Plan for security and compliance in Microsoft 365
Security and compliance solutions are important for organizations concerned about protecting their data or following legal or regulatory standards. For example, an organization wants to ensure that nobody in the company sends out company-confidential information using e-mail.
While the reasons to implement security and compliance solutions depend on your company’s focus, the following guideline is available: Office 365 security roadmap: Top priorities for the first 30 days, 90 days, and beyond.
The following diagram shows all the security considerations required to protect the data inside Microsoft 365.
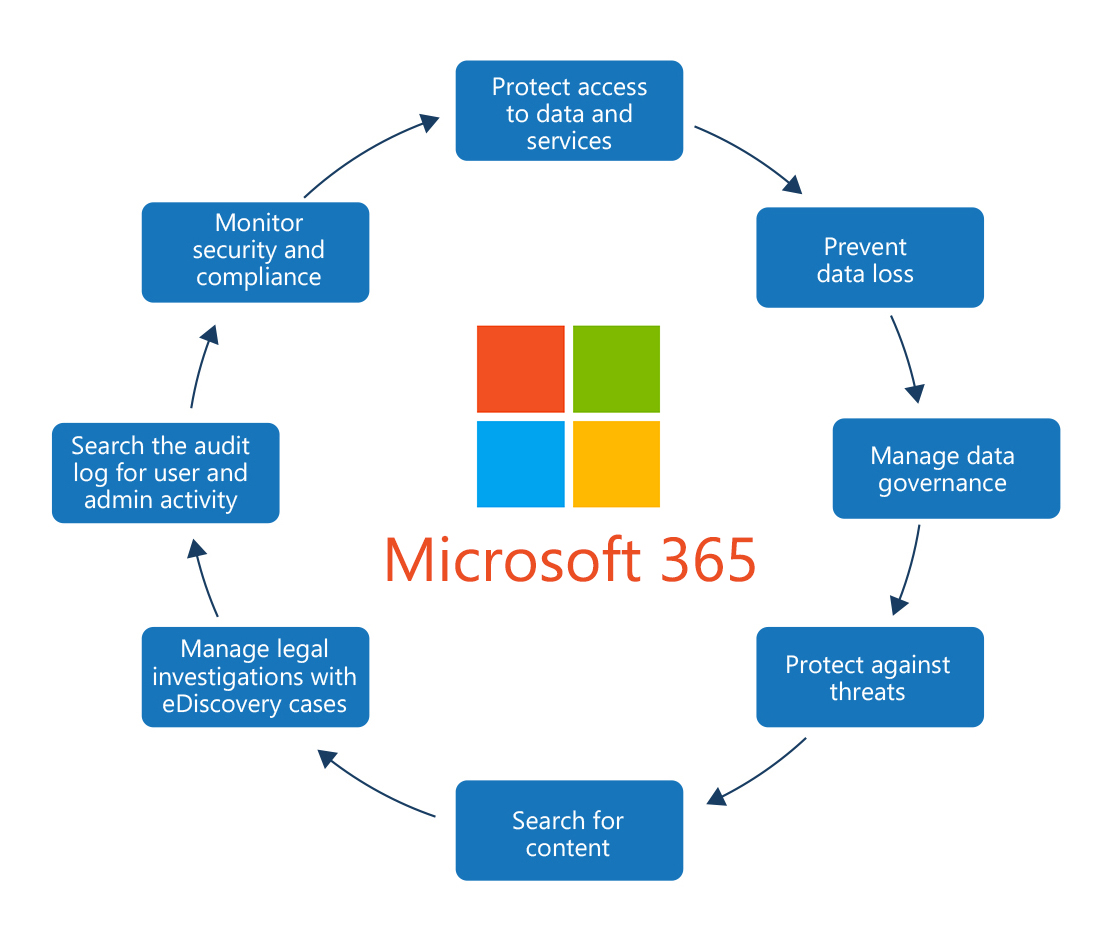
Plan for security and compliance in Microsoft 365
Managing security and compliance is a partnership. An organization is responsible for protecting its data, identities, and devices. At the same time, Microsoft is vigorously protecting Microsoft 365 services. Microsoft 365’s Enterprise Mobility + Security suite is designed to help organizations achieve the appropriate level of protection for their businesses.
The following table identifies the high-level steps that organizations should complete when planning for security and compliance in Microsoft 365.
| Planning steps | Description |
|---|---|
| Step 1: Review capabilities. | Familiarize yourself with the information protection capabilities in Microsoft 365. |
| Step 2: Check your Secure Score. | After setting up your Microsoft 365 subscription, take note of your starting score within the Microsoft Secure Score tool. Secure Score provides configuration suggestions that an organization can take to increase its score. The goal is to be aware of opportunities that you can take to protect your environment without negatively affecting your users' productivity. |
| Step 3: Plan access protection for identity and devices. | Organizations can defend against cyber-attacks and guard against data loss by: - Protecting access to data and services. - Securing email policies and configurations. Select this link to download the Identity and Device Protection for Microsoft 365 document. This document identifies the recommended capabilities for protecting identities and devices that access Microsoft 365, other SaaS services, and on-premises applications published with Microsoft Entra Application Proxy. |
| Step 4: Plan data protection based on data sensitivity. | Select this link to download the File Protection Solutions in the Microsoft 365 document. This document can help you plan your file protection capabilities based on recommended architectures for protecting files in Microsoft 365. |
| Step 5: Use the Microsoft Purview compliance portal. | The Microsoft Purview compliance portal provides a single view into the controls needed to manage the spectrum of Microsoft 365 data governance. The next unit in this training introduces you to the features in the Microsoft Purview compliance portal. |
| Step 6: Use beginning-to-end security scenarios as starting points. | Use these recommended configurations as a starting point for enterprise scale or sophisticated access security scenarios: - Secure email policies and configurations - Contoso in the Microsoft Cloud |
Microsoft 365 admin centers and dashboards
Configure your security and compliance settings in these admin centers and dashboards to protect your Microsoft 365 environment.
| Subscription | Management URL | Dashboards and admin centers |
|---|---|---|
| Microsoft 365 |
https://admin.microsoft.com |
- Microsoft 365 admin center - Microsoft Purview compliance portal - Exchange admin center - SharePoint admin center - OneDrive admin center |
| Enterprise Mobility + Security |
https://portal.azure.com |
- Microsoft Entra ID - Microsoft Mobile Application Management - Microsoft Intune |
| Enterprise Mobility + Security |
https://portal.cloudappsecurity.com |
- Microsoft Defender for Cloud Apps |
Note
Azure Active Directory (Azure AD) is now Microsoft Entra ID. Learn more.
Knowledge check
Choose the best response for each of the questions below.