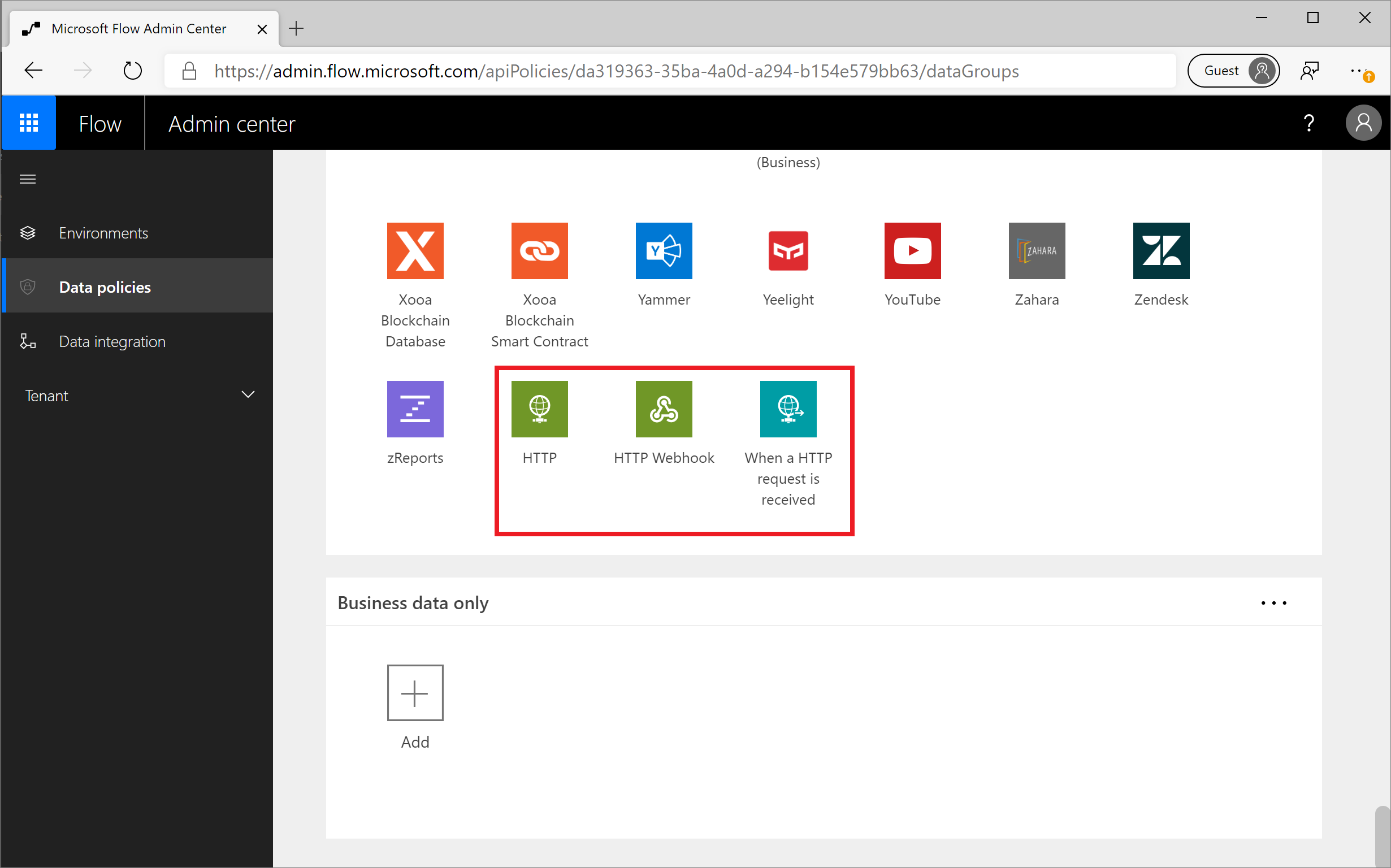
Manage HTTP connectors with a DLP policy
HTTP triggers and actions are built into Microsoft Power Platform and, by default, don’t appear as connectors in the DLP policy editor. However, it's possible to manage the triggers/actions that are shown in the following image.
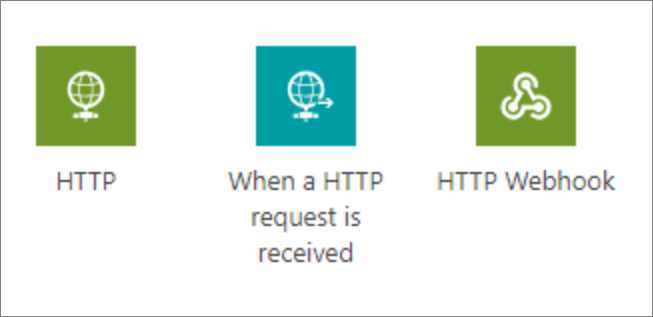
These triggers/actions can only be managed in DLP policies that have a schema version of 2018-11-01, which is discussed in the linked blog. Using this new schema version allows organizations to opt in to implementing these changes. Otherwise, it's highly possible that some flows that rely on DLPs will be broken, particularly if connectors are moved between data groups.
For example, suppose the HTTP action was previously not managed and is being used with connectors from the Business data group. If you then place the HTTP action in the Non-business data group, any flows that are using the HTTP action is suspended because of DLP violations if they contain other Business data group connectors.
Using the 2018-11-01 schema version, DLP policies can be constructed with either of the following tools:
Microsoft Power Platform Management connector
Power Apps and Power Automate PowerShell cmdlets
Many find using PowerShell to be simplest. Additional information about Power Apps and Power Automate PowerShell cmdlets can be found at PowerShell support for Power Apps.
After installing the prerequisite PowerShell modules, you can run the following statement, (New-AdminDlpPolicy -DisplayName "HTTP DLP Policy" -SchemaVersion 2018-11-01), which will create a new DLP policy that includes support for HTTP when you include a -SchemaVersion parameter of 2018-11-01. After you have run the previous statement, you'll be asked to sign in by using your admin credentials.
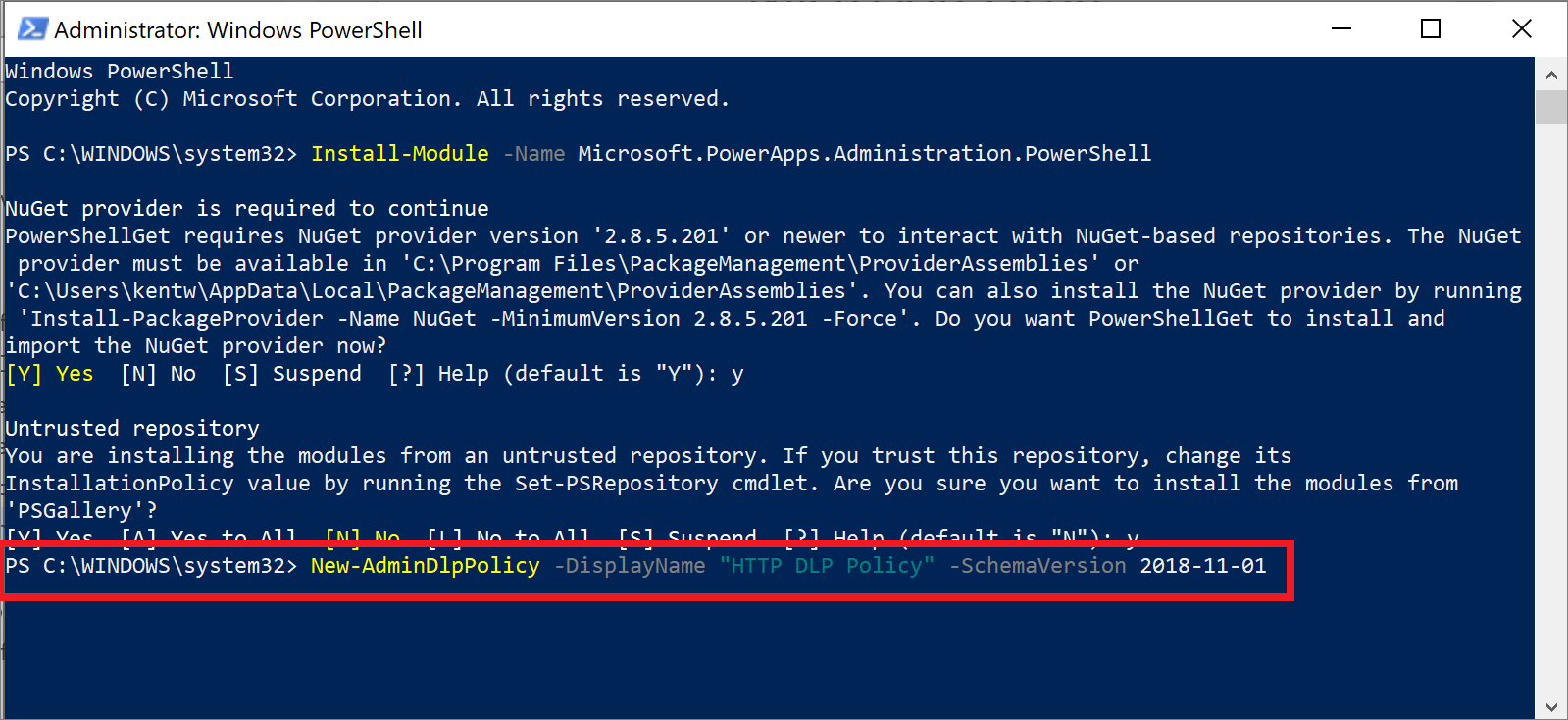
After the command has been run, you'll be provided a status output that includes the internal PolicyName and other attributes.
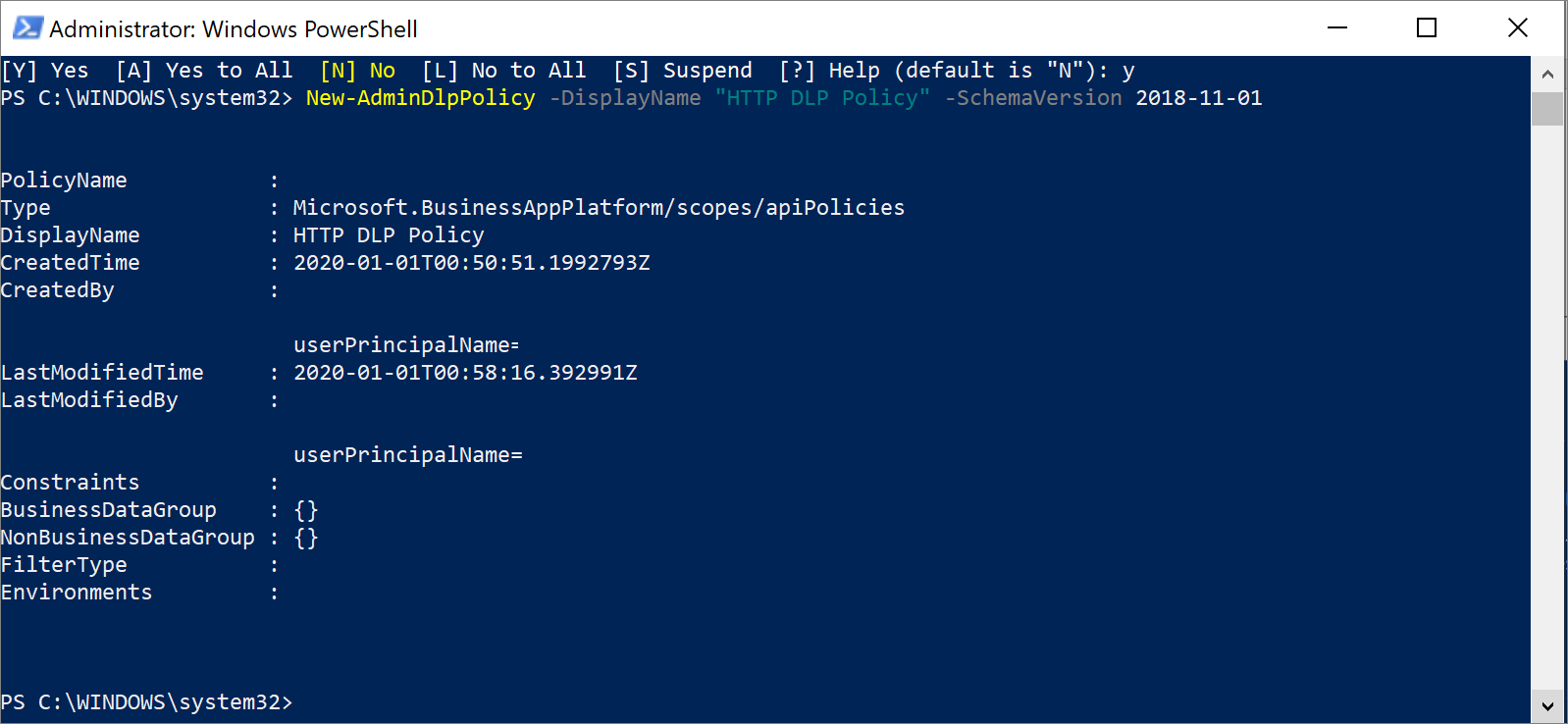
If you go to the Power Automate Admin Center, you discover that the DLP policy has been created.
Note
Because an environment parameter wasn't specified when you created this DLP policy, it's applicable to the entire tenant.
After you have explored this DLP policy, you'll find that your HTTP triggers and actions are included in your default data group, which in this case is No business data allowed. These connectors can be managed just like any other connectors and can be added to the Business data only data group.