Introduction to Microsoft 365 vulnerability management
At Microsoft, our approach to service security is built on an Assume Breach mentality. Assume Breach limits the trust placed in applications, services, identities, and networks by approaching them all—internal and external—as insecure and already compromised. These principles help to limit the impact of security vulnerabilities by reducing the damage an adversary can cause and enabling rapid detection and response to security threats.
Microsoft 365 is designed with security in mind to prevent security vulnerabilities, but that doesn't mean we assume our services are secure. We apply our Assume Breach mentality to vulnerability management by implementing a variety of complementary systems to proactively scan our environments for vulnerabilities and enable timely remediation. Our vulnerability management program continuously validates the security posture of the environment to prevent, detect, and remediate vulnerabilities before they can be exploited by an adversary.
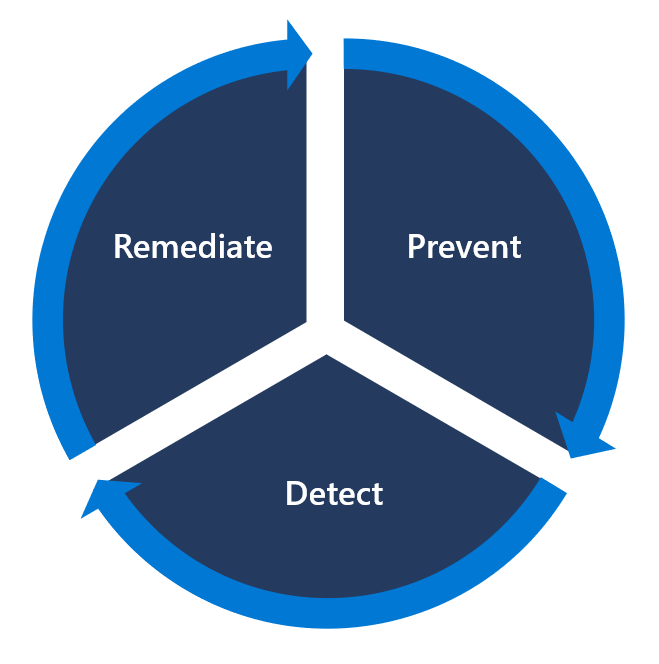
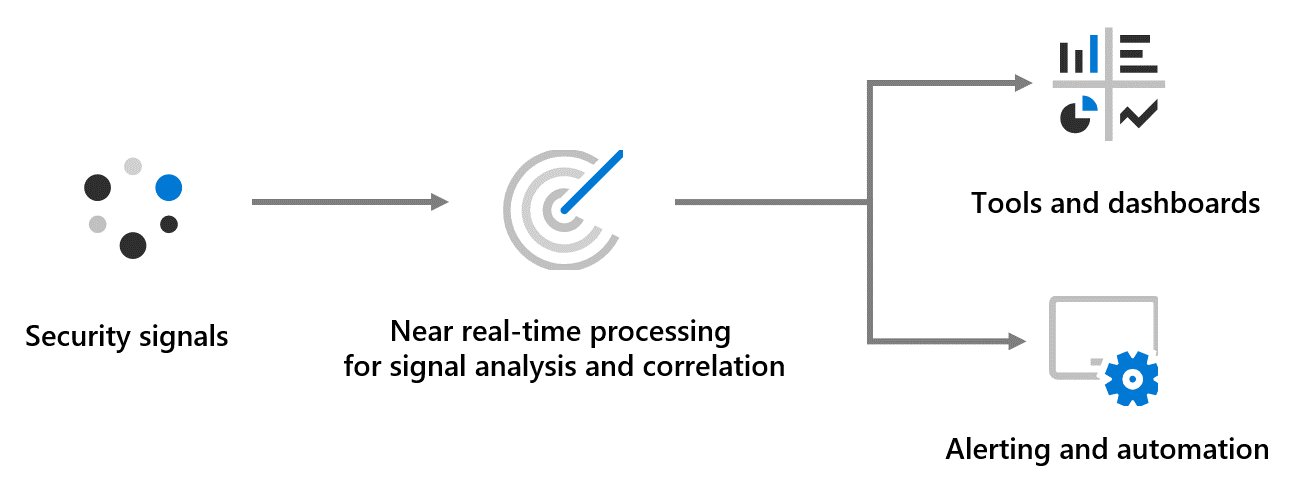
We recognize that even highly secure systems can be compromised. As a result, we also implement extensive and continuous security monitoring to rapidly detect and respond to security threats in Microsoft 365. Our security monitoring uses cloud-based, automated tools designed to detect and respond to incidents at the scale of Microsoft 365. When activity that indicates a potential incident is detected, our security monitoring systems trigger automated countermeasures and alert appropriate personnel. Potential security incidents detected by security monitoring activities are escalated to the Microsoft 365 Security Response team and follow the security incident response process.
Microsoft 365 coordinates its diverse vulnerability management and security monitoring activities to provide Defense-in-Depth against both known and unknown threats. These activities include automated machine state scanning, continuous security monitoring, and ongoing attack simulation and penetration testing.