritance logic holds true if the ACL is not protected. If the ACL is protected, all the ACEs from the Explicit ACL are copied into the assigned security descriptor, resetting any ACEs with the INHERITED_ACE bit set as well. The Inheritable ACL is not considered.
Note An explicitly specified ACL, whether a default ACL or not, can be empty or null.<96>
The remainder of this section documents the details of the algorithm outlined above as a set of nested subprocedures.