Implement multifactor authentication
Earlier training that examined user authentication options also introduced Microsoft Entra multifactor authentication (MFA). This unit examines in greater detail how organizations enable MFA and how it works.
The multifactor authentication process
Passwords are the most common method of authenticating a sign-in to a computer or online service, but they're also the most vulnerable. People can choose easy passwords and use the same passwords for multiple sign-ins to different computers and services.
To provide an extra level of security for sign-ins, you must use multifactor authentication (MFA), which uses both a password, which should be strong, and a second verification method based on:
- Something you have with you that isn't easily duplicated, such as a smart phone.
- Something you uniquely and biologically have, such as your fingerprints, face, or other biometric attribute.
The second verification method isn't employed until after the system verifies the user's password. With MFA, even if an attacker compromises a strong user password, they don't have your smart phone or your fingerprint to complete the sign-in.
Microsoft Entra multifactor authentication helps increase security by requesting two authentication methods. Users must sign-in with a username and a password and then use a second authentication method. The second method can be acknowledging a phone call, text message, or an app notification on their mobile phone. If the system verifies the username, password, and second authentication method, the user can sign-in to Microsoft 365. The system can also enable users who authenticate from a federated, on-premises directory for multifactor authentication.
The following graphic shows the difference between the different authentication factors:
- Something the user knows (Password)
- Something the user owns (Device)
- Something the user is (Biometrics)
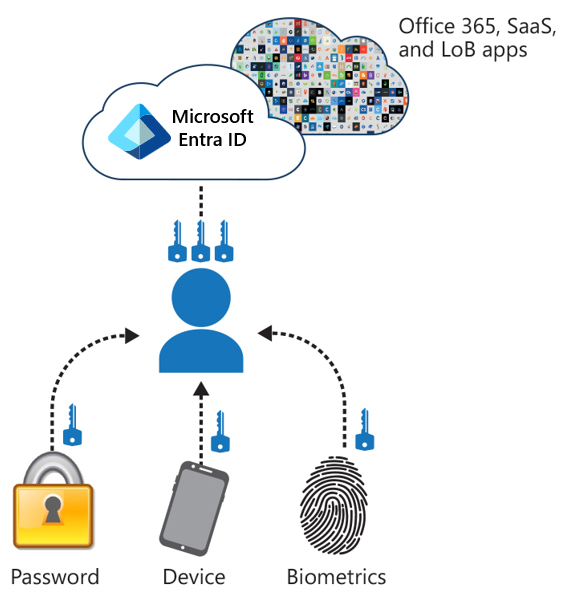
Multifactor authentication methods
Microsoft Entra multifactor authentication supports several methods of authentication, including:
- Phone call or text message verification. The default method of MFA in Microsoft 365. This method sends a verification code to the user's registered phone number through a phone call or text message.
- Microsoft Authenticator app. The app provides push notifications or one-time codes to verify the user's identity. The next training unit examines this MFA option.
- OATH hardware tokens. Physical tokens that generate a one-time password (OTP) for authentication.
- FIDO2 security keys. Physical security keys that support passwordless authentication. For more information, see Fast ID Online (FIDO) v2.0.
- Other third-party authenticator apps. Microsoft 365 also supports other authenticator apps that adhere to the Time-based One-Time Password (TOTP) protocol, such as Google Authenticator and Authy.
Microsoft 365 also offers Conditional Access policies that allow administrators to configure MFA based on specific conditions, such as location, device compliance, or user risk. This feature provides extra security by requiring MFA only when users meet certain conditions.
Note
Conditional Access policies were examined in an earlier training unit.
Enable multifactor authentication
MFA ensures that Microsoft 365 prompts users to provide extra verification when accessing sensitive data or performing certain actions. This extra verification can help protect the user's organization against unauthorized access and data breaches.
Microsoft 365 provides three ways for organizations to enable MFA:
- With Conditional Access policies
- With security defaults
- Legacy per-user MFA (not recommended for larger organizations)
Each of these methods is based on your Microsoft 365 plan, as outlined in the following table.
| Plan | Recommendation | Type of customer |
|---|---|---|
| All Microsoft 365 plans | Use Security Defaults, which require MFA for all user accounts. You can also configure per-user MFA on individual user accounts, but this method isn't recommended. | Small business |
| - Microsoft 365 Business Premium - Microsoft 365 E3 - Microsoft Entra ID P1 licenses |
Use Security Defaults or Conditional Access policies to require MFA for user accounts based on group membership, apps, or other criteria. | Small business to enterprise |
| - Microsoft 365 E5 - Microsoft Entra ID P2 licenses |
Use Microsoft Entra ID Protection and Conditional Access policies to require MFA based on sign-in risk criteria. | Enterprise |
The following sections outline each of these methods.
Use Conditional Access policies to enable MFA
Microsoft recommends that organizations use the Conditional Access feature to enable MFA. Conditional Access allows an organization to apply policies that control access to its cloud apps based on specific conditions, such as user location or device state.
Conditional Access policies are a set of rules that specify the conditions under which sign-ins are evaluated and allowed. For example, you can create a Conditional Access policy that states: If the user account name is a member of a group for users that are assigned the Exchange, user, password, security, SharePoint, or Global administrator roles, require MFA before allowing access.
This policy allows you to require MFA based on group membership, rather than trying to configure individual user accounts for MFA when they're assigned or unassigned from these administrator roles. You can also use Conditional Access policies for more advanced capabilities, such as requiring MFA for specific apps or when the sign-in is done from a compliant device, such as your laptop running Windows 10 or 11.
If an organization has more granular sign-in security needs, Conditional Access policies can offer it more control. Conditional Access lets you create and define policies that react to sign-in events and request other actions before a user is granted access to an application or service. These policies can allow regular sign-in when the user is on the corporate network or a registered device. They can also prompt for other verification factors when the user is remote or on a personal device.
Warning
Turn off both per-user MFA and Security Defaults before you enable Conditional Access policies. Per-user MFA and Security Defaults are baseline security features that provide a basic level of protection for all user accounts in an organization. When Conditional Access policies are enabled, they allow for more granular control and customization of access requirements based on specific conditions and scenarios. If you enable per-user MFA, Security Defaults, and Conditional Access policies simultaneously, it can lead to conflicts and inconsistencies in the authentication process, potentially resulting in unintended behavior or access issues.
An organization must have one of the following licenses to use Conditional Access policies:
- Microsoft 365 Business Premium
- Microsoft 365 E3 and E5
- Microsoft Entra ID P1 and Microsoft Entra ID P2 licenses
For small businesses with Microsoft 365 Business Premium, you can easily use Conditional Access policies with the following steps:
- Create a group to contain the user accounts that require MFA.
- Enable the Require MFA for global admins policy.
- Create a group-based Conditional Access policy with these settings:
- Assignments > Users and groups: The name of your group from Step 1 above.
- Assignments > Cloud apps or actions: All cloud apps.
- Access controls > Grant > Grant access > Require multifactor authentication.
- Enable the policy.
- Add a user account to the group created in Step 1 above and test.
- To require MFA for more user accounts, add them to the group created in Step 1.
This Conditional Access policy allows you to roll out the MFA requirement to your users at your own pace.
Enterprises should use Common Conditional Access policies to configure the following policies:
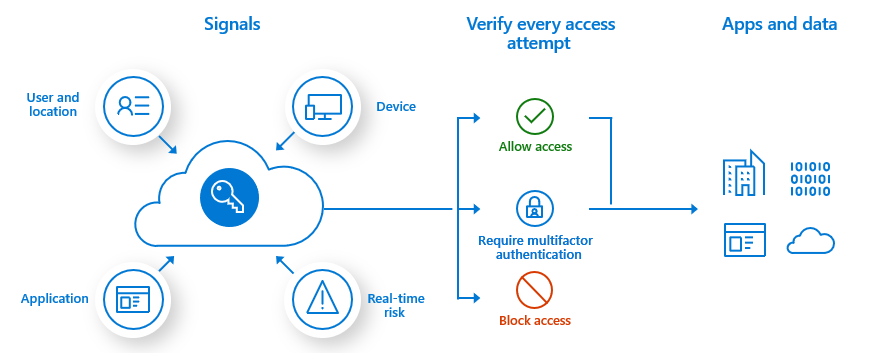
With Microsoft Entra ID Protection, you can create another Conditional Access policy to require MFA when sign-in risk is medium or high.
You can use Microsoft Entra ID Protection and risk-based Conditional Access policies with:
- Microsoft 365 E5
- Microsoft Entra ID P2 licenses
For more information, see this overview of Microsoft Entra ID Protection.
Use Security Defaults to enable MFA
Most organizations should begin by using either security defaults or Conditional Access policies to require MFA for their user account sign-ins. For most organizations, Security Defaults offer a good level of extra sign-in security. If your subscription is new, it might have Security Defaults already turned on for you automatically.
Security Defaults is a straightforward and easy-to-use option for enabling MFA in your organization. It requires minimal configuration, and organizations can quickly set it up. Security Defaults provides a basic level of security by turning on MFA, blocks legacy authentication protocols, and requires users to register for Microsoft Entra MFA. These features can help protect organizations from many common security threats.
The main drawback of using Security Defaults to turn on MFA is that you can't customize it based on specific conditions or scenarios. It's an all or nothing proposition. This requirement means that every user in an organization must use MFA when the company enables Security Defaults, regardless of each user's role, location, or the type of device they use. Organizations can find this requirement problematic if they have users who don't have access to a phone or other second factor device, or who limited connectivity to receive the MFA code. Additionally, some users can find MFA to be an inconvenience, which can result in resistance to the new security measures or decreased productivity.
Overall, using Security Defaults to enable MFA is a useful option for small or medium-sized organizations with limited IT resources, or for those organizations who need to quickly implement basic security measures. However, larger organizations with more complex security requirements might prefer the greater control and customization offered by Conditional Access policies.
You enable or disable security defaults from the Properties pane for Microsoft Entra ID in the Microsoft Entra admin center.
- Sign in to the Microsoft Entra admin center as a Security administrator, Conditional Access administrator, or Global administrator.
- In the Microsoft Entra admin center, in the left-hand navigation pane, select Overview.
- On the Overview page for your organization's tenant, the system displays the Overview tab by default. Select the Properties tab.
- Under the Security Defaults section, select the Manage security defaults link.
- On the Security defaults pane that appears, select in the Security defaults field. In the drop-down menu that appears, select Enabled.
- At the bottom of the pane, select Save.
Use legacy per-user MFA (not recommended for larger organizations)
Microsoft recommends using either security defaults or Conditional Access policies to require MFA for your user account sign-ins. However, if an organization can't use either of these methods, Microsoft strongly recommends enabling MFA on a per-user basis for user accounts that have administrator roles, especially the Global administrator role, for any size subscription.
While Security Defaults and Conditional Access policies can turn on MFA for all users in an organization, using the Microsoft 365 admin center enables you to turn on MFA on a per user basis. Per-user MFA is a quick and easy way to provide increased security for one or more user accounts. You can turn MFA on or off for whichever users you select.
Like Security Defaults, using the Microsoft 365 admin center to enable per-user MFA is a useful option for:
- Small or medium-sized organizations with limited IT resources.
- Those organizations who need to quickly implement basic security measures.
However, Microsoft recommends that larger organizations with more complex security requirements use Conditional Access policies or Security Defaults to implement MFA. For these organizations, Microsoft doesn't recommend using per-user MFA for the following reasons:
- Complexity and management. Per-user MFA requires individual configuration for each user. Managing MFA settings at this granular level can become cumbersome, especially in large organizations. Doing so places a large burden on administrators, who must handle user-specific requests, troubleshoot issues, and maintain consistency across the user base.
- Risk of misconfiguration. When you factor in human error, configuring MFA for each user manually increases the risk of misconfiguration. A mistake in settings could lead to security gaps or unnecessary disruptions. Additionally, misconfiguration can also lead to inconsistent policies. Different users might end up with varying MFA policies, leading to inconsistencies in security posture.
- Legacy authentication. Per-user MFA doesn't prevent legacy authentication, such as protocols like SMTP, IMAP, and POP3, from using only a password. Modern authentication prompts users to register MFA methods, but legacy protocols bypass this control. With this type of gap in an organization's security, attackers can exploit legacy authentication if they compromise a user’s credentials.
- Lack of contextual control. Conditional Access provides contextual control based on factors like location, device, and application. Per-user MFA lacks this context-awareness. Conditional Access also allows dynamic decisions based on risk levels, such as blocking access from suspicious locations, which isn't available with per-user MFA.
- Scalability and consistency. As your organization grows, managing per-user MFA becomes increasingly challenging. Conditional Access or security defaults ensure consistent MFA policies across all users.
A Microsoft 365 Administrator can enable multifactor authentication on a per-user basis in the Microsoft 365 admin center by completing the following steps:
- In the Microsoft 365 admin center, in the left-hand navigation pane, select Settings and then select Org settings.
- On the Org settings page, under the Services tab (which is displayed by default) select Multifactor authentication.
- In the Multifactor authentication pane that appears, select Configure multifactor authentication.
- On the multifactor authentication page, two tabs are available - one for users and one for service settings.
- On the users tab, you can enable (or disable) multifactor authentication for one or more users. You can begin by filtering the users who are displayed by selecting one of the options in the View drop-down menu. Once the system displays list of users that you want, you can update their multifactor authentication settings.
- To enable multifactor authentication for one or more users, complete the following steps:
- Select the users that you want to enable for multifactor authentication.
- In the user pane that appears, you can update the multifactor authentication settings for the users by selecting Manage user settings.
- In the Manage user settings window that appears, you can select any of the following options for the selected users, and then select save:
- Require selected users to provide contact methods again.
- Delete all existing app passwords generated by the selected users.
- Restore multifactor authentication on all remembered devices.
- In the user pane that appears, you can turn on multifactor authentication for the selected users by selecting Enable.
- In the About enabling multifactor auth window that appears, you can select the provided links to learn more about multifactor authentication. When you're ready, select the enable multifactor auth button, and then select close once the update is complete.
- The value in the multifactor AUTH STATUS column should change from Disabled to Enabled for each selected user.
- To enable (or disable) multifactor authentication for all the users in a CSV file by using the bulk import feature, complete the following steps:
- Select the bulk update button that appears at the top of the screen.
- In the Select a CSV file window that appears, you can select Download a sample file to see the file format the system requires. It includes each user's alias and the option to either enable or disable multifactor authentication for the user.
- When your file is ready, select Browse for file and select your CSV file.
- Select the arrow icon in the bottom right corner of the window.
- The Verifying file window that appears displays the number of user accounts the system verified. Select the arrow icon in the bottom right corner of the window to update the users.
- The Done window indicates the number of users the system updated. Close the window.
- On the service settings tab, you can update the global multifactor authentication settings for the organization. This tab enables you to update the following settings:
- app passwords section
- Allow users to create app passwords to sign-in to non-browser apps.
- Don't allow users to create app passwords to sign-in to non-browser apps.
- trusted ips section
- Skip multifactor authentication for requests from federated users on my intranet.
- Skip multifactor authentication for requests from following ranges of IP address subnets (enter the IP address subnets in the provided field).
- verification options section
- Select one or more of the multifactor authentication options:
- Call to phone. Users receive a phone call with instructions. The system signs in the user after they press the pound key.
- Text message to phone (selected by default). Users receive a text message containing a six-digit code that they must enter into the Microsoft 365 portal.
- Notification through mobile app (selected by default). Users configure a smartphone app that receives a notification that users need to confirm to sign in to Microsoft 365. Smartphone apps are available for Windows phone, iPhone, and Android devices.
- Verification code from mobile app or hardware token (selected by default). Users configure a smartphone app and enter the six-digit code from the app into the portal.
- Select one or more of the multifactor authentication options:
- remember multifactor authentication on trusted device section
- Allow users to remember multifactor authentication on devices they trust (between one to 365 days)
- Number of days users can trust devices for (the default value is 90 days)
- app passwords section
Optimize reauthorization prompts for Microsoft Entra multifactor authentication
One of the system settings options is to Remember multifactor authentication on trusted devices. This setting determines how often users must reauthenticate using their multifactor authentication method. You can optionally select the number of days that trusted devices can remember a user's multifactor authentication. Organizations can configure these reauthentication settings as needed for their environment, and for the user experience they want.
The Microsoft Entra default configuration for user sign-in frequency is a rolling window of 90 days. However, for optimal experience, Microsoft recommends that you use Conditional Access sign-in frequency to extend session lifetimes on trusted devices, locations, or low-risk sessions as an alternative to this setting. If you decide to implement this Remember multifactor authentication on trusted devices setting, be sure to extend the duration to 90 or more days.
Asking users for credentials on a frequent basis seems like a sensible thing to do, but doing so can cause problems. If users frequently enter their credentials without thinking, they can unintentionally supply them to a malicious credential prompt. As such, it can sound alarming to not ask for a user to sign back in, though any violation of IT policies revokes the session. Some examples include:
- a password change
- a noncompliant device
- an account disable operation.
Microsoft recommends the following configurations to give users the right balance of security and ease of use by asking them to sign-in at the right frequency:
- If you have Microsoft Entra Premium:
- Enable single sign-on (SSO) across applications using managed devices or Seamless SSO.
- If the user requires reauthorization, use a Conditional Access sign-in frequency policy.
- For users that sign-in from unmanaged devices or mobile device scenarios, persistent browser sessions may not be preferable. In this scenario, you can use Conditional Access to enable persistent browser sessions with sign-in frequency policies. Limit the duration to an appropriate time based on the sign-in risk, where a user with less risk has a longer session duration.
- If you have Microsoft 365 apps licenses or the free Microsoft Entra tier:
- Enable single sign-on (SSO) across applications using managed devices or Seamless SSO.
- Keep the Remain signed-in option enabled and guide your users to accept it.
- For mobile device scenarios, ensure your users use the Microsoft Authenticator app. This app acts as a broker to other Microsoft Entra federated apps. It reduces the authentication prompts on the device.
Note
Microsoft's research shows that these settings are right for most tenants. Some combinations of these settings, such as Remember multifactor authentication and Remain signed-in, can result in prompts for your users to authenticate too often. Regular reauthorization prompts are bad for user productivity and can make them more vulnerable to attacks.
Additional reading. For more information, see How it works: Microsoft Entra multifactor authentication.