Tutorial: Migración de WebLogic Server a Azure con Elastic en Azure como solución de registro
En este tutorial, implementará WebLogic Server (WLS) en Azure Virtual Machines (VM) e integrará con Elastic Cloud (Elasticsearch). También puede configurar Elastic Custom Logs para capturar datos de registro de WLS. Por último, use Kibana para buscar y analizar registros de WLS. Aunque cada componente se documenta individualmente, en este tutorial se muestra cómo se integran sin problemas para proporcionar una solución sólida de administración de registros para WLS en Azure.
En este tutorial, aprenderá a:
- Cree una instancia de Elastic en Azure.
- Implemente WLS en Azure.
- Configure los registros personalizados de Elastic para integrar los registros de WLS.
- Busque registros de WebLogic Server desde Kibana.
Prerrequisitos
- Una suscripción de Azure activa. Si no tiene una suscripción de Azure, cree una cuenta gratuita.
- La capacidad de implementar una de las aplicaciones de Azure de WLS en máquinas virtuales que se muestran en ¿Qué son las soluciones para ejecutar Oracle WebLogic Server en Azure Virtual Machines?
- Terminal para el acceso SSH a máquinas virtuales.
Implementación de WLS en Azure
Aprovisione WebLogic Server siguiendo los pasos indicados en ¿Cuáles son las soluciones para ejecutar Oracle WebLogic Server en máquinas virtuales Azure? Tanto "Implementar Oracle WebLogic Server con el servidor de administración en un solo nodo" como "Implementar el clúster de Oracle WebLogic Server en IaaS de Microsoft Azure" son compatibles con Elastic en Azure. En este tutorial se usa WebLogic en máquinas virtuales como ejemplo.
Nota
Es posible que el tamaño de máquina virtual predeterminado no tenga suficiente memoria para el agente elástico. Asegúrese de que el tamaño de máquina virtual seleccionado tenga al menos 2,5 GB de memoria. Standard_A2_v2 es el tamaño mínimo suficiente.
Después de rellenar la información necesaria, seleccione Crear para iniciar la implementación de WLS en Azure. La implementación suele tardar unos 30 minutos. Después de la implementación, vaya a Salidas y registre el valor de adminConsoleURL, que es la dirección URL para acceder a la Consola de administración.
Descripción de los registros de WebLogic
Los subsistemas de WebLogic Server usan servicios de registro para realizar un seguimiento de eventos como la implementación de aplicaciones y los errores del subsistema. Estos registros permiten que las instancias del servidor comuniquen su estado y respondan a eventos específicos, lo que proporciona información detallada que puede ayudar a solucionar problemas y supervisar. Los servicios de registro de WebLogic permiten notificar errores, escuchar mensajes de registro de subsistemas concretos y capturar actualizaciones de estado del sistema. Para obtener información más detallada sobre los servicios de registro de WebLogic, consulte Understanding WebLogic Logging Services.
Este tutorial se centra en la configuración de los siguientes registros clave de WebLogic:
Archivos de registro del servidor: normalmente se encuentran en el directorio de registros bajo la raíz de la instancia del servidor. La ruta de acceso suele ser DOMAIN_NAME/servers/SERVER_NAME/logs/SERVER_NAME.log.
Archivos de registro de dominio: estos registros proporcionan información general sobre el estado del dominio y se almacenan en los registros de del servidor de administración directorio. La ruta de acceso predeterminada es DOMAIN_NAME/servers/ADMIN_SERVER_NAME/logs/DOMAIN_NAME.log.
Registros de acceso HTTP: de forma predeterminada, los registros de acceso HTTP comparten el directorio y la directiva de rotación del registro del servidor. La ruta de acceso predeterminada es DOMAIN_NAME/servers/SERVER_NAME/logs/1access.log.
Puede configurar y administrar estos registros para facilitar la integración con herramientas de supervisión como Elastic en Azure, lo que permite el análisis centralizado de registros y las alertas en las instancias de WebLogic Server.
Mientras se implementa la oferta, puede ir directamente a y seguir los pasos descritos en la sección Creación de una instancia de Elasticsearch en Azure. Vuelva aquí cuando finalice la implementación de la oferta.
Conexión a la máquina WLS
Para acceder a la máquina virtual que ejecuta WebLogic Server (WLS), siga los pasos descritos en Conexión a la máquina virtual. En este tutorial, se va a conectar a la máquina que hospeda el servidor de administración de WebLogic, denominado adminVM.
Creación de una instancia de Elasticsearch en Azure
Elastic Cloud (Elasticsearch) para Azure es un ISV Services nativo de Azure que puede obtener de Azure Marketplace e implementar con Azure Portal. Los servicios ISV nativos de Azure permiten aprovisionar, administrar e integrar fácilmente servicios y software del proveedor de software independiente (ISV) en Azure. Elastic Cloud: El servicio ISV nativo de Azure está desarrollado y administrado por Microsoft y Elastic. Puede crear, aprovisionar y administrar recursos elásticos a través de Azure Portal. Elastic posee y opera la aplicación SaaS, incluidas las cuentas de Elastic creadas. Para obtener información general sobre Elastic Cloud (Elasticsearch), consulte ¿Qué es Elastic Cloud (Elasticsearch): un servicio ISV nativo de Azure?
Creación de Elastic en Azure
Para crear una aplicación elástica, siga los pasos descritos en Inicio rápido: Introducción a Elastic.
En el primer paso de la sección Crear recurso, siga estos pasos para los reemplazos:
En el panel Aspectos básicos, en la sección Detalles del plan, siga estos pasos:
- Para grupo de recursos, rellene un nombre de grupo de recursos único. En este tutorial se usa
elkrg1030. - En Nombre de recurso, introduzca un nombre único para su instancia de Elastic. Puede usar el mismo valor que usó para grupo de recursos.
- En Región, seleccione la región deseada.
- Mantenga los valores predeterminados para otros campos.
- Para grupo de recursos, rellene un nombre de grupo de recursos único. En este tutorial se usa
En el panel Registros & métricas, seleccione Enviar registros de actividad de suscripción y Enviar registros de recursos de Azure para todos los recursos definidos para supervisar los recursos de Azure. Sin embargo, este tutorial se centra únicamente en los registros de WLS y no cubre los registros de infraestructura.
Puede omitir las secciones Configuración de Azure OpenAI y Etiquetas.
Siga los pasos restantes del artículo.
Después de que la implementación se realice correctamente, continúe con la sección siguiente de este artículo.
Inicio de Kibana
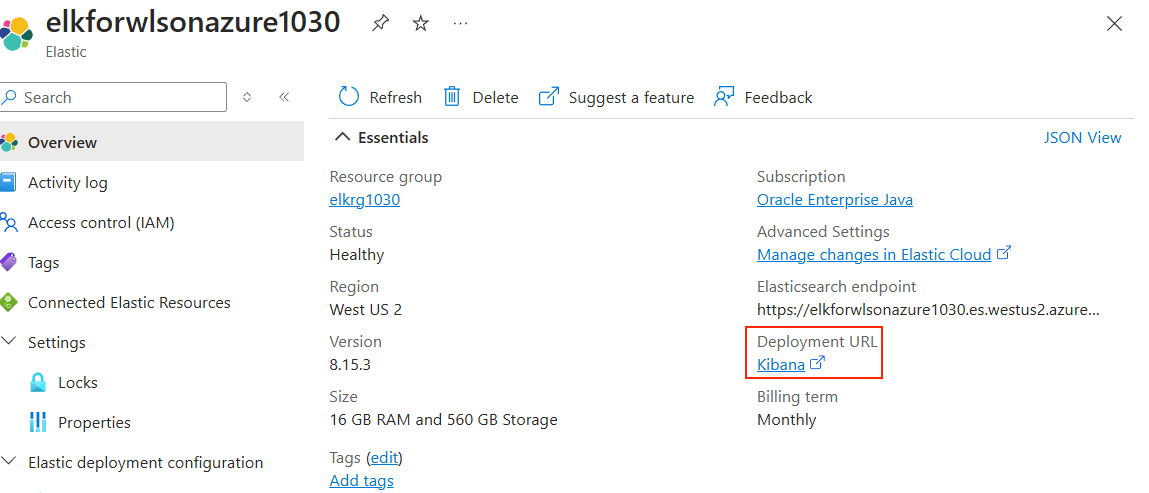
Después de implementar Elastic en Azure, abra el recurso Elastic desde el portal de Azure. Localice la URL de Kibana, junto a la etiqueta URL de implementación, como se muestra en la siguiente captura de pantalla:
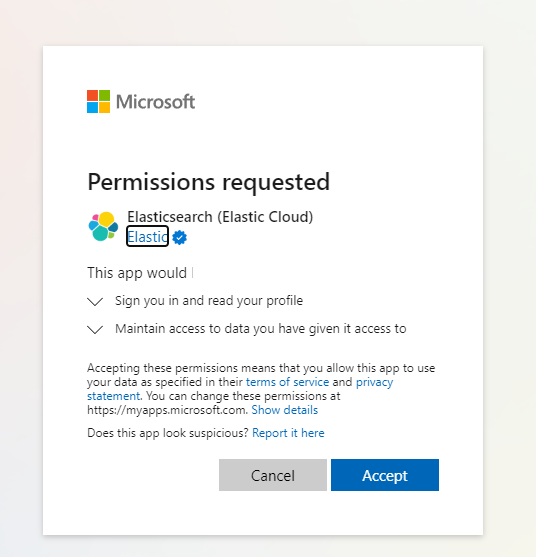
Al iniciar Kibana, se le pedirá que inicie sesión seleccionando una cuenta de Azure. Elija la cuenta de Azure que se usa para crear la implementación de Elastic y, a continuación, revise y acepte los permisos de Elasticsearch solicitados.
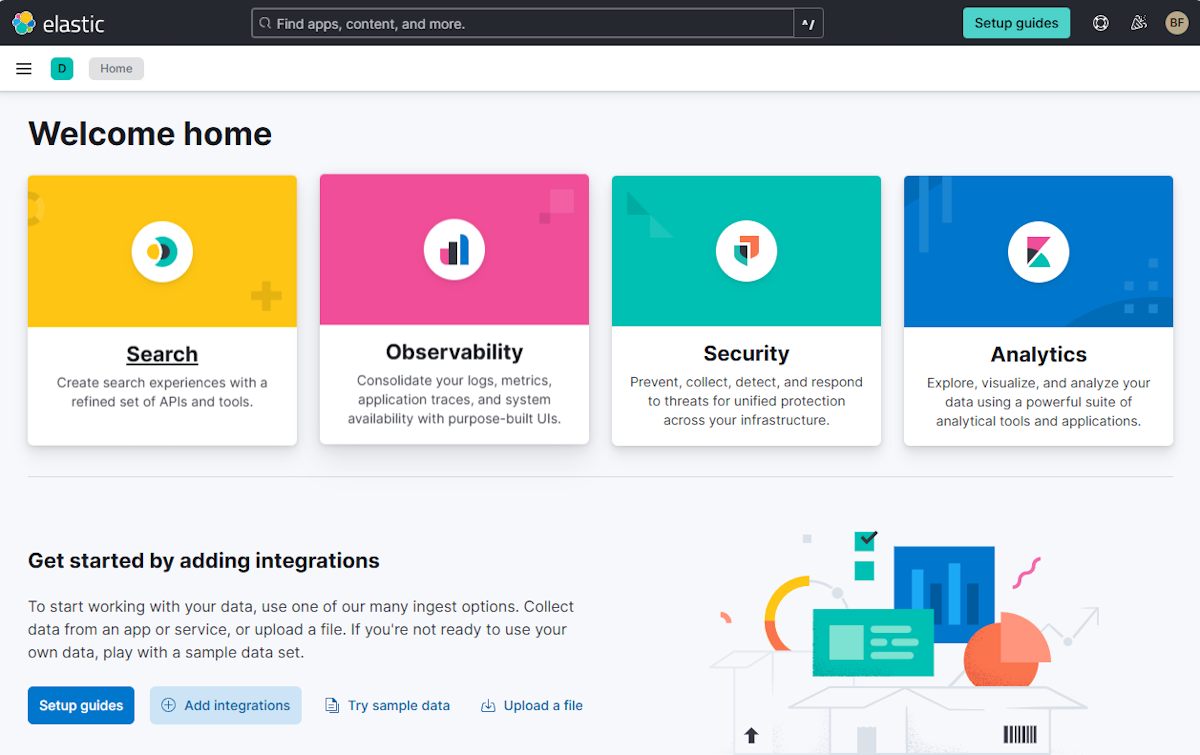
Después de iniciar sesión, el explorador navega a la página principal de Kibana, como se muestra en la captura de pantalla siguiente:
Configuración de registros personalizados elásticos e integración de registros de WLS
Siga estos pasos para configurar la integración de registros personalizada para WebLogic Server en Kibana:
Siga estos pasos para ir a la configuración de integración de Kibana:
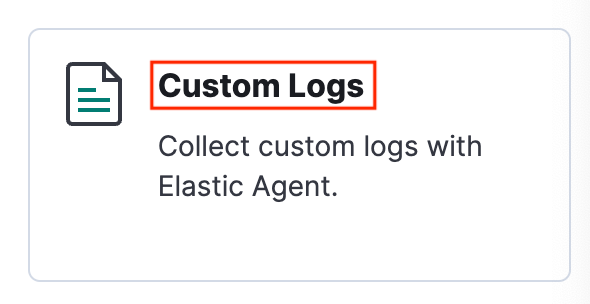
En la página de bienvenida de Kibana, busque Comienza añadiendo integraciones y luego seleccione Añadir integraciones.
Busque Registros personalizados y, a continuación, selecciónela.
Seleccione Agregar registros personalizados para ver las instrucciones para instalar elastic Agent y agregar integraciones.
Siga estos pasos para instalar el agente elástico:
Seleccione Instalar Elastic Agent, lo que muestra los pasos para la instalación.
SSH en la máquina WLS y, a continuación, cambie a privilegios raíz mediante el comando siguiente:
sudo su -Desde Kibana, copie el comando Linux Tar de la sección Instalar agente Elastic en su host y ejecútelo en la máquina WLS.
En el terminal de la máquina, confirme la instalación escribiendo y cuando se le solicite, como se muestra en el ejemplo siguiente:
Elastic Agent will be installed at /opt/Elastic/Agent and will run as a service. Do you want to continue? [Y/n]:yBusque el texto
Elastic Agent has been successfully installed.Este texto indica una instalación correcta. Si no ve este texto, solucione y resuelva el problema antes de continuar.
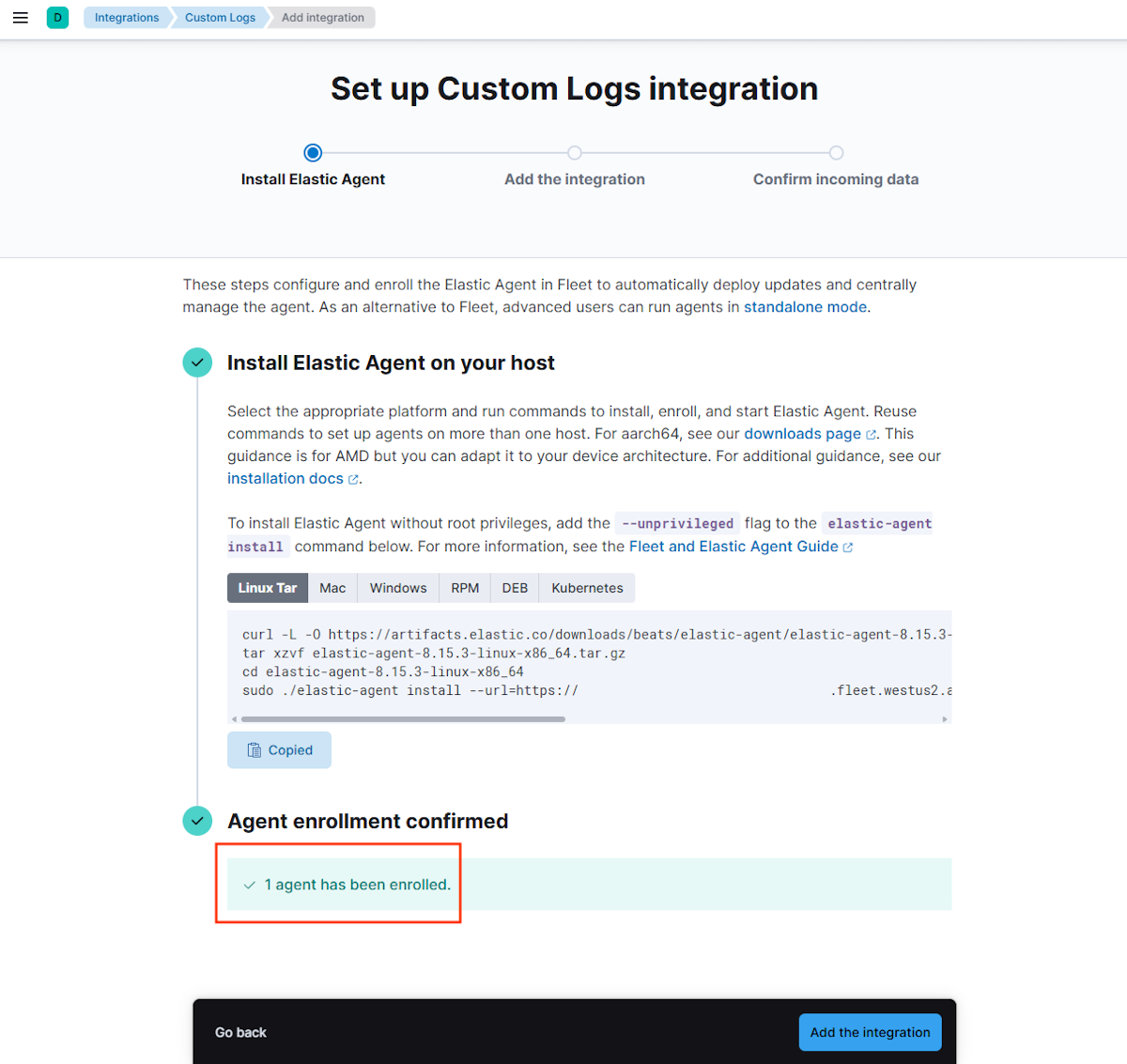
Compruebe la inscripción del agente. En Kibana, confirme la Inscripción del agente en Confirmar inscripción del agente.
Siga estos pasos para agregar la integración de los registros de dominio de WLS:
Seleccione Agregar la integración.
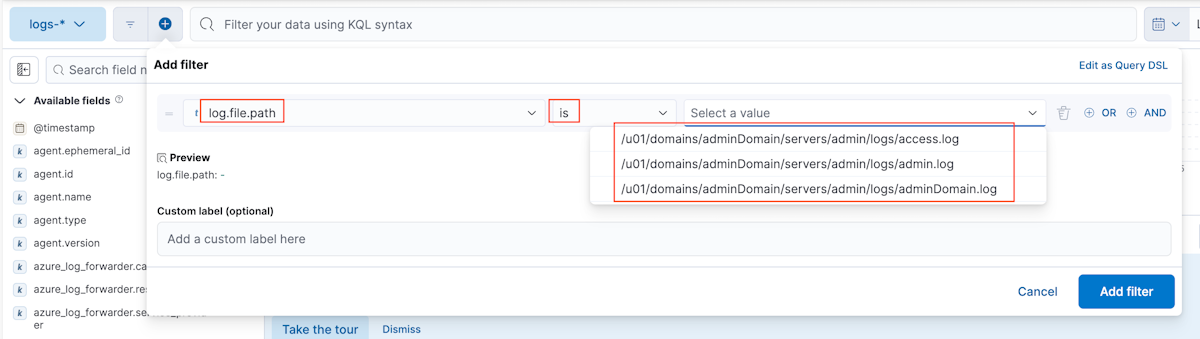
En Archivo de registro personalizado, configure las siguientes propiedades:
- Para Ruta del archivo de registro, utilice /u01/domains/adminDomain/servers/admin/logs/adminDomain.log.
- Para Nombre del conjunto de datos, utilice genérico.
Expanda Opciones avanzadas. Para Configuraciones personalizadas, establezca las siguientes propiedades:
- Para multiline.type, use el patrón .
- Para multiline.pattern, utilice "^####".
- Para multiline.negate, utilice true.
- Para multiline.match, utilice after.
Expanda Opciones avanzadas. En Nombre de integración, introduzca log-weblogic-domain-log.
Seleccione Confirmar datos entrantes para obtener una vista previa de los registros. A continuación, seleccione Ver activos ->Activos ->Vistas ->Logs para ver los registros de dominio en Kibana.
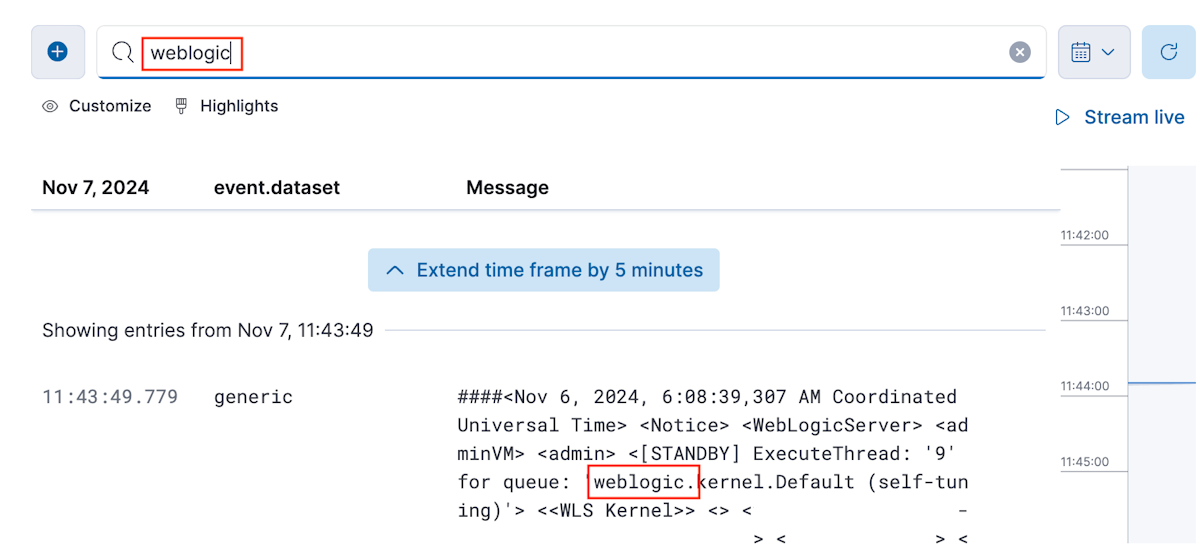
En el área de texto que contiene el texto Buscar mensajes de registro, introduzca la cadena weblogic y pulse Intro. Debería ver los mensajes de registro que contienen la cadena weblogic.
Siga estos pasos para agregar integraciones para los registros de servidor y los registros de acceso HTTP:
En Kibana, busque Integraciones y selecciónelo.
Seleccione Integraciones instaladas>registros personalizados>Agregar registros personalizados.
Escriba las configuraciones adecuadas de las listas siguientes para cada tipo de registro: servidor y registros de acceso HTTP. Después de rellenar todos los campos de configuración, seleccione Guardar y continuar y, a continuación, Guardar e implementar cambios.
Para el registro del servidor, use los siguientes valores:
Para Configuración de integración > Nombre de integración, utilice log-weblogic-server-log.
Para Archivo de registro personalizado > Ruta del archivo de registro, utilice /u01/domains/adminDomain/servers/admin/logs/admin.log.
Para Archivo de registro personalizado > Opciones avanzadas > Configuraciones personalizadas, utilice los siguientes valores:
- Para multiline.type, use el patrón .
- Para multiline.pattern, utilice "^####".
- Para multiline.negate, utilice true.
- Para multiline.match, utilice after.
Para ¿Dónde añadir esta integración? > Host existentes, utilice Mi primera directiva de agente.
Para los registros de acceso HTTP, use los siguientes valores:
- Para Configuración de la integración > Nombre de la integración, utilice log-http-access-log.
- Para Archivo de registro personalizado > Ruta del archivo de registro, utilice /u01/domains/adminDomain/servers/admin/logs/access.log.
- Para Archivo de registro personalizado > Opciones avanzadas > Configuraciones personalizadas, no se proporciona ninguna configuración.
- Para ¿Dónde añadir esta integración? > Host existentes, utilice Mi primera directiva de agente.
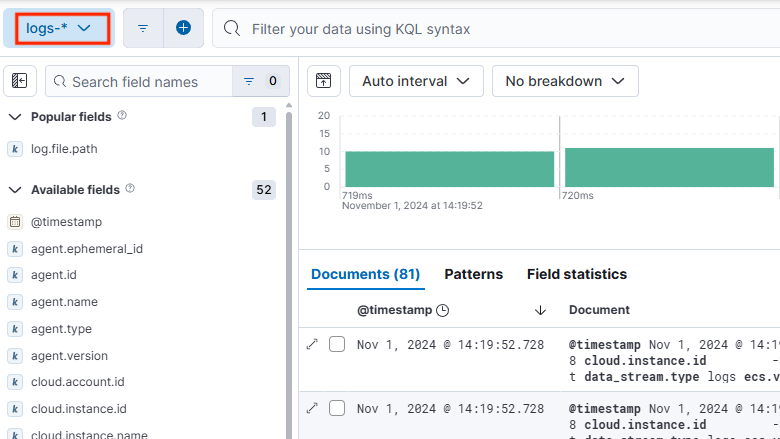
Buscar registros WLS en Kibana
Después de la integración, siga estos pasos para empezar a analizar los registros en Kibana:
Para acceder a la página Descubrir, abra el menú "hamburguesa". A continuación, en Análisis, seleccione Descubrir.
Para seleccionar el índice de registro, en la página Descubrir, seleccione logs-*.
Busque y filtre los registros de WLS. Para obtener más información sobre el uso de Discover, consulte Discover en la documentación de Kibana.
Nota
Si está ejecutando un clúster de WLS, es necesario instalar el Elastic Agent en cada máquina virtual y configurar los registros personalizados en los hosts correspondientes.
Limpieza de recursos
Si ya no usa la pila elástica o WLS, puede limpiarlas siguiendo los pasos descritos en esta sección.
Limpieza de WLS
Siga estos pasos para limpiar WLS:
En la página principal de Azure Portal, seleccione Grupos de recursos.
En el campo de texto Filtrar por cualquier campo..., escriba el nombre del grupo de recursos en el que creó la implementación de WLS.
Cuando la lista muestre el grupo de recursos, selecciónelo.
Desde la información general del grupo de recursos , seleccione Eliminar grupo de recursos .
En la sección ¿Está seguro de que desea eliminar sección?, escriba el nombre del grupo de recursos y, a continuación, seleccione Eliminar. Puede seguir trabajando con Azure Portal mientras se elimina el grupo de recursos y su contenido.
Limpieza de Elastic en Azure
Siga los mismos pasos que en la sección anterior para eliminar Elastic en Azure, pero use el nombre del grupo de recursos de la implementación de Elastic en Azure como grupo de recursos que se va a eliminar.
Paso siguiente
Continúe con el recorrido de migración mediante la exploración de WebLogic Server en Azure Virtual Machines.