Cloud security control and auditing
When you run an application on the cloud, different aspects of security must be controlled by different entities. For instance, the following figure (from Azure) shows the breakdown of security responsibilities between the provider and the customer.
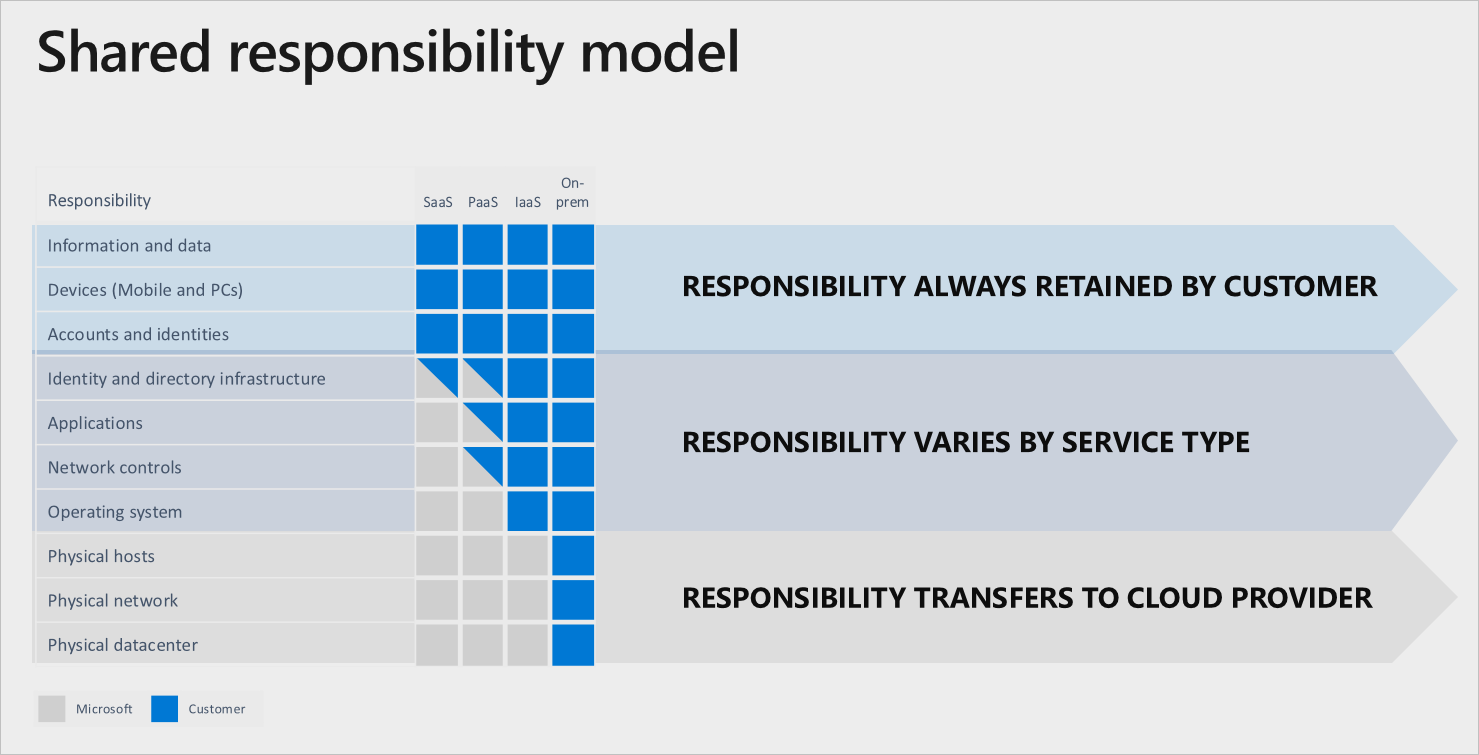
Figure 13: Security responsibilities in Azure (Source)
Many classes of applications require different infrastructure, process, and security certifications. Most cloud service providers will comply with a majority of the popular certifications and audit requirements followed in the US and Europe.
To develop an application that passes these compliance checks, both the cloud service providers and the application developers must apply a minimal set of security controls, which we will explore below. As with the rest of this course, we look at controls from a predominantly IaaS perspective. Obviously, as we move up the stack, the cloud service provider has to ensure the security of the resources it is responsible for.
For an IaaS cloud, the following table gives an overview of some of the the security controls to be implemented by both parties:
| Domain | Cloud service provider responsibility | Customer responsibility |
|---|---|---|
| Identity and access management | A cloud service provider must provide information to customers about who is using the service. This requires that they:
|
Using the authentication and access control service provided by the cloud provider, customers must:
|
| Availability and fault tolerance | To ensure that the cloud is resilient to failure, cloud service providers must have:
|
The redundancy provided by the cloud service provider has to be leveraged by the customer, who should:
|
| Patching and configuration management |
|
|
| Monitoring and detection | Verify that customer resources are not being used for nefarious activities (either intentionally or unintentionally), and take appropriate actions. |
|
| Data security |
|
|
| Cryptographic object security |
|
|
Providers will often build in services that simplify the process for customers to implement security controls. For example, Azure provides Azure Network Security Groups, which can act as external network firewalls.
The process of verifying the presence of these controls is known as a security audit. These audits can be done internally (by hiring a technical consultant) or externally (by a certifying agency). To host sensitive information on the cloud, both the provider and the customer must pass these audits.
References
- Mather, Tim et. al. (2009). Cloud security and privacy: an enterprise perspective on risks and compliance. O'Reilly Media
- Pucher, Alex et. al. (2012). A Survey on Cloud Provider Security Measures. University of California Santa Barbara