Explain the identity landscape
It's important to understand the identity landscape before reviewing other identity concepts. How does Microsoft think about identity when designing products and solutions? The essential lifecycle of identity.
| 1) Zero Trust |
|---|
| 2) Identity | 3) Actions |
|---|---|
| Business to Business (B2B) | Authenticate - Prove - AuthN |
| Business to Consumer (B2C) | Authorize - Get - AuthZ |
| Verifiable Credentials | Administer - Configure |
| (Decentralize Providers) | Audit - Report |
| 4) Usage | 5) Maintain |
|---|---|
| Access applications and data | Protect - Detect - Respond |
| Secure - Cryptography | |
| Dollars - Licenses |
First you have the guidance of always thinking and designing with zero trust in mind. Don't just give access to data and applications because the user has had access previously. You need to always confirm.
Second you have systems to provide verified accounts for users and applications. Identity services come from Microsoft Entra ID, from business-to-business federation, from business-to-customer, and from decentralized identity providers.
Third you have specific actions identity provides and to keep the systems running. Users and applications can authenticate and authorize to gain access to systems. And administrators need to monitor and maintain the identity systems with proper governance.
Fourth you get many actions that can be performed once your credentials are verified. Use applications and data, while taking advantage of other identity based services.
Fifth and finally, you need to always keep your systems up to date.
From classic identity to zero trust identity
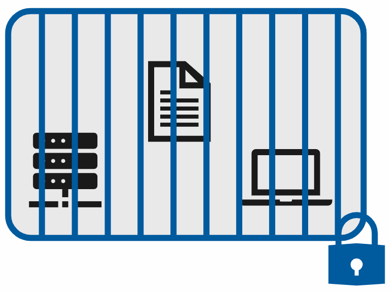
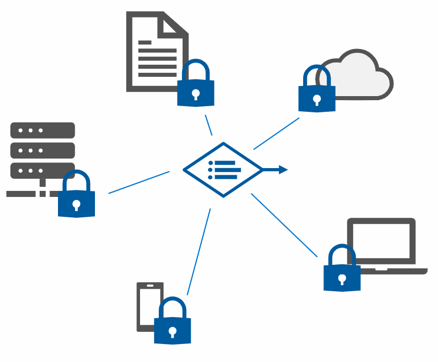
Historically, identity kept all your assets behind the firewall. Submit a username and password to get through the gate, and you had full access to everything. In the modern world, with the large number of cyber-attacks securing just the network doesn't work. One lost or stolen credential and bad actors have access to everything. With zero trust, you protect your assets anywhere with policy.
| Classic identity | Zero trust identity |
|---|---|
|
|
| Restrict everything to a secure network | Protect assets anywhere with central policy |
Each of these subjects will be covered in more detail over the rest of this module.