View sensitive data using Content explorer and Activity explorer
The Microsoft Purview compliance portal provides data classification analytics. It provides these capabilities through the Content explorer and Activity explorer tools. There's a separate page for each tool under the Data classification group in the Microsoft Purview compliance portal's navigation pane.
Content explorer. This tool provides visibility into the amount and types of sensitive data in an organization. It also enables users to filter by label or sensitivity type. Doing so displays a detailed view of locations where the system stores this sensitive data. It provides administrators with the ability to:
- Index the sensitive documents stored within supported Microsoft 365 workloads.
- Identify the sensitive information stored in each document.
- Identify documents that the system classified with sensitivity and retention labels.
Activity explorer. This tool shows the activities related to sensitive data and labels. For example, label downgrades, or external sharing that could expose content to risk. Activity Explorer displays the activities that are related to sensitive information used by end users. This data includes:
- Label activities
- Data loss prevention (DLP) logs
- Autolabeling
- Endpoint DLP
The following sections introduce each of these analytical tools.
License requirements for Content explorer and Activity explorer
Every account that accesses and uses data classification must have a license assigned to it from one of these subscriptions:
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5/G5/F5 Compliance
- Microsoft 365 F5 Security and Compliance
- Microsoft 365 E5/A5/F5/G5 Information Protection and Governance
- Office 365 E5
Content explorer
Content explorer shows a current snapshot of the items that have a sensitivity or retention label. It also shows the items classified as a sensitive information type in your organization.
Required permissions to access items in Content explorer
Microsoft Purview highly restricts access to Content explorer because it lets a user read the contents of scanned files.
Important
These permissions supersede permissions that organizations locally assigned to the items, which allow viewing of the content.
There are two roles that grant access to Content explorer. Organizations can grant these roles using the Microsoft Purview compliance portal:
- Content Explorer list viewer. Membership in this role group allows the user to see each item and its location in list view. Microsoft 365 preassigned the Data Classification list viewer role to this role group.
- Content Explorer content viewer. Membership in this role group allows the user to view the contents of each item in the list. Microsoft 365 preassigned the Data Classification content viewer role to this role group.
The accounts that an organization uses to access Content explorer must be in one or both of the role groups. These role groups are independent role groups and aren't cumulative. For example, if you want to grant an account the ability to view the items and their locations only, grant Content Explorer list viewer rights. If you want that same account to also be able to view the contents of the items in the list, you must also grant Content Explorer content viewer rights.
You can also assign either or both role to a custom role group to tailor access to Content explorer.
A Global admin can assign the necessary Content Explorer list viewer and Content Explorer content viewer role group membership.
Sensitive information types
A DLP policy can help protect sensitive information. In turn, the system defines this information as a sensitive information type. Microsoft 365 includes definitions for many common sensitive information types from across many different regions that are ready for organizations to use. For example, a credit card number, bank account numbers, national ID numbers, and Windows Live ID service numbers.
Sensitivity labels
A sensitivity label is simply a tag that indicates the value of the item to an organization. You can apply it manually or automatically. Once applied, the label gets embedded in the document. By doing so, it follows the document everywhere it goes. A sensitivity label enables various protective behaviors, such as mandatory watermarking or encryption.
For files that are in SharePoint and OneDrive, you must enable sensitivity labels for the corresponding data to surface in the Microsoft Purview compliance portal features. For more information, see Enable sensitivity labels for Office files in SharePoint and OneDrive.
Retention labels
A retention label enables organizations to define how long the system should keep a labeled item. It also enables organizations to define the steps to take before deleting it. You can apply retention labels either manually or automatically through policies. Retention labels can play a role in helping an organization stay in compliance with legal and regulatory requirements.
How to use Content explorer
A user with access to Content explorer should complete the following steps to access it:
- In the Microsoft Purview compliance portal, select Data classification in the navigation pane to expand this group.
- In the Data classification group, select Content explorer.
- On the Content explorer page, if you know the name of the label or the sensitive information type, you can type that into the filter box. Or you can browse for the item in the Sensitive info types column and select the label from the list.
- Selecting a Sensitive info types item displays All locations for the item in the middle of the page.
- Select a location in the All locations pane and drill down through the folder structure to the item.
- Select the item to open it natively in Content explorer.
Export
The export control creates a .csv file that contains a listing of whatever the focus of the pane is.
Note
It can take up to seven days for Content explorer to updates counts.
Filter
The Filter tool appears when you drill down into a location, such as an Exchange or Teams folder, or a SharePoint or OneDrive site.
The scope of the search tool is displayed in the All locations pane. What you can search on varies depending on the selected location.
- When Exchange or Teams is the selected location, you can search on the full email address of the mailbox. For example, user@domainname.com.
- When SharePoint or OneDrive is the selected location, the search tool appears when you drill down to site names, folders, and files.
You can search on:
| Value | Example |
|---|---|
| full site name | https://contoso.onmicrosoft.com/sites/sitename |
| file name | RES_Resume_1234.txt Note: Segments of this file name are the basis of the next three examples. |
| text at the beginning of a file name | RES |
| text after an underscore character in a file name | Resume or 1234 |
| file extension | txt |
Activity explorer
In the Data classification group of the Microsoft Purview compliance portals' navigation pane, the Overview and Content explorer pages provide visibility into what content the system discovered and labeled, and where that content resides. The Activity explorer page rounds out this suite of data classification analytics tools.
Activity explorer enables an organization to monitor the actions performed with its labeled content. Activity explorer also provides a historical view of activities on an organization's labeled content. It collects the activity information from the Microsoft 365 unified audit logs. It then transforms the data and presents it in the Activity explorer UI. Activity explorer reports on up to 30-day’s worth of data.
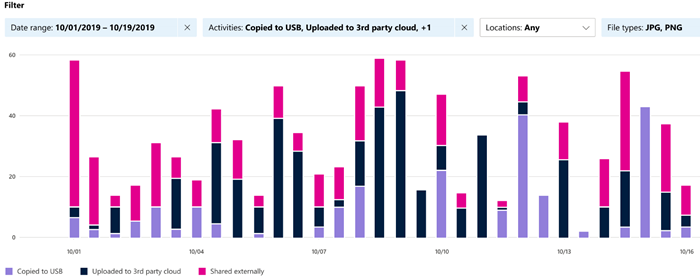
There are over 30 different filters available for use, including:
- Date range
- Activity type
- Location
- User
- Sensitivity label
- Retention label
- File path
- DLP policy
Required permissions to access Activity explorer
To access Activity explorer, you must be a member of any one of the following role groups or explicitly granted one of the following roles.
The list of applicable roles includes:
- Information Protection Admin
- Information Protection Analyst
- Information Protection Investigator
- Information Protection Reader
The list of applicable role groups includes:
- Information Protection
- Information Protection Admins
- Information Protection Analysts
- Information Protection Investigators
- Information Protection Readers
Microsoft 365 role groups include:
- Global administrator
- Compliance administrator
- Security administrator
- Compliance data administrator
Microsoft 365 roles include:
- Compliance administrator
- Security administrator
- Security Reader
Activity types
Activity explorer gathers activity information from the audit logs on multiple sources of activities. For more detailed information on what labeling activity makes it to Activity explorer, see Labeling events available in Activity explorer.
The source of activities includes:
- Sensitivity label activities and Retention labeling activities from Office native applications
- Microsoft Entra Protection add-in
- SharePoint Online
- Exchange Online (sensitivity labels only)
- OneDrive
Examples of activities from these various sources include:
- Label applied
- Label changed (upgraded, downgraded, or removed)
- Autolabeling simulation
- File read
Examples of Microsoft Entra Protection scanner and AIP client activities include:
- Protection applied
- Protection changed
- Protection removed
- Files discovered
Activity explorer also gathers DLP policy match events from Exchange Online, SharePoint Online, OneDrive, Teams Chat, Teams Channel (preview), on-premises SharePoint folders and libraries, on-premises file shares, and Windows 10 and 11 devices through Endpoint data loss prevention (DLP). Some example events from Windows 10 and 11 devices include the following file activities:
- Deletions
- Creations
- Copied to clipboard
- Modified
- Read
- Printed
- Renamed
- Copied to network share
- Accessed by unallowed app
Understanding what actions your organization took with your sensitive labeled content is essential in understanding the effectiveness of your organization's data lifecycle management. It helps you see if the controls that you have in place, such as Microsoft Purview Data Loss Prevention policies are effective. You can manage your various policies and take new actions to restrict the undesired behavior if either:
- Your existing controls aren't effective.
- You discover something unexpected. For example, many items downgraded from highly confidential to general.
Note
Activity explorer doesn't currently monitor retention activities for Exchange Online.
Knowledge check
Choose the best response for the following question.