Enable pass-through authentication
Microsoft Entra pass-through authentication (PTA) is a Microsoft 365 feature that can help enhance the security of user access to Microsoft 365 services. With PTA, users can authenticate to Microsoft 365 services using their on-premises Active Directory credentials, without the need to store passwords in the cloud. This design can help reduce the risk of password-related attacks, such as phishing or password spraying.
PTA also allows you to enforce policies such as multifactor authentication (MFA) and Conditional Access for Microsoft 365 services. So even if an attacker stole a user's on-premises credentials, they must still provide other authentication factors, such as a one-time passcode or a biometric factor, to gain access to Microsoft 365 services.
In addition, PTA provides real-time authentication validation. The system sends authentication requests directly to on-premises Active Directory rather than routing them through the cloud. This design can help improve authentication performance and reduce the risk of latency-related issues.
Overall, PTA can be an important component of a secure user access strategy in Microsoft 365, especially for organizations that:
- Need to maintain on-premises identity systems.
- Want to minimize the risk of password-related attacks.
Earlier training that examined user authentication options introduced you to Microsoft Entra pass-through authentication (PTA). This unit examines in greater detail the mechanics of how PTA works and how organizations enable it.
So why should organizations implement PTA?
Well, users typically prefer to maintain one set of sign-in credentials for both cloud and on-premises resources. The common sentiment is the fewer usernames and passwords to remember, the better. Many organizations achieve this goal by using Microsoft Entra Connect Sync with password hash synchronization. With this feature, Microsoft 365 completes password validation in the cloud.
However, some organizations prefer to have all authentication done on-premises. Companies that prefer on-premises authentication usually have a security requirement to immediately enforce on-premises user account states, password policies, and sign-in hours. In the past, organizations who preferred on-premises authentication would deploy Active Directory Federation Services (AD FS) and configure their Microsoft Entra tenant in federated mode. The system then directed each authentication request for resources either on-premises or in the cloud to the AD FS server the organization deployed locally.
The problem with this AD FS solution is that deployment and management of the locally deployed AD FS infrastructure was often too demanding, costly, and complex for many organizations. To address this issue, Microsoft updated Microsoft Entra Connect Sync to include an optional feature called Microsoft Entra pass-through authentication.
Microsoft Entra pass-through authentication ensures that password validation for services relying on Microsoft Entra ID always runs against an on-premises Active Directory. If PTA fails, the system runs automatic failover to password hash synchronization if the organization enabled automatic failover. Unlike the AD FS solution, PTA is easy to implement and maintain.
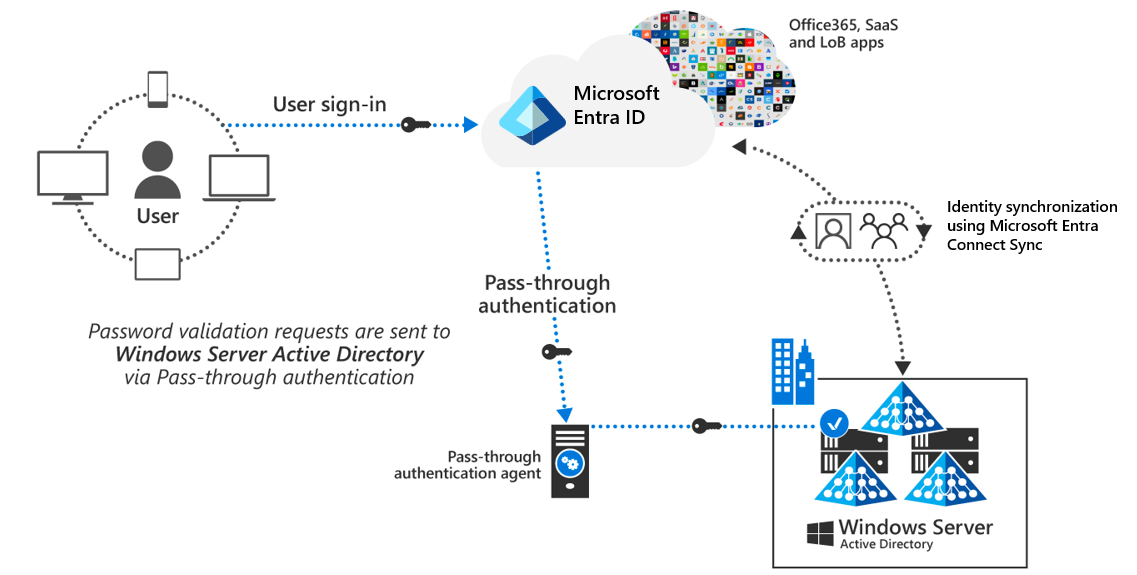
The Microsoft Entra pass-through authentication process
Microsoft Entra pass-through authentication is configured by using Microsoft Entra Connect Sync. It works by using an on-premises agent that listens for external password validation requests. An organization can deploy this agent to one or more servers to provide high availability. There's no need to deploy this server to the perimeter network, as all communication is outbound only. The organization should join the server that runs the agent for pass-through authentication to the Active Directory domain that contains the company's users.
The following graphic shows how the user sign-in process works when implementing PTA. In summary:
- The system displays the Microsoft Entra sign-in page to a user when they access a cloud service that relies on Microsoft Entra ID.
- After the user enters their credentials, the Microsoft Entra service checks if the organization configured the connector for pass-through authentication for the user’s domain.
- If the organization configured the connector, the system places the user's credentials on the connector queue for validation.
- A connector agent deployed on-premises then retrieves the user's credentials and authenticates them against the locally deployed Active Directory.
- The system returns the Active Directory's response to the connector, which in turn provides this response to Microsoft Entra ID.
Enabling Microsoft Entra pass-through authentication
To enable Microsoft Entra pass-through authentication, an organization must:
- Run the Microsoft Entra Connect Sync Setup Wizard.
- Select the Pass-through authentication option on the User Sign-in page.
An organization must deploy the first connector for pass-through authentication on the same server where Microsoft Entra Connect Sync runs. Microsoft recommends that organizations deploy an extra connector on at least one more server. Doing so helps achieve load balancing between the set of available connectors for both high availability and redundancy. An organization can download the Microsoft Entra Application Proxy Connector as a separate installation for other servers.
Organizations must ensure the availability of all ports required by Microsoft Entra pass-through authentication. The following table identifies these ports.
| Port | Description |
|---|---|
| 80 | Enables outbound HTTP traffic for security validation such as TLS/SSL certificate revocation lists. |
| 443 | Enables user authentication against Microsoft Entra ID. |
| 8080/443 | Enables the Connector bootstrap sequence and Connector automatic update. |
| 9090 | Enables Connector registration (required only for the Connector registration process). |
| 9091 | Enables Connector trust certificate automatic renewal. |
| 9352, 5671 | Enables communication between the Connector and the Microsoft Entra service for incoming requests. |
| 9350 | [Optional] Enables better performance for incoming requests. |
| 10100–10120 | Enables responses from the connector back to Microsoft Entra ID. |
Additional reading. For more information, see User sign-in with Microsoft Entra Pass-through Authentication.