Hi Yaswanth Reddy,
I have tested retrieving Azure Activity Logs via the API in my local environment. Please run the PowerShell script below to check if you can view the activity logs where your Service Principal is performing actions on the subscription.
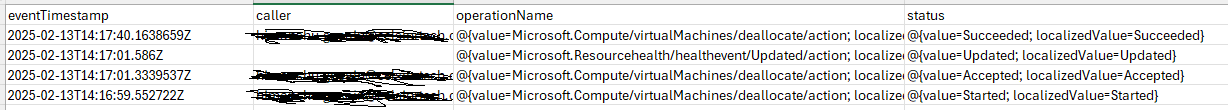
I have also attached the script's output for your reference
# Description: This script retrieves Azure Activity Logs for the last 60 minutes using a Service Principal Via API
##############################
# -----------------------------
# Step 1: Define Azure AD App (Service Principal) details
# -----------------------------
# Replace with your Azure AD Tenant ID
$tenantId = ""
# Replace with your Service Principal (App Registration) Client ID
$clientId = ""
# Replace with your Service Principal Client Secret (WARNING: Hardcoding secrets is not recommended)
$clientSecret = ""
# Replace with your Azure Subscription ID
$subscriptionId = ""
# -----------------------------
# Step 2: Obtain an Access Token
# -----------------------------
# Azure OAuth2 Token Endpoint for authentication
$tokenUrl = "https://login.microsoftonline.com/$tenantId/oauth2/token"
# Request body to obtain an access token (Using client credentials flow)
$body = @{
grant_type = "client_credentials" # Type of OAuth authentication flow
client_id = $clientId # Application (client) ID of Service Principal
client_secret = $clientSecret # Secret key for authentication
resource = "https://management.azure.com/" # Target Azure API resource
}
# Invoke REST API to fetch access token
$response = Invoke-RestMethod -Method Post -Uri $tokenUrl -ContentType "application/x-www-form-urlencoded" -Body $body
$accessToken = $response.access_token # Extract the access token from response
# -----------------------------
# Step 3: Define the Time Range (Last 60 Minutes)
# -----------------------------
# Get current time in UTC and subtract 60 minutes to filter logs
$startTime = (Get-Date).ToUniversalTime().AddMinutes(-60).ToString("yyyy-MM-ddTHH:mm:ssZ") # 1 hour ago
$endTime = (Get-Date).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ssZ") # Current time
# -----------------------------
# Step 4: Construct API Request for Azure Activity Logs
# -----------------------------
# Azure Monitor API Endpoint to fetch activity logs with time filter
$activityLogsUrl = "https://management.azure.com/subscriptions/$subscriptionId/providers/Microsoft.Insights/eventtypes/management/values?$filter=eventTimestampge '$startTime' and eventTimestamp le '$endTime'&api-version=2015-04-01"
# Headers for API request, including the Bearer token for authentication
$headers = @{
Authorization = "Bearer $accessToken" # Pass the access token for authentication
"Content-Type" = "application/json" # Define content type as JSON
}
# -----------------------------
# Step 5: Fetch Azure Activity Logs
# -----------------------------
# Call Azure Monitor REST API to retrieve activity logs
$logsResponse = Invoke-RestMethod -Method Get -Uri $activityLogsUrl -Headers $headers
# -----------------------------
# Step 6: Display & Export Logs
# -----------------------------
# Select relevant fields and export logs to a CSV file
$logsResponse.value | Select-Object eventTimestamp, caller, operationName, status | Export-Csv -Path ".\logs.csv" -NoTypeInformation
# Confirmation message
Write-Host "Logs exported successfully to logs.csv"
 Feel free to reach out if you have any further questions or need additional information—I’m happy to assist!
Feel free to reach out if you have any further questions or need additional information—I’m happy to assist!
Please provide your valuable comments 
Please do not forget to "Accept the answer” and “upvote it” wherever the information provided helps you, this can be beneficial to other community members.it would be greatly appreciated and helpful to others.
