Low-Privilege Monitoring
All workflows (discoveries, rules, monitors, and actions) in this management pack are bound to Run As Profiles.
To enable low-privilege monitoring, grant appropriate permissions to Run As accounts and map these accounts to respective Run As Profiles.
Note
The Virtual Log File Count monitor (VLF) doesn't support low-privilege monitoring on SQL Servers 2012 and 2014.
Create Active Directory accounts
In Active Directory, create the following domain users for low-privilege access to the target SQL Server instances:
- SQLTaskAction
- SQLDiscovery
- SQLMonitor
Create the SQLMPLowPriv domain group and add the following domain users to this group:
- SQLDiscovery
- SQLMonitor
Add the SQLMPLowPriv group to the Read-only Domain Controllers Active Directory security group.
Agent Monitoring
This section explains how to configure low-privilege agent monitoring.
On Agents
Grant the SQLTaskAction user and the SQLMPLowPriv group the Read permission for the registry key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Microsoft SQL ServerOn each monitored instance, grant the SQLMPLowPriv group the Read permission for the registry key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Microsoft SQL Server\[InstanceID]\MSSQLServer\ParametersAdd the SQLTaskAction and SQLMonitor users to the Event Log Readers Active Directory security local group.
Grant Execute Methods, Enable Account, Remote Enable, and Read Security permissions to SQLTaskAction and SQLMPLowPriv for the following WMI namespaces using the WMI Control:
- ROOT
- ROOT\CIMV2
- ROOT\DEFAULT
- ROOT\Microsoft\SqlServer\ComputerManagement11 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement12 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement13 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement14 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement15 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement16 (if exists)
Configure the Allow log on locally local security policy to allow the SQLTaskAction user and the SQLMPLowPriv domain group users to log on locally.
Note
If you're using System Center Operations Manager 2016, follow the steps above to provide Allow log on locally permission to Run As accounts. Learn more.
Configure the Log on as a Service local security policy to allow the SQLTaskAction user and the SQLMPLowPriv domain group users to sign in as a service.
Note
If you're using System Center Operations Manager 2019 or higher, follow the steps above to provide Log on as a Service permission to Run As accounts. Learn more.
In the Microsoft Monitoring Agent properties for the selected management group, set the Local System account to perform agent actions.
Extra Steps for Cluster SQL Server Instances
Take the steps above for each cluster node.
Grant to SQLMPLowPriv and SQLTaskAction the Remote Launch and Remote Activation DCOM permissions using DCOMCNFG.
Allow Windows Remote Management through Windows Firewall.
Grant the SQLMPLowPriv group Full Control to the cluster using Failover Cluster Manager.
Grant Execute Methods, Enable Account, Remote Enable, and Read Security permissions to SQLTaskAction and SQLMPLowPriv for the root\MSCluster WMI namespace using the WMI Control.
On SQL Server Instances
Open SQL Server Management Studio and connect to the SQL Server Database Engine instance.
In SQL Server Management Studio, for each instance of SQL Server Database Engine running on a monitored server, use the following SQL script to create and set the lowest privilege configuration for the SQLMPLowPriv domain account:
USE [master]; SET NOCOUNT ON; /*The domain account that System Center Operations Manager will use to access the SQL Server instance*/ DECLARE @accountname sysname = '<domainName>\<login_name>'; /*In some cases, administrators change the 'sa' account default name. This will retrieve the name of the account associated to princicpal_id = 1*/ DECLARE @sa_name sysname = 'sa'; SELECT @sa_name = [name] FROM sys.server_principals WHERE principal_id = 1 /*Create the server role with authorization to the account associated to principal id = 1. Create the role only if it does not already exist*/ DECLARE @createSrvRoleCommand nvarchar(200); SET @createSrvRoleCommand = 'IF NOT EXISTS (SELECT 1 FROM sys.server_principals WHERE [name] = ''SCOM_SQLMPLowPriv'') BEGIN CREATE SERVER ROLE [SCOM_SQLMPLowPriv] AUTHORIZATION [' + @sa_name + ']; END' EXEC(@createSrvRoleCommand); GRANT VIEW ANY DATABASE TO [SCOM_SQLMPLowPriv]; GRANT VIEW ANY DEFINITION TO [SCOM_SQLMPLowPriv]; GRANT VIEW SERVER STATE TO [SCOM_SQLMPLowPriv]; DECLARE @createLoginCommand nvarchar(200); SET @createLoginCommand = 'IF NOT EXISTS (SELECT 1 FROM sys.server_principals WHERE [name] = '''+ @accountname +''') BEGIN CREATE LOGIN '+ QUOTENAME(@accountname) +' FROM WINDOWS WITH DEFAULT_DATABASE=[master]; END' EXEC(@createLoginCommand); -- Add the login to the user-defined server role DECLARE @addServerMemberCommand nvarchar(200); SET @addServerMemberCommand = 'ALTER SERVER ROLE [SCOM_SQLMPLowPriv] ADD MEMBER ' + QUOTENAME(@accountname) + ';' EXEC(@addServerMemberCommand); -- Add the login and database role to each database DECLARE @createDatabaseUserAndRole nvarchar(max); SET @createDatabaseUserAndRole = ''; SELECT @createDatabaseUserAndRole = @createDatabaseUserAndRole + ' USE ' + QUOTENAME(db.name) + '; IF NOT EXISTS (SELECT 1 FROM sys.database_principals WHERE [name] = '''+ @accountname +''') BEGIN CREATE USER ' + QUOTENAME(@accountname) + ' FOR LOGIN ' + QUOTENAME(@accountname) + '; END; IF NOT EXISTS (SELECT 1 FROM sys.database_principals WHERE [name] = ''SCOM_SQLMPLowPriv'') BEGIN CREATE ROLE [SCOM_SQLMPLowPriv] AUTHORIZATION [dbo]; END; ALTER ROLE [SCOM_SQLMPLowPriv] ADD MEMBER ' + QUOTENAME(@accountname) + ';' FROM sys.databases db LEFT JOIN sys.dm_hadr_availability_replica_states hadrstate ON db.replica_id = hadrstate.replica_id WHERE db.database_id <> 2 AND db.user_access = 0 AND db.state = 0 AND db.is_read_only = 0 AND (hadrstate.role = 1 or hadrstate.role is null); EXEC(@createDatabaseUserAndRole); -- Add database specific permissions to database role USE [master]; GRANT EXECUTE ON sys.xp_readerrorlog TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON sys.xp_instance_regread TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [sys].[indexes] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [sys].[tables] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [sys].[dm_db_index_physical_stats] TO [SCOM_SQLMPLowPriv]; USE [msdb]; GRANT SELECT ON [dbo].[sysjobschedules] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysschedules] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[syscategories] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysjobs_view] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysjobactivity] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysjobhistory] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[syssessions] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_primary_databases] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_secondary_databases] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_monitor_history_detail] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_monitor_secondary] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_monitor_primary] TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON [dbo].[sp_help_job] TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON [dbo].[agent_datetime] TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON [dbo].[SQLAGENT_SUSER_SNAME] TO [SCOM_SQLMPLowPriv]; ALTER ROLE [SQLAgentReaderRole] ADD MEMBER [SCOM_SQLMPLowPriv];
On SMB Shares
Grant share permissions by opening the share properties dialog for the share that hosts SQL Server data files or SQL Server transaction log files.
Grant the Read permission to SQLMPLowPriv.
Grant NTFS permissions by opening the properties dialog for the shared folder and navigating to the Security tab.
Grant the Read permission to SQLMPLowPriv.
Optional Steps for Tasks on Agents
Some optional System Center Operations Manager tasks require a higher privilege on an agent machine and/or database to allow task execution.
Take the following steps on an agent machine or database only if you want to allow the System Center Operations Manager console operator to take remedial actions:
If the task is related to starting or stopping an NT service (such as DB Engine Service, SQL Server Agent service, SQL Full Text Search Service, Integration Services), on the agent machine, grant the SQLTaskAction user the permission to start or stop an NT service. This involves setting a service security descriptor. For more information, see Sc sdset.
Read the existing privileges for the given service using sc sdshow and grant extra privileges to the SQLTaskAction user.
For example, if the results of the sdshow command for SQL Server service are as follows:
*D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)*In this case, the following command grants sufficient access to SQLTaskAction for starting and stopping the SQL Server service. Replace 'SQLServerServiceName' and 'SID for SQLTaskAction' with the appropriate values and keep everything on a single line.
*sc sdset SQLServerServiceName D:(A;;GRRPWP;;;SID for SQLTaskAction)(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)*In SQL Server Management Studio, for each instance of SQL Server Database Engine running on a monitored server, create a login for SQLTaskAction:
USE [msdb]; CREATE USER [SQLTaskAction] FOR LOGIN [SQLTaskAction];Grant the db_owner database role for each database if the task is related to performing database checks:
- Check Catalog (DBCC)
- Check Database (DBCC)
- Check Disk (DBCC) (invokes DBCC CHECKALLOC)
USE [yourdatabase]; ALTER ROLE [db_owner] ADD MEMBER [SQLTaskAction];Grant the ALTER ANY DATABASE privilege to the SQLTaskAction login to run the task if the task is related to changing the database state:
- Set Database Offline
- Set Database Online
- Set Database to Emergency State
USE [master]; GRANT ALTER ANY DATABASE TO [SQLTaskAction];
In System Center Operations Manager
Create the following Windows-based Run As accounts:
- SQLTaskAction
- SQLDiscovery
- SQLMonitor
In System Center Operations Manager console, configure Run As Profiles as follows:
- Set the Microsoft SQL Server Task Run As Profile to use the SQLTaskAction Run As account.
- Set the Microsoft SQL Server Discovery Run As Profile to use the SQLDiscovery Run As account.
- Set the Microsoft SQL Server Monitoring Run As profile to use the SQLMonitor Run As account.
To prevent SQL Server monitoring issues, the SQLTaskAction, SQLDiscovery, and SQLMonitor Run As accounts should be used to manage the target as the Windows Computer object.
Agentless Monitoring
[Applicable to SQL Server on Windows and on Linux]
This section explains how to configure low-privilege agentless monitoring.
On SQL Server Instances
Open SQL Server Management Studio and connect to the SQL Server Database Engine instance.
In SQL Server Management Studio, for each instance of SQL Server Database Engine running on a monitored server, use the following SQL script to create and set the lowest privilege configuration for the SQLMPLowPriv account with Active Directory authentication:
USE [master]; SET NOCOUNT ON; /*The user account with SQL Server authentication that System Center Operations Manager will use to access the SQL Server instance*/ DECLARE @accountname sysname = '<domainName>\<login_name>'; /*In some cases, administrators change the 'sa' account default name. This will retrieve the name of the account associated to princicpal_id = 1*/ DECLARE @sa_name sysname = 'sa'; SELECT @sa_name = [name] FROM sys.server_principals WHERE principal_id = 1 /*Create the server role with authorization to the account associated to principal id = 1. Create the role only if it does not already exist*/ DECLARE @createSrvRoleCommand nvarchar(200); SET @createSrvRoleCommand = 'IF NOT EXISTS (SELECT 1 FROM sys.server_principals WHERE [name] = ''SCOM_SQLMPLowPriv'') BEGIN CREATE SERVER ROLE [SCOM_SQLMPLowPriv] AUTHORIZATION [' + @sa_name + ']; END' EXEC(@createSrvRoleCommand); GRANT VIEW ANY DATABASE TO [SCOM_SQLMPLowPriv]; GRANT VIEW ANY DEFINITION TO [SCOM_SQLMPLowPriv]; GRANT VIEW SERVER STATE TO [SCOM_SQLMPLowPriv]; DECLARE @createLoginCommand nvarchar(200); /*Create the login with SQL Server authentication using the password, and replace it with your value below*/ SET @createLoginCommand = 'IF NOT EXISTS (SELECT 1 FROM sys.server_principals WHERE [name] = '''+ @accountname +''') BEGIN CREATE LOGIN '+ QUOTENAME(@accountname) +' FROM WINDOWS WITH DEFAULT_DATABASE=[master]; END' EXEC(@createLoginCommand); -- Add the login to the user-defined server role DECLARE @addServerMemberCommand nvarchar(200); SET @addServerMemberCommand = 'ALTER SERVER ROLE [SCOM_SQLMPLowPriv] ADD MEMBER ' + QUOTENAME(@accountname) + ';' EXEC(@addServerMemberCommand); -- Add the login and database role to each database DECLARE @createDatabaseUserAndRole nvarchar(max); SET @createDatabaseUserAndRole = ''; SELECT @createDatabaseUserAndRole = @createDatabaseUserAndRole + ' USE ' + QUOTENAME(db.name) + '; IF NOT EXISTS (SELECT 1 FROM sys.database_principals WHERE [name] = '''+ @accountname +''') BEGIN CREATE USER ' + QUOTENAME(@accountname) + ' FOR LOGIN ' + QUOTENAME(@accountname) + '; END; IF NOT EXISTS (SELECT 1 FROM sys.database_principals WHERE [name] = ''SCOM_SQLMPLowPriv'') BEGIN CREATE ROLE [SCOM_SQLMPLowPriv] AUTHORIZATION [dbo]; END; ALTER ROLE [SCOM_SQLMPLowPriv] ADD MEMBER ' + QUOTENAME(@accountname) + ';' FROM sys.databases db LEFT JOIN sys.dm_hadr_availability_replica_states hadrstate ON db.replica_id = hadrstate.replica_id WHERE db.database_id <> 2 AND db.user_access = 0 AND db.state = 0 AND db.is_read_only = 0 AND (hadrstate.role = 1 or hadrstate.role is null); EXEC(@createDatabaseUserAndRole); -- Add database specific permissions to database role USE [master]; GRANT EXECUTE ON sys.xp_readerrorlog TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON sys.xp_instance_regread TO [SCOM_SQLMPLowPriv]; USE [msdb]; GRANT SELECT ON [dbo].[sysjobschedules] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysschedules] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[syscategories] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysjobs_view] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysjobactivity] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[sysjobhistory] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[syssessions] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_primary_databases] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_secondary_databases] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_monitor_history_detail] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_monitor_secondary] TO [SCOM_SQLMPLowPriv]; GRANT SELECT ON [dbo].[log_shipping_monitor_primary] TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON [dbo].[sp_help_job] TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON [dbo].[agent_datetime] TO [SCOM_SQLMPLowPriv]; GRANT EXECUTE ON [dbo].[SQLAGENT_SUSER_SNAME] TO [SCOM_SQLMPLowPriv]; ALTER ROLE [SQLAgentReaderRole] ADD MEMBER [SCOM_SQLMPLowPriv];
Some optional System Center Operations Manager tasks require a higher privilege on an agent machine and/or database to allow task execution.
Take the following steps only if you want to allow the System Center Operations Manager console operator to take remedial actions on that target:
In SQL Server Management Studio, for each instance of SQL Server Database Engine running on a monitored server, create a login for SQLTaskAction:
USE [msdb]; CREATE USER [SQLTaskAction] FOR LOGIN [SQLTaskAction];Grant the db_owner database role for each database if the task is related to performing database checks:
- Check Catalog (DBCC)
- Check Database (DBCC)
- Check Disk (DBCC) (invokes DBCC CHECKALLOC)
USE [yourdatabase]; ALTER ROLE [db_owner] ADD MEMBER [SQLTaskAction];Grant the ALTER ANY DATABASE privilege to the SQLTaskAction login to run the task if the task is related to changing the database state:
- Set Database Offline
- Set Database Online
- Set Database to Emergency State
USE [master]; GRANT ALTER ANY DATABASE TO [SQLTaskAction];
Using Monitoring Wizard
To configure low-privilege agentless monitoring using the monitoring wizard, perform the steps provided in the Configuring Agentless Monitoring Mode section, but with the following changes:
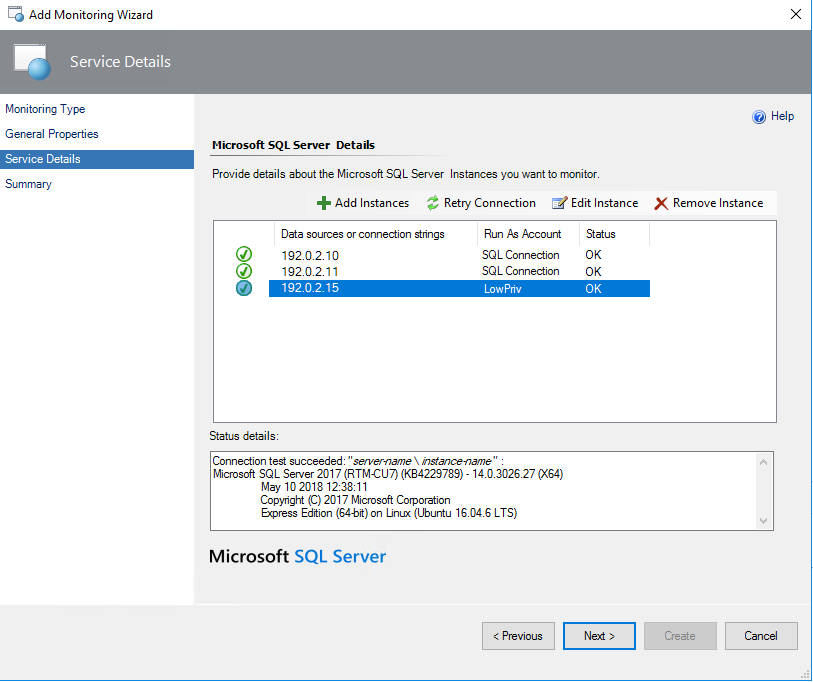
In the Add Monitoring Wizard window, select Add Instances.
In the Add Instances window, select a common Run As account with the appropriate SQL low-privilege login, and specify data sources and/or connection strings.
For example:
- 192.0.2.10;MachineName="server-name";InstanceName="instance-name";Platform="Windows"
- 192.0.2.11,50626;MachineName="server-name";InstanceName="instance-name";Platform="Windows"
- 192.0.2.15;MachineName="server-name";InstanceName="instance-name";Platform="Linux"
You can also create a new Run As account. For that, in the Add Instances window, select New, enter a new name for the Run As account, and specify credentials to access the SQL Server that you want to monitor.
After the connection is established, you can view and edit properties of the added instance.
Mixed Monitoring
To configure low-privilege mixed monitoring, perform the steps described in the Agent Monitoring section and do the following:
Managing Remote Access to WMI
To configure security for configurations with low-privilege accounts, perform the following steps on each mixed mode monitoring server:
Launch the mmc.exe console and add the following snap-ins:
- Component Services
- WMI Control (for a local computer)
Expand Component Services, right-click My Computer, and select Properties.
Open the COM Security tab.
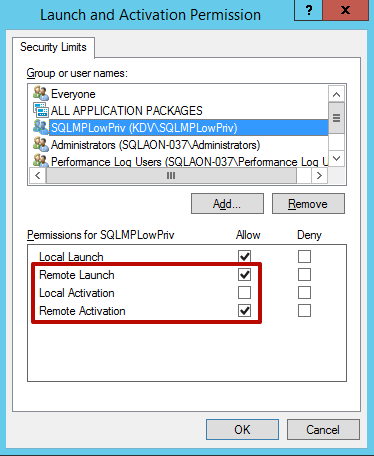
In the Launch and Activation Permissions section, select Edit Limits.
Grant the following permissions to the remote machine account:
- Remote Launch
- Remote Activation
Go to the WMI Control snap-in and open its properties.
Open the Security tab and select the following namespaces:
- ROOT\CIMV2
- ROOT\Microsoft\SqlServer
- ROOT\Microsoft\SqlServer\ComputerManagement11 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement12 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement13 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement14 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement15 (if exists)
- ROOT\Microsoft\SqlServer\ComputerManagement16 (if exists)
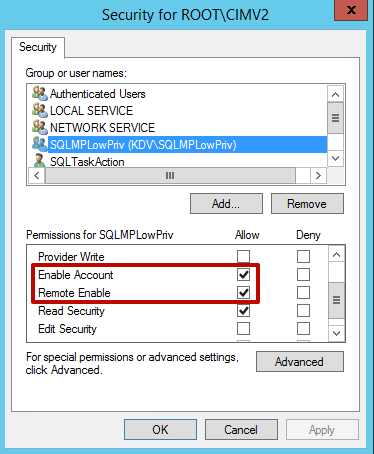
Select Security.
Grant the following permissions to the target computer:
- Enable Account
- Remote Enable
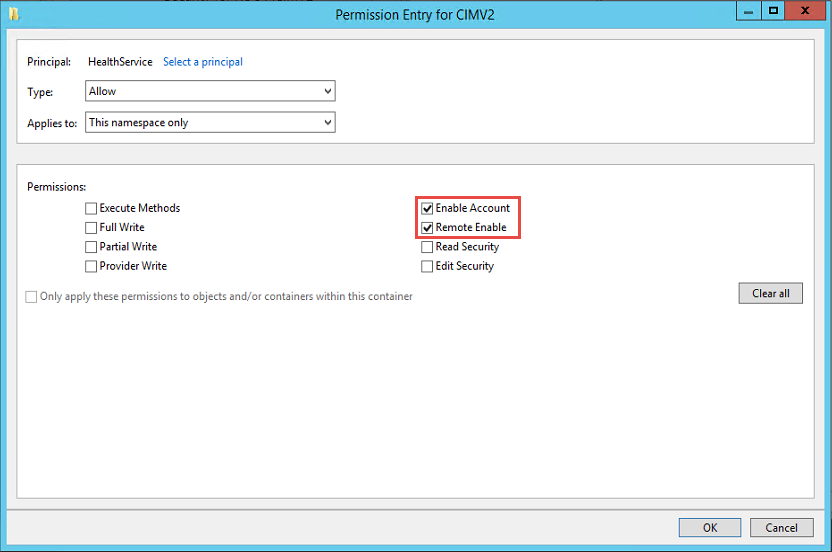
Select Advanced.
Select the target account and select Edit.
From the Applies to dropdown list, select This namespace only.
In the Permissions section, enable the following checkboxes:
- Enable Account
- Remote Enable
Granting Service Permissions
To get information about the services, grant required permissions according to the following steps:
Open the PowerShell console.
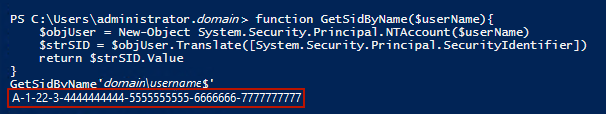
Run the following command to retrieve a Spotlight User SID.
function GetSidByName($userName){ $objUser = New-Object System.Security.Principal.NTAccount($userName) $strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier]) return $strSID.Value } GetSidByName 'domainName\userName'Replace domainName\userName with the domain and user names for the Spotlight User account.
From the Windows command prompt, run the following command to retrieve the current SDDL for the Services Control Manager:
sc sdshow scmanager > file.txtThe SDDL is saved to the file.txt file and looks similar to the following one:
D:(A;;CC;;;AU)(A;;CCLCRPRC;;;IU)(A;;CCLCRPRC;;;SU)(A;;CCLCRPWPRC;;;SY)(A;;KA;;;BA)S:(AU;FA;KA;;;WD)(AU;OIIOFA;GA;;;WD).Modify the SDDL string by copying the SDDL section that ends in IU (Interactive Users).
This section is enclosed in parentheses (that is, A;;CCLCRPRC;;;IU). Paste this clause directly after the clause you've copied.
Replace the IU string with the Spotlight User SID in the following text.
The new SDDL looks similar to the following one:
D:(A;;CC;;;AU)(A;;CCLCRPRC;;;IU) (A;;CCLCRPRC;;;A-1-22-3-4444444444-5555555555-6666666-7777777777)(A;;CCLCRPRC;;;SU)(A;;CCLCRPWPRC;;;SY)(A;;KA;;;BA) S:(AU;FA;KA;;;WD)(AU;OIIOFA;GA;;;WD)Set the security credentials to access the Service Control Manager by using the sdset command.
sc sdset scmanager "D:(A;;CC;;;AU)(A;;CCLCRPRC;;;IU)(A;;CCLCRPRC;;;SU)(A;;CCLCRPWPRC;;;SY)(A;;KA;;;BA)(A;;CCLCRPRC;;;A-1-22-3-4444444444-5555555555-6666666-7777777777)S:(AU;FA;KA;;;WD)(AU;OIIOFA;GA;;;WD)"Set rights for SQL Server, SQL agent, and SQL Full-text Filter Daemon Launcher services by using the Command-Line Tool SubInACL utility for the Spotlight User SID.
Run the utility with the following options:
subinacl.exe /service mssqlserver /GRANT= A-1-22-3-4444444444-5555555555-6666666-7777777777=LQSEI subinacl.exe /service sqlserveragent /GRANT= A-1-22-3-4444444444-5555555555-6666666-7777777777=LQSEI subinacl.exe /service mssqlfdlauncher /GRANT= A-1-22-3-4444444444-5555555555-6666666-7777777777=LQSEI
The following rights can be read as:
- L: Read contro
- Q: Query Service Configuration
- S: Query Service Status
- E: Enumerate Dependent Services
- I: Interrogate Service
Set the rights for ClusSvc (Cluster Service) using the Command-Line Tool SubInACL utility for the Spotlight User SID.
Run the utility with the following options:
subinacl.exe /service clussvc /GRANT= A-1-22-3-4444444444-5555555555-6666666-7777777777=LQSEI
Managing Remote Access to the Registry
Create a registry key to manage remote access to the registry.
To create a key, perform the following steps:
Open Registry Editor, and locate the following key
HKLM\SYSTEM\CurrentControlSet\ControlIn the Edit menu, select Add Key and enter the following values:
- Key Name: SecurePipeServers
- Class: REG_SZ
Locate the following key
HKLM\SYSTEM\CurrentControlSet\Control\SecurePipeServersIn the Edit menu, select Add Key and enter the following values:
- Key Name: winreg
- Class: REG_SZ
Locate the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurePipeServers\winregIn the Edit menu, select Add Key and enter the following values:
- Value Name: Description
- Data Type: REG_SZ
- String: Registry Server
Locate the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurePipeServers\winregRight-click winreg, select Permissions, and edit the current permissions, or add users or groups you want to grant access to.
Quit Registry Editor and restart Windows.