Trabajar con el panel de ITDR de Defender for Identity
En la página panel de Microsoft Defender for Identity se muestran datos que le ayudarán a analizar mejor la posición de seguridad, comprender lo bien que está protegido, identificar vulnerabilidades y realizar las acciones recomendadas.
Use la página Panel para ver información crítica y datos en tiempo real sobre la detección y respuesta de amenazas de identidad (ITDR). Vea gráficos y widgets que muestren información importante relacionada con el acceso no autorizado, el riesgo de la cuenta, las amenazas internas y las actividades anómalas y, a continuación, supervise y administre de forma proactiva posibles riesgos de seguridad relacionados con la identidad.
Requisitos previos
Para acceder a este nuevo panel, necesita:
Una licencia de Microsoft Defender for Identity y una licencia de Entra ID Identity Protection
Un rol de usuario con al menos los permisos del Lector de seguridad
Para ver una lista completa de recomendaciones y seleccionar todos los vínculos de acción recomendados, necesita el rol Administrador global .
Importante
Microsoft recomienda utilizar roles con la menor cantidad de permisos. Esto ayuda a mejorar la seguridad de la organización. Administrador global es un rol con privilegios elevados que debe limitarse a escenarios en los que no se puede usar un rol existente.
Acceso al panel
Para acceder al panel, inicie sesión en Microsoft 365 Defender y seleccione Panel de identidades>.
Por ejemplo:
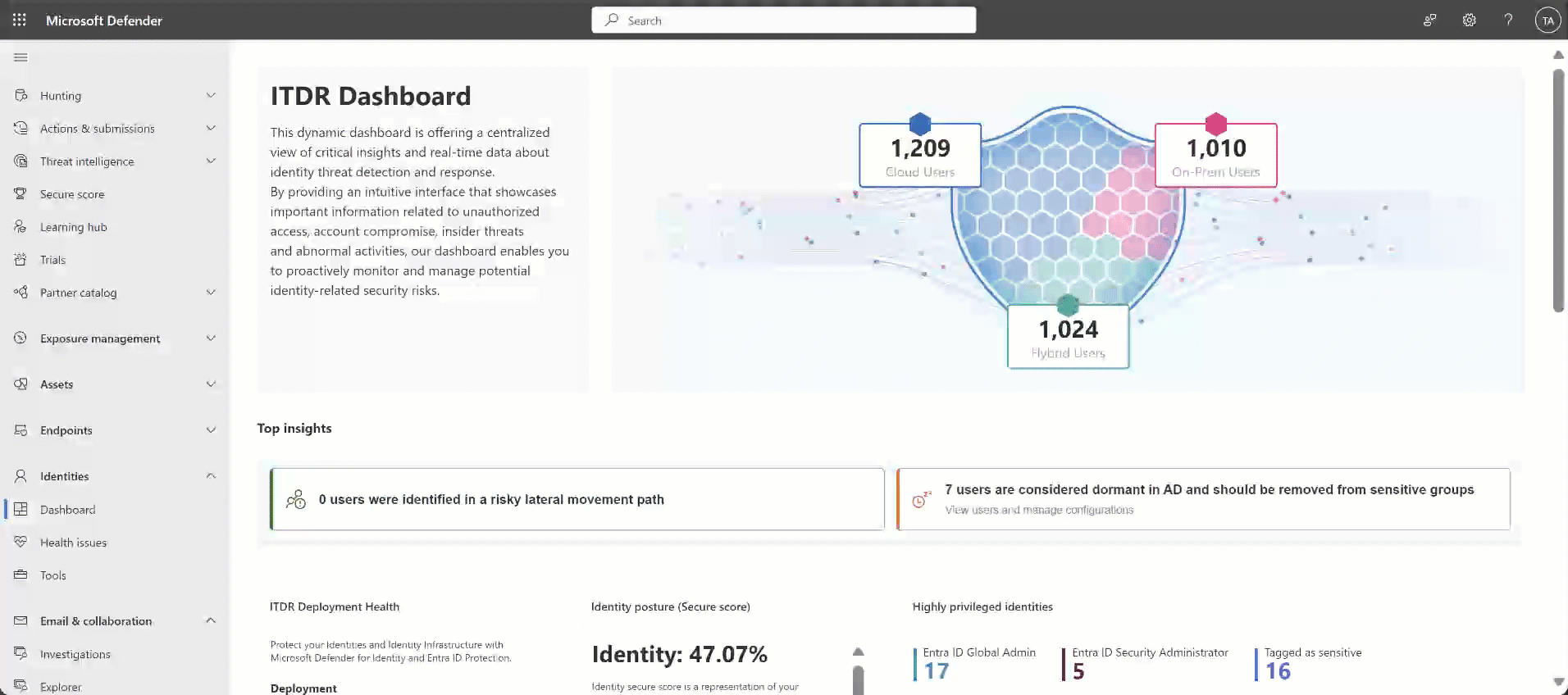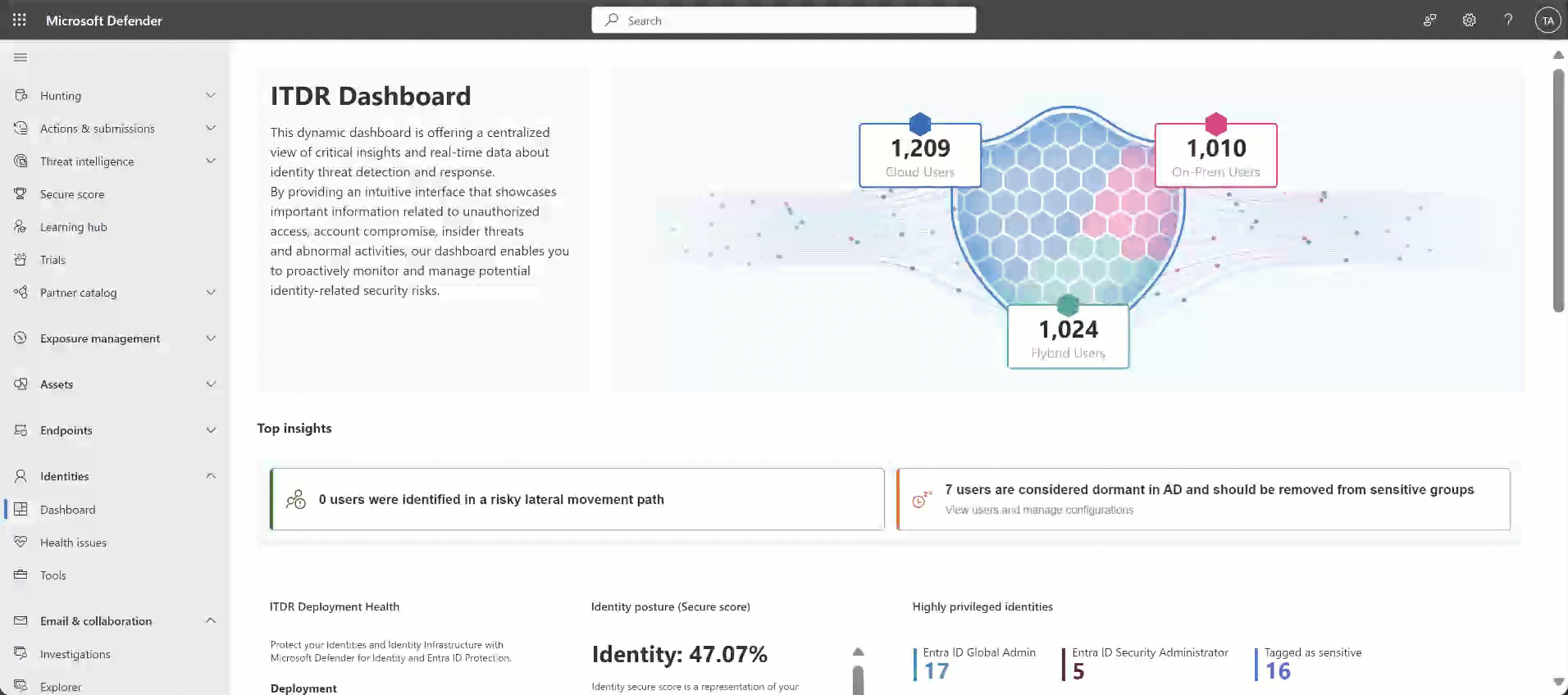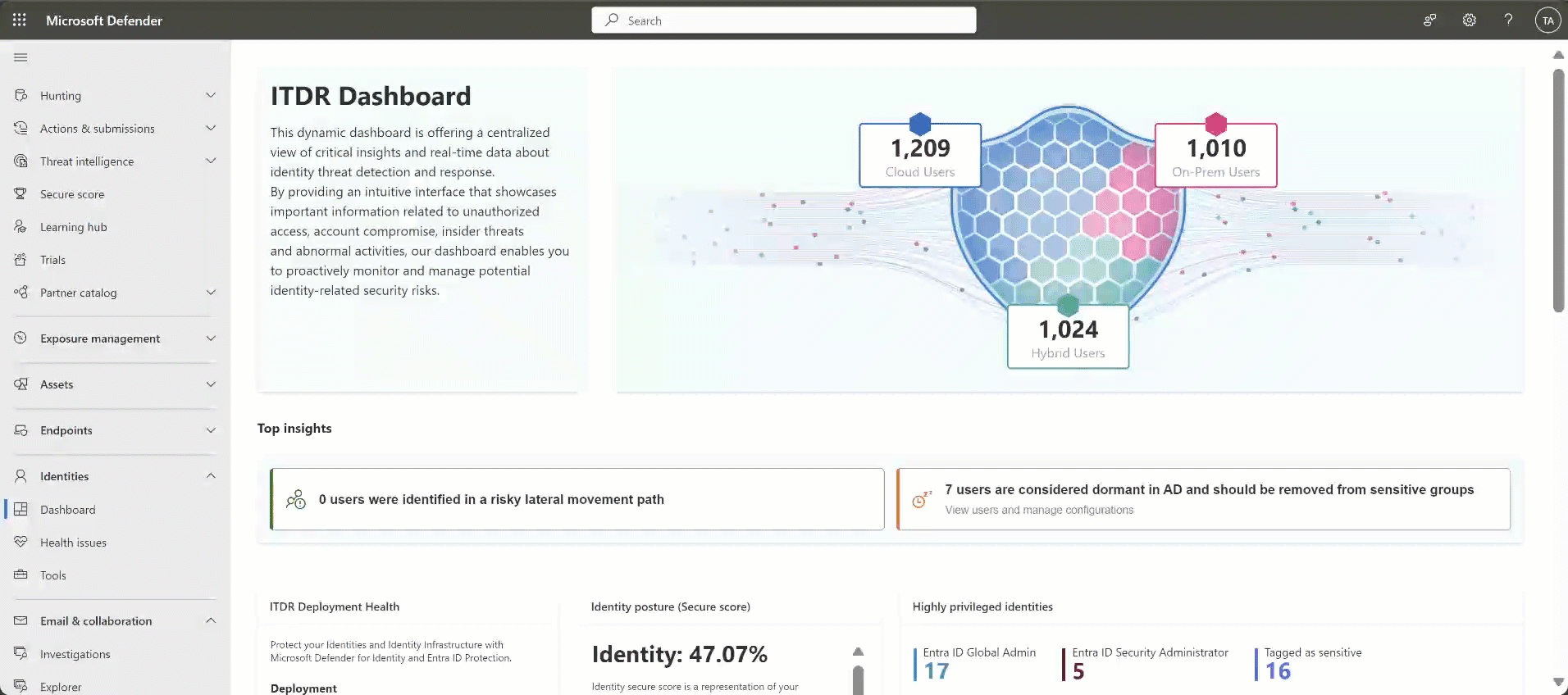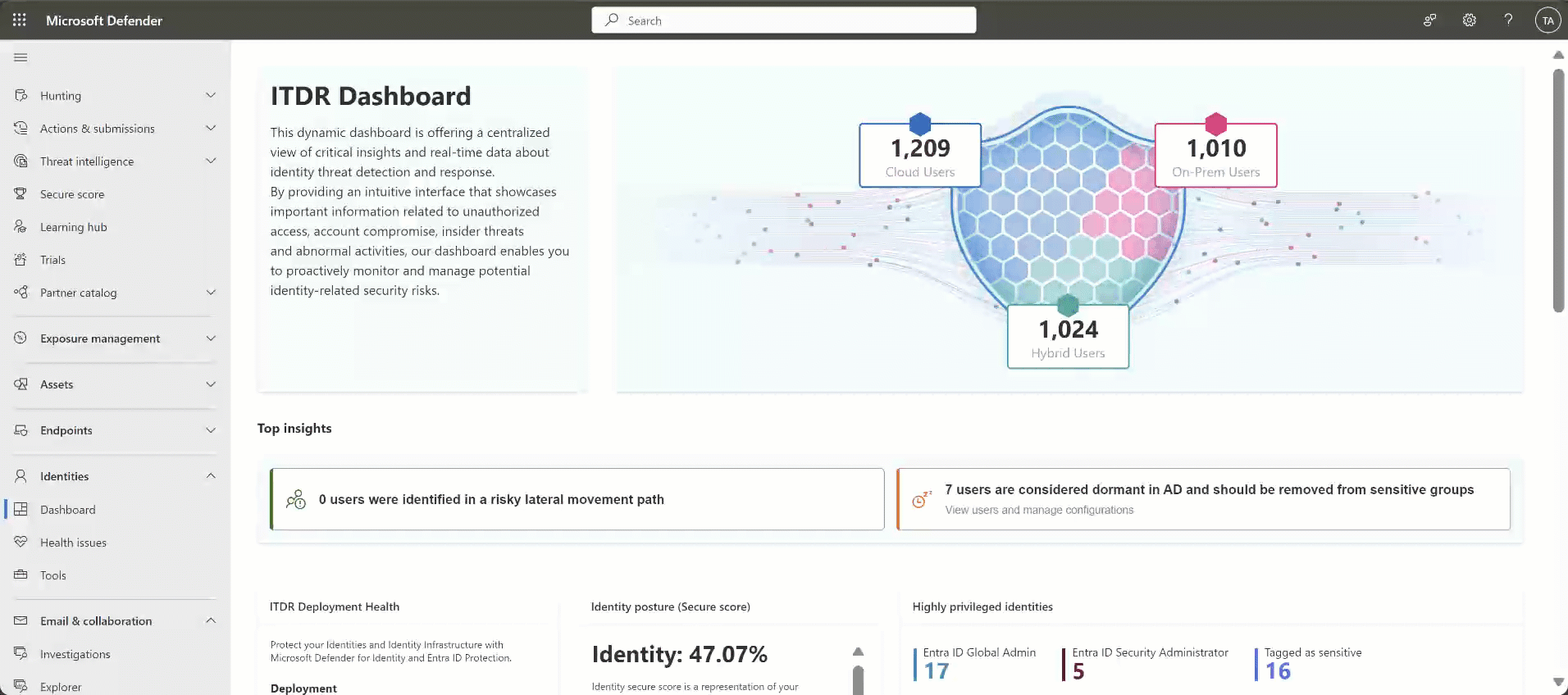
Referencia del widget del panel
En esta sección se describen los gráficos y widgets disponibles en el panel de ITDR.
Seleccione vínculos en las tarjetas para obtener más detalles, como documentación, recomendaciones relacionadas en Puntuación segura de Microsoft, etc.
| Nombre | Descripción |
|---|---|
| Información general sobre identidades (widget de Sheild) | Proporciona información general rápida sobre el número de usuarios en entornos híbridos, en la nube y locales (AD y Microsoft Entra ID). Esta característica incluye vínculos directos a la plataforma de búsqueda avanzada, que ofrecen información detallada del usuario al alcance de la mano. |
|
Conclusiones principales / Usuarios identificados en una ruta de desplazamiento lateral de riesgo |
Indica las cuentas confidenciales con rutas de desplazamiento lateral de riesgo, que son ventanas de oportunidad para los atacantes y pueden exponer riesgos. Se recomienda tomar medidas en las cuentas confidenciales que se encuentren con rutas de desplazamiento lateral de riesgo para minimizar el riesgo. Para obtener más información, consulte Descripción e investigación de las rutas de desplazamiento lateral (LMP) con Microsoft Defender for Identity. |
|
Conclusiones principales / Usuarios inactivos de Active Directory que deben quitarse de grupos confidenciales |
Listas cuentas que se han quedado sin usar durante al menos 180 días. Una ruta de acceso fácil y silenciosa en la organización es a través de cuentas inactivas que forman parte de grupos confidenciales, por lo que se recomienda quitar esos usuarios de grupos confidenciales. Para obtener más información, consulte Evaluación de la seguridad: Rutas de desplazamiento lateral (LMP) más arriesgadas. |
| Estado de implementación de ITDR | Listas cualquier progreso de la implementación del sensor, las alertas de estado y la disponibilidad de licencias. |
| Postura de identidad (puntuación segura) | La puntuación que se muestra representa la posición de seguridad de la organización con un enfoque en la puntuación de identidad , lo que refleja el estado de seguridad colectiva de las identidades. La puntuación se actualiza automáticamente en tiempo real para reflejar los datos que se muestran en los gráficos y las acciones recomendadas. Microsoft Secure Score se actualiza diariamente con datos del sistema con nuevos puntos para cada acción recomendada. Para obtener más información, consulte Puntuación segura de Microsoft. |
| Entidades con privilegios elevados | Listas un resumen de las cuentas confidenciales de su organización, incluidos los administradores de seguridad de Entra ID y los usuarios de administración global. |
| Incidentes relacionados con la identidad | Listas alertas de Defender for Identity y Protección de Microsoft Entra ID, así como los incidentes correspondientes pertinentes de los últimos 30 días. |
| Dominios con configuración no segura | Listas dominios de Active Directory que tienen opciones de configuración no seguras. Los dominios de Active Directory contienen muchas configuraciones relacionadas con la seguridad, lo que, cuando se configura de forma incorrecta, puede hacer que las organizaciones sean más susceptibles a los ciberataques. Asegúrese de configurar los dominios de acuerdo con los procedimientos recomendados de seguridad para reducir la probabilidad de que se ponga en peligro la identidad. Para obtener más información, consulte Evaluación de seguridad: Configuraciones de dominio no seguras |
| Usuarios activos de id. de entra en riesgo | Listas cuentas de usuario activas que pueden ser vulnerables a amenazas de seguridad, actividades inusuales o posibles riesgos. La identificación y administración de los usuarios en riesgo es un aspecto crucial para mantener un entorno de TI seguro. Para obtener más información, consulte Corrección de riesgos y desbloqueo de usuarios en Protección de Microsoft Entra ID. |
Pasos siguientes
Para obtener más información, consulte Microsoft Defender for Identity en Microsoft 365 Defender.