Describe Microsoft Defender for Identity
Microsoft Defender for Identity is a cloud-based security solution that uses signals from your on-premises identity infrastructure servers to detect threats, like privilege escalation or high-risk lateral movement, and reports on easily exploited identity issues.
At a high level, the way Microsoft Defender for Identity works is as follows:
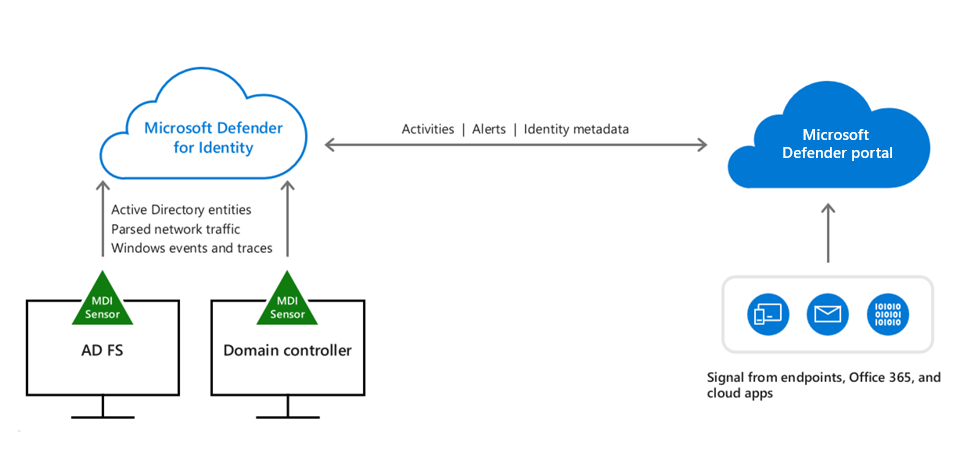
Microsoft Defender for Identity uses software-based sensors installed on your on-premises identity infrastructure servers (domain controllers and servers running Active Directory Federated Services and Active Directory Certificate Services).
The Defender for Identity sensor accesses the event logs it requires directly from the servers. After the logs and network traffic are parsed by the sensor, Defender for Identity sends only the parsed information to the Defender for Identity cloud service. The Defender for Identity cloud service uses the data/signals obtained to deliver an identity threat detection and response (IDTR) solution. Microsoft Defender for Identity helps security professionals, managing a hybrid environment, the functionality to:
- Prevent breaches, by proactively assessing your identity posture.
- Detect threats, using real-time analytics and data intelligence.
- Investigate suspicious activities, using clear, actionable incident information.
- Respond to attacks, using automatic response to compromised identities.
The configuration of the service and the signals and insights generated by the Microsoft Defender for Identity service are exposed through the Microsoft Defender portal that provides security teams a unified experience for investigating and responding to attacks.
Proactively assess your identity posture
Defender for Identity provides you with a clear view of your identity security posture, helping you to identify and resolve security issues before they can be exploited by attackers. For example, Microsoft Defender for Identity continuously monitors your environment to identify sensitive accounts with the riskiest lateral movement paths that expose a security risk, and reports on these accounts to assist you in managing your environment. Defender for Identity security assessments, available from Microsoft Secure Score, provide extra insights to improve your organizational security posture and policies.
Detect threats, using real-time analytics and data intelligence
Defender for Identity monitors and analyzes user activities and information across your network, including permissions and group membership, creating a behavioral baseline for each user. Defender for Identity then identifies anomalies with adaptive built-in intelligence. It gives insights into suspicious activities and events, revealing the advanced threats, compromised users, and insider threats facing your organization. Defender for Identity identifies these advanced threats at the source throughout the entire cyberattack kill-chain:
- Reconnaissance - Identify rogue users and attackers' attempts to gain information.
- Compromised credentials - Identify attempts to compromise user credentials using brute force attacks, failed authentications, user group membership changes, and other methods.
- Lateral movements - Detect attempts to move laterally inside the network to gain further control of sensitive users.
- Domain dominance - View attacker behavior if threat actors gain control over Active Directory, referred to as domain dominance, through remote code execution on the domain controller or other methods.
Investigate alerts and user activities
Defender for Identity is designed to reduce general alert noise, providing only relevant, important security alerts in a simple, real-time organizational attack timeline.
Use the Defender for Identity attack timeline view and the intelligence of smart analytics to stay focused on what matters. Also, you can use Defender for Identity to quickly investigate threats, and gain insights across the organization for users, devices, and network resources.
Microsoft Defender for Identity protects your organization from compromised identities, advanced threats, and malicious insider actions.
Remediation actions
Microsoft Defender for Identity supports remediation actions to be performed directly on your on-premises identities. Examples include:
Disable user in Active Directory: This will temporarily prevent a user from signing in to the on-premises network. This can help prevent compromised users from moving laterally and attempting to exfiltrate data or further compromise the network.
Reset user password – This will prompt the user to change their password on the next sign-in, ensuring that this account can't be used for further impersonation attempts.
Depending on your Microsoft Entra ID roles, you may see additional Microsoft Entra ID actions, such as requiring users to sign in again and confirming a user as compromised.
Microsoft Defender for Identity in the Microsoft Defender portal
Microsoft Defender for Identity is experienced through the Microsoft Defender portal. The Defender portal is the home for monitoring and managing security across your Microsoft identities, data, devices, apps, and infrastructure, allowing security admins to perform their security tasks, in one location.
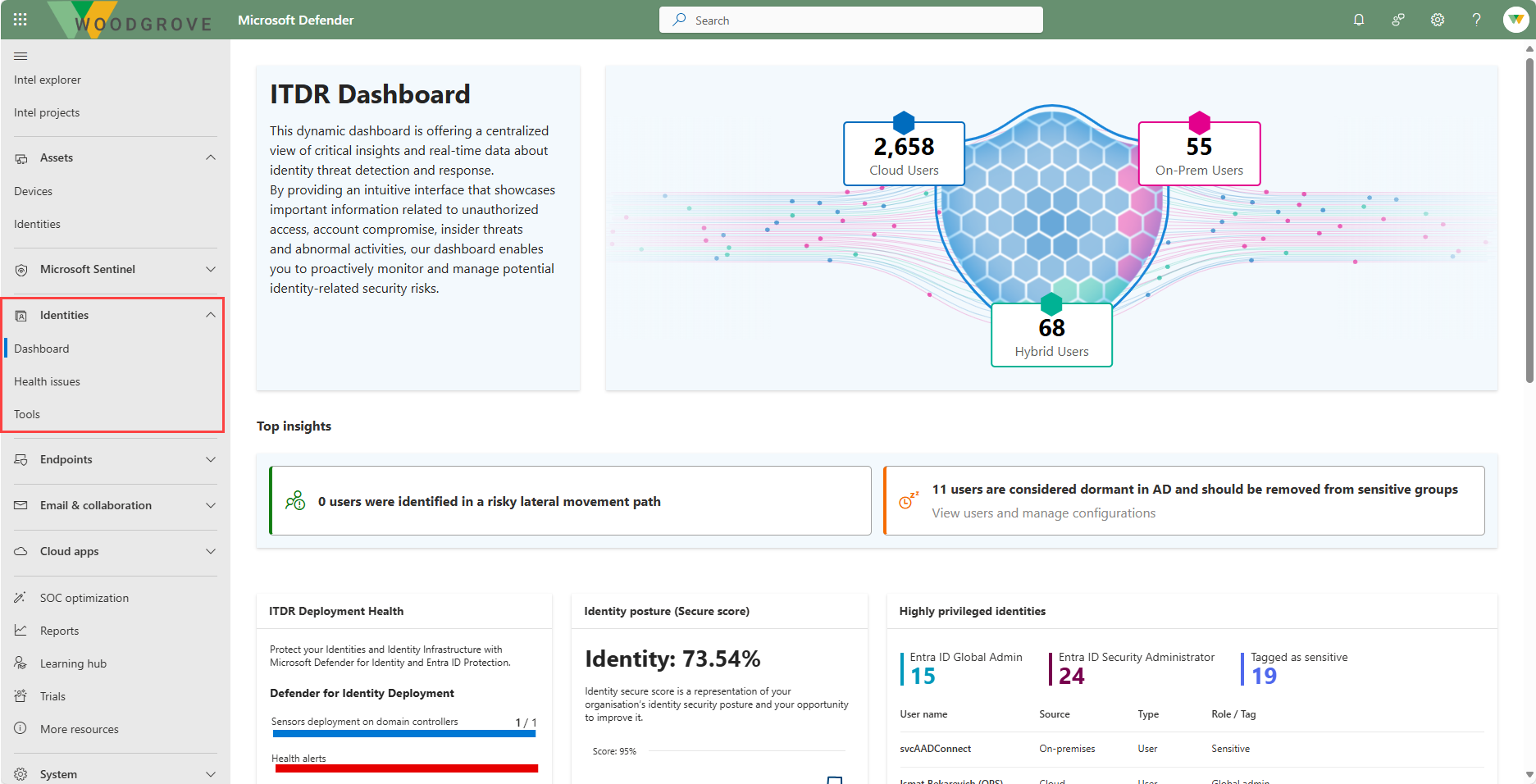
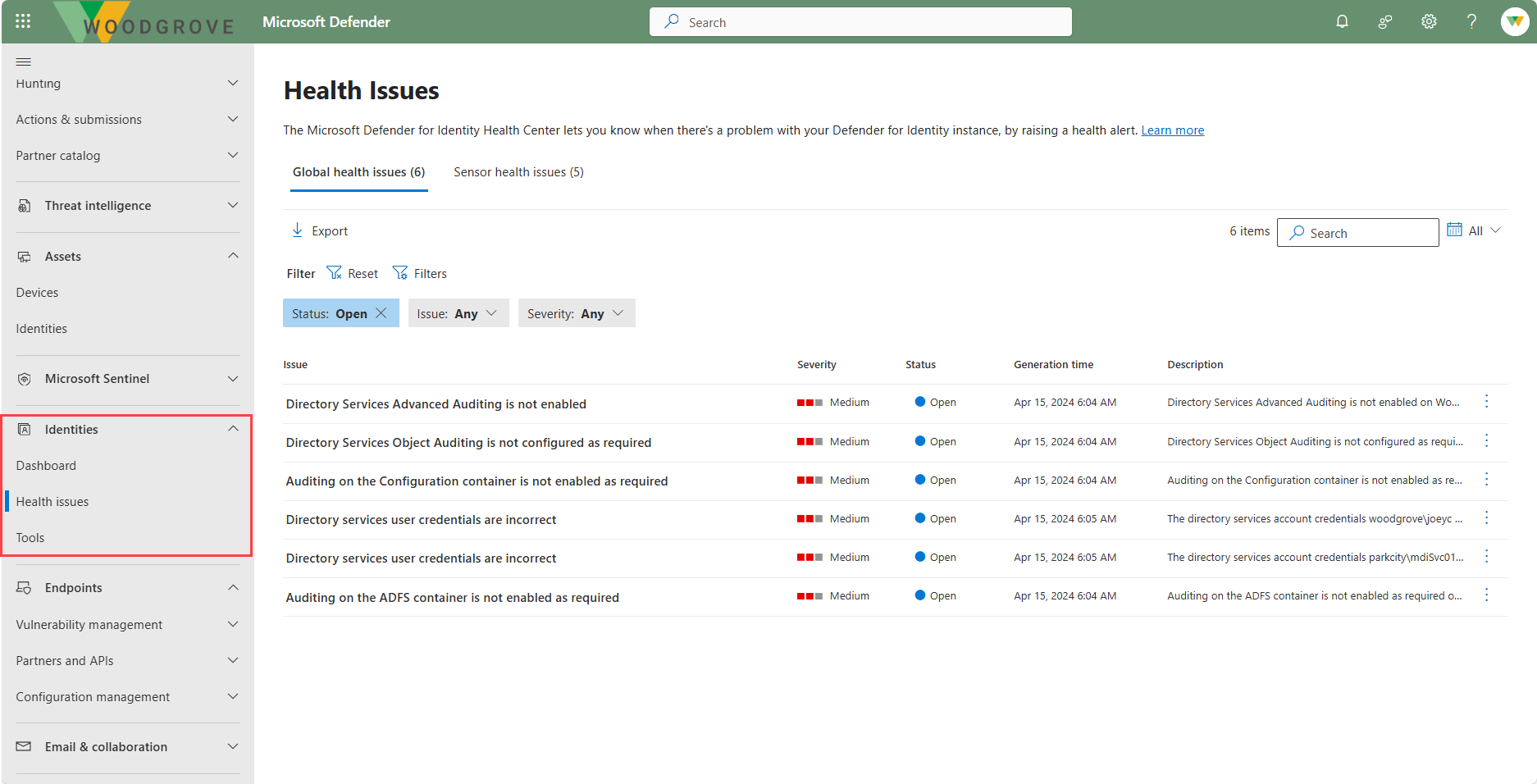
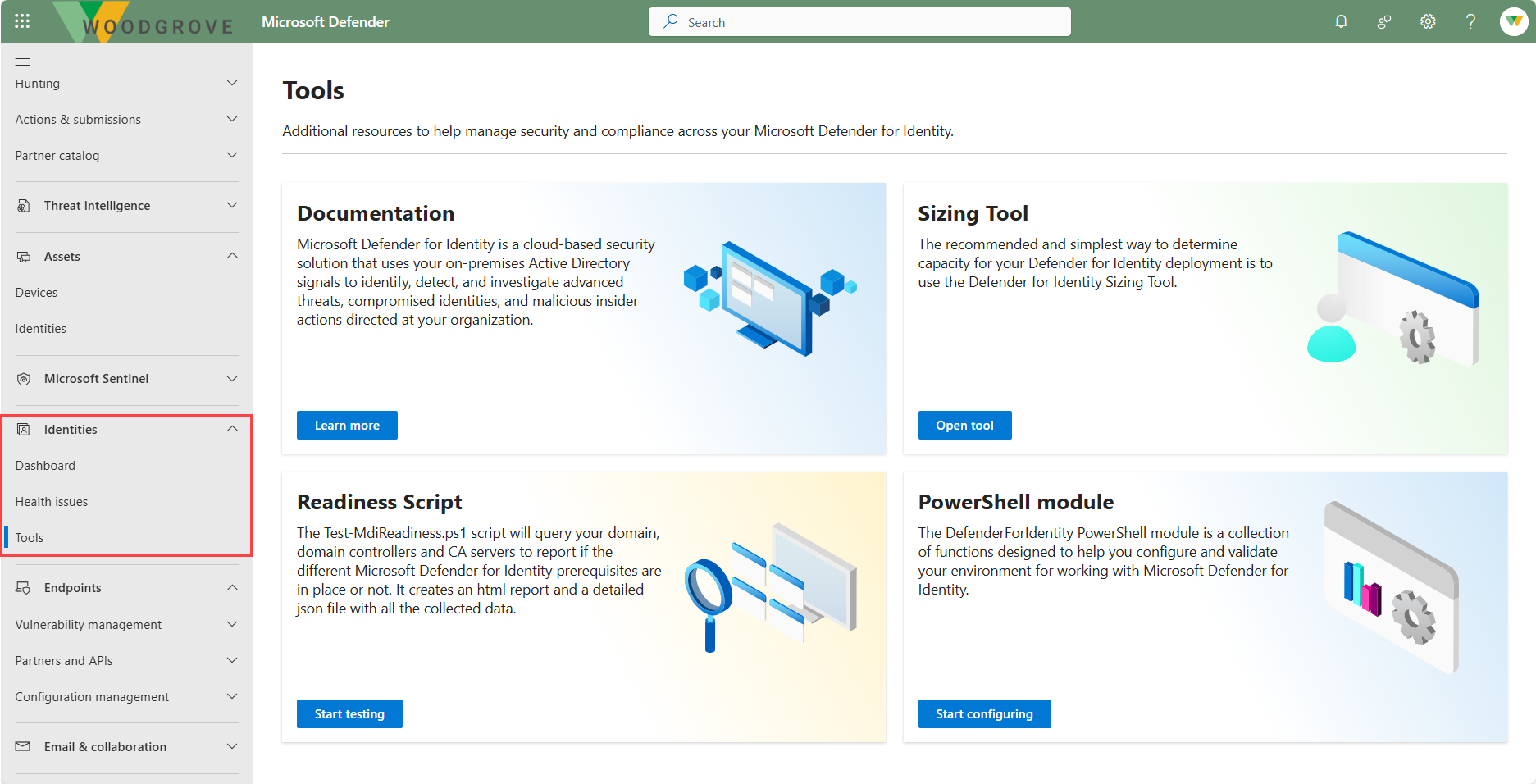
The Identities node on the left navigation panel of the Microsoft Defender portal includes the following:
The Microsoft Defender for Identity Dashboard provides critical insights and real time data about identity threat detection and response (ITDR).
The health Issues page lists any current health issues for your Defender for Identity deployment and sensors, alerting you to any problems in your Defender for Identity deployment.
The tools page lists additional information to help manage your Microsoft Defender for Identity environment. Examples include a readiness script that you can run to determine if all the Microsoft Defender for Identity prerequisites are in place, a PowerShell module with a collection of functions designed to help you configure and validate your environment for working Microsoft Defender for Identity, and more.
Settings, permissions, incidents and alerts, reports and other features are also available through the Microsoft Defender portal. More information is covered in the unit, "Describe the Microsoft Defender portal," included in this module.