Configure privileged access management
Configuring Privileged Access Management (PAM) in Microsoft Purview allows organizations to enforce structured access controls, reducing risks associated with standing administrative permissions.
Prerequisites
Before configuring PAM, ensure the following prerequisites are met:
- Microsoft 365 subscription: Verify that your organization's subscription includes support for PAM. Check subscription details.
- Appropriate roles: Ensure you have the Global Administrator or Exchange Administrator role to configure PAM.
- Plan access groups: Determine approvers and system accounts for privileged access requests.
Steps to configure privileged access management
Follow these steps to set up PAM in your organization:
1. Create an approver's group
Approver groups are responsible for reviewing and authorizing privileged access requests. Setting up a mail-enabled security group ensures requests are routed appropriately.
Sign into the Microsoft 365 admin center using your admin credentials.
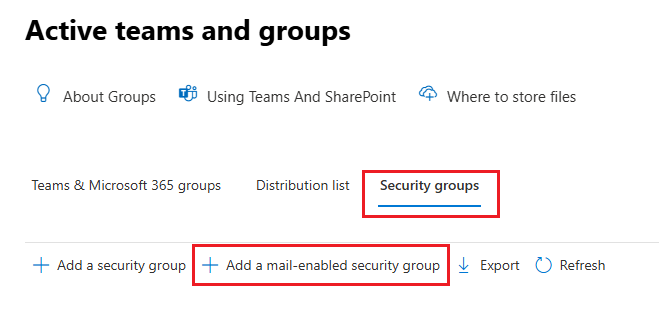
Navigate to Teams & groups > Active teams & groups using your admin credentials.
Select the Security groups tab, then choose Add a mail-enabled security group.
On the Set up the basics page, enter the following details:
- Name: Provide a descriptive name for the group.
- Description: Add a brief description of the group's purpose.
On the Assign owners page, assign an owner for the group.
On the Add members page, add individuals who will act as approvers.
On the Edit settings page, configure the group email address.
Select Create group. Wait a few minutes for the group to be fully configured.
2. Enable privileged access management
Enabling PAM activates the approval workflows, ensuring that sensitive administrative tasks require elevated permissions granted through controlled processes.
Enable privileged access management using the Microsoft 365 Admin Center
Sign into the Microsoft 365 Admin Center.
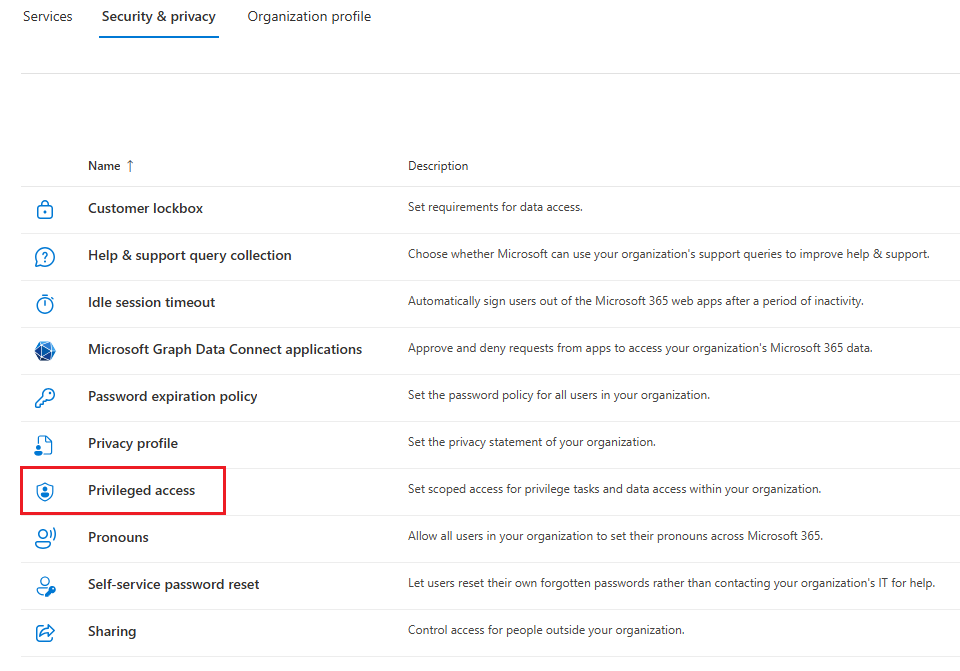
Go to Settings > Org settings > Security & privacy > Privileged access.
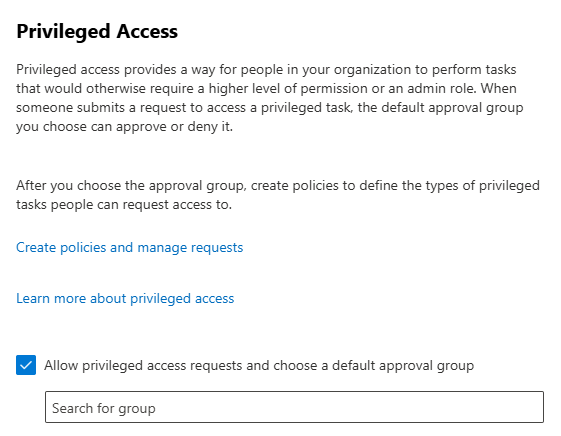
Select the checkbox for Allow privileged access requests and choose a default approval group.
Assign the approver's group created in Step 1 as the default approval group.
Save and close the settings.
Enable privileged access management using PowerShell
Use the Enable-ElevatedAccessControl cmdlet in Exchange Online PowerShell to enable privileged access management and assign the approver group. This ensures that privileged tasks require approval and defines the group responsible for approving these requests:
Enable-ElevatedAccessControl -AdminGroup '<default approver group>' -SystemAccounts @('<systemAccountUPN1>','<systemAccountUPN2>')
Example:
Enable-ElevatedAccessControl -AdminGroup 'pamapprovers@fabrikam.onmicrosoft.com' -SystemAccounts @('sys1@fabrikamorg.onmicrosoft.com', 'sys2@fabrikamorg.onmicrosoft.com')
The -AdminGroup parameter specifies the mail-enabled security group for approvals, while the -SystemAccounts parameter excludes specific accounts from privileged access controls, allowing essential system operations to continue uninterrupted.
3. Create access policies
Access policies define the rules under which privileged access is granted. These policies ensure that elevated permissions are provided only when necessary and under defined conditions.
Create an access policy using the Microsoft 365 Admin Center
Navigate to Settings > Org settings > Security & privacy > Privileged access.
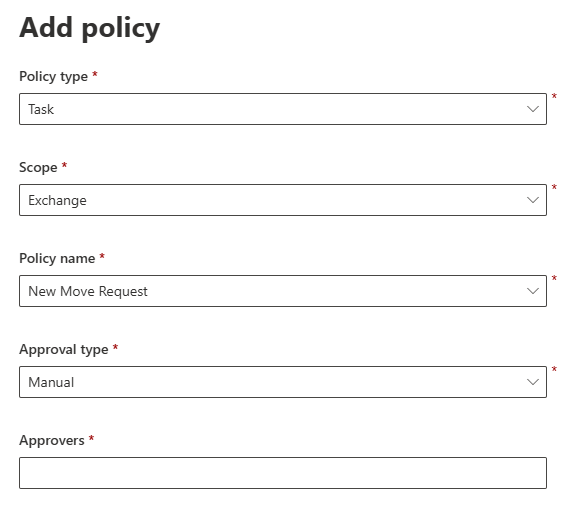
Select Create policies and manage requests > Manage policies > Add policy.
Configure the policy:
Policy type: Task, Role, or Role Group
Policy scope: Exchange
Policy name: Select from available options
Approval type: Manual or Auto
Approvers: Select the approver's group, if the Approval type is set to Manual
Select Create to add a new privileged access management policy.
Create an access policy using Exchange Management PowerShell
Use the New-ElevatedAccessApprovalPolicy cmdlet in PowerShell to create a privileged access policy. This policy defines the conditions under which elevated tasks are approved and executed:
New-ElevatedAccessApprovalPolicy -Task 'Exchange\<exchange management cmdlet name>' -ApprovalType <Manual, Auto> -ApproverGroup '<default/custom approver group>'
Example:
New-ElevatedAccessApprovalPolicy -Task 'Exchange\New-MoveRequest' -ApprovalType Manual -ApproverGroup 'mbmanagers@fabrikamorg.onmicrosoft.com'
-Task: Specifies the Exchange cmdlet that requires privileged access approval.-ApprovalType: Determines whether the approval is handled manually by an approver group (Manual) or automatically (Auto).-ApproverGroup: Identifies the mail-enabled security group responsible for approving requests when -ApprovalType is set to Manual.
4. Test and use privileged access management
Testing ensures that the configured policies and workflows operate as intended, allowing users to submit requests and approvers to act on them.
Submit a request: Users can request elevated permissions for tasks by navigating to the Privileged access section in the Microsoft 365 Admin Center or by using PowerShell.
Approve a request: Approvers review and act on requests via email notifications or directly in the Microsoft 365 Admin Center.
Configuring privileged access management ensures secure and temporary administrative permissions for sensitive tasks. By creating approver groups, enabling PAM, and defining access policies, organizations can enforce the principle of least privilege and enhance their security posture. Regular audits and reviews further strengthen PAM's effectiveness in safeguarding critical configurations and data.