Explore Security Defaults in Microsoft Entra ID
Microsoft Entra ID includes a set of preconfigured security settings called security defaults. Organizations can enable security defaults to provide baseline security for all users and applications in a Microsoft Entra tenant. Enabling security defaults is a simple and effective way to improve the security posture of your Microsoft Entra tenant without having to configure each security feature separately. However, it's important to note that security defaults provide basic security and might not meet the specific security requirements of all organizations. As a result, some organizations require other security features or configure their own custom policies to meet their specific security needs.
When an organization enables security defaults, the system automatically enables the following security features for all users in its Microsoft Entra tenant:
- Multifactor authentication (MFA) for all users.
- Block legacy authentication protocols.
- Require users to register for Microsoft Entra multifactor authentication when necessary.
- Require administrators to perform MFA.
- Protect privileged activities like access to the Microsoft Entra admin center.
This unit examines each of these features in greater detail.
Who should you use security defaults?
Given the inherent challenges in managing security, Microsoft makes security defaults available to everyone. In today's environment, identity-related attacks such as password spray, replay, and phishing commonly occur. Organizations stop more than 99.9% of these identity-related attacks by using multifactor authentication and blocking legacy authentication.
Microsoft wants to ensure that all organizations have at least a basic level of security enabled at no extra cost. As such, it designed Microsoft Entra security defaults for:
- Organizations who want to increase their security posture, but don't know how or where to start.
- Organizations using the free tier of Microsoft Entra licensing.
- Organizations that don't use Conditional Access policies.
Warning
Organizations can't use security defaults if they currently use Conditional Access policies. Conditional Access and security defaults are mutually exclusive. You can use one but not the other.
If an organization has Microsoft Entra Premium licenses, then Microsoft Entra security defaults may not be the right security solution for it. Why? Because Microsoft Entra Premium licenses provide access to more advanced security features than what's available with Microsoft Entra security defaults.
While Microsoft Entra security defaults provide a basic level of security, they may not meet the specific security requirements of all organizations, especially companies with more complex security needs. For example, Microsoft Entra Premium licenses provide access to features such as:
- Conditional Access policies, which allow organizations to configure granular access controls based on specific conditions such as user location, device state, and risk level.
- Identity Protection, which provides insights into identity risk events and allows organizations to configure policies to mitigate risk.
- Privileged Identity Management, which allows organizations to manage and monitor privileged access to resources in Microsoft Entra.
In summary, Microsoft Entra security defaults provide an excellent starting point for organizations that are just getting started with Microsoft Entra ID. However, organizations with Microsoft Entra Premium licenses should probably consider using more advanced security features to ensure they satisfy their security needs.
Enable security defaults
Organizations might already have security defaults enabled if Microsoft created their tenant on or after October 22, 2019. To protect all of its customers, Microsoft includes security defaults for all new tenants at creation. However, as previously mentioned, it's up to each organization to determine whether to enable this feature given its Microsoft Entra licensing and security requirements.
Important
Enabling security defaults immediately enforces multifactor authentication for all users in your tenant and blocks legacy authentication protocols. Therefore, before enabling security defaults, you should ensure that your organization is ready for these changes and you should notify your users of the new security requirements.
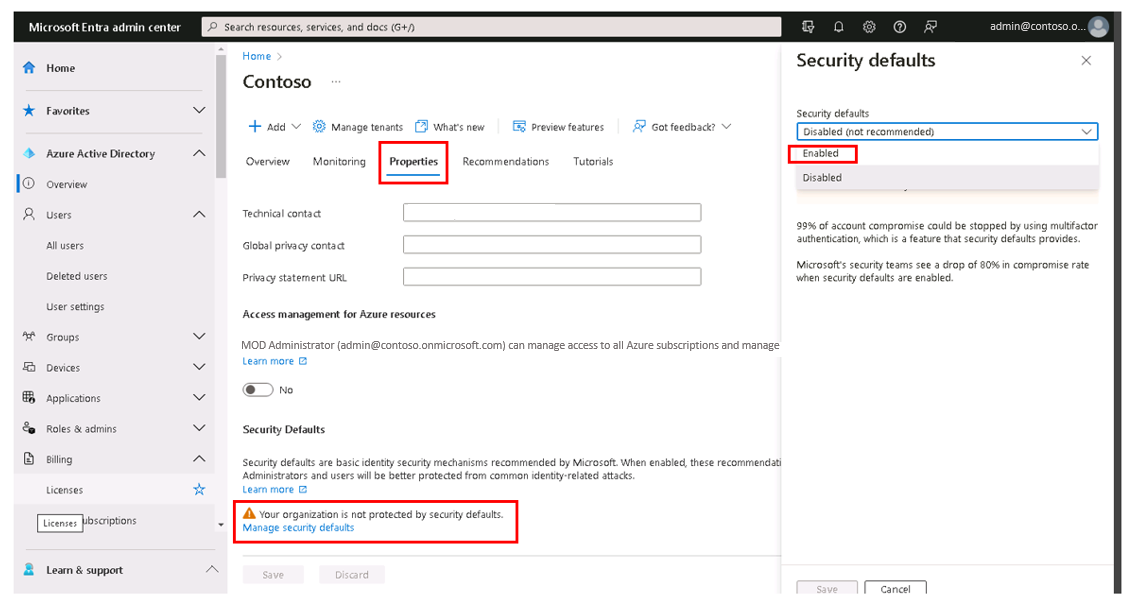
To enable security defaults in your directory:
- Sign in to the Microsoft Entra admin center as a Security administrator, Conditional Access administrator, or Global administrator.
- In the Microsoft Entra admin center, in the left-hand navigation pane, select Identity, and then select Overview.
- On the Overview page for your organization's tenant, the system displays the Overview tab by default. Select the Properties tab.
- Under the Security defaults section, select the Manage security defaults link.
- On the Security defaults pane that appears, select in the Security defaults field. In the drop-down menu that appears, select Enabled.
- At the bottom of the pane, select Save.
Enforced security default policies
The start of this unit examined the five security default policies the system automatically enforces when an organization enables security defaults. The following sections introduce these policies.
Require all users to register for Microsoft Entra multifactor authentication
All users in your tenant must register for multifactor authentication (MFA) in the form of the Microsoft Entra multifactor authentication. Users have 14 days to register for Microsoft Entra multifactor authentication by using the Microsoft Authenticator app or any app supporting OATH TOTP. After the 14 days pass, the user can't sign in until registration completes. A user's 14-day period begins following their first successful interactive sign-in after the organization enabled security defaults.
Require administrators to do multifactor authentication
Administrators increased access to their environment. Because of the power these highly privileged accounts have, they should treat them with special care. One common method to improve the protection of privileged accounts is to require a stronger form of account verification for sign-in. In Microsoft Entra ID, you can get a stronger account verification by requiring multifactor authentication.
Tip
Microsoft recommends having separate accounts for administration and standard productivity tasks. Doing so significantly reduces the number of times the system prompts your administrators for MFA.
After an organization enables Microsoft Entra multifactor authentication and its users register with MFA, the system requires the following Microsoft Entra administrator roles to complete extra authentication every time they sign in:
- Global administrator
- Application administrator
- Authentication administrator
- Billing administrator
- Cloud application administrator
- Conditional Access administrator
- Exchange administrator
- Helpdesk administrator
- Password administrator
- Privileged authentication administrator
- Security administrator
- SharePoint administrator
- User administrator
Require users to do multifactor authentication when necessary
Many people think that only administrator accounts need extra layers of authentication. Yes, administrators have broad access to sensitive information, and they can make changes to subscription-wide settings. But in reality, attackers frequently target end users.
After these attackers gain access, they can request access to privileged information for the original account holder. They can even download the entire directory to do a phishing attack on the whole organization.
One common method to improve protection for all users is to require a stronger form of account verification for everyone, such as multifactor authentication. After users complete registration, the system prompts for another authentication whenever necessary. Microsoft Entra ID decides when to prompt a user or multifactor authentication based on factors such as location, device, role, and task. This functionality protects all applications registered with Microsoft Entra ID including SaaS applications.
Note
B2B direct connect users must satisfy any multifactor authentication requirement from security defaults enabled in a resource tenant. This requirement includes multifactor authentication registration by the direct connect user in their home tenant.
Block legacy authentication protocols
To give users easy access to their organization's cloud apps, Microsoft Entra ID supports various authentication protocols, including legacy authentication. Legacy authentication refers to an authentication request made by:
- Clients that don't use modern authentication (for example, an Office 2010 client).
- Any client that uses older mail protocols such as IMAP, SMTP, or POP3.
Today, most compromising sign-in attempts come from legacy authentication. Legacy authentication doesn't support multifactor authentication. Even if you have a multifactor authentication policy enabled on your directory, an attacker can authenticate by using an older protocol and bypass multifactor authentication.
After an organization enables security defaults, the system blocks all authentication requests made by an older protocol. Security defaults also block Exchange Active Sync basic authentication.
Before an organization enables security defaults, it must ensure that its administrators don't use older authentication protocols. For more information, see How to move away from legacy authentication.
Protect privileged activities like access to the Microsoft Entra admin center
Organizations use various Azure services managed through the Azure Resource Manager API, including:
- Microsoft Entra admin center
- Azure PowerShell
- Azure CLI
Note
After you enable security defaults in your tenant, any user accessing these Azure services must complete multifactor authentication. This requirement includes both administrators and non-administrators.
Using Azure Resource Manager to manage your services is a highly privileged action. Azure Resource Manager can alter tenant-wide configurations, such as service settings and subscription billing. Single-factor authentication is vulnerable to various attacks like phishing and password spray.
Organizations should verify the identity of users who want to access Azure Resource Manager and update configurations. You verify their identity by requiring more authentication before you allow access.
Warning
Pre-2017 Exchange Online tenants have modern authentication disabled by default. To avoid the possibility of a sign-in loop while authenticating through these tenants, you must enable modern authentication.
Note
Microsoft Entra ID excludes the Microsoft Entra Connect synchronization account from security defaults. It doesn't prompt this account to register for or perform multifactor authentication. Organizations shouldn't use this account for other purposes.
Deployment considerations when enabling security defaults
Authentication methods
Once an organization enables security defaults, its users must register for and use Microsoft Entra multifactor authentication using the Microsoft Authenticator app using notifications. Users can use verification codes from the Microsoft Authenticator app, but they can only register using the notification option. Users can also use any third-party application using OATH TOTP to generate codes.
Warning
Organizations that use security defaults shouldn't disable authentication methods. If an organization disables methods, it can lead to locking the company out of its tenant.
All authentication methods should remain available to users enabled in the MFA service settings portal.
Backup administrator accounts
Every organization should configure at least two backup administrator accounts. Microsoft refers to these accounts as emergency access accounts.
Organizations might use these accounts when they can't use their normal administrator accounts. For example: The most recent Global Administrator left the organization. Microsoft Entra prevents the organization from deleting the remaining Global Administrator account from, but it doesn't prevent the organization from deleting or disabling the account on-premises. Either scenario can result in the organization being unable to recover the account.
Organizations should configure emergency access accounts as follows:
- Organizations must assign Global Administrator rights to emergency access accounts in Microsoft Entra ID.
- Organizations shouldn't use emergency access accounts on a daily basis.
- Organizations should protect emergency access accounts with a long, complex password.
Organizations should store the credentials for emergency access accounts offline in a secure location, such as a fireproof safe. Only authorized individuals should have access to these credentials.
Organizations can optionally choose to disable password expiration for emergency access accounts using PowerShell.
Additional reading. For more detailed information about emergency access accounts, see Manage emergency access accounts in Microsoft Entra ID.
B2B users
If an organization enables security defaults, the system treats any B2B guest users or B2B direct connect users that access the organization's directory the same as the organization's users.
Disabled MFA status
If an organization is a previous user of per-user based Microsoft Entra multifactor authentication, the Multifactor Authentication status page might not display users in an Enabled or Enforced status. The appropriate status for users who use security defaults or Conditional Access-based Microsoft Entra multifactor authentication is Disabled.
Conditional Access
Organizations can use Conditional Access to configure policies similar to security defaults, but with more granularity. Conditional Access policies allow selecting other authentication methods and the ability to exclude users. Microsoft Entra ID doesn’t include these features in security defaults.
Note
As previously stated, organizations that use Conditional Access can't enable security defaults.
Disabling security defaults
Organizations that enable security defaults can later choose to implement Conditional Access policies. To do so, they must first disable security defaults.