Manage user passwords
Microsoft 365 helps provide secure access by requiring users to sign in with a password. It also includes various password management features, including:
- Setting password expiration
- Resetting user and administrator passwords
- Eliminating bad passwords
The following sections examine these features. Keep in mind that users must have one of the following roles to perform these tasks:
- The Global Administrator, Security Administrator, and Privileged Role Administrator roles have the permissions necessary to perform all these password management tasks.
- The User Administrator and Password Administrator roles can reset passwords.
Setting password expiration
As an administrator, you can make user passwords expire after a defined number of days, or set passwords to never expire. The default password expiration policy in Microsoft 365 sets users' passwords to never expire. Why? Because current research strongly indicates that mandated password changes do more harm than good. They drive users to choose weaker passwords, reuse passwords, or update old passwords in ways that attackers can easily guess. Users often select predictable passwords composed of sequential words and numbers that are closely related to each other. In these cases, cybercriminals can easily predict the next password based on the previous password.
Tip
Password expiration requirements offer no containment benefits because cybercriminals almost always use credentials as soon as they compromise them. As such, Microsoft recommends enabling multifactor authentication, which is a more effective alternative to periodic password changes.
Should your organization choose to implement a password expiration policy, it can do so through the Microsoft 365 admin center. To change the default password expiration policy, your Microsoft 365 administrator should complete the following steps:
- Sign in to the Microsoft 365 admin center and, if necessary, select Show all in the navigation pane.
- In the navigation pane, select Settings and then select Org settings.
- On the Org settings page, the Services tab is displayed by default. Select the Security & privacy tab.
- In the Security & privacy tab, select Password expiration policy.
- In the Password expiration policy pane that appears, the Set passwords to never expire (recommended) option is selected by default. Select this option to clear the check box. Doing so enables the Days before passwords expire option.
- In the Days before passwords expire field, specify the number of days between 14 and 730 for password expiration.
- Select Save.
Let's assume an organization changed its password expiration policy so that passwords expire after 60 days. What happens if a user doesn't change their password before the expiration time elapses? There are two options:
- The user can still change it themselves by using the Password update page that appears the next time they sign in.
- An administrator can reset their password for them.
Resetting user passwords
If necessary, a Microsoft 365 administrator can reset a password for one or more users on the Active users page. You can choose from the following options:
- Assign a new, randomly generated password or a password of your choice.
- Select whether users need to change their password at their next sign-in.
Note
Microsoft 365 also includes a self-service password reset (SSPR) feature that enables users to reset their own password without requiring intervention by an administrator. However, SSPR isn't enabled by default. Instead, the Microsoft 365 Administrator must enable SSPR for all users or for specific groups. This feature is covered in greater detail in a later unit in this training module.
Resetting admin passwords
If an administrator forgets their own password, the two available options are:
- Ask another administrator to reset it for you. In this case, the other administrator must be either a Global admin, a User Management admin, or a Password admin. However, if the administrator who forgot their password is a Global admin, another Global administrator must reset it for them.
- Reset the password yourself. On the sign-in page for Microsoft 365, the "Can’t access your account?" link enables a user to reset their own password. After following the instructions provided in the link, the system sends an email with a link that enables the user to reset their password. If a user wants to reset their own password, they must first supply an alternative email address in their account settings. The email address can't be their Microsoft 365 email address. Additionally, if the organization uses either a custom domain name or directory synchronization, the user must update their account details with a phone number that can receive text notifications. In turn, the system sends an automatically generated code in a text message to this phone number. Once the user receives the message, they must enter this code on the mobile phone verification page.
Caution
When resetting the password yourself, you must complete the entire admin password reset process within 10 minutes; otherwise, you must start the process over.
Eliminating bad passwords
Many security guidance documents recommend that you:
- Don't use the same password in multiple places.
- Make passwords complex.
- Avoid derivatives of the word "password," such as P@$$w0rd or Pa55word.
- Avoid simple passwords like pw123, or your first or last names
Organizations can provide its users with guidance on how to choose passwords. However, many users often still use weak or insecure passwords. Microsoft Entra Password Protection detects and blocks known weak passwords and their variants. It can also block other weak terms that are specific to an organization.
Important
Azure Active Directory (Azure AD) is now Microsoft Entra ID. Learn more.
Microsoft Entra Password Protection automatically applies default global banned password lists to all users in a Microsoft Entra tenant. To support your own business and security needs, you can also define entries in a custom banned password list. When users change or reset their passwords, Microsoft 365 checks these banned password lists to enforce the use of strong passwords. To access Microsoft Entra Password Protection, you must be assigned one of the following roles: Global Administrator, Security Administrator, or Privileged Role Administrator.
Tip
Organizations shouldn't rely solely on strong passwords enforced by Microsoft Entra Password Protection. They should also use other features like Microsoft Entra Multi-Factor Authentication.
Global banned password list
Microsoft's Microsoft Entra Identity Protection team constantly analyzes Microsoft Entra security telemetry data looking for commonly used weak or compromised passwords. As part of their analysis, the team looks for base terms that users often use as the basis for weak passwords. When the team finds weak terms, they add them to the global banned password list. The contents of the global banned password list aren't based on any external data source. Instead, the results of Microsoft Entra security telemetry and analysis determine the list's contents.
Microsoft 365 uses the current version of the global banned password list to validate the strength of any changed or reset password. This validation check results in stronger passwords for all Microsoft Entra ID customers. Microsoft 365 automatically applies the global banned password list to all users in a Microsoft Entra tenant. There's nothing to enable or configure, nor can an organization disable the list.
Note
Cyber-criminals also use similar strategies in their attacks to identify common weak passwords and variations. To improve security, Microsoft doesn't publish the contents of the global banned password list.
Custom banned password list
Some organizations want to improve security and add their own customizations on top of the global banned password list. To add your own entries, you can use the custom banned password list. An organization should focus the terms it adds to its custom banned password list based on company-specific terms. For example:
- Brand names
- Product names
- Locations, such as company headquarters
- Company-specific internal terms
- Abbreviations that have specific company meaning
For example, consider the fictional organization named Fabrikam. The company operates from London. Fabrikam is a plastics manufacturer whose primary product is the world-renowned "Fabrikam Widget." For Fabrikam, it would be wasteful and less secure to block specific variations of these terms, such as:
- "Fabrikam!1"
- "Fabrikam@London"
- "FabrikamWidget"
- "!Fabrikam"
- "LondonHQ"
Instead, it would be much more efficient and secure to block only the key base terms, such as:
- "Fabrikam"
- "London"
- "Widget"
The password validation algorithm then automatically blocks weak variants and combinations.
When an organization adds terms to the custom banned password list, Microsoft Entra Password Protection combines the terms with the terms in the global banned password list. Microsoft 365 then validates password change or reset events against the combined set of these banned password lists.
Microsoft Entra ID limits the custom banned password list to a maximum of 1,000 terms. Microsoft didn't design the list for blocking a large number of passwords.
Tip
To fully receive the benefits of the custom banned password list, you should first understand how the system evaluates passwords before adding terms to the custom banned list. This approach lets you efficiently detect and block large numbers of weak passwords and their variants.
To enable the custom banned password list and add entries to it, complete the following steps in Microsoft Entra Password Protection:
Sign in to the Microsoft 365 admin center with either a Global Administrator, Security Administrator, or Privileged Role Administrator account.
In the Microsoft 365 admin center, in the navigation pane under the Admin centers group, select Identity.
In the Microsoft Entra admin center, select Protection in the navigation pane to expand the group, and then select Authentication methods.
On the Authentication methods | Policies page, in the middle pane under the Manage section, select Password protection.
On the Authentication methods | Password protection page, set the Enforce custom list option to Yes.
Add strings to the Custom banned password list, one string per line. The following considerations and limitations apply to the custom banned password list:
- The custom banned password list can contain up to 1000 terms.
- The custom banned password list is case-insensitive.
- The custom banned password list considers common character substitution, such as "o" and "0", or "a" and "@".
- The minimum string length is four characters, and the maximum is 16 characters.
Specify your own custom passwords to ban, as shown in the following example
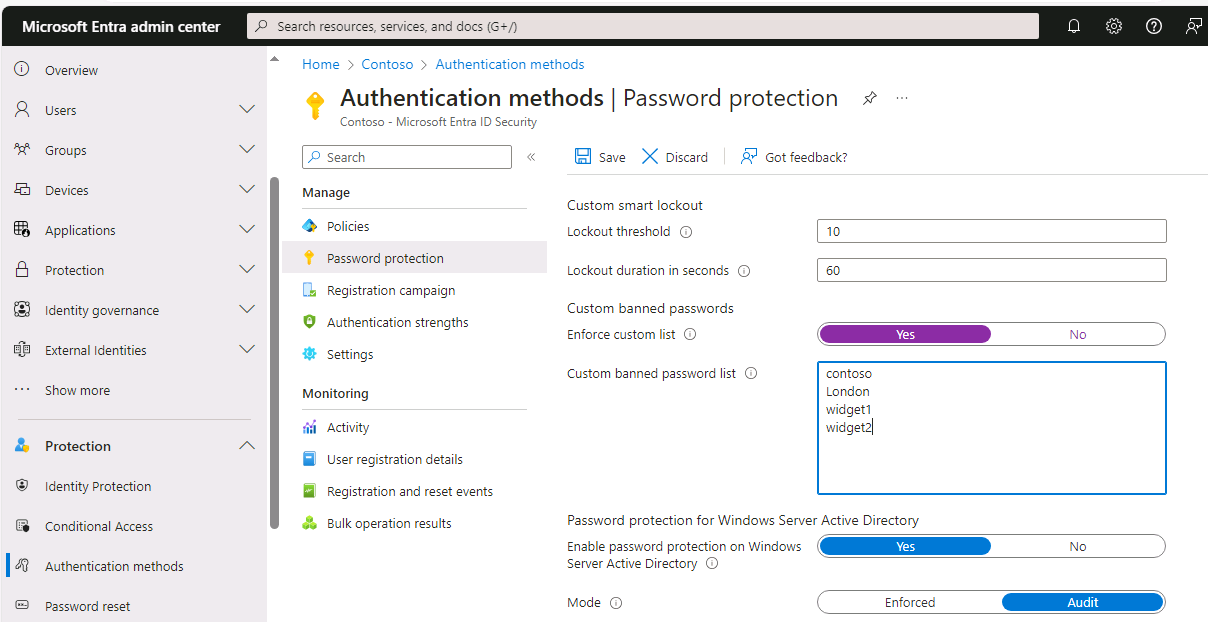
Set the Enable password protection on Windows Server Active Directory option to Yes.
Caution
If you set this option to No, all deployed Microsoft Entra Password Protection DC agents go into a quiescent mode where all passwords are accepted as-is. No validation activities are performed, and audit events aren't generated.
To enable the custom banned passwords and your entries, select Save on the menu bar.
Warning
It may take several hours for the system to apply updates to the custom banned password list.
For a hybrid environment, you can also deploy Microsoft Entra password protection to an on-premises environment. The system uses the same global and custom banned password lists for both cloud and on-premises password change requests.
Password spray attacks and third-party compromised password lists
Microsoft Entra Password Protection helps organizations defend against password spray attacks. Most password spray attacks don't attempt to attack any given individual account more than a few times. Otherwise, such behavior increases the likelihood of detection, either through account lockout or other means.
Instead, most password spray attacks submit only a few of the known weakest passwords against each of the accounts in an organization. This technique allows the attacker to quickly search for an easily compromised account and avoid potential detection thresholds.
Microsoft Entra Password Protection efficiently blocks all known weak passwords that hackers are likely to use in password spray attacks. It bases this protection on real-world security telemetry data from Microsoft Entra ID to build the global banned password list.
There are third-party websites that enumerate millions of compromised passwords from previous publicly known security breaches. It's common for third-party password validation products to be based on brute-force comparison against those millions of passwords. However, those techniques aren't the best way to improve overall password strength given the typical strategies used by password spray attackers.
Note
The global banned password list isn't based on any third-party data sources, including compromised password lists.
The global banned password list is small in comparison to some third-party bulk lists. However, Microsoft sources its content from real-world security telemetry of actual password spray attacks. This approach improves the overall security and effectiveness, and the password validation algorithm also uses smart fuzzy-matching techniques. As a result, Microsoft Entra Password Protection efficiently detects and blocks millions of the most common weak passwords.
Error messages that users see
When a user attempts to reset or change a password to banned value, the system displays one of the following error messages:
- "Unfortunately, your password contains a word, phrase, or pattern that makes your password easily guessable. Please try again with a different password."
- "Unfortunately, you can't use that password because it contains words or characters that have been blocked by your administrator. Please try again with a different password."
- "We've seen that password too many times before. Choose something harder to guess."
- "Choose a password that's harder for people to guess."
License requirements
| Users | Microsoft Entra Password Protection with global banned password list | Microsoft Entra Password Protection with custom banned password list |
|---|---|---|
| Cloud-only users | Microsoft Entra Free | Microsoft Entra Premium P1 or P2 |
| Users synchronized from on-premises AD DS | Microsoft Entra Premium P1 or P2 | Microsoft Entra Premium P1 or P2 |
Note
If an organization has on-premises AD DS users that it doesn't synchronize to Microsoft Entra ID, they also benefit from Microsoft Entra Password Protection based on existing licensing for synchronized users.
Knowledge check
Choose the best response for each of the questions below.