How to disable TLS 1.0 on an Azure App Service Web App
UPDATE as of 17-APR-2018 you can, read about that here.
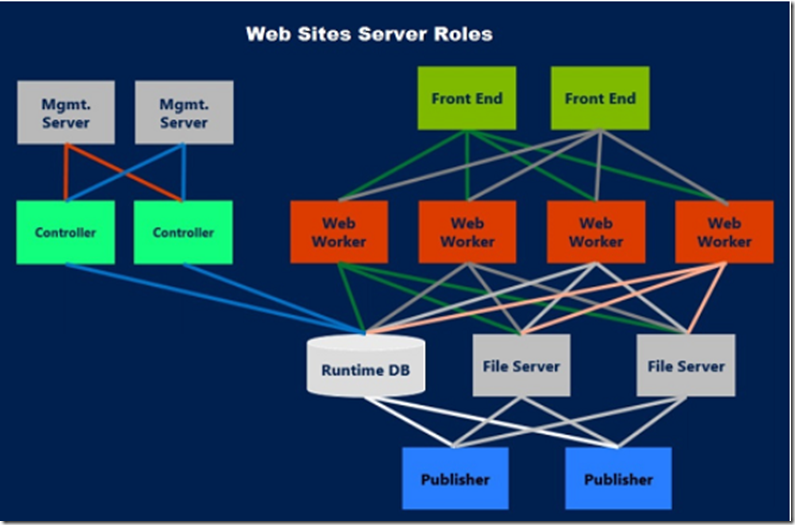
Short answer is, prior to 17-APR-2018, that you couldn't. (see alternative solution below) The reason is that when you deploy an Azure App Service it goes into a multi-tenant scale unit. A scale unit looks something like Figure 1, which I stole from here. Also, have a look at this forums discussion here.
Figure 1, Azure App Service scale unit, image taken from here
This scale unit has multiple customers running on it (i.e. multi-tenant). As SSL communication is offloaded on the Front Ends the only way to disable TLS 1.0 or TLS 1.1 (not supported) would be to make that configuration on the Front End, but then that would disable it for all other App Services running in that scale unit. Some customer may want it enabled for legacy reasons. NOTE: When you run in Basic, Standard or Premium mode the Web Worker in Figure 1 represents a virtual machine which is dedicated to the App Services running in your App Service Plan see here for more.
Solution
The solution is to get a scale unit all for yourself which is called an App Service Environment (ASE), see here. This gives you a scale unit and you can disable TLS 1.0, you cannot disable TLS 1.1 at the moment. The ASE also allows you to setup NSG and have more control over the feature.
You will need to access the resource explorer here and modifying the clusterSettings entry for the ASE, similar to the following and also discussed here.
"clusterSettings": [
{
"name": "DisableTls1.0",
"value": "1"
}
],
UPDATE #1: If you happen to get something like " 'Code': 'BadRequest', 'Message': 'An error occurred when updating the entry :" when trying disable TLS 1.0 on and App Service Environment, in resource explorer, in the same context as you where in when you received the error, look for an item named "dnsSuffix: <ASEName>.p.azurewebsites.net" and delete it. Then retry.
UPDATE #2: Apparently you can also try to put an Application Gateway in front of the App Service, but what I know is this only possible in front of an ILB ASE, but if you are going to deploy an ASE you wouldn't need the AG to disable TLS 1.0. See more about that here. Set-AzureRmApplicationGatewaySslPolicy -DisabledSslProtocols TLSv1_0, TLSv1_1 -ApplicationGateway $gw
UPDATE #3: I am not a PCI compliance officer and I am not clear on the date when the having TLS 1.0 enabled voids PCI compliance. However, it is my understanding that Azure App Services is PCI compliance and the removal or the ability to remove TLS 1.0 will happen before the compliance is voided. See here and here for some more information.
Comments
- Anonymous
May 04, 2017
A service like Trustwave is failing you for having TLS 1.0 enabled. You can download a document on their website to request a waiver until 2018, the official deadline for compliance. - Anonymous
June 16, 2017
WAF is another option, which used in this case would be a fancy way of saying reverse proxy with SSL termination at the proxy, which is what the application gateway is doing as well. There are a few options available in Azure, not just from Microsoft, virtual LTMs from F5 for example. - Anonymous
June 22, 2017
Having done this I found limitations and may not be for everyone. Some of the issues I ran into were Web Deploy did not work due to .net and had to create a group policy to modify some regkeys, also had to make sure that my Web App was set for .Net 4.6 when making out going connection or it would also try using TLS 1.0. Those I was able to fix. The one that I was not able to fix was that the Log Monitor, and Process Monitor require TLS 1.0 to be enabled or do not work, You can work around it by using Kudo, and maybe App Insights but If you are working on a new Branch/Slot you may not have(or want/need) App Insights enabled. In the end I felt that it there is still some kinks to work around before I could suggest using it, unless of course your compliance officer requires it. - Anonymous
September 10, 2017
@DubaStep is right, Application Gateway can be used to seamlessly achieve same. In a bid to pass PCI compliance, I used Application Gateway to disable TLS 1.0 and 1.1. - Anonymous
September 21, 2017
It would be a good feature to add an ability to disable TLSv1 with the standard PaaS offering. Also it would be good if there was an official timeline was published when this will be disabled to meet the 6/30/2018 deadline.- Anonymous
September 29, 2017
@Josh, it's not that simple or we'd have the option. The reason what is right at the beginning of the post and the whole reason this article exists. The phrase "multi-tenant scale unit" means it is on a shared host, meaning disabling it for one means disabling for all. There are still some that need TLS 1.0 now. You do have the option of disabling TLS 1.0 on your own, but it means moving your app service to a VM or using ASE as mentioned in this article.
- Anonymous